Illinois Business Law Journal
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Universidad Complutense De Madrid
UNIVERSIDAD COMPLUTENSE DE MADRID FACULTAD DE FILOLOGÍA Departamento de Filología Inglesa II TESIS DOCTORAL La familia como destino Eugene O'Neill y Sam Shepard MEMORIA PARA OPTAR AL GRADO DE DOCTOR PRESENTADA POR James William Flath Directores Félix Martín Gutiérrez Gustavo Sánchez Canales Madrid, 2014 © James William Flath, 2013 UNIVERSIDAD COMPLUTENSE DE MADRID Departamento de Filología Inglesa II TESIS DOCTORAL LA FAMILIA COMO DESTINO EN EUGENE O’NEILL Y SAM SHEPARD James William Flath Madrid, 2013 Directores: Dr. Félix Martín Gutiérrez Dr. Gustavo Sánchez Canales 1 Preface and acknowledgments This dissertation represents a culmination of work, reading and learning that has taken place over the past few years. I first became interested in the plays of Eugene O’Neill when I was an undergraduate in the United States. I came upon playwright Sam Shepard much later but from the beginning the similarities between the two struck me as uncanny. What moved me particularly was the way each playwright portrayed the time-honored American institution of the Family and how both focused on the idea that I’ve come to refer to as “family as fate.” I began to ask myself, why did these playwrights write such gut-wrenchingly harrowing portrayals of the family? To exorcise their own ghosts? To come to terms with themselves? But even more compelling is the question why are we so attracted to these plays? What do we see in these plays? Ourselves, our nation? I began my research to see if anyone had devoted a full-scale study to this phenomenon and discovered that others had also noticed the similarities but none had done as in-depth a study as I wished to do. -

From the on Inal Document. What Can I Write About?
DOCUMENT RESUME ED 470 655 CS 511 615 TITLE What Can I Write about? 7,000 Topics for High School Students. Second Edition, Revised and Updated. INSTITUTION National Council of Teachers of English, Urbana, IL. ISBN ISBN-0-8141-5654-1 PUB DATE 2002-00-00 NOTE 153p.; Based on the original edition by David Powell (ED 204 814). AVAILABLE FROM National Council of Teachers of English, 1111 W. Kenyon Road, Urbana, IL 61801-1096 (Stock no. 56541-1659: $17.95, members; $23.95, nonmembers). Tel: 800-369-6283 (Toll Free); Web site: http://www.ncte.org. PUB TYPE Books (010) Guides Classroom Learner (051) Guides Classroom Teacher (052) EDRS PRICE EDRS Price MF01/PC07 Plus Postage. DESCRIPTORS High Schools; *Writing (Composition); Writing Assignments; *Writing Instruction; *Writing Strategies IDENTIFIERS Genre Approach; *Writing Topics ABSTRACT Substantially updated for today's world, this second edition offers chapters on 12 different categories of writing, each of which is briefly introduced with a definition, notes on appropriate writing strategies, and suggestions for using the book to locate topics. Types of writing covered include description, comparison/contrast, process, narrative, classification/division, cause-and-effect writing, exposition, argumentation, definition, research-and-report writing, creative writing, and critical writing. Ideas in the book range from the profound to the everyday to the topical--e.g., describe a terrible beauty; write a narrative about the ultimate eccentric; classify kinds of body alterations. With hundreds of new topics, the book is intended to be a resource for teachers and students alike. (NKA) Reproductions supplied by EDRS are the best that can be made from the on inal document. -

Subverting Or Reasserting? Westworld (2016-) As an Ambiguous Critical Allegory of Gender Struggles
#24 SUBVERTING OR REASSERTING? WESTWORLD (2016-) AS AN AMBIGUOUS CRITICAL ALLEGORY OF GENDER STRUGGLES Miguel Sebastián-Martín Universidad de Salamanca Ilustración || Isela Leduc Artículo || Recibido: 19/07/2020 | Apto Comité Científico: 04/11/2020 | Publicado: 01/2021 DOI: 10.1344/452f.2021.24.9 [email protected] Licencia || Reconocimiento-No comercial-Sin obras derivadas 3.0 License 129 Resumen || Este artículo analiza las tres primeras temporadas de la serie de HBO Westworld (2016-2020), considerándolas una alegoría crítica de las relaciones de género. Se presta especial atención a la construcción autorreflexiva de sus mundos de ciencia ficción y a dos de los arcos narrativos de los personajes principales, las androides femeninas (o ginoides) Dolores y Maeve. Más específicamente, el ensayo consiste en un examen dialéctico de las ambigüedades narrativas de la serie, por lo que su argumento es doble. Por un lado, se argumenta que Westworld está clara y conscientemente construida como una alegoría crítica y que, como tal, sus mundos de ciencia ficción escenifican luchas sociales reales (principalmente, aquellas entre géneros) para narrar posteriormente su (intento) de derrocamiento. Por otro lado, en contra de esta interpretación crítico-alegórica, pero completándola, también se argumenta que Westworld no es una narrativa inequívocamente crítica y que, si vamos a examinar sus potenciales alegóricos, debemos considerar también cómo su realización puede ser obstaculizada y/o contradicha por ciertas ambigüedades narrativas. Palabras clave || Westworld | Ciencia ficción | Metaficción | Alegoría crítica | Género Abstract || This article analyses the first three seasons of HBO’s Westworld (2016-2020) by considering them a critical allegory of gender relations. In so doing, the text pays special attention to the self-reflexive construction of its SF worlds, and to two of the main characters’ arcs, the female androids (or gynoids) Dolores and Maeve. -

Metaphors of Patriarchy in Orphan Black and Westworld
Feminist Media Studies ISSN: 1468-0777 (Print) 1471-5902 (Online) Journal homepage: https://www.tandfonline.com/loi/rfms20 Metaphors of patriarchy in Orphan Black and Westworld Olivia Belton To cite this article: Olivia Belton (2020): Metaphors of patriarchy in OrphanBlack and Westworld, Feminist Media Studies, DOI: 10.1080/14680777.2019.1707701 To link to this article: https://doi.org/10.1080/14680777.2019.1707701 Published online: 21 Jan 2020. Submit your article to this journal Article views: 70 View related articles View Crossmark data Full Terms & Conditions of access and use can be found at https://www.tandfonline.com/action/journalInformation?journalCode=rfms20 FEMINIST MEDIA STUDIES https://doi.org/10.1080/14680777.2019.1707701 Metaphors of patriarchy in Orphan Black and Westworld Olivia Belton Leverhulme Centre for the Future of Intelligence, University of Cambridge, Cambridge, UK ABSTRACT ARTICLE HISTORY Orphan Black (2013–17) and Westworld (2016-) use their science Received 7 August 2018 fiction narratives to create metaphors for patriarchal oppression. Revised 12 November 2019 The female protagonists struggle against the paternalistic scientists Accepted 18 December 2019 and corporate leaders who seek to control them. These series break KEYWORDS away from more liberal representations of feminism on television Science fiction; television; by explicitly portraying how systemic patriarchal oppression seeks patriarchy; cyborgs; to control and exploit women, especially under capitalism. They feminism also engage with radical feminist ideas of separatism and compul- sory heterosexuality. The science fiction plots allow them to deal with feminist issues. Westworld uses computer programming as a metaphor for patriarchal social conditioning, while Orphan Black’s clones recall cyborg feminism. -
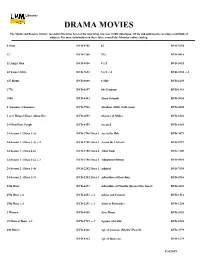
Drama Movies
Libraries DRAMA MOVIES The Media and Reserve Library, located in the lower level of the west wing, has over 9,000 videotapes, DVDs and audiobooks covering a multitude of subjects. For more information on these titles, consult the Libraries' online catalog. 0.5mm DVD-8746 42 DVD-5254 12 DVD-1200 70's DVD-0418 12 Angry Men DVD-0850 8 1/2 DVD-3832 12 Years a Slave DVD-7691 8 1/2 c.2 DVD-3832 c.2 127 Hours DVD-8008 8 Mile DVD-1639 1776 DVD-0397 9th Company DVD-1383 1900 DVD-4443 About Schmidt DVD-9630 2 Autumns, 3 Summers DVD-7930 Abraham (Bible Collection) DVD-0602 2 or 3 Things I Know About Her DVD-6091 Absence of Malice DVD-8243 24 Hour Party People DVD-8359 Accused DVD-6182 24 Season 1 (Discs 1-3) DVD-2780 Discs 1 Ace in the Hole DVD-9473 24 Season 1 (Discs 1-3) c.2 DVD-2780 Discs 1 Across the Universe DVD-5997 24 Season 1 (Discs 4-6) DVD-2780 Discs 4 Adam Bede DVD-7149 24 Season 1 (Discs 4-6) c.2 DVD-2780 Discs 4 Adjustment Bureau DVD-9591 24 Season 2 (Discs 1-4) DVD-2282 Discs 1 Admiral DVD-7558 24 Season 2 (Discs 5-7) DVD-2282 Discs 5 Adventures of Don Juan DVD-2916 25th Hour DVD-2291 Adventures of Priscilla Queen of the Desert DVD-4365 25th Hour c.2 DVD-2291 c.2 Advise and Consent DVD-1514 25th Hour c.3 DVD-2291 c.3 Affair to Remember DVD-1201 3 Women DVD-4850 After Hours DVD-3053 35 Shots of Rum c.2 DVD-4729 c.2 Against All Odds DVD-8241 400 Blows DVD-0336 Age of Consent (Michael Powell) DVD-4779 DVD-8362 Age of Innocence DVD-6179 8/30/2019 Age of Innocence c.2 DVD-6179 c.2 All the King's Men DVD-3291 Agony and the Ecstasy DVD-3308 DVD-9634 Aguirre: The Wrath of God DVD-4816 All the Mornings of the World DVD-1274 Aladin (Bollywood) DVD-6178 All the President's Men DVD-8371 Alexander Nevsky DVD-4983 Amadeus DVD-0099 Alfie DVD-9492 Amar Akbar Anthony DVD-5078 Ali: Fear Eats the Soul DVD-4725 Amarcord DVD-4426 Ali: Fear Eats the Soul c.2 DVD-4725 c.2 Amazing Dr. -

And Index. Geographic Name: Europe History 20Th Century
Includes bibliographical references (p. 245-260) and index. Geographic Name: Europe History 20th century. Geographic Name: Europe Economic conditions 1945-. Geographic Name: Europe Defenses. Rubrics: War and society Europe Politics and war. Download Where have all the soldiers gone : the transformation of modern Europe James J. Sheehan. leave here couple of words about this book: Tags: Art Soviet. Strategy is the calculated relationship of means to ends. At the highest military level, that relationship guides the use of the joint and combined military instrument of power to achieve national military strategic objectives. At the national or grand strategic level, the relationship becomes more complex, dealing with multiple, interrelated objectives that can only be achieved by the coordinated use of all the instruments of national power, to include that of the military. In a rapidly changing, increasingly more complicated and interdependent world, the U.S. military professional needs to u Defense Of The British Empire, 1914-1918; 7. The American Navy, 1922-1945; 8. The British Navy, 1918-1945; 9. Sea Power For Containment: The U.S. Navy In The Cold War; 10.The Future Of Sea Power Selected BibliographyIndex; About The Editors And Contributors These essays explore the link between the naval strength and global power of Great Britain and the United. States from 1815 to the present. The American theory of naval strategy, on the other hand, assumed that one had to engage the enemy in order to assure command of the sea. These case studies illustrate once again that naval history must include cultural, economic, political, and social contexts. -

Long Day's Journey Into Night, to Kill a Mockingbird and Julius Caesar
SUPPORT FOR THE 2018 SEASON OF THE STUDIO THEATRE IS GENEROUSLY PROVIDED BY SANDRA & JIM PITBLADO PRODUCTION SUPPORT IS GENEROUSLY PROVIDED BY ALICE & TIM THORNTON 2 CLASSICLASSIC FILMS OscarWildeCinema.com TM CINEPLEX EVENTS OPERA | DANCE | STAGE | GALLERY | CLASSIC FILMS For more information, visit Cineplex.com/Events @CineplexEvents EVENTS ™/® Cineplex Entertainment LP or used under license. CE_0226_EVCN_CPX_Events_Print_AD_5.375x8.375_v4.indd 1 2018-03-08 7:41 AM THE WILL TO BE FREE We all want to be free. But finding true freedom within our communities, within our families and within ourselves is no easy task. Nor is it easy to reconcile our own freedom with the political, religious and cultural freedoms of others. Happily, the conflict created by our search for freedom makes for great theatre... Shakespeare’s The Tempest, in which I’m delighted to direct Martha Henry, is a play about the yearning to be released from CLASSICCLASSI FILMS imprisonment, as revenge and forgiveness vie OscarWildeCinema.com TM for the upper hand in Prospero’s heart. Erin Shields’s exciting new interpretation of Milton’s Paradise Lost takes an ultra- contemporary look at humanity’s age-old desire for free will – and the consequences of acting on it. I’m very proud that we have the internationally renowned Robert Lepage with us directing Shakespeare’s Coriolanus, a play about early Roman democracy. It is as important to understanding the current state of our democratic institutions as is Shakespeare’s play about the end of the Roman Republic, Julius Caesar. Recent events have underlined the need for the iconic story To Kill a Mockingbird to be told, as a powerful reminder that there can be no freedom without justice. -
Long Day's Journey Into Night
Long Day’s Journey Into Night LONG DAY’S JOURNEY INTO NIGHT EUGENE O’NEILL CRITICAL EDITION Edited by William Davies King Foreword by Jessica Lange Foreword copyright © 2014 by Jessica Lange. Critical edition, including notes, chronology, essays, and bibliography, copyright © 2014 by William Davies King. Long Day’s Journey Into Night copyright © as an unpublished work 1955 by Carlotta Monterey O’Neill. Copyright © 1955 by Carlotta Monterey O’Neill. First published February 1956. Copyright © renewed 1984 by Yale University. Corrected edition copyright © 1989 by Yale University. All rights reserved. This book may not be reproduced, in whole or in part, including illustrations, in any form (beyond that copying permitted by Sections 107 and 108 of the US Copyright Law and except by reviewers for the public press), without written permission from the publishers. Yale University Press books may be purchased in quantity for educational, business, or promotional use. For information, please e-mail [email protected] (US office) or [email protected] (UK office). Frontispiece: Eugene O’Neill in 1939, at the time of writing Long Day’s Journey Into Night (Photo © Horace Bristol/Corbis. Louis Sheaffer–Eugene O’Neill Collection, Linda Lear Center for Special Collections & Archives, Connecticut College) Printed in the United States of America. Library of Congress Control Number: 2013956573 ISBN: 978-0-300-18641-3 (pbk.) 10 9 8 7 6 5 4 3 2 1 CAUTION: Professionals and amateurs are hereby warned that Long Day’s Journey Into Night, being fully protected under the copyright laws of the United States of America, the British Commonwealth, including Canada, and all other countries of the copyright union, is subject to royalties. -

“A New People and the Choices They Will Have to Make”
“A NEW PEOPLE AND THE CHOICES THEY WILL HAVE TO MAKE”: HUMANE HUMAN-AI COHABITATION IN HBO’S WESTWORLD By Merlijn Broersma S2598302 MA Dissertation LAX999M20 20 ECTS Dr. Timothy Jelfs 29 July, 2019 16618 words Broersma 1 In 1955, Disneyland’s opening “dedicat[ion] to the ideals, the dreams, and the hard facts that have created America” established the theme park as a peculiarly American space (Lambert 29). Just as the founding of the United States of America materialized a myth of freedom, theme parks turn myths into tangible experiences. French philosopher Jean Baudrillard argues, theme parks such as “Disneyland” are “presented as imaginary in order to make us believe that the rest” – those imaginary ideals, dreams, and hard facts that constitute the myth of America – “is real” (qtd. in Kellner 82). Although theme parks have spread all around the world, the most popular theme parks are all subdivisions of the American corporations Disney and Universal (Rubin 10-11). Theme Parks, then, as Baudrillard argued in his travel narrative America (1988), largely continue to function as “microcosm[s]” of American culture, which exploit “world[s] of the imagination” to elevate banal acts of consumption into mythical experiences (55). Similar to fully-immersive theme park attractions, which offer escape from the triviality that surrounds them, contemporary digital devices offer largely pleasure-driven environments where people all over the world spend increasing amounts of time. Nevertheless, theme park escapes remain space dependent, whereas digital escapes can be enjoyed boundlessly. For all this pleasure, however, James Williams argues in Stand Out of Our Light (2018) that contemporary “design[s] of digital technologies” are “fail[ing] to take into account our ‘almost infinite appetite for distractions’” – precisely that appetite which Aldous Huxley epitomized in Brave New World Revisited (1958) (11). -

Sam Shepard's Gothic Family Plays
University of Tennessee, Knoxville TRACE: Tennessee Research and Creative Exchange Doctoral Dissertations Graduate School 8-2003 The Other Side of Love: Sam Shepard’s Gothic Family Plays Eric Andrew Lee University of Tennessee - Knoxville Follow this and additional works at: https://trace.tennessee.edu/utk_graddiss Part of the English Language and Literature Commons Recommended Citation Lee, Eric Andrew, "The Other Side of Love: Sam Shepard’s Gothic Family Plays. " PhD diss., University of Tennessee, 2003. https://trace.tennessee.edu/utk_graddiss/2112 This Dissertation is brought to you for free and open access by the Graduate School at TRACE: Tennessee Research and Creative Exchange. It has been accepted for inclusion in Doctoral Dissertations by an authorized administrator of TRACE: Tennessee Research and Creative Exchange. For more information, please contact [email protected]. To the Graduate Council: I am submitting herewith a dissertation written by Eric Andrew Lee entitled "The Other Side of Love: Sam Shepard’s Gothic Family Plays." I have examined the final electronic copy of this dissertation for form and content and recommend that it be accepted in partial fulfillment of the requirements for the degree of Doctor of Philosophy, with a major in English. Stanton B. Garner, Jr, Major Professor We have read this dissertation and recommend its acceptance: Charles J. Maland, Thomas F. Haddox, Klaus van den Berg Accepted for the Council: Carolyn R. Hodges Vice Provost and Dean of the Graduate School (Original signatures are on file with official studentecor r ds.) To the Graduate Council: I am submitting herewith a dissertation written by Eric Andrew Lee entitled “The Other Side of Love: Sam Shepard’s Gothic Family Plays.” I have examined the final electronic copy of this dissertation for form and content and recommend that it be accepted in partial fulfillment of the requirements for the degree of Doctor of Philosophy, with a major in English. -

The Fallacy of Rape Narratives As Paths to Women’S Empowerment in Contemporary Television
Connecticut College Digital Commons @ Connecticut College Film Studies Honors Papers Film Studies Department 2020 “What Doesn’t Kill You Makes You Stronger:” The Fallacy of Rape Narratives as Paths to Women’s Empowerment in Contemporary Television Alessia S. Guise Connecticut College, [email protected] Follow this and additional works at: https://digitalcommons.conncoll.edu/filmhp Part of the Feminist, Gender, and Sexuality Studies Commons, and the Film and Media Studies Commons Recommended Citation Guise, Alessia S., "“What Doesn’t Kill You Makes You Stronger:” The Fallacy of Rape Narratives as Paths to Women’s Empowerment in Contemporary Television" (2020). Film Studies Honors Papers. 7. https://digitalcommons.conncoll.edu/filmhp/7 This Honors Paper is brought to you for free and open access by the Film Studies Department at Digital Commons @ Connecticut College. It has been accepted for inclusion in Film Studies Honors Papers by an authorized administrator of Digital Commons @ Connecticut College. For more information, please contact [email protected]. The views expressed in this paper are solely those of the author. “What Doesn’t Kill You Makes You Stronger:” The Fallacy of Rape Narratives as Paths to Women’s Empowerment in Contemporary Television An Honors Thesis Presented By Alessia S. Guise To The Department of Film Studies In Fulfillment of the Requirements for Honors in the Major Field Connecticut College New London, Connecticut May 2020 2 Acknowledgements I would first and foremost like to thank my advisor, Dr. Nina Martin. I have been Dr. M’s student since my first semester at Connecticut College, and I can honestly say that I would not be the scholar, the feminist, or the person I am today without her guidance and instruction throughout the past four years. -
University of Chester Department of English Mres in English EN7005 Dissertation 2017-18
‘Amazed anew’: The Posthuman Dream, the Repetitive System, and Novum Decay in Modern Works of SF Item Type Thesis or dissertation Authors Hay, Jonathan D. Citation Hay, J. D. (2018). ‘Amazed anew’: The Posthuman Dream, the Repetitive System, and Novum Decay in Modern Works of SF. (Masters thesis). University of Chester, United Kingdom. Publisher University of Chester Rights Attribution-NonCommercial-NoDerivs 3.0 United States Download date 26/09/2021 19:33:42 Item License http://creativecommons.org/licenses/by-nc-nd/3.0/us/ Link to Item http://hdl.handle.net/10034/621722 University of Chester Department of English MRes in English EN7005 Dissertation 2017-18 ‘Amazed anew’: The Posthuman Dream, the Repetitive System, and Novum Decay in Modern Works of SF J08836 J08836 Abstract This study contends that modern texts within the Science Fiction genre can be seen to espouse a posthuman dream, and so to encourage the (post)human reader, viewer, listener, or player to consider the posthuman potentialities of our species’ future in correspondence with their own social present. Modern Science Fiction texts achieve this figurative function through the employment of repetitive systems, through which they prominently depict recognizable elements of the (post)human present within their otherwise radically defamiliarizing posthuman milieu. Therefore, whilst the newnesses within Science Fiction texts have commonly been presumed to be the predominant element of the genre, this study enjoins that the mundane, quotidian or banal elements of the genre are just as vital to its constitution. This radical rereading of the genre is not heedlessly contrarian, but rather comprises an important critical intervention within the fields of Critical Posthumanism and Science Fiction Studies.