Chapter 29 Server Virtualization with Hyper-V
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Hyper-V on Windows 10
Hyper-V on Windows 10 LEAD | PROTECT | SUPPORT Industry leader in IT Solutions, Consulting and Cybersecurity Overview • Hyper-V is a “hypervisor” or a virtual machine monitor “VMM” • Made by Microsoft, free in Windows 10 Pro or Enterprise • Allows you to run virtual machines (guest machines) on your desktop (host machine) • Use cases include: • Running incompatible software • Experimenting with other operating systems (Windows, Linux, etc.) • Exporting virtual machines from your host into Azure Prerequisites • Windows 10 Pro / Enterprise / Education • 64-bit architecture • Hyper-V enabled in BIOS • At least 4GB RAM (8GB recommended) • At least 10GB disk space free (SSD recommended) What’s my build? • Windows key + “System Information” • Version (build) • Architecture • 64-bit (“x64”) vs 32-bit (“x86”) • CPU • RAM • Disk Enabling Hyper-V • “Turn Windows features on or off” • Hyper-V Creating your virtual machine • Download an ISO image (xx.iso) (i.e., Microsoft) • Create a virtual switch • Create a new virtual machine • Name it • Specify Generation • Specify RAM • Specify virtual switch • Specify disk space • Specify ISO Avoiding a Microsoft Live account • If you’re like me, you don’t want to have to create an account to set this up • If you’re on wifi, make sure your assigned virtual switch is set to ethernet • If you’re on ethernet, make sure your assigned virtual switch is set to wifi • When setting up a vm, if no internet is available, Microsoft lets you skip the required Microsoft Live account registration Last steps • Enter your license key (you need to purchase this) • Windows will require a license key for Windows 10 Enterprise • A single Win 10 Ent entitles you to (3) virtual machines • Budget $380 for this Win 10 Ent license (Linux is free) • Install your previously incompatible software • Backup your VHD before you start using it and periodically Hyper-V Demo LEAD | PROTECT | SUPPORT Industry leader in IT Solutions, Consulting and Cybersecurity Managed IT Services Cybersecurity & Compliance Technology Consulting Application Development. -
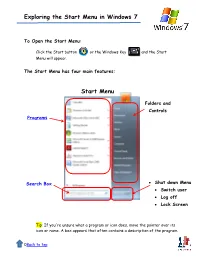
Exploring the Start Menu in Windows 7
Exploring the Start Menu in Windows 7 To Open the Start Menu: Click the Start button or the Windows Key and the Start Menu will appear. The Start Menu has four main features: Start Menu Folders and Controls Programs Shut down Menu Search Box Switch user Log off Lock Screen Tip: If you're unsure what a program or icon does, move the pointer over its icon or name. A box appears that often contains a description of the program. 0Back to top Exploring the Start Menu in Windows 7 Programs (Left Pane of the Start Menu) The programs list includes recently used programs and “Pinned” programs. Click once on a program icon to open it Jump List: If an entry has a black menu arrow, clicking on it will show a “Jump List” of recently opened and Pinned documents. Documents can be opened directly from this list. Jump List Left Click on “All Programs” to show a list of available programs and folders. Organize and move icons by left clicking, then dragging to the desired location. 0Back to top Exploring the Start Menu in Windows 7 Adding or Removing a Program on the Start Menu or Taskbar: Adding or “Pinning” a program on the Start Menu or Taskbar: 1. Find the program icon in the Start Menu, All Programs or Taskbar 2. Right click on the program icon 3. Select “Pin to Taskbar” and/or “Pin to Start Menu” 4. The icon will now be Pinned (stuck) to the selected area. 5. Icons can also be added to the Taskbar from the Start Menu by clicking on the icon in the Start Menu and dragging it to the Taskbar. -
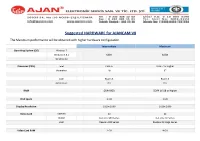
Suggested HARDWARE for AJANCAM V8 the Maximum Performance Will Be Obtained with Higher Hardware Configuration
Suggested HARDWARE for AJANCAM V8 The Maximum performance will be obtained with higher hardware configuration. Intermediate Maximum Operating System (OS) Windows 7 Windows 8, 8.1 64Bit 64 Bit Windows 10 Processor (CPU) Intel Core i5 Core i7 or Higher Generation 7th 8th AMD Ryzen 5 Ryzen 7 Architecture Zen Zen RAM DDR4 8GB DDR4 16 GB or Higher Disk Space 2 GB 2 GB Display Resolution 1920x 1080 1920x 1080 Video Card DIRECTX 12 12 NVIDIA GeForce 900 Series GeForce 10 Series AMD Raedon 300 Series Raedon RX Vega Series Video Card RAM 2 GB 4 GB Guidelines Software Requirements Windows 7 SP1 Windows 8 Windows 8.1 Windows 10 DirectX 11 DirectX 11 DirectX 11.1 DirectX 12 .Net Framework 4.5 .Net Framework 4.5 .Net Framework 4.5 .Net Framework 4.5 Windows 7 Notes Service Pack 1 must be installed on Windows 7. Refer: https://support.microsoft.com/en-us/help/15090/windows-7-install-service-pack-1-sp1 Platform Update for Windows 7 Platform update for Windows 7 must be installed. User can download from: https://www.microsoft.com/en-us/download/details.aspx?id=36805 and can read detailed instructions here. For 32 Bit, Windows6.1-KB2670838-x86.msu For 64 Bit, Windows6.1-KB2670838-x64.msu Note: Platform Update is required only for Windows 7. For windows 8, 8.1 and 10, platform update is not required. Optional: If you are facing graphics card related issues please see the following Update Graphics Card Driver (Optional) When users face problems with their graphics cards, they should try to update graphics card drivers as follows: 1) Open the Run dialog box by pressing and holding the “Windows” key, then press the “R” key. -

KEYBOARD SHORTCUTS (Windows)
KEYBOARD SHORTCUTS (Windows) Note: For Mac users, please substitute the Command key for the Ctrl key. This substitution with work for the majority of commands _______________________________________________________________________ General Commands Navigation Windows key + D Desktop to foreground Context menu Right click Alt + underlined letter Menu drop down, Action selection Alt + Tab Toggle between open applications Alt, F + X or Alt + F4 Exit application Alt, Spacebar + X Maximize window Alt, Spacebar + N Minimize window Ctrl + W Closes window F2 Renames a selected file or folder Open Programs To open programs from START menu: Create a program shortcut and drop it into START menu To open programs/files on Desktop: Select first letter, and then press Enter to open Dialog Boxes Enter Selects highlighted button Tab Selects next button Arrow keys Selects next (>) or previous button (<) Shift + Tab Selects previous button _______________________________________________________________________ Microsoft Word Formatting Ctrl + P Print Ctrl + S Save Ctrl + Z Undo Ctrl + Y Redo CTRL+B Make text bold CTRL+I Italicize CTRL+U Underline Ctrl + C Copy Ctrl + V Paste Ctrl + X Copy + delete Shift + F3 Change case of letters Ctrl+Shift+> Increase font size Ctrl+Shift+< Decrease font size Highlight Text Shift + Arrow Keys Selects one letter at a time Shift + Ctrl + Arrow keys Selects one word at a time Shift + End or Home Selects lines of text Change or resize the font CTRL+SHIFT+ > Increase the font size 1 KEYBOARD SHORTCUTS (Windows) CTRL+SHIFT+ < -
![Drobo Dashboard Release Notes Release Date: May 14, 2013 VERSION INFORMATION Drobo Dashboard: Version 2.5.2 [64171] (Mac) Version 2.5.2 [64171] (Windows)](https://docslib.b-cdn.net/cover/6977/drobo-dashboard-release-notes-release-date-may-14-2013-version-information-drobo-dashboard-version-2-5-2-64171-mac-version-2-5-2-64171-windows-1076977.webp)
Drobo Dashboard Release Notes Release Date: May 14, 2013 VERSION INFORMATION Drobo Dashboard: Version 2.5.2 [64171] (Mac) Version 2.5.2 [64171] (Windows)
Drobo Dashboard Release Notes Release Date: May 14, 2013 VERSION INFORMATION Drobo Dashboard: Version 2.5.2 [64171] (Mac) Version 2.5.2 [64171] (Windows) KEY HIGHLIGHTS This is a new release version of Drobo Dashboard for Mac and Windows. Key highlights of this release are: This version of Drobo Dashboard is compatible with all Drobo models - Drobo Gen 2, Drobo FS, Drobo S, DroboPro, DroboPro FS, B800fs, DroboElite, B800i, B1200i, Drobo 5D, Drobo Mini and Drobo 5N. Fixed iSCSI connectivity issues due to Java update on Mac OSX 10.8.x hosts Localization improvements Fixed unexpected quit on Mac OSX 10.8.x hosts KNOWN ISSUES All Operating Systems Symptom: Attempting to install multiple versions of Drobo Dashboard at the same time, will fail. Condition: Installing a different (newer or older) Drobo Dashboard version over the existing Drobo Dashboard version installed on the host system, will overwrite the existing version. Workaround: Always use the latest supported version of Drobo Dashboard. Symptom: Attempting to log in with an incorrect iSCSI CHAP password will return generic error. Condition: When logging in a volume with an incorrect CHAP password, Drobo Dashboard will report “Operation failed” error. Workaround: Enter the correct password. If you do not remember the correct password, you can reset the password by logging in as administrator in Drobo Dashboard, disabling CHAP password and re-enabling CHAP password by entering a new value in the password field. Symptom: Formatting volumes when connected to Drobo B1200i via the management port is not available. Condition: When connected to Drobo B1200i via the management port, Drobo Dashboard can be used for changing device settings and creating or deleting volumes. -
Essential Accessibility Windows User Manual
Windows USER MANUAL TABLE OF CONTENTS GETTING STARTED WITH ESSENTIAL ACCESSIBILITY™ .............................................1 What is eSSENTIAL Accessibility™?............................................................................. 1 eSSENTIAL Accessibility™: A quick overview ......................................................... 1 About this manual................................................................................................................ 1 INTRODUCTION: WINDOWS APPLICATION ..................................................................2 What is the Windows application? ............................................................................... 2 System Requirements........................................................................................................ 2 How to install the Windows Application.................................................................... 3 GETTING STARTED WITH THE WINDOWS APPLICATION .......................................3 Starting and updating the Windows application..................................................... 3 Windows application description ................................................................................. 4 “Exit” button or how to close the application ........................................................... 5 “Help” button or getting help on using the Windows application .................... 6 How to move in the settings............................................................................................ 6 General settings -

Hyper-V on Dell Poweredge VRTX Deployment Guide Notes, Cautions, and Warnings
Microsoft Windows Server 2012 R2 - Hyper-V on Dell PowerEdge VRTX Deployment Guide Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your computer. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. Copyright © 2015 Dell Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual property laws. Dell™ and the Dell logo are trademarks of Dell Inc. in the United States and/or other jurisdictions. All other marks and names mentioned herein may be trademarks of their respective companies. 2015 - 07 Rev. A00 Contents 1 Abbreviations......................................................................................................... 5 2 Audience.................................................................................................................6 3 Scope.......................................................................................................................7 4 Overview................................................................................................................ 8 5 Solution requirements......................................................................................... 9 Hardware requirements........................................................................................................................ 9 Software requirements..........................................................................................................................9 -

Windows 10 First Use.1903.Pdf
************** READ ME FIRST ************** If the computer does not start or will not boot to the below instructions please contact us first. While we do our best to ensure safe transit, parts inside can get loose with all the bouncing around and even if the box looks undamaged, those lose parts will stop the computer from booting properly or at all. Email us at: [email protected] or call us at (405) 241-8300 and we will fully help you. ** Do not connect your Ethernet Cable or Wireless adapter at first; you will be prompted to connect during setup. ** 1. The first time you power on your computer, Windows Flag appears while files in the background load “Just a moment”. 2. “Let’s start with region. Is this right?”; United States is selected (leave this), click Yes. 3. “Is this the right keyboard layout?”; US is selected (leave this), click Yes. 4. “Want to add a second keyboard layout?”, click Skip. 5. “Let’s connect you to a network”; plug in your Ethernet Cable or a USB Wireless Adapter (sold separately) if available. a. If you don’t have internet setup yet, click I don’t have internet (bottom left) and Skip to step 8. b. If using Wireless, click on your network, click Connect. Enter security key and click Next. “Allow your PC to be discoverable”, choose Yes or No, will connect and then click Next (bottom right). c. If using Ethernet Cable, it will automatically connect you, click Next (bottom right). 6. “Setting up”, (this might take several minutes), Don’t turn off your device. -

X2O Media Player-C
X2O Media Player-C Setup Guide This document provides instructions for setting up the X2O Media Player-C. Copyright © 2020 X2O Media Inc. All rights reserved. All trademarks are the property of their respective owners. Setup Guide Table of Contents Introduction ....................................................................................................................................................................... 3 System Layout ................................................................................................................................................................... 3 Disk Layout .................................................................................................................................................................... 3 Account Layout ............................................................................................................................................................ 4 System Security ................................................................................................................................................................. 5 Unneeded Services Disabled ................................................................................................................................... 5 Windows Firewall ......................................................................................................................................................... 5 Antivirus ......................................................................................................................................................................... -

Windows Storage Server 2012
DIGILIANT Windows Storage Server 2012 User’s Guide Copyright © 2012 Digiliant, LLC. All Rights Reserved. This User’s Guide is provided AS‐IS and Digiliant, LLC makes no warranty as to its accuracies or use. Any use of this documentation or the information contained therein is at the risk of the user. Documentation may include technical or other inaccuracies or typographical errors. Digiliant, LLC reserves the right to make changes to this documentation at any time without prior notice. Digiliant and the Digiliant Logo are registered trademarks of Digiliant, LLC and may not be used without writtrn permission. Microsoft, Microsoft Windows Storage Server 2012, the Windows Logo, and all other trademarks are the property of Microsoft Corporation and their respective owners. No part of this documentation may be reproduced, transmited, or translated by any means, electronic, mechanical, optical, other by any other means without the prior written permission of Digiliant, LLC. 1 OVERVIEW OF WINDOWS STORAGE SERVER 2012 ................................................................................................ 1 NEW STORAGE INNOVATIONS IN WINDOWS STORAGE SERVER 2012......................................................................................... 1 The goals for storage were to deliver innovations in four areas: ..................................................................................... 1 New capabilities: .................................................................................................................................................................... -

Windows 10: Part 1
Windows 10: Part 1 Updated: May 2018 Price: $2.00 A Special Note on Terminology Windows 10 accepts both mouse and touch commands. This means that you could use either mouse clicks or touch gestures interchangeably. Throughout this document, you will read either click, tap, or click/tap. Please note that you can click on anything that says “tap,” and you can tap on anything that says “click.” Click = Tap Double Click = Double Tap Click and Drag = Tap and Drag Right Click = Tap and Hold NOTE: You must have a touchscreen to use touch commands. What is Windows 10? Windows 10 is Microsoft’s latest operating system for home and work computers. An operating system (OS) is a collection of software that enables the user to interact with the computer. Currently, Windows is still the most popular OS on the market for personal or home computers. The Microsoft Account Before we go further, let’s talk about the Microsoft Account. When you first upgrade to Windows 10, or purchase a computer with Windows 10, you will have the opportunity to create a Microsoft ID. NOTE: You do not have to create an ID, but some features require you to create an account. A Microsoft ID allows you to access Internet-connected apps, the Microsoft Store, and Cortana. If these terms are new to you—don’t worry!—we will explain them later. For now, know that as you get more used to the computer, you may need to create a Microsoft account to use additional features in Windows. Lesson 1: Touring Windows 10 The Desktop After you start your computer and sign into Windows, you will see the desktop. -

Streamlined OS Deployment Using Bootable USB Devices and Lifecycle Controller Simplify OS Installation on Dell EMC Poweredge Servers by Using USB Devices
Streamlined OS deployment using bootable USB devices and Lifecycle Controller Simplify OS installation on Dell EMC PowerEdge servers by using USB devices. Abstract This Dell EMC Technical White Paper provides detailed information about the capabilities of Lifecycle Controller to deploy operating systems via bootable USB devices on Dell EMC PowerEdge servers. Lifecycle Controller provides a quick and easy way to install an operating system using a CD, DVD, or an ISO image. Operating system installation is now further simplified by adding support for USB devices. October 2018 Dell EMC Technical White Paper Revisions Revisions Date Description October 2018 Initial release Acknowledgements This paper was produced by the following members of the Dell EMC engineering team: Author: Rohit Kumar Arehalli The information in this publication is provided “as is.” Dell Inc. makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose. Use, copying, and distribution of any software described in this publication requires an applicable software license. © 2018 Dell Inc. or its subsidiaries. All Rights Reserved. Dell, EMC, Dell EMC and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners. Dell believes the information in this document is accurate as of its publication date. The information is subject to change without notice. 2 Streamlined