X2O Media Player-C
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lab Report: 7.1.6 Configure Windows Defender
Lab Report: 7.1.6 Configure Windows Defender Your Performance Your Score: 0 of 6 (0%) Pass Status: Not Passed Elapsed Time: 12 seconds Required Score: 100% Task Summary Perform a full scan once per week Hide Details Perform the scan on Saturday Perform the scan at midnight (12:00 am) Perform a full system scan Check for updates before scanning Configure default actions to take Hide Details Remove severe alert items Remove high alert items Remove medium alert items Allow low alert items Apply recommended actions to items detected during a scan Configure advanced options Hide Details Scan email Scan removable drives Display items from all users of this computer Perform a quick scan Explanation In this lab, your task is to configure Windows Defender as follows: Automatic scanning setting: Frequency: Saturday Approximate time: 12:00 am Type: Full scan (A quick scan checks the areas of the computer that spyware is likely to affect, and a full scan checks all files and programs on the computer) Check for updated definitions before scanning: Enabled Default actions settings: Severe alert items: Remove High alert items: Remove Medium alert items: Remove Low alert items: Allow Apply recommended actions: Enabled Advanced settings: Scan email: Enabled Scan removable drives: Enabled Administrator settings: Display items from all users of this computer: Enabled Complete this lab as follows: 1. Right-click Start > Control Panel. 2. In the top right corner under View by, select Small icons from the drop-down list. 3. Select Windows Defender. 4. Select Tools. 5. Under Settings, select Options. 6. Make sure Automatically scan my computer (recommended) is selected to allow Windows Defender to scan the computer automatically. -

Mitigating Service Account Credential Theft on Windows
Mitigating Service Account Credential Theft on Windows Reducing the risk of automated authentication against untrusted endpoints Version 1.0.0 Last Updated: 2014-09-16 Mitigating Service Account Credential Theft on Windows Disclaimer This document is for informational purposes only. The authors make no warranties, express, implied, or statutory as to the information in the document. This document is provided "as-is". Information and views expressed in this document, including URLs and other Internet website references, may change without notice. You bear the risk of using it. This document is provided under the Creative Commons Attribution 4.0 International (CC BY 4.0) license. The names of actual companies and products mentioned herein may be the trademarks of their respective owners. Authors HD Moore Joe Bialek Ashwath Murthy Rapid7 Microsoft Palo Alto Networks Contents Executive Summary ................................................................................................................................................................ 1 Introduction ............................................................................................................................................................................ 2 Attacks .................................................................................................................................................................................... 2 Kerberos ............................................................................................................................................................................. -

Windows Server Security Best Practices
Windows Server Security – Best Practices v.3.0.5 Windows Server Security Best Practices Revised – February 7, 2020 Version 2.0.0 ______________________________________________________________________________________ Page 1 of 10 Windows Server Security – Best Practices v.3.0.5 Initial Document Created by: 2009 Windows Server Security Best Practices Committee Document Creation Date: August 21, 2009 Revision Revised by: 2019 Windows Server Security Best Practices Committee Revision Date: February 7, 2020 Version Number: 2.0.0 Acknowledgments The final release document is a collaborative work between the following committee members: Freddie Lewis Khushbu Desai Theodore McDonald Tanya Sootes Usage The ever-changing nature of information technology prevents this document from being entirely inclusive but should serve as a general guideline. This document is not intended to supersede or replace policy. Please feel free to query the Windows Server Team ([email protected]) or the Systems Administrator Group ([email protected]) for additional guidance. ______________________________________________________________________________________ Page 2 of 10 Windows Server Security – Best Practices v.3.0.5 Table of Contents Initial Document 2 Revision 2 Acknowledgments 2 Usage 2 1. Security Best Practices 5 1.1. User Environment 5 1.1.1. Server Account Control 5 1.1.2. Administrator and Equivalents 5 1.1.3. Delegating Control 5 1.1.4. Password Policy 5 1.2. File and Print Serving 5 1.2.1. Folder and NTFS Permissions 5 1.2.2. Print Management 6 1.3. Remote Access 6 1.3.1. Remote Desktop 6 1.3.2. Off-Campus Access 6 1.4. OS Configuration and Maintenance 6 1.4.1. -

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -

Hyper-V on Windows 10
Hyper-V on Windows 10 LEAD | PROTECT | SUPPORT Industry leader in IT Solutions, Consulting and Cybersecurity Overview • Hyper-V is a “hypervisor” or a virtual machine monitor “VMM” • Made by Microsoft, free in Windows 10 Pro or Enterprise • Allows you to run virtual machines (guest machines) on your desktop (host machine) • Use cases include: • Running incompatible software • Experimenting with other operating systems (Windows, Linux, etc.) • Exporting virtual machines from your host into Azure Prerequisites • Windows 10 Pro / Enterprise / Education • 64-bit architecture • Hyper-V enabled in BIOS • At least 4GB RAM (8GB recommended) • At least 10GB disk space free (SSD recommended) What’s my build? • Windows key + “System Information” • Version (build) • Architecture • 64-bit (“x64”) vs 32-bit (“x86”) • CPU • RAM • Disk Enabling Hyper-V • “Turn Windows features on or off” • Hyper-V Creating your virtual machine • Download an ISO image (xx.iso) (i.e., Microsoft) • Create a virtual switch • Create a new virtual machine • Name it • Specify Generation • Specify RAM • Specify virtual switch • Specify disk space • Specify ISO Avoiding a Microsoft Live account • If you’re like me, you don’t want to have to create an account to set this up • If you’re on wifi, make sure your assigned virtual switch is set to ethernet • If you’re on ethernet, make sure your assigned virtual switch is set to wifi • When setting up a vm, if no internet is available, Microsoft lets you skip the required Microsoft Live account registration Last steps • Enter your license key (you need to purchase this) • Windows will require a license key for Windows 10 Enterprise • A single Win 10 Ent entitles you to (3) virtual machines • Budget $380 for this Win 10 Ent license (Linux is free) • Install your previously incompatible software • Backup your VHD before you start using it and periodically Hyper-V Demo LEAD | PROTECT | SUPPORT Industry leader in IT Solutions, Consulting and Cybersecurity Managed IT Services Cybersecurity & Compliance Technology Consulting Application Development. -
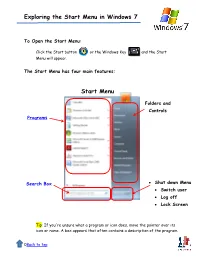
Exploring the Start Menu in Windows 7
Exploring the Start Menu in Windows 7 To Open the Start Menu: Click the Start button or the Windows Key and the Start Menu will appear. The Start Menu has four main features: Start Menu Folders and Controls Programs Shut down Menu Search Box Switch user Log off Lock Screen Tip: If you're unsure what a program or icon does, move the pointer over its icon or name. A box appears that often contains a description of the program. 0Back to top Exploring the Start Menu in Windows 7 Programs (Left Pane of the Start Menu) The programs list includes recently used programs and “Pinned” programs. Click once on a program icon to open it Jump List: If an entry has a black menu arrow, clicking on it will show a “Jump List” of recently opened and Pinned documents. Documents can be opened directly from this list. Jump List Left Click on “All Programs” to show a list of available programs and folders. Organize and move icons by left clicking, then dragging to the desired location. 0Back to top Exploring the Start Menu in Windows 7 Adding or Removing a Program on the Start Menu or Taskbar: Adding or “Pinning” a program on the Start Menu or Taskbar: 1. Find the program icon in the Start Menu, All Programs or Taskbar 2. Right click on the program icon 3. Select “Pin to Taskbar” and/or “Pin to Start Menu” 4. The icon will now be Pinned (stuck) to the selected area. 5. Icons can also be added to the Taskbar from the Start Menu by clicking on the icon in the Start Menu and dragging it to the Taskbar. -

Microsoft Windows Server 2019 Version 1809 Hyper-V
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

Firewall Configuration Guide
CardAccess Firewall Configuration Guide (For Windows 7 Pro, Windows 8.1 Pro, Windows Server 2008 R2 and Windows 2012 R2) DATE: 11 JULY 2014 DOCUMENT PERTAINS TO: CONFIGURING THE WINDOWS FIREWALL REVISION: REV B CardAccess © Continental 2011 Firewall Configuration Guide 1 DISCLAIMER Continental Instruments LLC makes no representations or warranties with respect to the contents hereof and specifical- ly disclaims any implied warranties of merchantability or fitness for any particular purpose. Further, Continental Instru- ments LLC reserves the right to revise this publication and to make changes from time to time in the content hereof without obligation of Continental Instruments LLC to notify any person of such revision or changes. If possible, always refer to the Continental Access website (www.cicaccess.com; click Support) for the latest documentation, as the re- leased CD may not contain the latest documentation. Copyright © 2011 by Continental Instruments LLC. All rights reserved. No part of this publication may be re- produced, transmitted, transcribed, or stored in a retrieval system, without the prior written permission of Continental Instruments LLC, 355 Bayview Avenue, Amityville, NY 11701. Telephone: 631-842-9400 • FAX: 631-842-9135 • GSA# GS-07F-0039H. ProxCard® and ProxKey® are trademarks of the HID© Corporation. Microsoft® and Windows® are trademarks of their the Microsoft Corporation. Trilogy® is a registered trademark of Alarm Lock. All other trademarks, service marks, and product or service names described in this manual are for identification purposes only and may be trademarks or regis- tered trademarks of their respective owners. The absence of a name or logo in this document does not constitute a waiver of any and all intellectual property rights that NAPCO Security Technologies, Inc. -
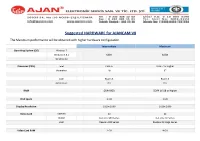
Suggested HARDWARE for AJANCAM V8 the Maximum Performance Will Be Obtained with Higher Hardware Configuration
Suggested HARDWARE for AJANCAM V8 The Maximum performance will be obtained with higher hardware configuration. Intermediate Maximum Operating System (OS) Windows 7 Windows 8, 8.1 64Bit 64 Bit Windows 10 Processor (CPU) Intel Core i5 Core i7 or Higher Generation 7th 8th AMD Ryzen 5 Ryzen 7 Architecture Zen Zen RAM DDR4 8GB DDR4 16 GB or Higher Disk Space 2 GB 2 GB Display Resolution 1920x 1080 1920x 1080 Video Card DIRECTX 12 12 NVIDIA GeForce 900 Series GeForce 10 Series AMD Raedon 300 Series Raedon RX Vega Series Video Card RAM 2 GB 4 GB Guidelines Software Requirements Windows 7 SP1 Windows 8 Windows 8.1 Windows 10 DirectX 11 DirectX 11 DirectX 11.1 DirectX 12 .Net Framework 4.5 .Net Framework 4.5 .Net Framework 4.5 .Net Framework 4.5 Windows 7 Notes Service Pack 1 must be installed on Windows 7. Refer: https://support.microsoft.com/en-us/help/15090/windows-7-install-service-pack-1-sp1 Platform Update for Windows 7 Platform update for Windows 7 must be installed. User can download from: https://www.microsoft.com/en-us/download/details.aspx?id=36805 and can read detailed instructions here. For 32 Bit, Windows6.1-KB2670838-x86.msu For 64 Bit, Windows6.1-KB2670838-x64.msu Note: Platform Update is required only for Windows 7. For windows 8, 8.1 and 10, platform update is not required. Optional: If you are facing graphics card related issues please see the following Update Graphics Card Driver (Optional) When users face problems with their graphics cards, they should try to update graphics card drivers as follows: 1) Open the Run dialog box by pressing and holding the “Windows” key, then press the “R” key. -

Windows Firewall with Advanced Security Page 1 of 115
Windows Firewall with Advanced Security Page 1 of 115 Windows Firewall with Advanced Security You can use Windows Firewall with Advanced Security to help you protect the computers on your network. Windows Firewall with Advanced Security includes a stateful firewall that allows you to determine which network traffic is permitted to pass between your computer and the network. It also includes connection security rules that use Internet Protocol security (IPsec) to protect traffic as it travels across the network. Important Windows Firewall with Advanced Security is designed for administrators of a managed network to secure network traffic in an enterprise environment. Home users should use the Windows Firewall program in Control Panel instead. To start the Windows Firewall program, click Start, click Control Panel, click System and Security, and then click Windows Firewall. You can access Help for the Windows Firewall program either by pressing the F1 key on the main Windows Firewall page, or by clicking the links found on many of the Windows Firewall dialog boxes. For more information about Windows Firewall with Advanced Security, see Windows Firewall with Advanced Security Content Roadmap (http://go.microsoft.com/fwlink/?linkid=64342) in the Windows Server TechCenter. Overview of Windows Firewall with Advanced Security Understanding Firewall Rules Understanding Connection Security Rules Understanding Firewall Profiles Monitoring Windows Firewall with Advanced Security Default Settings for Windows Firewall with Advanced Security Configuring Firewall Rules Resources for Windows Firewall with Advanced Security User Interface: Windows Firewall with Advanced Security Overview of Windows Firewall with Advanced Security What is Windows Firewall with Advanced Security? file://C:\Users\Malli\AppData\Local\Temp\~hhADBE.htm 9/29/2011 Windows Firewall with Advanced Security Page 2 of 115 Windows Firewall with Advanced Security combines a host firewall and Internet Protocol security (IPsec). -

KEYBOARD SHORTCUTS (Windows)
KEYBOARD SHORTCUTS (Windows) Note: For Mac users, please substitute the Command key for the Ctrl key. This substitution with work for the majority of commands _______________________________________________________________________ General Commands Navigation Windows key + D Desktop to foreground Context menu Right click Alt + underlined letter Menu drop down, Action selection Alt + Tab Toggle between open applications Alt, F + X or Alt + F4 Exit application Alt, Spacebar + X Maximize window Alt, Spacebar + N Minimize window Ctrl + W Closes window F2 Renames a selected file or folder Open Programs To open programs from START menu: Create a program shortcut and drop it into START menu To open programs/files on Desktop: Select first letter, and then press Enter to open Dialog Boxes Enter Selects highlighted button Tab Selects next button Arrow keys Selects next (>) or previous button (<) Shift + Tab Selects previous button _______________________________________________________________________ Microsoft Word Formatting Ctrl + P Print Ctrl + S Save Ctrl + Z Undo Ctrl + Y Redo CTRL+B Make text bold CTRL+I Italicize CTRL+U Underline Ctrl + C Copy Ctrl + V Paste Ctrl + X Copy + delete Shift + F3 Change case of letters Ctrl+Shift+> Increase font size Ctrl+Shift+< Decrease font size Highlight Text Shift + Arrow Keys Selects one letter at a time Shift + Ctrl + Arrow keys Selects one word at a time Shift + End or Home Selects lines of text Change or resize the font CTRL+SHIFT+ > Increase the font size 1 KEYBOARD SHORTCUTS (Windows) CTRL+SHIFT+ < -

Mediasite System Requirements & Troubleshooting
Mediasite System Requirements & Troubleshooting Mediasite Viewer controls: System Requirements: Sonic Foundry recommends a viewer's computer meet the following system requirements for the best presentation viewing experience with Mediasite Viewer: Windows Windows 2000, Windows XP, Windows 2003, or Windows Vista Display resolution of 800x600 pixels or greater 768 MB of memory (RAM) or greater 1 Mediasite System Requirements & Troubleshooting Windows-compatible sound card Microsoft Internet Explorer 6.0 SP1 or later, or Firefox 2.0 or later Windows Media Player 9.0 or later Download Here Broadband Internet connection (DSL 256 Kbps & above) for live and on- demand presentations. Dial-up (54 Kbps) will not work with Mediasite. We also recommend using a wired connection (Ethernet) instead of a wireless connection, where it is possible. Enable Javacript 1. Internet Explorer: 1. Menu: Tools » Internet Options 2. Click on the Security tab 3. Click the Custom Level button near the bottom 4. Scroll down the list to Scripting, Active scripting 5. Click Enable 6. Click OK Twice 2. Firefox: 1. Menu: Tools » Options 2. Click on the Content icon/tab 3. Check the box for Enable JavaScript 4. Click OK 3. Or upgrade your browser to a version that supports JavaScript 1.2 or higher. Download Here Mac Mac OS X 10.4.8 or later 768 MB of memory (RAM) or greater Safari 2.0.4 or later or Firefox 2.0 or later Enable Javascript 1. Select "Safari" from the top menu 2. Choose "Preferences" 3. Choose "Security” 4. Select the checkbox next to "Enable JavaScript" Silverlight 1.0 (viewers will be prompted to install this when viewing a presentation) Download Here Please note that the following features are not currently available with the Silverlight viewer: speed control, closed captioning, and full screen video.