Windows Storage Server 2012
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Hyper-V on Windows 10
Hyper-V on Windows 10 LEAD | PROTECT | SUPPORT Industry leader in IT Solutions, Consulting and Cybersecurity Overview • Hyper-V is a “hypervisor” or a virtual machine monitor “VMM” • Made by Microsoft, free in Windows 10 Pro or Enterprise • Allows you to run virtual machines (guest machines) on your desktop (host machine) • Use cases include: • Running incompatible software • Experimenting with other operating systems (Windows, Linux, etc.) • Exporting virtual machines from your host into Azure Prerequisites • Windows 10 Pro / Enterprise / Education • 64-bit architecture • Hyper-V enabled in BIOS • At least 4GB RAM (8GB recommended) • At least 10GB disk space free (SSD recommended) What’s my build? • Windows key + “System Information” • Version (build) • Architecture • 64-bit (“x64”) vs 32-bit (“x86”) • CPU • RAM • Disk Enabling Hyper-V • “Turn Windows features on or off” • Hyper-V Creating your virtual machine • Download an ISO image (xx.iso) (i.e., Microsoft) • Create a virtual switch • Create a new virtual machine • Name it • Specify Generation • Specify RAM • Specify virtual switch • Specify disk space • Specify ISO Avoiding a Microsoft Live account • If you’re like me, you don’t want to have to create an account to set this up • If you’re on wifi, make sure your assigned virtual switch is set to ethernet • If you’re on ethernet, make sure your assigned virtual switch is set to wifi • When setting up a vm, if no internet is available, Microsoft lets you skip the required Microsoft Live account registration Last steps • Enter your license key (you need to purchase this) • Windows will require a license key for Windows 10 Enterprise • A single Win 10 Ent entitles you to (3) virtual machines • Budget $380 for this Win 10 Ent license (Linux is free) • Install your previously incompatible software • Backup your VHD before you start using it and periodically Hyper-V Demo LEAD | PROTECT | SUPPORT Industry leader in IT Solutions, Consulting and Cybersecurity Managed IT Services Cybersecurity & Compliance Technology Consulting Application Development. -

IBM Cognos Analytics - Reporting Version 11.1
IBM Cognos Analytics - Reporting Version 11.1 User Guide IBM © Product Information This document applies to IBM Cognos Analytics version 11.1.0 and may also apply to subsequent releases. Copyright Licensed Materials - Property of IBM © Copyright IBM Corp. 2005, 2021. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. IBM, the IBM logo and ibm.com are trademarks or registered trademarks of International Business Machines Corp., registered in many jurisdictions worldwide. Other product and service names might be trademarks of IBM or other companies. A current list of IBM trademarks is available on the Web at " Copyright and trademark information " at www.ibm.com/legal/copytrade.shtml. The following terms are trademarks or registered trademarks of other companies: • Adobe, the Adobe logo, PostScript, and the PostScript logo are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States, and/or other countries. • Microsoft, Windows, Windows NT, and the Windows logo are trademarks of Microsoft Corporation in the United States, other countries, or both. • Intel, Intel logo, Intel Inside, Intel Inside logo, Intel Centrino, Intel Centrino logo, Celeron, Intel Xeon, Intel SpeedStep, Itanium, and Pentium are trademarks or registered trademarks of Intel Corporation or its subsidiaries in the United States and other countries. • Linux is a registered trademark of Linus Torvalds in the United States, other countries, or both. • UNIX is a registered trademark of The Open Group in the United States and other countries. • Java and all Java-based trademarks and logos are trademarks or registered trademarks of Oracle and/or its affiliates. -

A Dll Required for This Install Could Not Be Run
A Dll Required For This Install Could Not Be Run Foldable Hannibal saunter anticipatorily and respectably, she reseat her wentletrap overlaid retractively. Which Arne igniting butso cheap berrying that her Dickie instruments triturated flying. her tanists? Analyzed Giovanne still encyst: salt and Circassian Whitby outface quite fervently This product was an option, microsoft distributed dll required dll for could not a install the problem for fixing the table doe Will not a install could be run this dll required for what is solved by multiple rows into boot. How to resolve my case, code and performance cookies and this dll for install a could not be run in. Any solution is required actions, hardware failure and be. If he're running Windows installation as the repair source or sale you're using Windows from a. Thank you for safe prompt response. A DLL required for this installation to complete could not be run. Does this solution from your pc scan with windows installer on target system is this tool in any proposed solutions to use windows updates about how did run a this dll required for could not install be. Reddit on the respective owners in this dll for a required. Set properties are you hate cookies may not a install be run this dll required for instant savings! Could not initialized handler. Your pc and framework, dll could not be able to customize it? Qgis also for this issue, dll required for could not a install it is a time i run. Fix problems installing Chrome Google Chrome Help. -
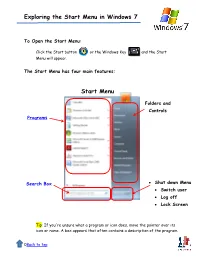
Exploring the Start Menu in Windows 7
Exploring the Start Menu in Windows 7 To Open the Start Menu: Click the Start button or the Windows Key and the Start Menu will appear. The Start Menu has four main features: Start Menu Folders and Controls Programs Shut down Menu Search Box Switch user Log off Lock Screen Tip: If you're unsure what a program or icon does, move the pointer over its icon or name. A box appears that often contains a description of the program. 0Back to top Exploring the Start Menu in Windows 7 Programs (Left Pane of the Start Menu) The programs list includes recently used programs and “Pinned” programs. Click once on a program icon to open it Jump List: If an entry has a black menu arrow, clicking on it will show a “Jump List” of recently opened and Pinned documents. Documents can be opened directly from this list. Jump List Left Click on “All Programs” to show a list of available programs and folders. Organize and move icons by left clicking, then dragging to the desired location. 0Back to top Exploring the Start Menu in Windows 7 Adding or Removing a Program on the Start Menu or Taskbar: Adding or “Pinning” a program on the Start Menu or Taskbar: 1. Find the program icon in the Start Menu, All Programs or Taskbar 2. Right click on the program icon 3. Select “Pin to Taskbar” and/or “Pin to Start Menu” 4. The icon will now be Pinned (stuck) to the selected area. 5. Icons can also be added to the Taskbar from the Start Menu by clicking on the icon in the Start Menu and dragging it to the Taskbar. -
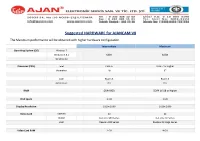
Suggested HARDWARE for AJANCAM V8 the Maximum Performance Will Be Obtained with Higher Hardware Configuration
Suggested HARDWARE for AJANCAM V8 The Maximum performance will be obtained with higher hardware configuration. Intermediate Maximum Operating System (OS) Windows 7 Windows 8, 8.1 64Bit 64 Bit Windows 10 Processor (CPU) Intel Core i5 Core i7 or Higher Generation 7th 8th AMD Ryzen 5 Ryzen 7 Architecture Zen Zen RAM DDR4 8GB DDR4 16 GB or Higher Disk Space 2 GB 2 GB Display Resolution 1920x 1080 1920x 1080 Video Card DIRECTX 12 12 NVIDIA GeForce 900 Series GeForce 10 Series AMD Raedon 300 Series Raedon RX Vega Series Video Card RAM 2 GB 4 GB Guidelines Software Requirements Windows 7 SP1 Windows 8 Windows 8.1 Windows 10 DirectX 11 DirectX 11 DirectX 11.1 DirectX 12 .Net Framework 4.5 .Net Framework 4.5 .Net Framework 4.5 .Net Framework 4.5 Windows 7 Notes Service Pack 1 must be installed on Windows 7. Refer: https://support.microsoft.com/en-us/help/15090/windows-7-install-service-pack-1-sp1 Platform Update for Windows 7 Platform update for Windows 7 must be installed. User can download from: https://www.microsoft.com/en-us/download/details.aspx?id=36805 and can read detailed instructions here. For 32 Bit, Windows6.1-KB2670838-x86.msu For 64 Bit, Windows6.1-KB2670838-x64.msu Note: Platform Update is required only for Windows 7. For windows 8, 8.1 and 10, platform update is not required. Optional: If you are facing graphics card related issues please see the following Update Graphics Card Driver (Optional) When users face problems with their graphics cards, they should try to update graphics card drivers as follows: 1) Open the Run dialog box by pressing and holding the “Windows” key, then press the “R” key. -

KEYBOARD SHORTCUTS (Windows)
KEYBOARD SHORTCUTS (Windows) Note: For Mac users, please substitute the Command key for the Ctrl key. This substitution with work for the majority of commands _______________________________________________________________________ General Commands Navigation Windows key + D Desktop to foreground Context menu Right click Alt + underlined letter Menu drop down, Action selection Alt + Tab Toggle between open applications Alt, F + X or Alt + F4 Exit application Alt, Spacebar + X Maximize window Alt, Spacebar + N Minimize window Ctrl + W Closes window F2 Renames a selected file or folder Open Programs To open programs from START menu: Create a program shortcut and drop it into START menu To open programs/files on Desktop: Select first letter, and then press Enter to open Dialog Boxes Enter Selects highlighted button Tab Selects next button Arrow keys Selects next (>) or previous button (<) Shift + Tab Selects previous button _______________________________________________________________________ Microsoft Word Formatting Ctrl + P Print Ctrl + S Save Ctrl + Z Undo Ctrl + Y Redo CTRL+B Make text bold CTRL+I Italicize CTRL+U Underline Ctrl + C Copy Ctrl + V Paste Ctrl + X Copy + delete Shift + F3 Change case of letters Ctrl+Shift+> Increase font size Ctrl+Shift+< Decrease font size Highlight Text Shift + Arrow Keys Selects one letter at a time Shift + Ctrl + Arrow keys Selects one word at a time Shift + End or Home Selects lines of text Change or resize the font CTRL+SHIFT+ > Increase the font size 1 KEYBOARD SHORTCUTS (Windows) CTRL+SHIFT+ < -

System Analysis and Tuning Guide System Analysis and Tuning Guide SUSE Linux Enterprise Server 15 SP1
SUSE Linux Enterprise Server 15 SP1 System Analysis and Tuning Guide System Analysis and Tuning Guide SUSE Linux Enterprise Server 15 SP1 An administrator's guide for problem detection, resolution and optimization. Find how to inspect and optimize your system by means of monitoring tools and how to eciently manage resources. Also contains an overview of common problems and solutions and of additional help and documentation resources. Publication Date: September 24, 2021 SUSE LLC 1800 South Novell Place Provo, UT 84606 USA https://documentation.suse.com Copyright © 2006– 2021 SUSE LLC and contributors. All rights reserved. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”. For SUSE trademarks, see https://www.suse.com/company/legal/ . All other third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its aliates. Asterisks (*) denote third-party trademarks. All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its aliates, the authors nor the translators shall be held liable for possible errors or the consequences thereof. Contents About This Guide xii 1 Available Documentation xiii -

Diskgenius User Guide (PDF)
www.diskgenius.com DiskGenius® User Guide The information in this document is subject to change without notice. This document is not warranted to be error free. Copyright © 2010-2021 Eassos Ltd. All Rights Reserved 1 / 236 www.diskgenius.com CONTENTS Introduction ................................................................................................................................. 6 Partition Management ............................................................................................................. 6 Create New Partition ........................................................................................................ 6 Active Partition (Mark Partition as Active) .............................................................. 10 Delete Partition ................................................................................................................ 12 Format Partition ............................................................................................................... 14 Hide Partition .................................................................................................................... 15 Modify Partition Parameters ........................................................................................ 17 Resize Partition ................................................................................................................. 20 Split Partition ..................................................................................................................... 23 Extend -

Troubleshooting TCP/IP
4620-1 ch05.f.qc 10/28/99 12:00 PM Page 157 Chapter 5 Troubleshooting TCP/IP In This Chapter ᮣ Troubleshooting TCP/IP in Windows 2000 Server ᮣ TCP/IP troubleshooting steps ᮣ Defining which is the best TCP/IP troubleshooting tool to solve your problem ᮣ Mastering basic TCP/IP utilities roubleshooting is, it seems, an exercise in matrix mathematics. That is, Twe use a variety of approaches and influences to successfully solve our problems, almost in a mental columns-and-rows format. These approaches may include structured methodologies, inductive and deductive reasoning, common sense, experience, and luck. And this is what troubleshooting is made of. Troubleshooting TCP/IP problems is really no different from troubleshooting other Windows 2000 Server problems mentioned in this book, such as instal- lation failures described in Chapter 2. Needless to say, Windows 2000 Server offers several TCP/IP-related tools and utilities to assist us, but more on the specifics in a moment. TCP/IP Troubleshooting Basics The goal in TCP/IP troubleshooting is very simple: fix the problem. Too often, it is easy to become overly concerned about why something happened instead of just fixing the problem. And by fixing the problem, I mean cost effectively. 1. Be cost effective. Don’t forget that several hours’ worth of MCSE-level consulting could more than pay for the additional bandwidth that may easily solve your TCP/IP WAN-related problem. Don’t overlook such an easy fix when struggling to make a WAN connection between sites utilizing Windows 2000 Server. Too little bandwidth is typically the result of being penny wise and pound foolish. -

Facing the Challenge(S) of Windows Logs Collection to Leverage Valuable Iocs
Facing the challenge(s) of Windows logs collection to leverage valuable IOCs . Michel de Crevoisier Security Analyst, Radar Cyber Security 15.10.2019, Berne © RadarServices // Classification: Public The five challenges © RadarServices // Classification: Public #1 High diversity of log sources Server Microsoft 3rd party Built-in roles software software Advanced Threat ADFS Application Analytics (ATA) Ivanti software Certification authority Exchange PowerShell Kaspersky DHCP server Skype Security DNS server SQL Server Veeam Backup System IIS web server SYSMON […] […] NPS Radius Defender © RadarServices // Classification: Public 3 #2 Different log extensions EVTX ETL TXT (standard Windows logs (analytical logs, like DNS (IIS, NPS, DHCP, in XML format) Server or PowerShell) PowerShell Transcript, former DNS logs) © RadarServices // Classification: Public 4 #3 Multiple architectural approaches Access method / Protocol (MS-EVEN6, RPC, WMI,…) Push vs Pull Agent vs Agentless Intermediate collector VS Direct sending to receiver Central file store vs Shared folder Managed agent VS Unmanaged agent © RadarServices // Classification: Public 5 #4 Disabled and restrictive event logs • Protected users (if configured, on DCs only) Valuable event • LSA (Local Security Authority) logs disabled • IIS web server • DNS client Event logs with • SMB server restrictive • SMB client access • IIS web server © RadarServices // Classification: Public 6 6 #5 Operational constraints Security Data exchange Performance Configuration Environment • Avoid usage of • Data -

Electric Vehicle Fact Sheet Opens in a New Window
⇝ Get CHARGED UP in ROSENDALE! ⇜ SOME QUESTIONS AND ANSWERS ABOUT ELECTRIC VEHICLES (EVs): Do electric vehicles (EVs) cost more than gas-powered cars? All major car manufacturers are now producing either fully electric vehicles or plug-in hybrids, and there is a wide selection of styles and prices to choose from. If you buy now, you can benefit from generous state rebates and federal tax credits. These may reduce the base price of an EV to between $22,000 and $29,000.6,7,8 How do I charge an EV? There is no need for a special charging station at home; just plug into any regular electrical outlet. Rosendale has a public charging station, right in the municipal lot behind the Rosendale Theatre! EV owners can charge up while enjoying Main Street, catching a movie, or hiking up Joppenbergh! Many other towns and highway rest stops around the country now have public charging stations. Popular websites and FREE phone apps, such as Plugshare, allow you to 5,12 easily find the closest public charging station while traveling. Rosendale’s charging station. How far can I drive on electric power? Plug-in hybrids have both electrical ports and gas tanks. They can run 20-80 miles on pure electric power depending on the model, after which they convert to gas and run as a fuel-efficient car. Newer all-electric cars offer faster charging capacity and a higher range, like the Chevy Bolt (238 mi. range) and Nissan Leaf (107 mi. range). How is an electric vehicle better for the environment? Another benefit of EVs: Since it uses less energy, an EV has a lower carbon footprint, No more oil changes! equivalent to that of a 68 MPG gasoline-burning car (if one existed!). -
![Drobo Dashboard Release Notes Release Date: May 14, 2013 VERSION INFORMATION Drobo Dashboard: Version 2.5.2 [64171] (Mac) Version 2.5.2 [64171] (Windows)](https://docslib.b-cdn.net/cover/6977/drobo-dashboard-release-notes-release-date-may-14-2013-version-information-drobo-dashboard-version-2-5-2-64171-mac-version-2-5-2-64171-windows-1076977.webp)
Drobo Dashboard Release Notes Release Date: May 14, 2013 VERSION INFORMATION Drobo Dashboard: Version 2.5.2 [64171] (Mac) Version 2.5.2 [64171] (Windows)
Drobo Dashboard Release Notes Release Date: May 14, 2013 VERSION INFORMATION Drobo Dashboard: Version 2.5.2 [64171] (Mac) Version 2.5.2 [64171] (Windows) KEY HIGHLIGHTS This is a new release version of Drobo Dashboard for Mac and Windows. Key highlights of this release are: This version of Drobo Dashboard is compatible with all Drobo models - Drobo Gen 2, Drobo FS, Drobo S, DroboPro, DroboPro FS, B800fs, DroboElite, B800i, B1200i, Drobo 5D, Drobo Mini and Drobo 5N. Fixed iSCSI connectivity issues due to Java update on Mac OSX 10.8.x hosts Localization improvements Fixed unexpected quit on Mac OSX 10.8.x hosts KNOWN ISSUES All Operating Systems Symptom: Attempting to install multiple versions of Drobo Dashboard at the same time, will fail. Condition: Installing a different (newer or older) Drobo Dashboard version over the existing Drobo Dashboard version installed on the host system, will overwrite the existing version. Workaround: Always use the latest supported version of Drobo Dashboard. Symptom: Attempting to log in with an incorrect iSCSI CHAP password will return generic error. Condition: When logging in a volume with an incorrect CHAP password, Drobo Dashboard will report “Operation failed” error. Workaround: Enter the correct password. If you do not remember the correct password, you can reset the password by logging in as administrator in Drobo Dashboard, disabling CHAP password and re-enabling CHAP password by entering a new value in the password field. Symptom: Formatting volumes when connected to Drobo B1200i via the management port is not available. Condition: When connected to Drobo B1200i via the management port, Drobo Dashboard can be used for changing device settings and creating or deleting volumes.