Krinsky, a Would Survive
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

September / October
AMERICAN SOCIETY FOR YAD VASHEM Vol. 46-No. 1 ISSN 0892-1571 September/October 2019-Tishri/Cheshvan 5780 “TWO ARE BETTER THAN ONE… AND A THREEFOLD CORD CANNOT QUICKLY BE BROKEN” n Sunday, November 17, 2019, the are leaders of numerous organizations, including membrance for their grandparents, and to rein- American Society for Yad Vashem AIPAC, WIZO, UJA, and American Friends of force their commitment to Yad Vashem so that will be honoring three generations of Rambam Hospital. the world will never forget. Oone family at our Annual Tribute Din- Jonathan and Sam Friedman have been ll three generations, including ner in New York City. The Gora-Sterling-Fried- deeply influenced by Mona, David and their ex- David’s three children — Ian and his man family reflects the theme of this year’s traordinary grandparents, Jack and Paula. Grow- wife Laura, Jeremy and his wife Tribute Dinner, which comes from Kohelet. “Two ing up, they both heard Jack tell his story of AMorgan, and Melissa — live in the are better than one… and a threefold cord can- survival and resilience at the Yom HaShoah pro- greater New York City area. They gather often, not quickly be broken” (4:9-12). All three gener- ations are proud supporters of Yad Vashem and are deeply committed to the mission of Holo- caust remembrance and education. Paula and Jack Gora will receive the ASYV Remembrance Award, Mona and David Sterling will receive the ASYV Achievement Award, and Samantha and Jonathan Friedman and Paz and Sam Friedman will receive the ASYV Young Leadership Award. -

Online Security and Privacy
Security & Privacy Guide Security and Privacy Guide When thinking about security and privacy settings you should consider: What do you want to protect? Who do you want to protect it from? Do you need to protect it? How bad are the consequences if you fail to protect it? How much trouble are you prepared to go to? These questions should be asked whilst considering what information you are accessing (which websites), how you are accessing the information, (what device you are using) and where you are accessing the information (at home, work, public place). Security & Privacy When looking at your Digital Security you are protecting your information against malicious attacks and malware. (Malware is software intentionally designed to cause damage to a computer). Digital Privacy is different as you are deciding what information you are prepared to share with a website or App (or its third party partners) that you are already using. Permission to share this information can be implicit once you start using a website or App. Some websites or Apps will allow you to control how they use your information. Security Physical access: How secure is the device you are using? Is it kept in a locked building, at home, or do you use it when you are out and about? Does anyone else have access to the device? Do you require a passcode or password to unlock your device? Virtual access: Have you updated your IOS software (on an iPad) or installed the latest anti-virus software on your device? Most devices will prompt you when an update is available. -

Password Managers an Overview
Peter Albin Lexington Computer and Technology Group March 13, 2019 Agenda One Solution 10 Worst Passwords of 2018 Time to Crack Password How Hackers Crack Passwords How Easy It Is To Crack Your Password How Do Password Managers Work What is a Password Manager Why use a Password Manager? Cloud Based Password Managers Paid Password Managers Free Password Managers How to Use LastPass How to Use Dashlane How to Use Keepass Final Reminder References March 13, 2019 2 One Solution March 13, 2019 3 10 Worst Passwords of 2018 1. 123456 2. password 3. 123456789 4. 12345678 5. 12345 6. 111111 7. 1234567 8. sunshine 9. qwerty 10. iloveyou March 13, 2019 4 Time to Crack Password March 13, 2019 5 Time to Crack Password March 13, 2019 6 Time to Crack Password March 13, 2019 7 Time to Crack Password Time to crack password "security1" 1600 1400 1200 1000 Days 800 Days 600 400 200 0 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 2013 2014 2015 2016 Year March 13, 2019 8 How Hackers Crack Passwords https://youtu.be/YiRPt4vrSSw March 13, 2019 9 How Easy It Is To Crack Your Password https://youtu.be/YiRPt4vrSSw March 13, 2019 10 How Do Password Managers Work https://youtu.be/DI72oBhMgWs March 13, 2019 11 What is a Password Manager A password manager will generate, retrieve, and keep track of super-long, crazy-random passwords across countless accounts for you, while also protecting all your vital online info—not only passwords but PINs, credit-card numbers and their three-digit CVV codes, answers to security questions, and more … And to get all that security, you’ll only need to remember a single password March 13, 2019 12 Why use a Password Manager? We are terrible at passwords We suck at creating them the top two most popular remain “123456” and “password” We share them way too freely We forget them all the time We forget them all the time A password manager relieves the burden of thinking up and memorizing unique, complex logins—the hallmark of a secure password. -

Handbook on Judaica Provenance Research: Ceremonial Objects
Looted Art and Jewish Cultural Property Initiative Salo Baron and members of the Synagogue Council of America depositing Torah scrolls in a grave at Beth El Cemetery, Paramus, New Jersey, 13 January 1952. Photograph by Fred Stein, collection of the American Jewish Historical Society, New York, USA. HANDBOOK ON JUDAICA PROVENANCE RESEARCH: CEREMONIAL OBJECTS By Julie-Marthe Cohen, Felicitas Heimann-Jelinek, and Ruth Jolanda Weinberger ©Conference on Jewish Material Claims Against Germany, 2018 Table of Contents Foreword, Wesley A. Fisher page 4 Disclaimer page 7 Preface page 8 PART 1 – Historical Overview 1.1 Pre-War Judaica and Jewish Museum Collections: An Overview page 12 1.2 Nazi Agencies Engaged in the Looting of Material Culture page 16 1.3 The Looting of Judaica: Museum Collections, Community Collections, page 28 and Private Collections - An Overview 1.4 The Dispersion of Jewish Ceremonial Objects in the West: Jewish Cultural Reconstruction page 43 1.5 The Dispersion of Jewish Ceremonial Objects in the East: The Soviet Trophy Brigades and Nationalizations in the East after World War II page 61 PART 2 – Judaica Objects 2.1 On the Definition of Judaica Objects page 77 2.2 Identification of Judaica Objects page 78 2.2.1 Inscriptions page 78 2.2.1.1 Names of Individuals page 78 2.2.1.2 Names of Communities and Towns page 79 2.2.1.3 Dates page 80 2.2.1.4 Crests page 80 2.2.2 Sizes page 81 2.2.3 Materials page 81 2.2.3.1 Textiles page 81 2.2.3.2 Metal page 82 2.2.3.3 Wood page 83 2.2.3.4 Paper page 83 2.2.3.5 Other page 83 2.2.4 Styles -

Gaono Minejimo Planas ENG
2020 PLAN FOR THE COMMEMORATION OF THE YEAR OF THE VILNA GAON AND OF THE HISTORY OF THE JEWS OF LITHUANIA QUARTER 1 Chapter I COMMEMORATIONS AND CONFERENCES Action (project) Responsible implementer Implementation deadline 1. To hold commemorations in Vilnius and Kaunas Ministry of Foreign Affairs Quarter 1, 2020 of the 120th anniversary of the birth of Chiune Sugihara February 2020, April 2020, May 2020, 12-18 October 2020 2. To draft and circulate a letter to municipalities inviting Office of the Government, Ministry of Quarter 1, 2020 them to hold events for the commemoration of the Culture, Association of Local year of the Vilna Gaon and of the history of the Jews Authorities in Lithuania, Lithuanian of Lithuania Jewish (Litvak) Community Chapter II CULTURAL, EDUCATIONAL AND INFORMATIONAL ACTIVITIES 3. To hold a series of events: ‘Litvaks and Literature: Ministry of Culture, Lithuanian Culture Quarter 1, 2020 Input of the Lithuanian Jews into the World Literature Institute, Lithuanian Jewish (Litvak) 20-23February 2020 Heritage’ at Vilnius Book Fair Community 4. To run a tolerance campaign #VieningaLietuva Ministry of Foreign Affairs, Department Quarter 3, 2019 - (unified Lithuania) of National Minorities under the Quarter 1, 2020 Government of the Republic of Lithuania, Secretariat of the International Commission for the Evaluation of the Crimes of the Nazi and Soviet Occupation Regimes in Lithuania, public establishment House of National Communities, Lithuanian Jewish (Litvak) Community 5. To hold an exhibition of works by Vilnius-born most Vilna Gaon State Jewish Museum, Quarter 4, 2019 - renowned twentieth-century Brasil’s modernist Lasar Ministry of Culture, Ministry of Foreign Quarter 1, 2020 Segall Affairs 28 November 2019 – 1 March 2020 THE YEAR OF THE VILNA GAON JEWISH HISTORY IN LITHUANIA 2020 PLAN FOR THE COMMEMORATION OF THE YEAR OF THE VILNA GAON AND OF THE HISTORY OF THE JEWS OF LITHUANIA / 1 QUARTER 1 Chapter II Action (project) Responsible implementer Implementation deadline 6. -

UCLA Electronic Theses and Dissertations
UCLA UCLA Electronic Theses and Dissertations Title Yiddish Songs of the Shoah: A Source Study Based on the Collections of Shmerke Kaczerginski Permalink https://escholarship.org/uc/item/6x72f9t5 Author Werb, Bret Publication Date 2014 Peer reviewed|Thesis/dissertation eScholarship.org Powered by the California Digital Library University of California UNIVERSITY OF CALIFORNIA Los Angeles Yiddish Songs of the Shoah A Source Study Based on the Collections of Shmerke Kaczerginski A dissertation submitted in partial satisfaction of the requirements for the degree Doctor of Philosophy in Ethnomusicology by Bret Charles Werb 2014 Copyright © Bret Charles Werb 2014 ABSTRACT OF THE DISSERTATION Yiddish Songs of the Shoah A Source Study Based on the Collections of Shmerke Kaczerginski by Bret Charles Werb Doctor of Philosophy in Ethnomusicology University of California, Los Angeles, 2014 Professor Timothy Rice, Chair This study examines the repertoire of Yiddish-language Shoah (or Holocaust) songs prepared for publication between the years 1945 and 1949, focusing its attention on the work of the most influential individual song collector, Shmerke Kaczerginski (1908-1954). Although a number of initiatives to preserve the “sung folklore” of the Nazi ghettos and camps were undertaken soon after the end of the Second World War, Kaczerginski’s magnum opus, the anthology Lider fun di getos un lagern (Songs of the Ghettos and Camps), published in New York in 1948, remains unsurpassed to this day as a resource for research in the field of Jewish folk and popular music of the Holocaust period. ii Chapter one of the dissertation recounts Kaczerginski’s life story, from his underprivileged childhood in Vilna, Imperial Russia (present-day Vilnius, Lithuania), to his tragic early death in Argentina. -

Handbuch Zur Judaica Provenienz Forschung: Zeremonialobjekte
Looted Art and Jewish Cultural Property Initiative Salo Baron und Mitglieder des Synagogue Council of America bei der Beerdigung von Torah Rollen beim Beth El Friedhof, Paramus, New Jersey, 13 Jänner 1952. Foto von Fred Stein, Sammlung der American Jewish Historical Society, New York, USA. HANDBUCH ZUR JUDAICA PROVENIENZ FORSCHUNG: ZEREMONIALOBJEKTE Von Julie-Marthe Cohen, Felicitas Heimann-Jelinek, und Ruth Jolanda Weinberger ins Deutsche übersetzt von: Felicitas Heimann-Jelinek Die deutsche Übersetzung kam dank der großzügigen Unterstützung der Beauftragten der Bundesregierung für Kultur und Medien zustande. ©Conference on Jewish Material Claims Against Germany, 2019 Inhalt Vorwort, Wesley A. Fisher Seite 4 Verzichtserklärung Seite 7 Einleitung Seite 8 TEIL 1 – Historische Übersicht 1.1. Judaica- und jüdische Museumssammlungen der Vorkriegszeit: Eine Übersicht Seite 12 1.2 Nazi-Organisationen und Raubkunst Seite 17 1.3 Die Plünderung von Judaica: Sammlungen von Museen, Gemeinden und Privatpersonen – Ein Überblick Seite 29 1.4 Die Zerstreuung jüdischer Zeremonialobjekte im Westen nach 1945: Jewish Cultural Reconstruction Seite 44 1.5 Die Zerstreuung jüdischer Zeremonialobjekte im Osten: Die Sowjetischen Trophäenbrigaden und Verstaatlichungen im Osten nach dem Zweiten Weltkrieg Seite 63 TEIL 2 – Judaica Objekte 2.1 Zur Definition von Judaica-Objekten Seite 79 2.2 Zur Identifikation von Judaica-Objekten Seite 80 2.2.1 Inschriften Seite 80 2.2.1.1 Personennamen Seite 80 2.2.1.2 Gemeinde- und Ortsnamen Seite 81 2.2.1.3 Datierungen Seite -

The Case of Interaction Problems Between Password Managers and Websites
They Would do Better if They Worked Together: The Case of Interaction Problems Between Password Managers and Websites Nicolas HuamanC ∗ Sabrina Amft∗ Marten OltroggeC Yasemin Acary ∗ Sascha FahlC ∗ CCISPA Helmholtz Center for Information Security ∗Leibniz University Hannover yMax Planck Institute for Security and Privacy Abstract—Password managers are tools to support users with previous research on PWMs mostly focuses on PWM security the secure generation and storage of credentials and logins issues and usability and adoption challenges. Multiple studies used in online accounts. Previous work illustrated that building researched the security of different PWM types, finding that password managers means facing various security and usability challenges. For strong security and good usability, the interaction both browser-based and locally installed PWMs are vulner- between password managers and websites needs to be smooth and able to problems such as key theft or secret recovery from effortless. However, user reviews for popular password managers temporary files, as well as weaknesses within typical features suggest interaction problems for some websites. Therefore, to the such as autofill [64]. Other research focused on the usability best of our knowledge, this work is the first to systematically iden- of PWMs and were able to show that user adoption of PWMs tify these interaction problems and investigate how 15 desktop password managers, including the ten most popular ones, are is motivated by convenience of usage and usability [59]. affected. We use a qualitative analysis approach to identify 39 While security benefits can also be a driving factor for PWM interaction problems from 2,947 user reviews and 372 GitHub adoption, in the majority of cases these where only mentioned issues for 30 password managers. -

Violins of Hope: Teacher's Guide
Teacher’s Guide sponsors: Dominion Energy WINDSOR Charitable Foundation FOUNDATION TABLE OF CONTENTS Overview of Music During the Holocaust 1 Politics & Propaganda 1 Resistance 3 Responses 5 Memory 7 Violins of Hope Amnon Weinstein 9 James Grymes 10 About Violins of Hope: Instruments of Hope 10 and Liberation in Mankind’s Darkest Hour Introduction to Violin Descriptions 11 The Feivel Wininger Violin 12 The Haftel Violin 13 The Auschwitz Violin 14 Violin from Lyon, France 15 You Can Make a Difference 18 The Holocaust: A Glossary 19 Holocaust History Timeline 22 Works Cited 30 Adapted from the Violins of Hope: Teacher’s Guide to Accompany Violins of Hope Program developed by Danielle Kahane-Kaminsky, Tennessee Holocaust Commission, December 2017. Overview of Music During the Holocaust During the Holocaust, music played many different roles. From the rise of Nazi power in Germany to the end of World War II, governments and individuals used music for a variety of reasons. Here are four prominent main themes of music during Nazi Germany and the Holocaust: • Politics and Propaganda • Resistance • Responses • Memory Source: http://holocaustmusic.ort.org/ Politics & Propaganda For the Nazis, music was not only a source of national pride, but also a tool for propaganda to influence German society. They felt music had a unique significance and power to seduce and sway the masses. Shortly after the Third Reich gained power in 1933, orchestras and conservatories were nationalized and funded by the state, and popular performers were recruited to serve as propaganda outlets for the Reich. The Nazi Party made widespread use of music in its publicity, and music featured prominently at rallies and other public events. -

Jewish Labor Bund's
THE STARS BEAR WITNESS: THE JEWISH LABOR BUND 1897-2017 112020 cubs בונד ∞≥± — A 120TH ANNIVERSARY CELEBRATION OF THE FOUNDING OF THE JEWISH LABOR BUND October 22, 2017 YIVO Institute for Jewish Research at the Center for Jewish History Sponsors YIVO Institute for Jewish Research, Jonathan Brent, Executive Director Workmen’s Circle, Ann Toback, Executive Director Media Sponsor Jewish Currents Executive Committee Irena Klepisz, Moishe Rosenfeld, Alex Weiser Ad Hoc Committee Rochelle Diogenes, Adi Diner, Francine Dunkel, Mimi Erlich Nelly Furman, Abe Goldwasser, Ettie Goldwasser, Deborah Grace Rosenstein Leo Greenbaum, Jack Jacobs, Rita Meed, Zalmen Mlotek Elliot Palevsky, Irene Kronhill Pletka, Fay Rosenfeld Gabriel Ross, Daniel Soyer, Vivian Kahan Weston Editors Irena Klepisz and Daniel Soyer Typography and Book Design Yankl Salant with invaluable sources and assistance from Cara Beckenstein, Hakan Blomqvist, Hinde Ena Burstin, Mimi Erlich, Gwen Fogel Nelly Furman, Bernard Flam, Jerry Glickson, Abe Goldwasser Ettie Goldwasser, Leo Greenbaum, Avi Hoffman, Jack Jacobs, Magdelana Micinski Ruth Mlotek, Freydi Mrocki, Eugene Orenstein, Eddy Portnoy, Moishe Rosenfeld George Rothe, Paula Sawicka, David Slucki, Alex Weiser, Vivian Kahan Weston Marvin Zuckerman, Michael Zylberman, Reyzl Zylberman and the following YIVO publications: The Story of the Jewish Labor Bund 1897-1997: A Centennial Exhibition Here and Now: The Vision of the Jewish Labor Bund in Interwar Poland Program Editor Finance Committee Nelly Furman Adi Diner and Abe Goldwasser -
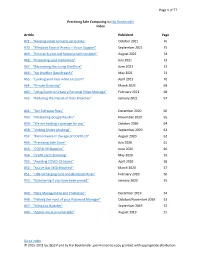
Practicing Safe Computing by Hal Bookbinder Index
Page 1 of 77 Practicing Safe Computing by Hal Bookbinder Index Article Published Page #71: “Keeping email contacts up to date” October 2021 76 #70: “Windows Ease of Access – Vision Support” September 2021 75 #69: “Even an 8-year-old Yahoo breach can bite!” August 2021 74 #68: “Protecting your credentials” July 2021 73 #67: ”Recovering files using OneDrive” June 2021 72 #66: “Yet Another Data Breach!” May 2021 71 #65: “Looking your best while on Zoom” April 2021 70 #64: “Private Browsing” March 2021 69 #63: “Using Zoom to Create a Personal Video Message” February 2021 68 #62: “Reducing the Impact of Data Breaches” January 2021 67 #61: “Ten Software Fixes” December 2020 66 #60: “Misleading Google Results” November 2020 65 #59: “We are holding a package for you” October 2020 64 #58: “Vishing (Voice phishing)” September 2020 63 #57: “Ransomware in the age of COVID-19” August 2020 62 #56: “Practicing Safe Zoom” July 2020 61 #55: “COVID-19 Statistics” June 2020 60 #54: “Credit card skimming” May 2020 59 #53: “Avoiding COVID-19 Scams” April 2020 58 #52: “You've Got DNA Matches!” March 2020 57 #51: “USB recharging cord and Bluetooth Risks” February 2020 56 #50: “Discovering if you have been pwned” January 2020 55 #49: “Data Management and Protection” December 2019 54 #48: “Making the most of your Password Manager” October/November 2019 53 #47: “Windows Updates” September 2019 52 #46: “Apples are also vulnerable” August 2019 51 Go to Index © 2015-2021 by JGSCV and by Hal Bookbinder, permission to copy granted with appropriate attribution. -

Options Pour La Gestion Des Mots De Passe
PROTÉGER SES COMPTES EN LIGNE: QUELLES SONT MES OPTIONS ? MARS 2021 PRÉPARÉ PAR: DENIS BERGERON 1 Introduction ⬛ Protéger nos comptes en ligne avec des mots de passe robustes et propres à chacun peut se faire de différentes façons. ⬛ Sujets traités dans cette présentation: ⬛ Évaluer nos besoins ⬛ Revue des options disponibles pour gérer ses mots de passe. ⬛ Un outil complémentaire efficace: l’authentification à double facteur 2 Protéger ses comptes en ligne Partie 1 Survol des options disponibles Revue des besoins vs options disponibles Gestionnaires de mots de passe en ligne 3 Protéger ses comptes en ligne Partie 2 Gestionnaires avec données dans notre appareil: Myki et KeePass Gérer ses mots de passe avec son fureteur Fichier « maison » crypté L’authentification à double facteur (2FA) 4 Survol des options disponibles ⬛ Plusieurs façons de gérer nos mots de passe. 1.Gestionnaires de mots de passe en ligne ⬛ Quelques exemples de gestionnaires payants: Dashlane 1Password Keeper LastPass NordPass RoboForm 5 Survol des options disponibles 1.Gestionnaires de mots de passe en ligne (suite) ⬛ Quelques exemples de gestionnaires offrant une version gratuite: Dashlane (1 appareil, 50 mots de passe max.) Keeper (1 appareil) LastPass (1 type d’appareil) RoboForm (1 appareil) NordPass (1 appareil à la fois) etc. ⬛ Exemple de gestionnaire offrant une solution open source: Bitwarden 6 Survol des options disponibles 2.Quelques fureteurs web pour gérer ses mots de passe Firefox Chrome Edge Safari 3.Gestionnaires sauvegardant nos mots de passe à l’intérieur même de notre appareil Myki KeePass (application open source) 4.Fichier maison crypté et sauvegardé localement ou dans notre espace cloud 7 Besoins vs options disponibles ⬛ Pour nous aider à choisir: Analyser nos besoins ou attentes par rapport aux possibilités de chaque option.