Virtual Machine Technologies and Their Application in the Delivery of ICT
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

OLD PRETENDER Lovrenc Gasparin, Fotolia
COVER STORY Bochs Emulator Legacy emulator OLD PRETENDER Lovrenc Gasparin, Fotolia Gasparin, Lovrenc Bochs, the granddaddy of all emulators, is alive and kicking; thanks to regular vitamin jabs, the lively old pretender can even handle Windows XP. BY TIM SCHÜRMANN he PC emulator Bochs first saw the 2.2.6 version in the Universe reposi- box). This also applies if you want to the light of day in 1994. Bochs’ tory; you will additionally need to install run Bochs on a pre-Pentium CPU, such Tinventor, Kevin Lawton, distrib- the Bximage program. (Bximage is al- as a 486. uted the emulator under a commercial li- ready part of the Bochs RPM for open- After installation, the program will cense before selling to French Linux ven- SUSE.) If worst comes to worst, you can simulate a complete PC, including CPU, dor Mandriva (which was then known always build your own Bochs from the graphics, sound card, and network inter- as MandrakeSoft). Mandriva freed the source code (see the “Building Bochs” face. The virtual PC in a PC works so emulator from its commercial chains, re- leasing Bochs under the LGPL license. Building Bochs If you prefer to build your own Bochs, or an additional --enable-ne2000 parameter Installation if you have no alternative, you will first to configure. The extremely long list of Bochs has now found a new home at need to install the C++ compiler and de- parameters in the user manual [2] gives SourceForge.net [1] (Figure 1). You can veloper packages for the X11 system. you a list of available options. -

CASE STUDY Userful Multiplier and Win4lin Pro Reduce Costs of Point
CASE STUDY TM Userful Multiplier and Win4Lin Pro Reduce Costs of Point-of-Sale Terminals A Case Study by Omni Technology Solutions, leverage the Linux Desktop, he recommended the Userful a Userful Partner Multiplier*, a software add-on that allows multiple users to share a single computer. Win4Lin Pro Desktop was installed to allow Birchwood to run Simply Accounting on Linux. “Userful Multiplier* cut the hardware DOSEMU, which comes bundled with SUSE Linux, handled costs in half and Win4Lin Pro Desktop the DOS-based Framer’s Assistant point-of-sale application provided Windows compatibility to run quite nicely. their Simply Accounting package.” “Birchwood Art Gallery was always running into virus and - Mike Ducharme, spyware infections when they were using Windows 98 and IT consultant, Windows XP. Even with up-to-date anti-virus and anti- Birchwood Art Gallery spyware software, the systems were still getting major infections on a monthly basis, resulting in costly down-time Overview until they were cleaned up,” said Mr. Ducharme. “The security of Novell’s SUSE Linux Desktop provides peace of mind to Birchwood Art Gallery - based in Winnipeg, Canada - their staff,” continued Ducharme, “allowing them to carry out specializes in fine art reproductions and original artwork their work activities without fear of virus or spyware infesta- by a wide range of Canadian and international artists. On tion. Additionally, the Userful Multiplier* cut the hardware their web site and in their gallery, you will find artwork, costs in half and Win4Lin Pro Desktop provided Windows sculptures, prints and books from hundreds of artists. Lyn compatibility to run their Simply Accounting package.” Chercoe and Carole Solmundson, Birchwood Art Gallery’s owners, have earned a reputation for customer service The Results excellence since 1993 and sell art online all over the world. -

Introduction to Virtualization Virtualization
Introduction to Virtualization Prashant Shenoy Computer Science CS691D: Hot-OS Lecture 2, page 1 Virtualization • Virtualization: extend or replace an existing interface to mimic the behavior of another system. – Introduced in 1970s: run legacy software on newer mainframe hardware • Handle platform diversity by running apps in VMs – Portability and flexibility Computer Science CS691D: Hot-OS Lecture 2, page 2 Types of Interfaces • Different types of interfaces – Assembly instructions – System calls – APIs • Depending on what is replaced /mimiced, we obtain different forms of virtualization Computer Science CS691D: Hot-OS Lecture 2, page 3 Types of Virtualization • Emulation – VM emulates/simulates complete hardware – Unmodified guest OS for a different PC can be run • Bochs, VirtualPC for Mac, QEMU • Full/native Virtualization – VM simulates “enough” hardware to allow an unmodified guest OS to be run in isolation • Same hardware CPU – IBM VM family, VMWare Workstation, Parallels,… Computer Science CS691D: Hot-OS Lecture 2, page 4 Types of virtualization • Para-virtualization – VM does not simulate hardware – Use special API that a modified guest OS must use – Hypercalls trapped by the Hypervisor and serviced – Xen, VMWare ESX Server • OS-level virtualization – OS allows multiple secure virtual servers to be run – Guest OS is the same as the host OS, but appears isolated • apps see an isolated OS – Solaris Containers, BSD Jails, Linux Vserver • Application level virtualization – Application is gives its own copy of components that are not shared • (E.g., own registry files, global objects) - VE prevents conflicts – JVM Computer Science CS691D: Hot-OS Lecture 2, page 5 Examples • Application-level virtualization: “process virtual machine” • VMM /hypervisor Computer Science CS691D: Hot-OS Lecture 2, page 6 The Architecture of Virtual Machines J Smith and R. -

Virtual Alpha User Guide for Avanti, Avantiflex, & Freeaxp 05-JAN-2018 Version 3.0: This Manual Covers All Releases of Avanti™, Avantiflex™ and Freeaxp™
Migration Specialties International, Inc. 217 West 2nd Street, Florence, CO 81226-1403 +1 719-784-9196 E-mail: [email protected] www.MigrationSpecialties.com Continuity in Computing Virtual Alpha User Guide for Avanti, AvantiFlex, & FreeAXP 05-JAN-2018 Version 3.0: This manual covers all releases of Avanti™, AvantiFlex™ and FreeAXP™. This manual describes how to install and use Avanti, AvantiFlex, and FreeAXP, Migration Specialties' AlphaServer 400 hardware emulators. AvantiFlex and Avanti are commercial products that require purchase of a product license. AvantiFlex and Avanti include 30 days of manufacturer support after purchase and the option to buy an extended support contract. FreeAXP can be used for personal and commercial purposes. FreeAXP is unsupported without purchase of a support contract. If you have questions or problems with FreeAXP and have not purchased a support contract, visit the FreeAXP forum at the OpenVMS Hobbyist web site. Avanti & Avanti Flex Links Product Info: http://www.migrationspecialties.com/Emulator-Alpha.html User Guide: http://www.migrationspecialties.com/pdf/VirtualAlpha_UserGuide.pdf Release Notes: http://www.migrationspecialties.com/pdf/VirtualAlpha_ReleaseNotes.pdf License: http://www.migrationspecialties.com/pdf/AvantiLicense.pdf SPD: http://www.migrationspecialties.com/pdf/Avanti_SPD.pdf Pricing Guide: http://www.migrationspecialties.com/pdf/VirtualAlphaPricingGuide.pdf FreeAXP Links Product Info: http://www.migrationspecialties.com/FreeAXP.html User Guide: http://www.migrationspecialties.com/pdf/VirtualAlpha_UserGuide.pdf Release Notes: http://www.migrationspecialties.com/pdf/VirtualAlpha_ReleaseNotes.pdf License: http://www.migrationspecialties.com/pdf/FreeAXP_License.pdf SPD: http://www.migrationspecialties.com/pdf/FreeAXP_SPD.pdf User Forum: http://www.vmshobbyist.com/forum/viewforum.php?forum_id=163 Download: http://www.migrationspecialties.com/FreeAXP.html Copyright 2018, Migration Specialties. -

Virtualizing Servers with Xen
Virtualization Xen Features Escalabilidade Performance QoS Implementation Future Virtualizing servers with Xen Evaldo Gardenali VI International Conference of Unix at UNINET Virtualization Xen Features Escalabilidade Performance QoS Implementation Future Outline Virtualization Xen Features Scalability Performance Quality of Service Implementation Future of Xen Virtualization Xen Features Escalabilidade Performance QoS Implementation Future Overview Why? Support heterogeneous environments: Linux r 2.4 e 2.6, NetBSD r , Plan9 r FreeBSD r , OpenSolaris r Consolidate work Legacy Systems Gradual Upgrade Service Isolation Quality of Service Isolated testing and development Ease of administration Ease of relocation and migration Virtualization Xen Features Escalabilidade Performance QoS Implementation Future Virtualization Techniques Single System Image: Ensim r , Vservers, CKRM, VirtuozzoTM, BSD r jail(), Solaris r Zones √ Groups processes in “resource containers” Hard to get isolation × Emulation: QEMU, Bochs √ Portable Extremely slow × Virtualization: VMware r , VirtualPC r √ Runs unmodified Operating Systems Virtualizing x86 is inefficient × User Mode Kernel: User Mode Linux, CoLinux Guest runs as a process on the host OS × Low performance (I/O, context switches) × Paravirtualization: Xen r , Denali √ Excellent performance Requires port to special architecture × Virtualization Xen Features Escalabilidade Performance QoS Implementation Future Virtualization Techniques Single System Image: Ensim r , Vservers, CKRM, VirtuozzoTM, BSD r jail(), Solaris -

Virtualization of Linux Based Computers: the Linux-Vserver Project
VirtualizationVirtualization ofof LinuxLinux basedbased computers:computers: thethe LinuxLinux--VServerVServer projectproject BenoBenoîîtt desdes Ligneris,Ligneris, Ph.Ph. D.D. [email protected] Objectives:Objectives: Objectives:Objectives: 1)1) PresentPresent thethe availableavailable programsprograms thatthat cancan provideprovide aa virtualizationvirtualization ofof LinuxLinux computerscomputers withwith differentdifferent technologies.technologies. Objectives:Objectives: 1)1) PresentPresent thethe availableavailable programsprograms thatthat cancan provideprovide aa virtualizationvirtualization ofof LinuxLinux computerscomputers withwith differentdifferent technologies.technologies. 2)2) FocusFocus onon LinuxLinux--VServers:VServers: aa veryvery lightweightlightweight andand effectiveeffective technologytechnology forfor thethe regularregular LinuxLinux useruser notnot interstedintersted inin KernelKernel hacking.hacking. PlanPlan PlanPlan ● IntroductionIntroduction PlanPlan ● IntroductionIntroduction ● OverviewOverview ofof thethe availableavailable technologytechnology PlanPlan ● IntroductionIntroduction ● OverviewOverview ofof thethe availableavailable technologytechnology ● ClassificationClassification ofof thethe problems:problems: usageusage criteriacriteria PlanPlan ● IntroductionIntroduction ● OverviewOverview ofof thethe availableavailable technologytechnology ● ClassificationClassification ofof thethe problems:problems: usageusage criteriacriteria ● ComparativeComparative studystudy ofof thethe existingexisting -

Linux Games Page 1 of 7
Linux Games Page 1 of 7 Linux Games INTRODUCTION such as the number of players and the size of the map, then you start the game. Once the game is running clients may Hello. My name is Andrew Howlett. I've been using Linux join the game. Clients connect to the game using TCP/IP, since 1997. In 2000 I cutover to Linux for all my projects, so it is very easy to play multi-player games over the except I dual-booted Windows to play games. I like to play Internet. Like many Free games, clients are available for computer games. About a year ago I stopped dual booting. many platforms, including Windows, Amiga and Now I play computer games under Linux. The games I Macintosh. So there are lots of players out there. If you play can be divided into four groups: Free Games, native don't want to play against other humans, then Freeciv linux commercial games, Windows Emulated games, and includes some nasty AIs. Win4Lin enabled games. This presentation will demonstrate games from each of these four groups. BZFlag Platform BZFlag is a tank combat game along the same lines as the old BattleZone game. Like FreeCiv, BZFlag uses a client/ Before I get started, a little bit about my setup so you can server architecture over TCP/IP networks. Unlike FreeCiv, relate this to whatever you are running. This is a P3 900 the game contains no AIs – you must play this game MHz machine. It has a Crystal Sound 4600 sound card and against other humans (? entities ?) over the Internet. -
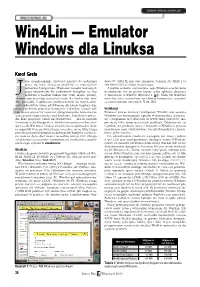
Win4lin — Emulator Windows Dla Linuksa
Win4Lin — Emulator Windows dla Linuksa Karol Grela ako chemik−organik, używający Linuksa do codziennej dows 95 OSR2 PL mój stary komputer Pentium 233 MMX z 64 pracy, nie mam zazwyczaj problemu ze znalezieniem MB RAM−u był aż nadto wystarczający. potrzebnych programów. Większość narzędzi tworzonych Z punktu widzenia użytkownika, sesja Windows uruchomiona przez naukowców dla naukowców kompiluje się bez w emulatorze jest po prostu jeszcze jedną aplikacją działającą problemu w każdym Uniksie (np. VMD, mopac, platon), w środowisku X Window (Rysunek 1, [8a]). Okno MS Windows a komercyjne posiadają zazwyczaj wersje dla Linuksa (np. mol− może być także wyświetlone na zdalnym komputerze, za pomo− den, pcmodel). Z aplikacjami przeznaczonymi dla innych syste− cą mechanizmów sieciowych X−ów [8b]. mów uniksowych, takimi jak XWinnmr dla Silicon Graphics, daje się bez problemu pracować w systemie X Window. Czasem jed− Instalacja nak muszę używać lub testować oprogramowanie, które nie po− Ponieważ proces instalacji i konfiguracji Win4Lin oraz systemu siada jeszcze odpowiednika pod Linuksem. Dodatkowo prowa− Windows jest wyczerpująco opisany w dokumentacji dostarcza− dzę kilka projektów, takich jak ChemPerfect — zestaw narzędzi nej z programem oraz dostępnej na WWW firmy TreLOS [5], sku− chemicznych do Wordperfecta. Projekt ten rozwijam w dwu wer− pię się na kilku mniej oczywistych punktach. Zakładam też, że sjach — dla Windows i Linuksa. Czasem muszę wprowadzić drob− Czytelnik zna podstawy pracy z Linuksem (i Windows), posiada ne poprawki w tej pierwszej wersji, a nie chce mi się tylko z tego uprawnienia roota i (ewentualnie) wie jak skompilować i zainsta− powodu restartować komputera i ładować MS Windows. Co więcej, lować jądro systemu. -

Parallels Desktop® Upgrade to Windows 7 User's Guide
Parallels Desktop® Upgrade to Windows 7 User's Guide Copyright © 1999-2010 Parallels Holdings, Ltd. and its affiliates. All rights reserved. Parallels Holdings, Ltd. c/o Parallels International GMbH. Parallels International GmbH Vordergasse 49 CH8200 Schaffhausen Switzerland Tel: + 49 (6151) 42996 - 0 Fax: + 49 (6151) 42996 - 255 www.parallels.com Copyright © 1999-2010 Parallels Holdings, Ltd. and its affiliates. All rights reserved. This product is protected by United States and international copyright laws. The product’s underlying technology, patents, and trademarks are listed at http://www.parallels.com/trademarks. Microsoft, Windows, Windows Server, Windows NT, Windows Vista, and MS-DOS are registered trademarks of Microsoft Corporation. Linux is a registered trademark of Linus Torvalds. Mac is a registered trademark of Apple, Inc. All other marks and names mentioned herein may be trademarks of their respective owners. 3 Contents Introduction 5 About Parallels Desktop Upgrade to Windows 7......................................................................................... 5 About This Guide......................................................................................................................................... 6 Organization of This Guide .............................................................................................................. 6 Documentation Conventions............................................................................................................. 7 Getting Help................................................................................................................................................ -

Virtualization Technologies Overview Course: CS 490 by Mendel
Virtualization technologies overview Course: CS 490 by Mendel Rosenblum Name Can boot USB GUI Live 3D Snaps Live an OS on mem acceleration hot of migration another ory runnin disk alloc g partition ation system as guest Bochs partially partially Yes No Container s Cooperati Yes[1] Yes No No ve Linux (supporte d through X11 over networkin g) Denali DOSBox Partial (the Yes No No host OS can provide DOSBox services with USB devices) DOSEMU No No No FreeVPS GXemul No No Hercules Hyper-V iCore Yes Yes No Yes No Virtual Accounts Imperas Yes Yes Yes Yes OVP (Eclipse) Tools Integrity Yes No Yes Yes No Yes (HP-UX Virtual (Integrity guests only, Machines Virtual Linux and Machine Windows 2K3 Manager in near future) (add-on) Jail No Yes partially Yes No No No KVM Yes [3] Yes Yes [4] Yes Supported Yes [5] with VMGL [6] Linux- VServer LynxSec ure Mac-on- Yes Yes No No Linux Mac-on- No No Mac OpenVZ Yes Yes Yes Yes No Yes (using Xvnc and/or XDMCP) Oracle Yes Yes Yes Yes Yes VM (manage d by Oracle VM Manager) OVPsim Yes Yes Yes Yes (Eclipse) Padded Yes Yes Yes Cell for x86 (Green Hills Software) Padded Yes Yes Yes No Cell for PowerPC (Green Hills Software) Parallels Yes, if Boot Yes Yes Yes DirectX 9 Desktop Camp is and for Mac installed OpenGL 2.0 Parallels No Yes Yes No partially Workstati on PearPC POWER Yes Yes No Yes No Yes (on Hypervis POWER 6- or (PHYP) based systems, requires PowerVM Enterprise Licensing) QEMU Yes Yes Yes [4] Some code Yes done [7]; Also supported with VMGL [6] QEMU w/ Yes Yes Yes Some code Yes kqemu done [7]; Also module supported -

Crossover Compared to Competing Emulation Solutions
CrossOver Compared to Competing Emulation Solutions CrossOver Compared to Competing Emulation Solutions CrossOver Compared to Competing Emulation Solutions Overview: Whether you’re running a Linux or Mac OS X machine, chances are you need a way to run at least some Windows applications or games that aren’t available on your platform of choice. And you have your choice of potential solutions to this problem. This page illustrates some of the key Every Windows advantages that CrossOver has in relation to the compatibility solution has other compatibility solutions. pros and cons. When presented with the need to run Windows applications on a Mac or Linux machine, you have basically three main choices: Dual-booting: running two separate operating systems on one PC, and switching between them as needed by rebooting. Applications such as Apple’s Bootcamp allow this to occur on a Mac OS X machine, for example. Running a virtual machine: Emulation products such as VMWare and Parallels allow you to install a copy of Windows within a logical partition within your native operating system. The Windows applications essentially run in a separate “box within a box.” Running Wine or CrossOver: Unlike emulation, Wine is a re-implementation of the Win32 API, allowing applications to run as if natively on the target OS. CrossOver is a commercialized version of Wine. Each solution has its advantages and disadvantages. This document is provided to help identify and evaluate key points of comparison between CodeWeavers’ CrossOver products and some of its key competitors. Technology Approach General Approach Dual-booting is exactly what it sounds like—shutting down one operating system, starting another, and dealing with the file transfer issues associated with same. -

An Empirical Study Into the Security Exposure to Hosts of Hostile Virtualized Environments
An Empirical Study into the Security Exposure to Hosts of Hostile Virtualized Environments Tavis Ormandy [email protected] Google, Inc. Abstract machine monitor is ‘root secure’[25], meaning that no level of As virtual machines become increasingly commonplace as privilege within the virtualized guest environment permits a method of separating hostile or hazardous code from com- interference with the host system. modity systems, the potential security exposure from imple- Detection mentation flaws has increased dramatically. This paper Detecting virtualized environments has been explored in investigates the state of popular virtual machine implementa- detail by other researchers[22]. Virtual machines employed in tions for x86 systems, employing a combination of source code malware analysis or honeypots should endeavour to be unde- auditing and blackbox random testing to assess the security tectable or risk changing the behaviour of the emulated code. exposure to the hosts of hostile virtualized environments. An emulated malware sample could choose to act benignly, Keywords for example, but when executed on a physical machine imme- virtualization, security, software testing diately performs some malicious action. Detection will not be considered any further in this paper, although being able to detect a virtual machine, or more spe- I. INTRODUCTION cifically, virtual machine implementation, may be a prerequi- Secure isolation is one of the fundamental concepts of vir- site for the more serious attacks investigated in this paper. tualization[15], confining a program to a virtualized environ- Without being able to identify which virtual machine imple- ment should guarantee that any action performed inside the mentation is present, an attacker would have difficulty deter- virtual machine cannot interfere with the system that hosts it1.