Crossover Compared to Competing Emulation Solutions
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ubuntu Kung Fu
Prepared exclusively for Alison Tyler Download at Boykma.Com What readers are saying about Ubuntu Kung Fu Ubuntu Kung Fu is excellent. The tips are fun and the hope of discov- ering hidden gems makes it a worthwhile task. John Southern Former editor of Linux Magazine I enjoyed Ubuntu Kung Fu and learned some new things. I would rec- ommend this book—nice tips and a lot of fun to be had. Carthik Sharma Creator of the Ubuntu Blog (http://ubuntu.wordpress.com) Wow! There are some great tips here! I have used Ubuntu since April 2005, starting with version 5.04. I found much in this book to inspire me and to teach me, and it answered lingering questions I didn’t know I had. The book is a good resource that I will gladly recommend to both newcomers and veteran users. Matthew Helmke Administrator, Ubuntu Forums Ubuntu Kung Fu is a fantastic compendium of useful, uncommon Ubuntu knowledge. Eric Hewitt Consultant, LiveLogic, LLC Prepared exclusively for Alison Tyler Download at Boykma.Com Ubuntu Kung Fu Tips, Tricks, Hints, and Hacks Keir Thomas The Pragmatic Bookshelf Raleigh, North Carolina Dallas, Texas Prepared exclusively for Alison Tyler Download at Boykma.Com Many of the designations used by manufacturers and sellers to distinguish their prod- ucts are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. The Pragmatic Starter Kit, The Pragmatic Programmer, Pragmatic Programming, Pragmatic Bookshelf and the linking g device are trademarks of The Pragmatic Programmers, LLC. -

Virtual Machine Technologies and Their Application in the Delivery of ICT
Virtual Machine Technologies and Their Application In The Delivery Of ICT William McEwan accq.ac.nz n Christchurch Polytechnic Institute of Technology Christchurch, New Zealand [email protected] ABSTRACT related areas - a virtual machine or network of virtual machines can be specially configured, allowing an Virtual Machine (VM) technology was first ordinary user supervisor rights, and it can be tested implemented and developed by IBM to destruction without any adverse effect on the corporation in the early 1960's as a underlying host system. mechanism for providing multi-user facilities This paper hopes to also illustrate how VM in a secure mainframe computing configurations can greatly reduce our dependency on environment. In recent years the power of special purpose, complex, and expensive laboratory personal computers has resulted in renewed setups. It also suggests the important additional role interest in the technology. This paper begins that VM and VNL is likely to play in offering hands-on by describing the development of VM. It practical experience to students in a distance e- discusses the different approaches by which learning environment. a VM can be implemented, and it briefly considers the advantages and disadvantages Keywords: Virtual Machines, operating systems, of each approach. VM technology has proven networks, e-learning, infrastructure, server hosting. to be extremely useful in facilitating the Annual NACCQ, Hamilton New Zealand July, 2002 www. Annual NACCQ, Hamilton New Zealand July, teaching of multiple operating systems. It th offers an alternative to the traditional 1. INTRODUCTION approaches of using complex combinations Virtual Machine (VM) technology is not new. It was of specially prepared and configured OS implemented on mainframe computing systems by the images installed via the network or installed IBM Corporation in the early 1960’s (Varian 1997 pp permanently on multiple partitions or on 3-25, Gribben 1989 p.2, Thornton 2000 p.3, Sugarman multiple physical hard drives. -

Linux on the Road
Linux on the Road Linux with Laptops, Notebooks, PDAs, Mobile Phones and Other Portable Devices Werner Heuser <wehe[AT]tuxmobil.org> Linux Mobile Edition Edition Version 3.22 TuxMobil Berlin Copyright © 2000-2011 Werner Heuser 2011-12-12 Revision History Revision 3.22 2011-12-12 Revised by: wh The address of the opensuse-mobile mailing list has been added, a section power management for graphics cards has been added, a short description of Intel's LinuxPowerTop project has been added, all references to Suspend2 have been changed to TuxOnIce, links to OpenSync and Funambol syncronization packages have been added, some notes about SSDs have been added, many URLs have been checked and some minor improvements have been made. Revision 3.21 2005-11-14 Revised by: wh Some more typos have been fixed. Revision 3.20 2005-11-14 Revised by: wh Some typos have been fixed. Revision 3.19 2005-11-14 Revised by: wh A link to keytouch has been added, minor changes have been made. Revision 3.18 2005-10-10 Revised by: wh Some URLs have been updated, spelling has been corrected, minor changes have been made. Revision 3.17.1 2005-09-28 Revised by: sh A technical and a language review have been performed by Sebastian Henschel. Numerous bugs have been fixed and many URLs have been updated. Revision 3.17 2005-08-28 Revised by: wh Some more tools added to external monitor/projector section, link to Zaurus Development with Damn Small Linux added to cross-compile section, some additions about acoustic management for hard disks added, references to X.org added to X11 sections, link to laptop-mode-tools added, some URLs updated, spelling cleaned, minor changes. -

CASE STUDY Userful Multiplier and Win4lin Pro Reduce Costs of Point
CASE STUDY TM Userful Multiplier and Win4Lin Pro Reduce Costs of Point-of-Sale Terminals A Case Study by Omni Technology Solutions, leverage the Linux Desktop, he recommended the Userful a Userful Partner Multiplier*, a software add-on that allows multiple users to share a single computer. Win4Lin Pro Desktop was installed to allow Birchwood to run Simply Accounting on Linux. “Userful Multiplier* cut the hardware DOSEMU, which comes bundled with SUSE Linux, handled costs in half and Win4Lin Pro Desktop the DOS-based Framer’s Assistant point-of-sale application provided Windows compatibility to run quite nicely. their Simply Accounting package.” “Birchwood Art Gallery was always running into virus and - Mike Ducharme, spyware infections when they were using Windows 98 and IT consultant, Windows XP. Even with up-to-date anti-virus and anti- Birchwood Art Gallery spyware software, the systems were still getting major infections on a monthly basis, resulting in costly down-time Overview until they were cleaned up,” said Mr. Ducharme. “The security of Novell’s SUSE Linux Desktop provides peace of mind to Birchwood Art Gallery - based in Winnipeg, Canada - their staff,” continued Ducharme, “allowing them to carry out specializes in fine art reproductions and original artwork their work activities without fear of virus or spyware infesta- by a wide range of Canadian and international artists. On tion. Additionally, the Userful Multiplier* cut the hardware their web site and in their gallery, you will find artwork, costs in half and Win4Lin Pro Desktop provided Windows sculptures, prints and books from hundreds of artists. Lyn compatibility to run their Simply Accounting package.” Chercoe and Carole Solmundson, Birchwood Art Gallery’s owners, have earned a reputation for customer service The Results excellence since 1993 and sell art online all over the world. -

Technical White Paper: Running Applications Under
Technical White Paper: Running Applications Under CrossOver: An Analysis of Security Risks Running Applications Under CrossOver: An Analysis of Security Risks Wine, Viruses, and Methods of Achieving Security Overview: Wine is a Windows compatibility technology that allows a wide variety of Windows Running Windows software to run as-if-natively on Unix-based software via CrossOver operating systems like Linux and Mac OS X. From a theoretical standpoint, Wine should is, on average, much safer also enable malware and viruses to run, thereby than running them under (unfortunately) exposing Wine users to these same Windows hazards. However, CrossOver (based on Wine) also incorporates security features that bring this risk down to almost zero. This White Paper examines the reasons behind the enhanced safety that CrossOver provides. With the increasing popularity of running Windows software on Linux and Mac OS X via compatibility solutions such as Wine, VMWare, and Parallels, users have been able to enjoy a degree of computing freedom heretofore unseen. Yet with that freedom has come peril. As many VMWare and Parallels users have discovered, running applications like Outlook and IE under those PC emulation solutions also opens up their machine to the same viruses and malware they faced under Windows. Indeed, one of the first things any VMWare or Parallels customer should do upon is install a commercial anti-virus package. Failure to do so can result in a host of dire consequences for their Windows partition, just as it would if they were running a Windows PC. Not surprisingly, a question we sometimes hear is whether or not Wine exposes users to the same level of risk. -

Bringing Windows to the Linux Desktop
BRINGING WINDOWS TO THE LINUX DESKTOP In a perfect world, the operating system that you use wouldn't matter. We're moving towards that with the growing use and availability of Web applications. But the day when the operating system is irrelevant is still awhile off. Right now, though, Windows is the dominant operating system. And there are no Linux versions of the popular and most widely-used applications for Windows -- programs like Microsoft Office and Adobe Photoshop. If you're a Linux user and you need to play nicely with the Windows world, conventional wisdom dictates that you either need a separate desktop computer or laptop computer that's running Windows or a system that dual boots. If you're adventurous, you can install a virtualization tool like VM Ware or Virtual Box. This software recreates Windows on your Linux box. The only problem with those solutions is that they need a lot of hard drive space and CPU. There is another choice: fake it. Faking it What do I mean by faking it? Using software that fools Windows applications into believing that they're actually running on Windows and not on Linux. It does this by creating what's called anapplication layer between the Windows program and Linux. The application layer simulates the Windows environment -- calls to the operating system, DLLs, drivers, and the like. Unlike the other solutions mentioned earlier, using an application layer only adds a bit of extra load to your computer -- a few megabytes of disk space and a couple of megabytes of RAM. -

Windows Legacy Application Support Under Wine
White Paper: Windows Legacy Application Support Under Wine Windows Legacy Application Support Under Wine Windows Legacy Application Support Under Wine Overview: With the constant pressure from Microsoft to migrate to newer versions of Windows, many users are left with unpalatable options for running their older applications. Wine Wine offers a viable offers a viable, inexpensive alternative for keeping alternative for keeping these legacy applications functioning in perpetuity. legacy Windows apps It is a truism that the needs of customers and vendors are often at running in perpetuity. cross-purposes. Nowhere has this been more vividly demonstrated than in the forced upgrade cycles of the Microsoft Windows platform, which have completely reversed the leverage customers normally wield over their suppliers. In many cases, end-users have seen little utility in switching to newer versions of Windows, but have been left with essentially zero choice in the matter. Forced OS upgrades have, in turn, forced the migration of many legacy applications. These older Windows programs—which in many cases are still perfectly functional—must either be redeveloped for a newer Windows platform, or replaced. This places yet another cost on top of the cost of the OS upgrade. However, this cycle, which once appeared unbreakable, now seems to be weakening. For one thing, Windows is no longer as dominant as it once was on the desktop. The rise of both Mac OS X and Linux have begun eating into the monopolistic power of Microsoft to dictate these cycles. Second is the fact that users now have a realistic alternative The MS OS forced- for running their legacy apps. -

Linux Networking Cookbook.Pdf
Linux Networking Cookbook ™ Carla Schroder Beijing • Cambridge • Farnham • Köln • Paris • Sebastopol • Taipei • Tokyo Linux Networking Cookbook™ by Carla Schroder Copyright © 2008 O’Reilly Media, Inc. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (safari.oreilly.com). For more information, contact our corporate/institutional sales department: (800) 998-9938 or [email protected]. Editor: Mike Loukides Indexer: John Bickelhaupt Production Editor: Sumita Mukherji Cover Designer: Karen Montgomery Copyeditor: Derek Di Matteo Interior Designer: David Futato Proofreader: Sumita Mukherji Illustrator: Jessamyn Read Printing History: November 2007: First Edition. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. The Cookbook series designations, Linux Networking Cookbook, the image of a female blacksmith, and related trade dress are trademarks of O’Reilly Media, Inc. Java™ is a trademark of Sun Microsystems, Inc. .NET is a registered trademark of Microsoft Corporation. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. -

Linux Games Page 1 of 7
Linux Games Page 1 of 7 Linux Games INTRODUCTION such as the number of players and the size of the map, then you start the game. Once the game is running clients may Hello. My name is Andrew Howlett. I've been using Linux join the game. Clients connect to the game using TCP/IP, since 1997. In 2000 I cutover to Linux for all my projects, so it is very easy to play multi-player games over the except I dual-booted Windows to play games. I like to play Internet. Like many Free games, clients are available for computer games. About a year ago I stopped dual booting. many platforms, including Windows, Amiga and Now I play computer games under Linux. The games I Macintosh. So there are lots of players out there. If you play can be divided into four groups: Free Games, native don't want to play against other humans, then Freeciv linux commercial games, Windows Emulated games, and includes some nasty AIs. Win4Lin enabled games. This presentation will demonstrate games from each of these four groups. BZFlag Platform BZFlag is a tank combat game along the same lines as the old BattleZone game. Like FreeCiv, BZFlag uses a client/ Before I get started, a little bit about my setup so you can server architecture over TCP/IP networks. Unlike FreeCiv, relate this to whatever you are running. This is a P3 900 the game contains no AIs – you must play this game MHz machine. It has a Crystal Sound 4600 sound card and against other humans (? entities ?) over the Internet. -

Cryptographic File Systems Performance: What You Don't Know Can Hurt You Charles P
Cryptographic File Systems Performance: What You Don't Know Can Hurt You Charles P. Wright, Jay Dave, and Erez Zadok Stony Brook University Appears in the proceedings of the 2003 IEEE Security In Storage Workshop (SISW 2003) Abstract interact with disks, caches, and a variety of other com- plex system components — all having a dramatic effect Securing data is more important than ever, yet cryp- on performance. tographic file systems still have not received wide use. In this paper we perform a real world performance One barrier to the adoption of cryptographic file systems comparison between several systems that are used is that the performance impact is assumed to be too high, to secure file systems on laptops, workstations, and but in fact is largely unknown. In this paper we first moderately-sized file servers. We also emphasize multi- survey available cryptographic file systems. Second, programming workloads, which are not often inves- we perform a performance comparison of a representa- tigated. Multi-programmed workloads are becoming tive set of the systems, emphasizing multiprogrammed more important even for single user machines, in which workloads. Third, we discuss interesting and counterin- Windowing systems are often used to run multiple appli- tuitive results. We show the overhead of cryptographic cations concurrently. We expect cryptographic file sys- file systems can be minimal for many real-world work- tems to become a commodity component of future oper- loads, and suggest potential improvements to existing ating systems. systems. We have observed not only general trends with We present results from a variety of benchmarks, an- each of the cryptographic file systems we compared but alyzing the behavior of file systems for metadata op- also anomalies based on complex interactions with the erations, raw I/O operations, and combined with CPU operating system, disks, CPUs, and ciphers. -
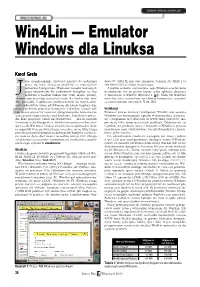
Win4lin — Emulator Windows Dla Linuksa
Win4Lin — Emulator Windows dla Linuksa Karol Grela ako chemik−organik, używający Linuksa do codziennej dows 95 OSR2 PL mój stary komputer Pentium 233 MMX z 64 pracy, nie mam zazwyczaj problemu ze znalezieniem MB RAM−u był aż nadto wystarczający. potrzebnych programów. Większość narzędzi tworzonych Z punktu widzenia użytkownika, sesja Windows uruchomiona przez naukowców dla naukowców kompiluje się bez w emulatorze jest po prostu jeszcze jedną aplikacją działającą problemu w każdym Uniksie (np. VMD, mopac, platon), w środowisku X Window (Rysunek 1, [8a]). Okno MS Windows a komercyjne posiadają zazwyczaj wersje dla Linuksa (np. mol− może być także wyświetlone na zdalnym komputerze, za pomo− den, pcmodel). Z aplikacjami przeznaczonymi dla innych syste− cą mechanizmów sieciowych X−ów [8b]. mów uniksowych, takimi jak XWinnmr dla Silicon Graphics, daje się bez problemu pracować w systemie X Window. Czasem jed− Instalacja nak muszę używać lub testować oprogramowanie, które nie po− Ponieważ proces instalacji i konfiguracji Win4Lin oraz systemu siada jeszcze odpowiednika pod Linuksem. Dodatkowo prowa− Windows jest wyczerpująco opisany w dokumentacji dostarcza− dzę kilka projektów, takich jak ChemPerfect — zestaw narzędzi nej z programem oraz dostępnej na WWW firmy TreLOS [5], sku− chemicznych do Wordperfecta. Projekt ten rozwijam w dwu wer− pię się na kilku mniej oczywistych punktach. Zakładam też, że sjach — dla Windows i Linuksa. Czasem muszę wprowadzić drob− Czytelnik zna podstawy pracy z Linuksem (i Windows), posiada ne poprawki w tej pierwszej wersji, a nie chce mi się tylko z tego uprawnienia roota i (ewentualnie) wie jak skompilować i zainsta− powodu restartować komputera i ładować MS Windows. Co więcej, lować jądro systemu. -

An Empirical Study Into the Security Exposure to Hosts of Hostile Virtualized Environments
An Empirical Study into the Security Exposure to Hosts of Hostile Virtualized Environments Tavis Ormandy [email protected] Google, Inc. Abstract machine monitor is ‘root secure’[25], meaning that no level of As virtual machines become increasingly commonplace as privilege within the virtualized guest environment permits a method of separating hostile or hazardous code from com- interference with the host system. modity systems, the potential security exposure from imple- Detection mentation flaws has increased dramatically. This paper Detecting virtualized environments has been explored in investigates the state of popular virtual machine implementa- detail by other researchers[22]. Virtual machines employed in tions for x86 systems, employing a combination of source code malware analysis or honeypots should endeavour to be unde- auditing and blackbox random testing to assess the security tectable or risk changing the behaviour of the emulated code. exposure to the hosts of hostile virtualized environments. An emulated malware sample could choose to act benignly, Keywords for example, but when executed on a physical machine imme- virtualization, security, software testing diately performs some malicious action. Detection will not be considered any further in this paper, although being able to detect a virtual machine, or more spe- I. INTRODUCTION cifically, virtual machine implementation, may be a prerequi- Secure isolation is one of the fundamental concepts of vir- site for the more serious attacks investigated in this paper. tualization[15], confining a program to a virtualized environ- Without being able to identify which virtual machine imple- ment should guarantee that any action performed inside the mentation is present, an attacker would have difficulty deter- virtual machine cannot interfere with the system that hosts it1.