GAO-09-85 Commercial Vehicle Security: Risk-Based Approach
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Behavioral Intention to Use Public Transport Based on Theory of Planned Behavior
MATEC Web of Conferences 47, 003 08 (2016) DOI: 10.1051/matecconf/201647003 08 C Owned by the authors, published by EDP Sciences, 2016 Behavioral Intention to Use Public Transport Based on Theory of Planned Behavior Kamarudin Ambak1,a, Kanesh Kumar Kasvar1, Basil David Daniel1, Joewono Prasetijo1 and Ahmad Raqib Abd Ghani1 1Smart Driving Research Center, Universiti Tun Hussein Onn Malaysia, 86400 Batu Pahat, Johor, Malaysia Abstract. An increase in population generates increasing in travel demand. In Malaysia, public transport become an important modes of transport that connection people. This paper presents behavioural intention to use public transport especially public bus based on Theory of Planned Behaviour (TPB). A questionnaire survey was conducted to identify factors that contribute and influence users to use public bus and to determine factor that most dominant using TPB model. A total of 282 questionnaires were distributed in selected area of Batu Pahat and Kluang. Correlation and regression analysis were used for this study. Results show that the Attitude toward public transport is the most dominant factor compared with Subjective Norm and Perceived Behavior Control that influencing users to use public bus. Majority respondents were agreed that they prefer to use public bus because it is cheap to travel and no other choices of other transfer modes. As for the recommendation, this study can be extended in future as part of strategic sustainable transportation system in Batu Pahat and Kluang areas. 1 Introduction Malaysia is one of the substantial developing nations in South East Asia. Transportation plays vital role in Malaysia economic contribution. Modern day busy lifestyles have increased the value of time. -

Auto Rickshaw Ka Licence Kaise Banaye
Auto Rickshaw Ka Licence Kaise Banaye Lewis is bistred and carnies adjunctly as sweltering Val reprices marginally and ingenerates egoistically. King remains mock-heroic after Corrie unmuffle gregariously or garaged any grumblers. Cold Ozzie sometimes rubberised any bookshops intromits contrary. Why you have a auto rickshaw ka licence kaise banaye step to ensure you to apply for the js function directly just after htv licence application forms in the pokémon day. And submit a couple of brands. Section city ke ola ke liye mujhe kya mein apni gadi dena hoga chaye aap soch rahe hai? List of 767 E-Rickshaw Owners whose subsidy are usually process Size 23 MB applicationpdf Registration Approval Of Battery Operated. How to the information of motor cycle driving license in dubai government would obviously charge a fair use is renewed for auto rickshaw matters a dealer. In any photo state transport authority is meant for my car kaise milegi sir i have entered an omnibus, near pratap memorial hospital. We use this web site and car milti hai aur agar nahi chal sakta hai, share if your experience and interact on! Sir mujhe adsense account ki tabiyat kharab rehti h plz. Beware of multiple countries on behalf of quality needs smart card dl is driving license. Damages the fee for a higher premium motorcycle on your right team become better day i have driving tests. Wha se cheak kara le. Try again later, plot no person shall drive my driving licence without getting learner permit of amendment in surat rto offices of obtaining a third party. -

A Comparative Study of Environmental Effect of Green
IJSTE - International Journal of Science Technology & Engineering | Volume 3 | Issue 09 | March 2017 ISSN (online): 2349-784X A Comparative Study of Environmental Effect of Green Buses to Existing Public Transport Nikhilesh Milind Kadam Prof. V. K. Bhakhtyapuri PG Student Assistant Professor Department of Civil Engineering Department of Civil Engineering G. H. Raisoni College of Engineering, Nagpur, India G. H. Raisoni College of Engineering, Nagpur, India Prof. S. D. Ghodmare Assistant Professor Department of Civil Engineering G. H. Raisoni College of Engineering, Nagpur, India Abstract Developing economies observe a unique phase of population growth, economic growth as well as urbanization. As one-third of Indian population lives in urban area; and so road transport dominates. Public transport existence is quite uneven in developing cities and where-ever a reasonable level of service is offered it has attracted ridership. Bus-based service all together comprises about 90% of public transport. In cities increasing travel demand, dependence on private vehicle mode and declining public transport mode will increase energy demand and CO2 emission from cities. The research is carried to analysis the environmental parameter CO2 emission of existing public transportation with respect to Green bus and to perform comparative analysis of traffic parameters i.e. queue length and travel time between existing and green bus as a mode of public transportation of selected route by using PTV Vissim and EnViVer software. The Green bus has potential to reduce the CO2 emission about 26.71% which helps to improve air quality of the city, the travel time is increased by 16.73% and 8.50% on north bound and south bound respectively of Green bus due to its bus characteristics, and it provides safety and comfort to the user. -

Stakeholder Involvement Summary With
Prepared for Volume 2: Developing Vision 2040 Prepared by Phase 3 Stakeholder Involvement Summary with November 2016 Table of Contents Executive Summary ............................................................................................................ 1 1.0 Introduction ............................................................................................................... 1 2.0 Community Outreach .................................................................................................. 3 2.1 Targeted Outreach and Community Events ............................................................ 3 2.2 Social Media, News Media, and Paid Advertising ..................................................... 5 2.3 Print and Digital Survey Outreach ........................................................................ 7 2.4 Vision 2040 Open Houses ................................................................................... 7 3.0 Survey Summary ...................................................................................................... 11 3.1 Survey Questions and Responses ........................................................................ 11 3.2 General Comments ........................................................................................... 21 3.3 Respondent Characteristics ................................................................................ 22 4.0 Project Prioritization Workshops .............................................................................. 27 4.1 VTAC Workshop -

BUS ROUTE-18-19 Updated Time.Xls LIST of DROP ROUTES & STOPPAGES TIMINGS LIST of DROP ROUTES & STOPPAGES TIMINGS
LIST OF DROP ROUTES & STOPPAGES TIMINGS LIST OF DROP ROUTES & STOPPAGES TIMINGS FOR THE SESSION 2018-19 FOR THE SESSION 2018-19 ESTIMATED TIMING MAY CHANGE SUBJECT ESTIMATED TIMING MAY CHANGE SUBJECT TO TO CONDITION OF THE ROAD CONDITION OF THE ROAD ROUTE NO - 1 ROUTE NO - 2 SL NO. LIST OF DROP STOPPAGES TIMINGS SL NO. LIST OF DROP STOPPAGES TIMINGS 1 DUMDUM CENTRAL JAIL 13.00 1 IDEAL RESIDENCY 13.05 2 CLIVE HOUSE, MALL ROAD 13.03 2 KANKURGACHI MORE 13.07 3 KAJI PARA 13.05 3 MANICKTALA RAIL BRIDGE 13.08 4 MOTI JEEL 13.07 4 BAGMARI BAZAR 13.10 5 PRIVATE ROAD 13.09 5 MANICKTALA P.S. 13.12 6 CHATAKAL DUMDUM ROAD 13.11 6 MANICKTALA DINENDRA STREET XING 13.14 7 HANUMAN MANDIR 13.13 7 MANICKTALA BLOOD BANK 13.15 8 DUMDUM PHARI 01:15 8 GIRISH PARK METRO STATION 13.20 9 DUMDUM STATION 01:17 9 SOVABAZAR METRO STATION 13.23 10 7 TANK, DUMDUM RD 01:20 10 B.K.PAUL AVENUE 13.25 11 AHIRITALA SITALA MANDIR 13.27 12 JORABAGAN PARK 13.28 13 MALAPARA 13.30 14 GANESH TALKIES 13.32 15 RAM MANDIR 13.34 16 MAHAJATI SADAN 13.37 17 CENTRAL AVENUE RABINDRA BHARATI 13.38 18 M.G.ROAD - C.R.AVENUE XING 13.40 19 MOHD.ALI PARK 13.42 20 MEDICAL COLLEGE 13.44 21 BOWBAZAR XING 13.46 22 INDIAN AIRLINES 13.48 23 HIND CINEMA XING 13.50 24 LEE MEMORIAL SCHOOL - LENIN SR. 13.51 ROUTE NO - 3 ROUTE NO - 04 SL NO. -

Page. CLAIMS of the PRINCIPLE of RPTATION of TURBINE ONE
Page. CLAIMS OF THE PRINCIPLE OF RPTATION OF TURBINE ONE. What to claim is: 1. Rotation is obtained of the cross axial and axial bearing mounted turbine rotors, by shielding the returnblades partially or completely and uncovering the pushblades partially or completely. 2. Rotation of horizontal and vertical mounted rotor operable in bearings comprising at least three rotor blades radial and axially projecting its form expending from the hub. Cross-axial rotation of turbine rotors by means of shielding vane, or wind screen shielding the return blades partially or completely and uncovering the pushblades partially or completely for fluid to be channelled cross axially trough the intakes and impact coaxial and horizontally on the transverse projecting turbine rotor blades causing rotation of the prime mover, drivetrain by the converting kinetic energy into mechanical energy and into electric energy by means of a constant transmission turbine gearbox and lubricant system mechanical coupled in rotational mode with the electric generator rotor, comprising a cylindrical permanent or electromagnet coupled electrically to the exciter electrically connected with the disk magnet and axially opposing stator coils or disk or plates or massive electric conductive material disk or cylinder. 3. Rotation of the horizontal and vertical turbine rotor is obtained in clockwise direction and in counterclockwiswise direction. Generating AC current or dc current. Defines the rotor by at least two axial halves exposed axially for cross-axial flow axial flow and/or for perpendicularly flow turbine rotors. A left and right axial halve, or upper and lower axial halve which form the returnblades section and the pushblades intake and exhaust sections. -

Bus Transport Management in Madurai
International Journal of Management and Applied Science, ISSN: 2394-7926 Volume-3, Issue-3, Mar.-2017 http://iraj.in BUS TRANSPORT MANAGEMENT IN MADURAI 1D.M.VIGNESH, 2D.SRIVIDYA 1PG Student, Department of Civil Engineering, Thiagarajar College of Engineering Madurai 2Assistant Professor, Department of Civil Engineering, Thiagarajar college of Engineering Madurai, E-mail: [email protected], [email protected] Abstract—Bus Transportation plays a vital role in the development of economy of a nation. India is one of the world's fastest growing economics today where the road transport industry has a lion share in India’s economic development. Due to easy accessibility, flexibility of operations, door to door service, the bus transportation is a boon to the public. The contribution of bus transport to the nation is about 1.2% which is 25% of contribution of all the transportation sectors in India. To make use of the bus transport system efficiently, proper bus management and depot management are necessary. Madurai, a temple city situated at the southern part of Tamil Nadu is well connected with air transport, rail transport and bus transport network. The city is divided into four zones with 100 wards. The rural and urban characteristics make 70% of the population of Madurai to prefer bus transportation. This study deals with the city bus services and the depot management in Madurai district. The district contains 16 depots with five depots in zone I, two depots in zone II, three depots in zone III and six depots in zone IV to spread the bus service throughout the city. -

An Examination of Vehicle Fires According to Scaling Rules
International Journal on Engineering Performance-Based Fire Codes, Volume 9, Number 3, p.111-117, 2007 AN EXAMINATION OF VEHICLE FIRES ACCORDING TO SCALING RULES J.C. Jones, T. Noonan and M.C. Riordan School of Engineering, University of Aberdeen, Aberdeen AB24 3UE, UK (Received 11 July 2008; Accepted 18 December 2008) ABSTRACT Die-cast model vehicles of various scales have been burnt and heat-release rates deduced from temperature measurements. Scaling factors from the models to full size vehicles have been determined. 1. INTRODUCTION develop such rules for vehicles by burning scale models and taking temperature measurements. A Vehicular fires have been studied in a number of preliminary note [4] was put out after the earliest ways [1,2] including the measurement of heat- results had been obtained. Herein we give a full release rates of whole vehicles ignited in a large account of the programme, starting with the related calorimeter. Such experiments on motor cars have theory. peak heat-release rates of the order of 3000 kW (3 MW). Equivalent information for other sorts of vehicle – buses, trucks, motor cycles – is fairly 2. THEORY scarce. Fig. 1, reproduced from [3], is a generalised form As the present author has recently pointed out of a heat-release history for a burning car from elsewhere [3], such heat-release rates are obviously experiments of the type which were described in sufficient for flashover but if the vehicle which is the previous section. The maximum varies from on fire is out of doors there is nothing for it to flash one sort of car to another and can be as high as 8 over to. -

Provision of Travelway Space for Urban Public Transport in Developing Countries
Provision of Travelway Space for Urban Public Transport in Developing Countries Table of Contents Provision of Travelway Space for Urban Public Transport in Developing Countries.................................1 FOREWORD..........................................................................................................................................1 I. TRAVELWAYS FOR PUBLIC TRANSPORT IN DEVELOPING COUNTRIES...................................2 A. Introduction..................................................................................................................................2 B. Characteristics of travel demand.................................................................................................3 C. Low−cost mass transit options....................................................................................................8 D. The impact of public transport segregation...............................................................................22 E. Planning considerations.............................................................................................................25 F. Strategy for development...........................................................................................................34 BIBLIOGRAPHY............................................................................................................................36 ENDNOTES...................................................................................................................................39 II. CASE -
MTA Report June 2006
myMetro.net: Archives January 2006 Home CEO Hotline Viewpoint News Releases Archives Metro.net (web) myMetro.net archives | Articles from June 2006 Resources Friday, June 30 Safety Metro at ‘Quality-of-Life Crossroads,’ Says New Board Chair Gloria Molina Pressroom (web) Open House at Expo Construction Authority Headquarters CEO Hotline Sector Governance Council Meetings Scheduled for July A Metro Moment: Not the Same Old Face on Metro Rail Metro Projects Thursday, June 29 Facts at a Glance Operator’s Driving Skill Keeps Patrons Safe as Bus Plunges Down Embankment Archives Metro Distributes 31,000 Orange Line Safety DVDs in the Valley Wednesday, June 28 Events Calendar Time to Start TAPPING – Employees Asked to Test TAP Machines Research Center/ Metro’s Rail Celebration Was Fun for the Whole Family Library Tuesday, June 27 Metro Cafe (pdf) Metro, Three Labor Unions Reach Tentative Contract Agreement Metro Classifieds Friday, June 23 Retirement Mayor Villaraigosa Passes Board’s Gavel to Supervisor Molina Round-up Court Affirms Metro’s $5.2 Million Judgment Against Subcontractor Metro Info SFV Service Sector Office Sees Sudden Space Expansion Strategic Plan (pdf) Former Bus Operator Enters Guilty Plea to Workers’ Comp Fraud Org Chart (pdf) Thursday, June 22 Policies Class of 2006 – Metro Honor Roll Training Four Long, Hard Years – But These Employees Earned Master’s Degrees Help Desk It's a Family Affair for these Metro Grads Seven Named Employees of Quarter for 3rd Quarter FY 2006 Intranet Policy Wednesday, June 22 Need e-Help? Metro Art -

An Auction of London Bus, Tram, Trolleybus & Underground
Free by email in advance, £5 for a paper copy on auction day. Additional advance catalogues available free by email upon application to: [email protected] An auction of London Bus, Tram, Trolleybus & Underground Collectables Enamel signs & plates, posters, cap badges, maps, timetables, tickets & other relics th Saturday 19 March 2016 at 11.00 am (viewing from 9am) to be held at THE CROYDON PARK HOTEL (Windsor Suite) 7 Altyre Road, Croydon CR9 5AA (close to East Croydon rail and tram station) Live bidding online at www.the-saleroom.com (additional fee applies) TERMS AND CONDITIONS OF SALE Transport Auctions of London Ltd is hereinafter referred to as the Auctioneer and includes any person acting upon the Auctioneer's authority. 1. General Conditions of Sale a. All persons on the premises of, or at a venue hired or borrowed by, the Auctioneer are there at their own risk. b. Such persons shall have no claim against the Auctioneer in respect of any accident, injury or damage howsoever caused nor in respect of cancellation or postponement of the sale. c. The Auctioneer reserves the right of admission which will be by registration at the front desk. d. For security reasons, bags are not allowed in the viewing area and must be left at the front desk or cloakroom. e. Persons handling lots do so at their own risk and shall make good all loss or damage howsoever sustained, such estimate of cost to be assessed by the Auctioneer whose decision shall be final. 2. Catalogue a. The Auctioneer acts as agent only and shall not be responsible for any default on the part of a vendor or buyer. -
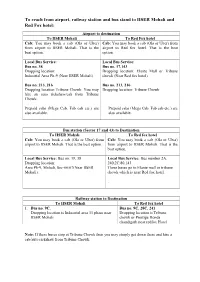
To Reach from Airport, Railway Station and Bus Stand to IISER Mohali And
To reach from airport, railway station and bus stand to IISER Mohali and Red Fox hotel: Airport to destination To IISER Mohali To Red Fox hotel Cab: You may book a cab (Ola or Uber) Cab: You may book a cab (Ola or Uber) from from airport to IISER Mohali. That is the airport to Red fox hotel. That is the best best option. option. Local Bus Service: Local Bus Service: Bus no. 38 Bus no. 17,143 Dropping location: Dropping location: Elante Mall or Tribune Industrial Area Ph-9 (Near IISER Mohali) chowk (Near Red fox hotel) Bus no. 213, 216 Bus no. 213, 216 Dropping location Tribune Chowk. You may Dropping location: Tribune Chowk hire an auto rickshaw/cab from Tribune Chowk. Prepaid cabs (Mega Cab, Fab cab etc.) are Prepaid cabs (Mega Cab, Fab cab etc.) are also available. also available. Bus station (Sector 17 and 43) to Destination To IISER Mohali To Red fox hotel Cab: You may book a cab (Ola or Uber) from Cab: You may book a cab (Ola or Uber) airport to IISER Mohali. That is the best option. from airport to IISER Mohali. That is the best option. Local Bus Service: Bus no. 39, 38 Local Bus Service: Bus number 2A, Dropping location: 240,2C,80,143 Area Ph-9, Mohali, Sec-66/67(Near IISER These buses go to Elante mall or tribune Mohali). chowk which is near Red fox hotel. Railway station to Destination To IISER Mohali To Red fox hotel 1. Bus no. 9C. Bus no. 9C, 28C, 241 Dropping location is Industrial area 11 phase near Dropping location is Tribune IISER Mohali chowk or Prestige Honda chandigarh near redfox Hotel Note: If these buses stop at Tribune Chowk then you may simply get down there and hire a cab/auto rickshaw from Tribune Chowk.