U.S. Army Special Forces Group (Airborne) (U)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Afghanistan State Structure and Security Forces
European Asylum Support Office Afghanistan State Structure and Security Forces Country of Origin Information Report August 2020 SUPPORT IS OUR MISSION European Asylum Support Office Afghanistan State Structure and Security Forces Country of Origin Information Report August 2020 More information on the European Union is available on the Internet (http://europa.eu). ISBN: 978-92-9485-650-0 doi: 10.2847/115002 BZ-02-20-565-EN-N © European Asylum Support Office (EASO) 2020 Reproduction is authorised, provided the source is acknowledged, unless otherwise stated. For third-party materials reproduced in this publication, reference is made to the copyrights statements of the respective third parties. Cover photo: © Al Jazeera English, Helmand, Afghanistan 3 November 2012, url CC BY-SA 2.0 Taliban On the Doorstep: Afghan soldiers from 215 Corps take aim at Taliban insurgents. 4 — AFGHANISTAN: STATE STRUCTURE AND SECURITY FORCES - EASO COUNTRY OF ORIGIN INFORMATION REPORT Acknowledgements This report was drafted by the European Asylum Support Office COI Sector. The following national asylum and migration department contributed by reviewing this report: The Netherlands, Office for Country Information and Language Analysis, Ministry of Justice It must be noted that the review carried out by the mentioned departments, experts or organisations contributes to the overall quality of the report, it but does not necessarily imply their formal endorsement of the final report, which is the full responsibility of EASO. AFGHANISTAN: STATE STRUCTURE AND SECURITY -

Blue Light: America's First Counter-Terrorism Unit Jack Murphy
Blue Light: America's First Counter-Terrorism Unit Jack Murphy On a dark night in 1977, a dozen Green Berets exited a C-130 aircraft, parachuting into a very different type of war. Aircraft hijackings had become almost commonplace to the point that Johnny Carson would tell jokes about the phenomena on television. But it was no laughing matter for the Department of Defense, who realized after the Israeli raid on Entebbe, that America was woefully unprepared to counter terrorist attacks. This mission would be different. The Special Forces soldiers guided their MC1-1B parachutes towards the ground but their element became separated in the air, some of the Green Berets landing in the trees. The others set down alongside an airfield, landing inside a thick cloud of fog. Their target lay somewhere through the haze, a military C-130 aircraft that had been captured by terrorists. Onboard there were no hostages, but a black box, a classified encryption device that could not be allowed to fall into enemy hands. Airfield seizures were really a Ranger mission, but someone had elected to parachute in an entire Special Forces battalion for the operation. The HALO team was an advanced element, inserted ahead of time to secure the aircraft prior to the main assault force arriving. Despite missing a number of team members at the rally point, the Green Berets knew they were quickly approaching their hit time. They had to take down the aircraft and soon. Armed with suppressed Sten guns, they quietly advanced through the fog. Using the bad weather to their advantage, they were able to slip right between the sentries posted to guard the aircraft. -

International Conference KNOWLEDGE-BASED ORGANIZATION Vol
International Conference KNOWLEDGE-BASED ORGANIZATION Vol. XXIII No 1 2017 RISK MANAGEMENT IN THE DECISION MAKING PROCESS CONCERNING THE USE OF OUTSOURCING SERVICES IN THE BULGARIAN ARMED FORCES Nikolay NICHEV “Vasil Levski“ National Military University, Veliko Tarnovo, Bulgaria [email protected] Abstract: Outsourcing services in the armed forces are a promising tool for reducing defence spending which use shall be determined by previously made accurate analysis of peacetime and wartime tasks of army structures. The decision to implement such services allows formations of Bulgarian Army to focus on the implementation of specific tasks related to their combat training. Outsourcing is a successful practice which is applied both in the armies of the member states of NATO and in the Bulgarian Army. Using specialized companies to provide certain services in formations provides a reduction in defence spending, access to technology and skills in terms of financial shortage. The aim of this paper is to analyse main outsourcing risks that affect the relationship between the military formation of the Bulgarian army, the structures of the Ministry of Defence of the Republic of Bulgaria and service providers, and to assess those risks. The basic steps for risk management in outsourcing activities are determined on this base. Keywords: outsourcing, risk management, outsourcing risk 1. Introduction It is measured by its impact and the Outsourcing is an effective tool to generate probability of occurrence, and its new revenue, and the risks that may arise, management is the process of identifying, draw our attention to identifying the main analysing, evaluating, monitoring, types of outsourcing risks. This requires the countering and reporting the risks that may focus of current research on studying and affect the achievement of the objectives of evaluating the possibility of the occurrence an organisation and the implementation of of such risks, and the development of a the necessary control activities in order to system for risks management on this basis. -

Research Special Forces.Indd
www.kcl.ac.uk/lhcma a WORLD WAR WORLDTWO WAR Research Guide Swww.kcl.ac.uk/lhcm pecial Forces Liddell Hart Centre for Military Archives www.kcl.ac.uk/lhcma a EVANS, Maj P H (1913-1994) LAYCOCK, Maj Gen Sir Robert (1907-1968) Trained with Special Operations Executive (SOE) Commanded Special Service Brigade, ‘Layforce’, in Palestine and Egypt, 1943; served with SOE 1941, and Middle East Commando, 1941-194; Special Forces Force 133, Greece, 1943-1944 commanded Special Service Brigade, UK, Diaries, 1943-1944, detailing SOE training, 1942-1943, for the organisation and training of service as instructor, Allied Military Mission Commandos; Chief of Combined Operations, WORLD WAR TWO This guide offers brief descriptions of material held in the Liddell Commando School, Pendalophos, British 1943-1947 Hart Centre for Military Archives relating to the role of Special relations with Greek partisans, and SOE Completed application forms for volunteer Forces in World War Two. Further biographical information about harassment and demolition activity in Greece; Commando officers [1940]; papers on reports,www.kcl.ac.uk/lhcm 1944, on reconnaissance missions in Commando training, 1940-1941; notes and each of the individuals named and complete summary descriptions the Vitsi area, West Macedonia, Greece, and memoranda on Commando operations, on Operation NOAH’S ARK, Allied and Greek 1941-1942; papers on Operation BLAZING and of the papers held here may be consulted on the Centre’s website resistance missions during the German Operation AIMWELL, for raids on Alderney, (see contact details on the back page), where information about withdrawal from Greece; correspondence 1942; notes on the planning of Operation between Evans and other Allied officers, West CORKSCREW for the capture of Pantelleria, the location of the Centre, opening hours and how to gain access Macedonia, Greece, 1944; captured German Linosa and Lampedusa Islands, Mediterranean, may also be found. -

The Internal Security Forces (I.S.F) in Lebanon Their Creation – History- Development
The Internal Security Forces (I.S.F) in Lebanon Their creation – History- Development First : The creation of the I.S.F. Lebanon did not know a police organization, in the modern and legal meaning, before the creation of a lebanese gendarmerie by virtue of protocol 1861. Before this year, the Lebanese Emirs, with the help of their armed men, were in charge of policing, law enforcement and tax-collect. We will present hereunder a summary concerning the creation of the I.S.F. 1- The mandate of Emir Fakhreddine II (He came to power in 1589): The Emir Fakhreddine II is considered to be the founder of the modern Lebanese state. After a perturbated childhood, he came to power in 1589 and started instantly working for the unification of the country, by destroying some independent ephemeral Lebanese families, who were dissenters. In order to control policing and for the execution of ordinary police missions, the Emir has created a group of armed men, named “Zelems” i.e. direct servants. There were also another little groups of “Zelems” for feudal lords. If internal disorders became alarming and threatening the total security of the country, the Emir did not hesitate to ask help from his professional elements “The Sikmans”, who were foreign mercenaries. Nevertheless, he avoided the participation of “Bedouins”, used to theft and murders, instead of military actions. 2- The mandate of Emir Bechir II (He came to power in 1788) There were two kinds of military elements for policing: the first are “Cavaliers” of Emir Bechir the great and “Tax Collector” or “Hawalie” whose functions were as gendarmes, threatening evildoers. -

This Index Lists the Army Units for Which Records Are Available at the Eisenhower Library
DWIGHT D. EISENHOWER LIBRARY ABILENE, KANSAS U.S. ARMY: Unit Records, 1917-1950 Linear feet: 687 Approximate number of pages: 1,300,000 The U.S. Army Unit Records collection (formerly: U.S. Army, U.S. Forces, European Theater: Selected After Action Reports, 1941-45) primarily spans the period from 1917 to 1950, with the bulk of the material covering the World War II years (1942-45). The collection is comprised of organizational and operational records and miscellaneous historical material from the files of army units that served in World War II. The collection was originally in the custody of the World War II Records Division (now the Modern Military Records Branch), National Archives and Records Service. The material was withdrawn from their holdings in 1960 and sent to the Kansas City Federal Records Center for shipment to the Eisenhower Library. The records were received by the Library from the Kansas City Records Center on June 1, 1962. Most of the collection contained formerly classified material that was bulk-declassified on June 29, 1973, under declassification project number 735035. General restrictions on the use of records in the National Archives still apply. The collection consists primarily of material from infantry, airborne, cavalry, armor, artillery, engineer, and tank destroyer units; roughly half of the collection consists of material from infantry units, division through company levels. Although the collection contains material from over 2,000 units, with each unit forming a separate series, every army unit that served in World War II is not represented. Approximately seventy-five percent of the documents are from units in the European Theater of Operations, about twenty percent from the Pacific theater, and about five percent from units that served in the western hemisphere during World War II. -
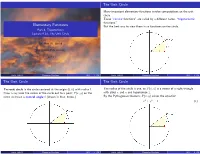
4.1 Unit Circle Cosine & Sine (Slides 4-To-1).Pdf
The Unit Circle Many important elementary functions involve computations on the unit circle. These \circular functions" are called by a different name, \trigonometric functions." Elementary Functions But the best way to view them is as functions on the circle. Part 4, Trigonometry Lecture 4.1a, The Unit Circle Dr. Ken W. Smith Sam Houston State University 2013 Smith (SHSU) Elementary Functions 2013 1 / 54 Smith (SHSU) Elementary Functions 2013 2 / 54 The Unit Circle The Unit Circle The unit circle is the circle centered at the origin (0; 0) with radius 1. The radius of the circle is one, so P (x; y) is a vertex of a right triangle Draw a ray from the center of the circle out to a point P (x; y) on the with sides x and y and hypotenuse 1. circle to create a central angle θ (drawn in blue, below.) By the Pythagorean theorem, P (x; y) solves the equation x2 + y2 = 1 (1) Smith (SHSU) Elementary Functions 2013 3 / 54 Smith (SHSU) Elementary Functions 2013 4 / 54 Central Angles and Arcs Central Angles and Arcs An arc of the circle corresponds to a central angle created by drawing line segments from the endpoints of the arc to the center. The Babylonians (4000 years ago!) divided the circle into 360 pieces, called degrees. This choice is a very human one; it does not have a natural mathematical reason. (It is not \intrinsic" to the circle.) The most natural way to measure arcs on a circle is by the intrinsic unit of measurement which comes with the circle, that is, the length of the radius. -

Counterterrorism and the Role of Special Operations Forces
C O R P O R A T I O N CHILDREN AND FAMILIES The RAND Corporation is a nonprofit institution that helps improve policy and EDUCATION AND THE ARTS decisionmaking through research and analysis. ENERGY AND ENVIRONMENT HEALTH AND HEALTH CARE This electronic document was made available from www.rand.org as a public service INFRASTRUCTURE AND of the RAND Corporation. TRANSPORTATION INTERNATIONAL AFFAIRS LAW AND BUSINESS Skip all front matter: Jump to Page 16 NATIONAL SECURITY POPULATION AND AGING PUBLIC SAFETY Support RAND SCIENCE AND TECHNOLOGY Browse Reports & Bookstore TERRORISM AND Make a charitable contribution HOMELAND SECURITY For More Information Visit RAND at www.rand.org Explore RAND Testimony View document details Testimonies RAND testimonies record testimony presented by RAND associates to federal, state, or local legislative committees; government-appointed commissions and panels; and private review and oversight bodies. Limited Electronic Distribution Rights This document and trademark(s) contained herein are protected by law as indicated in a notice appearing later in this work. This electronic representation of RAND intellectual property is provided for non- commercial use only. Unauthorized posting of RAND electronic documents to a non-RAND website is prohibited. RAND electronic documents are protected under copyright law. Permission is required from RAND to reproduce, or reuse in another form, any of our research documents for commercial use. For information on reprint and linking permissions, please see RAND Permissions. Testimony Counterterrorism and the Role of Special Operations Forces Seth G. Jones RAND Office of External Affairs CT-408 April 2014 Testimony presented before the House Foreign Affairs Committee, Subcommittee on Terrorism, Non-Proliferation, and Trade on April 8, 2014 This product is part of the RAND Corporation testimony series. -

Countering Terrorism Online with Artificial Intelligence an Overview for Law Enforcement and Counter-Terrorism Agencies in South Asia and South-East Asia
COUNTERING TERRORISM ONLINE WITH ARTIFICIAL INTELLIGENCE AN OVERVIEW FOR LAW ENFORCEMENT AND COUNTER-TERRORISM AGENCIES IN SOUTH ASIA AND SOUTH-EAST ASIA COUNTERING TERRORISM ONLINE WITH ARTIFICIAL INTELLIGENCE An Overview for Law Enforcement and Counter-Terrorism Agencies in South Asia and South-East Asia A Joint Report by UNICRI and UNCCT 3 Disclaimer The opinions, findings, conclusions and recommendations expressed herein do not necessarily reflect the views of the Unit- ed Nations, the Government of Japan or any other national, regional or global entities involved. Moreover, reference to any specific tool or application in this report should not be considered an endorsement by UNOCT-UNCCT, UNICRI or by the United Nations itself. The designation employed and material presented in this publication does not imply the expression of any opinion whatsoev- er on the part of the Secretariat of the United Nations concerning the legal status of any country, territory, city or area of its authorities, or concerning the delimitation of its frontiers or boundaries. Contents of this publication may be quoted or reproduced, provided that the source of information is acknowledged. The au- thors would like to receive a copy of the document in which this publication is used or quoted. Acknowledgements This report is the product of a joint research initiative on counter-terrorism in the age of artificial intelligence of the Cyber Security and New Technologies Unit of the United Nations Counter-Terrorism Centre (UNCCT) in the United Nations Office of Counter-Terrorism (UNOCT) and the United Nations Interregional Crime and Justice Research Institute (UNICRI) through its Centre for Artificial Intelligence and Robotics. -

A Memoir by the Founder of the US Militarys Most Secretive Special
DELTA FORCE: A MEMOIR BY THE FOUNDER OF THE U.S. MILITARYS MOST SECRETIVE SPECIAL- OPERATIONS UNIT PDF, EPUB, EBOOK Charlie A. Beckwith,Donald Knox | 384 pages | 27 May 2013 | HarperCollins Publishers Inc | 9780062249692 | English | New York, United States Delta Force: A Memoir by the Founder of the U.S. Militarys Most Secretive Special- Operations Unit PDF Book Rival warlords weighed their military decisions according to personal agendas. Footer Emails Suck. Your email address will not be published. Beckwith gives particular credit to a South Vietnamese helicopter pilot in Vietnam, but later adversely views USMC helicopter pilots in Iran, a strange contrast. The lowest-priced brand-new, unused, unopened, undamaged item in its original packaging where packaging is applicable. That's unfortunate because I think Col Beckwith was a great man and had lots of wisdom in his memoir. Hot Best Seller. David — Feb 01, I am not sure if he dose not see that in the book or he is honest enough to lay it out as it happened. Hard to put down. Both books should be read to get a good picture of the unit. Not that well written, not that gripping or human. Forrest — Jul 13, See details. This New York Times bestseller chronicles his life, his struggles, and, ultimately, his ultimate sacrifice in Afghanistan. Buy It Now. You may also like. The chapters focusing on the bureaucracy in the US military in the early- to mid-seventies weren't particularly interesting. He talks at length about his time with 22SAS and as an English man i can only hope they knew what high regard he had for them. -

Ausa Background Brief (
AUSA BACKGROUND BRIEF ( No. 42 April 1992 SPECIAL OPERATIONS FORCES: A PRIMER Introduction A small but critical portion of the Total Force is made up of the special operations forces (SOF) of the Army, Navy and Air Force, which are comprised of special operations, psychological operations and civil affairs organizations. Special operations forces are task organized to conduct contingency operations. Special operations forces are designed to augment theater-based forces and, in response to a crisis situation, normally operate with an appropriate mix of conventional forces under theater control. ( Almost all SOF missions require joint planning; also, they are used for missions with allied or coalition forces as well as for a number of ongoing ground missions in many countries. U.S. Special Operations Command The joint nature ofSOF operations was recognized in the establishment of a permanent unified command, the U.S. Special Operations Command (USSOCOM). The USSOCOM commander-in chief commands all active and reserve Special Operations, Psychological Operations and Civil Affairs forces of the Army, Navy and Air Force (about 47,000 personnel). USSOCOM supports other unified commands responsible for crisis responses in their respective geographic areas of responsibility. The U.S. Special Operations Command is composed of four subordinate commands: U.S. Army Special Operations Command, Naval Special Warfare Command, Air Force Special Opera tions Command and Joint Special Operations Command. U.S. Army Special Operations Command (USASOC), headquartered at Fort Bragg, North Carolina, is composed of active component and reserve component Army forces consisting of Special Forces groups, a Ranger regiment, Psychological Operations groups, a Special Operations Aviation regiment, Civil Affairs commands, and special operations signal and support units. -

SCENARIOS Possible Developments in the Profile of the Displaced Population and Humanitarian Access Over the Next 18 Months June 2019
DISPLACEMENT AND ACCESS IN AFGHANISTAN: SCENARIOS Possible developments in the profile of the displaced population and humanitarian access over the next 18 months June 2019 Any questions? Please contact [email protected] Scenario 1 Central government strengthens; reduced violence Scenario 3 Central government weakens; regions strengthen President elected in September receives broad support from all Afghans, a Following inconclusive elections, none of the parties have the power to extend substantive US-Taliban peace deal is reached, and GoA and Taliban agree to negotiate territorial control significantly but seek to consolidate their positions by exerting a form of shared governance. International forces begin a phased withdrawal. Splinter increasing control over the population, including in major urban areas. The GoA is elements of the Taliban, the ISK, and others disrupt security, but this is localised. largely symbolic and provides only specific, limited support to the regions. Conflict International support for state building and counterterrorism increases as part of a intensifies in many areas, predominantly the north, east, and southeast, as faction post-peace economic package while overall humanitarian funding decreases. China leaders seek to maximise areas under their control. Foreign funding reduces. and India begin large-scale investment. Scenario 4 Ineffective central governance; widespread conflict Scenario 2 Limited central governance; increased non-state actor influence A major shock renders the central government ineffective and unable to govern beyond Kabul. With central government focused almost entirely internally and on re- establishing security in Kabul, provincial power brokers seize the opportunity to establish de facto control over the provinces. The balance of power moves from Kabul GoA continues to exert limited political control beyond major urban centres.