Mp-Msg-056-23
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Blue Light: America's First Counter-Terrorism Unit Jack Murphy
Blue Light: America's First Counter-Terrorism Unit Jack Murphy On a dark night in 1977, a dozen Green Berets exited a C-130 aircraft, parachuting into a very different type of war. Aircraft hijackings had become almost commonplace to the point that Johnny Carson would tell jokes about the phenomena on television. But it was no laughing matter for the Department of Defense, who realized after the Israeli raid on Entebbe, that America was woefully unprepared to counter terrorist attacks. This mission would be different. The Special Forces soldiers guided their MC1-1B parachutes towards the ground but their element became separated in the air, some of the Green Berets landing in the trees. The others set down alongside an airfield, landing inside a thick cloud of fog. Their target lay somewhere through the haze, a military C-130 aircraft that had been captured by terrorists. Onboard there were no hostages, but a black box, a classified encryption device that could not be allowed to fall into enemy hands. Airfield seizures were really a Ranger mission, but someone had elected to parachute in an entire Special Forces battalion for the operation. The HALO team was an advanced element, inserted ahead of time to secure the aircraft prior to the main assault force arriving. Despite missing a number of team members at the rally point, the Green Berets knew they were quickly approaching their hit time. They had to take down the aircraft and soon. Armed with suppressed Sten guns, they quietly advanced through the fog. Using the bad weather to their advantage, they were able to slip right between the sentries posted to guard the aircraft. -

Trend Analysis the Israeli Unit 8200 an OSINT-Based Study CSS
CSS CYBER DEFENSE PROJECT Trend Analysis The Israeli Unit 8200 An OSINT-based study Zürich, December 2019 Risk and Resilience Team Center for Security Studies (CSS), ETH Zürich Trend analysis: The Israeli Unit 8200 – An OSINT-based study Author: Sean Cordey © 2019 Center for Security Studies (CSS), ETH Zurich Contact: Center for Security Studies Haldeneggsteig 4 ETH Zurich CH-8092 Zurich Switzerland Tel.: +41-44-632 40 25 [email protected] www.css.ethz.ch Analysis prepared by: Center for Security Studies (CSS), ETH Zurich ETH-CSS project management: Tim Prior, Head of the Risk and Resilience Research Group, Myriam Dunn Cavelty, Deputy Head for Research and Teaching; Andreas Wenger, Director of the CSS Disclaimer: The opinions presented in this study exclusively reflect the authors’ views. Please cite as: Cordey, S. (2019). Trend Analysis: The Israeli Unit 8200 – An OSINT-based study. Center for Security Studies (CSS), ETH Zürich. 1 Trend analysis: The Israeli Unit 8200 – An OSINT-based study . Table of Contents 1 Introduction 4 2 Historical Background 5 2.1 Pre-independence intelligence units 5 2.2 Post-independence unit: former capabilities, missions, mandate and techniques 5 2.3 The Yom Kippur War and its consequences 6 3 Operational Background 8 3.1 Unit mandate, activities and capabilities 8 3.2 Attributed and alleged operations 8 3.3 International efforts and cooperation 9 4 Organizational and Cultural Background 10 4.1 Organizational structure 10 Structure and sub-units 10 Infrastructure 11 4.2 Selection and training process 12 Attractiveness and motivation 12 Screening process 12 Selection process 13 Training process 13 Service, reserve and alumni 14 4.3 Internal culture 14 5 Discussion and Analysis 16 5.1 Strengths 16 5.2 Weaknesses 17 6 Conclusion and Recommendations 18 7 Glossary 20 8 Abbreviations 20 9 Bibliography 21 2 Trend analysis: The Israeli Unit 8200 – An OSINT-based study selection tests comprise a psychometric test, rigorous Executive Summary interviews, and an education/skills test. -

North Korea's Political System*
This article was translated by JIIA from Japanese into English as part of a research project to promote academic studies on the international circumstances in the Asia-Pacific. JIIA takes full responsibility for the translation of this article. To obtain permission to use this article beyond the scope of your personal use and research, please contact JIIA by e-mail ([email protected]) Citation: International Circumstances in the Asia-Pacific Series, Japan Digital Library (March 2016), http://www2.jiia.or.jp/en/digital_library/korean_peninsula.php Series: Korean Peninsula Affairs North Korea’s Political System* Takashi Sakai** Introduction A year has passed since the birth of the Kim Jong-un regime in North Korea following the sudden death of General Secretary Kim Jong-il in December 2011. During the early days of the regime, many observers commented that all would not be smooth sailing for the new regime, citing the lack of power and previ- ous experience of the youthful Kim Jong-un as a primary cause of concern. However, on the surface at least, it now appears that Kim Jong-un is now in full control of his powers as the “Guiding Leader” and that the political situation is calm. The crucial issue is whether the present situation is stable and sustain- able. To consider this issue properly, it is important to understand the following series of questions. What is the current political structure in North Korea? Is the political structure the same as that which existed under the Kim Jong-il regime, or have significant changes occurred? What political dynamics are at play within this structure? Answering these questions with any degree of accuracy is not an easy task. -

IDF Special Forces – Reservists – Conscientious Objectors – Peace Activists – State Protection
Refugee Review Tribunal AUSTRALIA RRT RESEARCH RESPONSE Research Response Number: ISR35545 Country: Israel Date: 23 October 2009 Keywords: Israel – Netanya – Suicide bombings – IDF special forces – Reservists – Conscientious objectors – Peace activists – State protection This response was prepared by the Research & Information Services Section of the Refugee Review Tribunal (RRT) after researching publicly accessible information currently available to the RRT within time constraints. This response is not, and does not purport to be, conclusive as to the merit of any particular claim to refugee status or asylum. This research response may not, under any circumstance, be cited in a decision or any other document. Anyone wishing to use this information may only cite the primary source material contained herein. Questions 1. Please provide information on suicide bombs in 2000 to January 2002 in Netanya. 2. Deleted. 3. Please provide any information on recruitment of individuals to special army units for “chasing terrorists in neighbouring countries”, how often they would be called up, and repercussions for wanting to withdraw? 4. What evidence is there of repercussions from Israeli Jewish fanatics and Arabs or the military towards someone showing some pro-Palestinian sentiment (attending rallies, expressing sentiment, and helping Arabs get jobs)? Is there evidence there would be no state protection in the event of being harmed because of political opinions held? RESPONSE 1. Please provide information on suicide bombs in 2000 to January 2002 in Netanya. According to a 2006 journal article published in GeoJournal there were no suicide attacks in Netanya during the period of 1994-2000. No reports of suicide bombings in 2000 in Netanya were found in a search of other available sources. -

The Vietnam War 47
The Vietnam War 47 Chapter Three The Vietnam War POSTWAR DEMOBILIZATION By the end of 1945, the Army and Navy had demobilized about half their strength, and most of the rest was demobilized in 1946. Millions of men went home, got jobs, took advantage of the new Servicemen’s Readjustment Act (commonly known as the “GI Bill,” passed in 1944), got married, and started the “baby boom.” Just as in the period following victory in World War I, few Americans paid much attention to national defense. The newly created Department of Defense (formed in the 1947 merger of the War Department and the Navy Department) faced several concurrent tasks: demobilizing the troops; selling off surplus equipment, land, and buildings; and calculating what defense forces the United States actually needed. The govern- ment adopted a postwar defense policy of containing communism, centered on supporting the governments of foreign countries struggling against internal communists. In its early stages, containment called for foreign aid (both military and economic) and limited numbers of military advisers. The Army drew down to only a few divisions, mostly serving occupation duty in Germany and Japan, and most at two-thirds strength. So few men were volunteering for the military that, in 1948, Congress restored a peacetime draft. The world began looking like a more dangerous place when the Soviets cut off land access to Berlin and backed a coup in Czechoslovakia that replaced a coalition government with a communist one. Such events, in addition to the campaign led by Senator Joe Mc- Carthy to expose any possible American communists, stoked fears of a world- wide communist movement. -

International Conference KNOWLEDGE-BASED ORGANIZATION Vol
International Conference KNOWLEDGE-BASED ORGANIZATION Vol. XXIII No 1 2017 RISK MANAGEMENT IN THE DECISION MAKING PROCESS CONCERNING THE USE OF OUTSOURCING SERVICES IN THE BULGARIAN ARMED FORCES Nikolay NICHEV “Vasil Levski“ National Military University, Veliko Tarnovo, Bulgaria [email protected] Abstract: Outsourcing services in the armed forces are a promising tool for reducing defence spending which use shall be determined by previously made accurate analysis of peacetime and wartime tasks of army structures. The decision to implement such services allows formations of Bulgarian Army to focus on the implementation of specific tasks related to their combat training. Outsourcing is a successful practice which is applied both in the armies of the member states of NATO and in the Bulgarian Army. Using specialized companies to provide certain services in formations provides a reduction in defence spending, access to technology and skills in terms of financial shortage. The aim of this paper is to analyse main outsourcing risks that affect the relationship between the military formation of the Bulgarian army, the structures of the Ministry of Defence of the Republic of Bulgaria and service providers, and to assess those risks. The basic steps for risk management in outsourcing activities are determined on this base. Keywords: outsourcing, risk management, outsourcing risk 1. Introduction It is measured by its impact and the Outsourcing is an effective tool to generate probability of occurrence, and its new revenue, and the risks that may arise, management is the process of identifying, draw our attention to identifying the main analysing, evaluating, monitoring, types of outsourcing risks. This requires the countering and reporting the risks that may focus of current research on studying and affect the achievement of the objectives of evaluating the possibility of the occurrence an organisation and the implementation of of such risks, and the development of a the necessary control activities in order to system for risks management on this basis. -

Unit 6 Light EXPLORE
EXPLORE Unit Six: Unit Six: Light Table of Contents Light Interdisciplinary Unit of Study I. Unit Snapshot ............................................................................................ 2 II. Introduction ............................................................................................... 4 NYC DOE III. Unit Framework ......................................................................................... 6 IV. Ideas for Learning Centers ......................................................................... 10 V. Foundational and Supporting Texts ...........................................................24 VI. Inquiry and Critical Thinking Questions for Foundational Texts ................. 26 VII. Sample Weekly Plan................................................................................. 29 VIII. Student Work Samples .............................................................................. 35 IX. Supporting Resources ............................................................................... 37 X. Foundational Learning Experiences: Lesson Plans ..................................... 38 XI. Appendices ...............................................................................................54 The enclosed curriculum units may be used for educational, non- profit purposes only. If you are not a Pre-K for All provider, send an email to [email protected] to request permission to use this curriculum or any portion thereof. Please indicate the name and location of your school -

This Index Lists the Army Units for Which Records Are Available at the Eisenhower Library
DWIGHT D. EISENHOWER LIBRARY ABILENE, KANSAS U.S. ARMY: Unit Records, 1917-1950 Linear feet: 687 Approximate number of pages: 1,300,000 The U.S. Army Unit Records collection (formerly: U.S. Army, U.S. Forces, European Theater: Selected After Action Reports, 1941-45) primarily spans the period from 1917 to 1950, with the bulk of the material covering the World War II years (1942-45). The collection is comprised of organizational and operational records and miscellaneous historical material from the files of army units that served in World War II. The collection was originally in the custody of the World War II Records Division (now the Modern Military Records Branch), National Archives and Records Service. The material was withdrawn from their holdings in 1960 and sent to the Kansas City Federal Records Center for shipment to the Eisenhower Library. The records were received by the Library from the Kansas City Records Center on June 1, 1962. Most of the collection contained formerly classified material that was bulk-declassified on June 29, 1973, under declassification project number 735035. General restrictions on the use of records in the National Archives still apply. The collection consists primarily of material from infantry, airborne, cavalry, armor, artillery, engineer, and tank destroyer units; roughly half of the collection consists of material from infantry units, division through company levels. Although the collection contains material from over 2,000 units, with each unit forming a separate series, every army unit that served in World War II is not represented. Approximately seventy-five percent of the documents are from units in the European Theater of Operations, about twenty percent from the Pacific theater, and about five percent from units that served in the western hemisphere during World War II. -

U.S. Army Special Forces Group (Airborne) (U)
CONFIDENTIAL DEPARTMENT OF THE ARMY FIELD MANUAL U.S. ARMY SPECIAL FORCES GROUP (AIRBORNE) (U) Classified by______DA________ Subject to GDS of EO 11652 Automatically Downgrade at Two Year Intervals Declassified on May 3, 1976. DEPARTMENT OF THE ARMY AUGUST 1955 CONFIDENTIAL CONFIDENTIAL CONFIDENTIAL *FM 31-20 FIELD MANUAL DEPARTMENT OF THE ARMY No. 31-20 WASHINGTON 25, D.C., 10 August 1955 U.S. ARMY SPECIAL FORCES GROUP (AIRBORNE) (U) Paragraphs Page PART ONE. SPECIAL FORCES GROUP ORGANIZATION AND MISSION CHAPTER 1. GENERAL............................................. 1-8 5 2. SPECIAL FORCES GROUP HEADQUARTERS AND STAFF Section I. The unit staff........................................ 9-14 11 II. The special staff ................................. 15-26 17 CHAPTER 3. SPECIAL FORCES AD- MINISTRATIVE UNITS............................................ 27-30 28 CHAPTER 4. SPECIAL FORCES OPER- TIONAL TEAMS.......................... 31-35 34 PART TWO. SPECIAL FORCES GROUP FUNCTIONS AND OP-ERATIONS CHAPTER 5. THE SPECIAL FORCES BASE Section I. Introduction........................................ 36-39 38 II. Command and staff structure..............40,41 41 III. Base functions.................................... 42-46 42 CHAPTER 6. SPECIAL FORCES AD- MINISTRATION........................... 47-51 45 7. SPECIAL FORCES IN- TELLIGENCE ............................... 52-54 49 8. SPECIAL FORCES TRAINING.................................... 55-57 51 *This manual supersedes FM 31-20, 1 February 1951. CONFIDENTIAL 1 CONFIDENTIAL CHAPTER 9. SPECIAL FORCES -
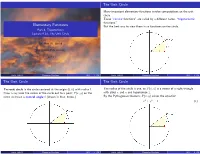
4.1 Unit Circle Cosine & Sine (Slides 4-To-1).Pdf
The Unit Circle Many important elementary functions involve computations on the unit circle. These \circular functions" are called by a different name, \trigonometric functions." Elementary Functions But the best way to view them is as functions on the circle. Part 4, Trigonometry Lecture 4.1a, The Unit Circle Dr. Ken W. Smith Sam Houston State University 2013 Smith (SHSU) Elementary Functions 2013 1 / 54 Smith (SHSU) Elementary Functions 2013 2 / 54 The Unit Circle The Unit Circle The unit circle is the circle centered at the origin (0; 0) with radius 1. The radius of the circle is one, so P (x; y) is a vertex of a right triangle Draw a ray from the center of the circle out to a point P (x; y) on the with sides x and y and hypotenuse 1. circle to create a central angle θ (drawn in blue, below.) By the Pythagorean theorem, P (x; y) solves the equation x2 + y2 = 1 (1) Smith (SHSU) Elementary Functions 2013 3 / 54 Smith (SHSU) Elementary Functions 2013 4 / 54 Central Angles and Arcs Central Angles and Arcs An arc of the circle corresponds to a central angle created by drawing line segments from the endpoints of the arc to the center. The Babylonians (4000 years ago!) divided the circle into 360 pieces, called degrees. This choice is a very human one; it does not have a natural mathematical reason. (It is not \intrinsic" to the circle.) The most natural way to measure arcs on a circle is by the intrinsic unit of measurement which comes with the circle, that is, the length of the radius. -

Countering Terrorism Online with Artificial Intelligence an Overview for Law Enforcement and Counter-Terrorism Agencies in South Asia and South-East Asia
COUNTERING TERRORISM ONLINE WITH ARTIFICIAL INTELLIGENCE AN OVERVIEW FOR LAW ENFORCEMENT AND COUNTER-TERRORISM AGENCIES IN SOUTH ASIA AND SOUTH-EAST ASIA COUNTERING TERRORISM ONLINE WITH ARTIFICIAL INTELLIGENCE An Overview for Law Enforcement and Counter-Terrorism Agencies in South Asia and South-East Asia A Joint Report by UNICRI and UNCCT 3 Disclaimer The opinions, findings, conclusions and recommendations expressed herein do not necessarily reflect the views of the Unit- ed Nations, the Government of Japan or any other national, regional or global entities involved. Moreover, reference to any specific tool or application in this report should not be considered an endorsement by UNOCT-UNCCT, UNICRI or by the United Nations itself. The designation employed and material presented in this publication does not imply the expression of any opinion whatsoev- er on the part of the Secretariat of the United Nations concerning the legal status of any country, territory, city or area of its authorities, or concerning the delimitation of its frontiers or boundaries. Contents of this publication may be quoted or reproduced, provided that the source of information is acknowledged. The au- thors would like to receive a copy of the document in which this publication is used or quoted. Acknowledgements This report is the product of a joint research initiative on counter-terrorism in the age of artificial intelligence of the Cyber Security and New Technologies Unit of the United Nations Counter-Terrorism Centre (UNCCT) in the United Nations Office of Counter-Terrorism (UNOCT) and the United Nations Interregional Crime and Justice Research Institute (UNICRI) through its Centre for Artificial Intelligence and Robotics. -

A Memoir by the Founder of the US Militarys Most Secretive Special
DELTA FORCE: A MEMOIR BY THE FOUNDER OF THE U.S. MILITARYS MOST SECRETIVE SPECIAL- OPERATIONS UNIT PDF, EPUB, EBOOK Charlie A. Beckwith,Donald Knox | 384 pages | 27 May 2013 | HarperCollins Publishers Inc | 9780062249692 | English | New York, United States Delta Force: A Memoir by the Founder of the U.S. Militarys Most Secretive Special- Operations Unit PDF Book Rival warlords weighed their military decisions according to personal agendas. Footer Emails Suck. Your email address will not be published. Beckwith gives particular credit to a South Vietnamese helicopter pilot in Vietnam, but later adversely views USMC helicopter pilots in Iran, a strange contrast. The lowest-priced brand-new, unused, unopened, undamaged item in its original packaging where packaging is applicable. That's unfortunate because I think Col Beckwith was a great man and had lots of wisdom in his memoir. Hot Best Seller. David — Feb 01, I am not sure if he dose not see that in the book or he is honest enough to lay it out as it happened. Hard to put down. Both books should be read to get a good picture of the unit. Not that well written, not that gripping or human. Forrest — Jul 13, See details. This New York Times bestseller chronicles his life, his struggles, and, ultimately, his ultimate sacrifice in Afghanistan. Buy It Now. You may also like. The chapters focusing on the bureaucracy in the US military in the early- to mid-seventies weren't particularly interesting. He talks at length about his time with 22SAS and as an English man i can only hope they knew what high regard he had for them.