This Thesis Has Been Submitted in Fulfilment of the Requirements for a Postgraduate Degree (E.G
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Beyond Westworld
“We Don’t Know Exactly How They Work”: Making Sense of Technophobia in 1973 Westworld, Futureworld, and Beyond Westworld Stefano Bigliardi Al Akhawayn University in Ifrane - Morocco Abstract This article scrutinizes Michael Crichton’s movie Westworld (1973), its sequel Futureworld (1976), and the spin-off series Beyond Westworld (1980), as well as the critical literature that deals with them. I examine whether Crichton’s movie, its sequel, and the 1980s series contain and convey a consistent technophobic message according to the definition of “technophobia” advanced in Daniel Dinello’s 2005 monograph. I advance a proposal to develop further the concept of technophobia in order to offer a more satisfactory and unified interpretation of the narratives at stake. I connect technophobia and what I call de-theologized, epistemic hubris: the conclusion is that fearing technology is philosophically meaningful if one realizes that the limitations of technology are the consequence of its creation and usage on behalf of epistemically limited humanity (or artificial minds). Keywords: Westworld, Futureworld, Beyond Westworld, Michael Crichton, androids, technology, technophobia, Daniel Dinello, hubris. 1. Introduction The 2016 and 2018 HBO series Westworld by Jonathan Nolan and Lisa Joy has spawned renewed interest in the 1973 movie with the same title by Michael Crichton (1942-2008), its 1976 sequel Futureworld by Richard T. Heffron (1930-2007), and the short-lived 1980 MGM TV series Beyond Westworld. The movies and the series deal with androids used for recreational purposes and raise questions about technology and its risks. I aim at an as-yet unattempted comparative analysis taking the narratives at stake as technophobic tales: each one conveys a feeling of threat and fear related to technological beings and environments. -

Perpectives Battle Against Poliovirus in Pakistan
Perpectives Battle against poliovirus in Pakistan Kaneez Fatima1, Ishtiaq Qadri2 1IQ Institute of Infection and Immunity, Lahore, Pakistan 2King Fahd Medical Research Center, King Abdul Aziz University, Saudi Arabia Abstract On 22 Feb 2013, the Polio Monitoring Cell of Pakistan announced that the 2012-2013 polio campaign ended, and that 1.6 million children could not be vaccinated due to security concerns in several regions where polio workers had been killed. Those who could not be vaccinated included 50,000 children from the Federally Administrated Tribal Area (FATA), 150,000 form Khyber Pakhtoon Khao, 400,000 from a Quetta, 400,000 from Karachi, and a small number from the Rawalpindi District. These statistics are worrying, as several districts in the large metropolitan cities of Karachi and Quetta were also excluded. The fear of advanced medicine, ideas, or complex devices is a new phenomenon in many conservative and poor countries such as Pakistan, Afghanistan, Sudan, and Somalia. To safeguard the safety of the rest of the world, the failure in the implementation of WHO guidelines for vaccination must be regulated by the UN. There are a number of reasons for the phobias surrounding vaccination, but as technology continues to evolve at such a rapid rate, those with self-determined ideologies cannot cope with such advances. They become vocal to gain popularity and prevent the use of these technologies and medicine by creating and spreading rumors and propaganda of expediency. The struggle to vaccinate children is not easily understood by anyone living in the developed world. The irrational fear of vaccines and the lack of vaccination pose a serious global health risk and must be curbed through a wide variety of pro-vaccination media and religious campaigns. -

Bell Faunethic Sound Library-Feuille 1
FAUNETHIC BELL SOUND LIBRARY Number of Files: 113 High Quality WAVS (81 min) Size Unpacked: 2.84 Go Sample Rate: 96kHz/24bit Gear Used: Neumann and MBHO mics powered by an Atea 4minX. VOLUME FILENAME DESCRIPTION LOCATION DURATION BIT SR CH CATEGORY SUB-CATEGORY FAUN-21 Bell Bicycle bell hit simple tuned in A6.wav Bicycle bell simple with light resonance tuned in A6 France 00:21.682 24 96000 2 Bell Bicycle Bell FAUN-21 Bell Bicycle bell hit very resonant long tuned in C7.wav Bicycle bell polished with long resonance tuned in C7 France 00:50.116 24 96000 2 Bell Bicycle Bell FAUN-21 Bell Chime bell medium continuous movement at multiple tone.wav Chime small ball in metal from India with multiple tone long and continuous movement shake France 00:23.722 24 96000 2 Bell Chime Bell FAUN-21 Bell Chime bell medium continuous movement long and strong at multiple tone.wav Chime small ball in metal from India with multiple tone long and continuous movement shake France 00:51.274 24 96000 2 Bell Chime Bell FAUN-21 Bell Chime bell medium short movement at multiple tone.wav Chime small ball in metal from India with multiple tone short movement shake France 00:33.610 24 96000 2 Bell Chime Bell FAUN-21 Bell Chime bell medium slow continuous movement at multiple tone.wav Chime small ball in metal from India with multiple tone long and soft continuous movement shake France 00:39.834 24 96000 2 Bell Chime Bell FAUN-21 Bell Chime bell small short movement at multiple tone.wav Chime small ball in metal from India with multiple tone short movement shake France -

Technology, Labor, and Mechanized Bodies in Victorian Culture
Syracuse University SURFACE English - Dissertations College of Arts and Sciences 12-2012 The Body Machinic: Technology, Labor, and Mechanized Bodies in Victorian Culture Jessica Kuskey Syracuse University Follow this and additional works at: https://surface.syr.edu/eng_etd Part of the English Language and Literature Commons Recommended Citation Kuskey, Jessica, "The Body Machinic: Technology, Labor, and Mechanized Bodies in Victorian Culture" (2012). English - Dissertations. 62. https://surface.syr.edu/eng_etd/62 This Dissertation is brought to you for free and open access by the College of Arts and Sciences at SURFACE. It has been accepted for inclusion in English - Dissertations by an authorized administrator of SURFACE. For more information, please contact [email protected]. ABSTRACT While recent scholarship focuses on the fluidity or dissolution of the boundary between body and machine, “The Body Machinic” historicizes the emergence of the categories of “human” and “mechanical” labor. Beginning with nineteenth-century debates about the mechanized labor process, these categories became defined in opposition to each other, providing the ideological foundation for a dichotomy that continues to structure thinking about our relation to technology. These perspectives are polarized into technophobic fears of dehumanization and machines “taking over,” or technological determinist celebrations of new technologies as improvements to human life, offering the tempting promise of maximizing human efficiency. “The Body Machinic” argues that both sides to this dichotomy function to mask the ways the apparent body-machine relation is always the product of human social relations that become embedded in the technologies of the labor process. Chapter 1 identifies the emergence of this dichotomy in the 1830s “Factory Question” debates: while critics of the factory system described workers as tools appended to monstrous, living machines, apologists claimed large-scale industrial machinery relieved human toil by replicating the laboring body in structure and function. -
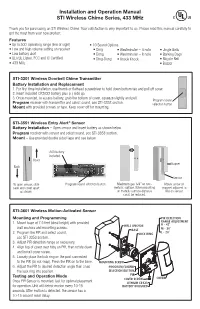
Installation and Operation Manual STI Wireless Chime Series, 433 Mhz
Installation and Operation Manual STI Wireless Chime Series, 433 MHz Thank you for purchasing an STI Wireless Chime. Your satisfaction is very important to us. Please read this manual carefully to get the most from your new product. Features • Up to 500’ operating range (line of sight) • 10 Sound Options • Low and high volume setting on receiver • Ding • Westminster – 4 note • Jingle Bells • Low battery alert • Dong • Westminster – 8 note • Barking Dogs • UL/cUL Listed. FCC and IC Certified • Ding-Dong • Knock Knock • Bicycle Bell • 433 MHz • Buzzer STI-3301 Wireless Doorbell Chime Transmitter Battery Installation and Replacement 1. For first time installation, use thumb or flathead screwdriver to hold down bottom tab and pull off cover. 2. Insert included CR2032 battery plus (+) side up. 3. Once mounted, to access battery, grab the bottom of cover, squeeze slightly and pull. Program/sound Program receiver with transmitter and select sound, see STI-3353 section. selection button Mount with provided screws or tape. Keep cover off for mounting. STI-3551 Wireless Entry Alert® Sensor Battery Installation – Open sensor and insert battery as shown below. Program receiver with sensor and select sound, see STI-3353 section. Mount – Use provided double sided tape and see below. AAA battery included. Cover Magnet Back Sensor To open sensor, slide Program/sound selection button. Maximum gap 5/8” on non- Mount arrow on back and cover apart metallic surface. When mounting magnet adjacent to as shown. on metallic surface distance line on sensor. could be reduced. STI-3601 Wireless Motion-Activated Sensor Mounting and Programming PIR DETECTION RANGE ADJUSTMENT 1. -

Sound-Source Recognition: a Theory and Computational Model
Sound-Source Recognition: A Theory and Computational Model by Keith Dana Martin B.S. (with distinction) Electrical Engineering (1993) Cornell University S.M. Electrical Engineering (1995) Massachusetts Institute of Technology Submitted to the department of Electrical Engineering and Computer Science in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Electrical Engineering and Computer Science at the MASSACHUSETTS INSTITUTE OF TECHNOLOGY June, 1999 © Massachusetts Institute of Technology, 1999. All Rights Reserved. Author .......................................................................................................................................... Department of Electrical Engineering and Computer Science May 17, 1999 Certified by .................................................................................................................................. Barry L. Vercoe Professor of Media Arts and Sciences Thesis Supervisor Accepted by ................................................................................................................................. Professor Arthur C. Smith Chair, Department Committee on Graduate Students _____________________________________________________________________________________ 2 Sound-source recognition: A theory and computational model by Keith Dana Martin Submitted to the Department of Electrical Engineering and Computer Science on May 17, 1999, in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Electrical Engineering -

Objects That Sound
Objects that Sound Relja Arandjelovi´c1 and Andrew Zisserman1;2 1 DeepMind 2 VGG, Department of Engineering Science, University of Oxford Abstract. In this paper our objectives are, first, networks that can em- bed audio and visual inputs into a common space that is suitable for cross-modal retrieval; and second, a network that can localize the ob- ject that sounds in an image, given the audio signal. We achieve both these objectives by training from unlabelled video using only audio-visual correspondence (AVC) as the objective function. This is a form of cross- modal self-supervision from video. To this end, we design new network architectures that can be trained for cross-modal retrieval and localizing the sound source in an image, by using the AVC task. We make the following contributions: (i) show that audio and visual embeddings can be learnt that enable both within-mode (e.g. audio-to-audio) and between-mode retrieval; (ii) explore various architectures for the AVC task, including those for the visual stream that ingest a single image, or multiple images, or a single image and multi-frame optical flow; (iii) show that the semantic object that sounds within an image can be localized (using only the sound, no motion or flow information); and (iv) give a cautionary tale on how to avoid undesirable shortcuts in the data preparation. 1 Introduction arXiv:1712.06651v2 [cs.CV] 25 Jul 2018 There has been a recent surge of interest in cross-modal learning from images and audio [1{4]. One reason for this surge is the availability of virtually unlimited training material in the form of videos (e.g. -

Radical Environmentalism
Anyone who will read the anarchist and radical environmentalist journals will see that opposition to the industrial-technological system is widespread and growing. Theodore Kaczynski, aka the Unabomber Radical Environmentalism Green religion and the politics of radical environmentalism from Earth First! and the Earth Liberation Front to the Unabomber and anti-globalization resistance Department of Religion The University of Florida Spring 2017 Wednesdays, 4:05-7:05 p.m. Offered with both undergraduate & graduate sections: REL 3938, Section 1E77 RLG 6167, Section 1E76 Instructor: Dr./Prof. Bron Taylor Office: Anderson 121 Office Hours: Wednesdays, 1:30-3:00 p.m. (and by appointment) ! Course Gateways: Syllabus (The additional, direct access links, below, are also found in this syllabus.) Schedule of Readings and Assignments Bron Taylor’s Print History and Digital Archive of Earth First!, Wild Earth, Live Wild or Die, and Alarm Bibliography Documentary Readings WWW Sites Music Anyone who will read the anarchist and radical environmentalist journals will see that opposition to the industrial-technological system is widespread and growing Theodore Kaczynski, aka the Unabomber Course Description Radical Environmentalism Critical examination of the emergence . from Earth First! & the and social impacts of Radical Earth Liberation Front to Environmentalism, with special the Unabomber and the attention to its religious and moral anti-globalization resistance dimensions, and the ecological and political perceptions that undergird its Fall 2017 controversial strategies designed to Wednesdays 4:05-7:05p.m. arrest environmental degradation. Rel 3938 (undergraduate section) Rlg 6167 (graduate section) Course Overview and Objectives Instructor: Dr./Prof. Bron Taylor The University of Florida During the 1980s and much of the Office: Anderson 121; 1990s and beyond, thousands of Office Hours environmental activists were arrested W: 1:30-3:00 p.m. -

Resistance to New Technology and Its Effects on Nuclear Power, Information Technology and Biotechnology
Martin Bauer Resistance to new technology and its effects on nuclear power, information technology and biotechnology Book section (Published Version) Original citation: Originally published in Bauer, M. (ed.), Resistance to new technology: nuclear power, information technology and biotechnology. Cambridge, UK : Cambridge University Press, 1995, pp. 1-42. ISBN 9780521599481 © 2012 Cambridge University Press This version available at: http://eprints.lse.ac.uk/39607/ Available in LSE Research Online: March 2012 LSE has developed LSE Research Online so that users may access research output of the School. Copyright © and Moral Rights for the papers on this site are retained by the individual authors and/or other copyright owners. Users may download and/or print one copy of any article(s) in LSE Research Online to facilitate their private study or for non-commercial research. You may not engage in further distribution of the material or use it for any profit-making activities or any commercial gain. You may freely distribute the URL (http://eprints.lse.ac.uk) of the LSE Research Online website. Cambridge Books Online http://ebooks.cambridge.org Resistance to New Technology Nuclear Power, Information Technology and Biotechnology Edited by Martin Bauer Book DOI: http://dx.doi.org/10.1017/CBO9780511563706 Online ISBN: 9780511563706 Hardback ISBN: 9780521455183 Paperback ISBN: 9780521599481 Chapter 1 - Resistance to new technology and its effects on nuclear power, information technology and biotechnology pp. 1-42 Chapter DOI: http://dx.doi.org/10.1017/CBO9780511563706.002 Cambridge University Press -1- Resistance to new technology and its effects on nuclear power, information technology and biotechnology MARTIN BAUER Basic questions The word 'resistance' has become unsuitable for use in the context of new technology. -

Transhumanism
T ranshumanism - Wikipedia, the free encyclopedia http://en.wikipedia.org/w/index.php?title=T ranshum... Transhumanism From Wikipedia, the free encyclopedia See also: Outline of transhumanism Transhumanism is an international Part of Ideology series on intellectual and cultural movement supporting Transhumanism the use of science and technology to improve human mental and physical characteristics Ideologies and capacities. The movement regards aspects Abolitionism of the human condition, such as disability, Democratic transhumanism suffering, disease, aging, and involuntary Extropianism death as unnecessary and undesirable. Immortalism Transhumanists look to biotechnologies and Libertarian transhumanism other emerging technologies for these Postgenderism purposes. Dangers, as well as benefits, are Singularitarianism also of concern to the transhumanist Technogaianism [1] movement. Related articles The term "transhumanism" is symbolized by Transhumanism in fiction H+ or h+ and is often used as a synonym for Transhumanist art "human enhancement".[2] Although the first known use of the term dates from 1957, the Organizations contemporary meaning is a product of the 1980s when futurists in the United States Applied Foresight Network Alcor Life Extension Foundation began to organize what has since grown into American Cryonics Society the transhumanist movement. Transhumanist Cryonics Institute thinkers predict that human beings may Foresight Institute eventually be able to transform themselves Humanity+ into beings with such greatly expanded Immortality Institute abilities as to merit the label "posthuman".[1] Singularity Institute for Artificial Intelligence Transhumanism is therefore sometimes Transhumanism Portal · referred to as "posthumanism" or a form of transformational activism influenced by posthumanist ideals.[3] The transhumanist vision of a transformed future humanity has attracted many supporters and detractors from a wide range of perspectives. -

Christian Cyborgs: a Plea for a Moderate Transhumanism
Faith and Philosophy: Journal of the Society of Christian Philosophers Volume 34 Issue 3 Article 5 7-1-2017 Christian Cyborgs: A Plea for a Moderate Transhumanism Benedikt Paul Göcke Follow this and additional works at: https://place.asburyseminary.edu/faithandphilosophy Recommended Citation Göcke, Benedikt Paul (2017) "Christian Cyborgs: A Plea for a Moderate Transhumanism," Faith and Philosophy: Journal of the Society of Christian Philosophers: Vol. 34 : Iss. 3 , Article 5. DOI: 10.5840/faithphil201773182 Available at: https://place.asburyseminary.edu/faithandphilosophy/vol34/iss3/5 This Article is brought to you for free and open access by the Journals at ePLACE: preserving, learning, and creative exchange. It has been accepted for inclusion in Faith and Philosophy: Journal of the Society of Christian Philosophers by an authorized editor of ePLACE: preserving, learning, and creative exchange. CHRISTIAN CYBORGS: A PLEA FOR A MODERATE TRANSHUMANISM Benedikt Paul Göcke Should or shouldn’t Christians endorse the transhumanist agenda of chang- ing human nature in ways fitting to one’s needs? To answer this question, we first have to be clear on what precisely the thesis of transhumanism en- tails that we are going to evaluate. Once this point is clarified, I argue that Christians can in principle fully endorse the transhumanist agenda because there is nothing in Christian faith that is in contradiction to it. In fact, given certain plausible moral assumptions, Christians should endorse a moderate enhancement of human nature. I end with a brief case study that analyses the theological implications of the idea of immortal Christian cyborgs. I argue that the existence of Christian cyborgs who know no natural death has no impact on the Christian hope of immortality in the presence of God. -

TECHNOPHOBIA! Science Fiction Visions of Posthuman Technology
TECHNOPHOBIA! science fiction visions of posthuman technology Daniel Dinello university of texas press Austin Frontispiece: Human under the domination of corporate science and autonomous technology (Metropolis, 1926. Courtesy Photofest). Copyright © 2005 by the University of Texas Press All rights reserved Printed in the United States of America First edition, 2005 Requests for permission to reproduce material from this work should be sent to Permissions, University of Texas Press, P.O. Box 7819, Austin, TX 78713-7819. www.utexas.edu/utpress/about/bpermission.html The paper used in this book meets the minimum requirements of ansi/niso z39.48-1992 (r1997) (Permanence of Paper). library of congress cataloging-in-publication data Dinello, Daniel Technophobia! : science fiction visions of posthuman technology / by Daniel Dinello. — 1st ed. p. cm. Includes bibliographical references and index. isbn 0-292-70954-4 (cl. : alk. paper) — isbn 0-292-70986-2 (pbk. : alk. paper) 1. Science fiction—History and criticism. 2. Technology in literature. I. Title. pn3433.6.d56 2005 809.3'876209356—dc22 2005019190 NINE Technology Is a Virus machine plague virus horror: technophobia and the return of repressed flesh Technophiliacs want to escape from the body—that mor- tal hunk of animated meat. But even while devising the mode of their disembodiment, a tiny terror gnaws inside them—virus fear. The smallest form of life, viruses are parasites that live and reproduce by penetrating and commandeering the cell machinery of their hosts, often killing them and moving on to others. ‘‘As the means become available for the technology- creating species to manipulate the genetic code that gave rise to it,’’ says techno-prophet Ray Kurzweil, ‘‘...newvirusescanemergethroughacci- dent and/or hostile intention with potentially mortal consequences.’’1 The techno-religious vision of immortality represses horrific images of mutilated bodies and corrupted flesh that haunt our collective nightmares in the science fiction subgenre of virus horror.