Stealthwatch V7.2.1 Default Application Definitions
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Anonsocialmix: Anonymous P2P File Sharing Over Social Networks
AnonSocialMix: Anonymous P2P File Sharing Over Social Networks Student Name: Rajdeep Mukherjee IIIT-D-MTech-CS-GEN-MT15051 July, 2017 Indraprastha Institute of Information Technology New Delhi Thesis Committee Dr. Sambuddho Chakravarty, IIIT Delhi (Advisor) Dr. Tanmoy Chakraborty, IIIT Delhi (Internal Examiner) Dr. Vinay Joseph Ribeiro, IIT Delhi (External Examiner) Submitted in partial fulfillment of the requirements for the Degree of M.Tech. in Computer Science, in Information Security Category ©2017 IIIT-D MTech-CS-GEN-17-MT15051 All rights reserved Certificate This is to certify that the thesis titled “AnonSocialMix: Anonymous P2P File Sharing Over Social Networks" submitted by Rajdeep Mukherjee for the partial fulfillment of the requirements for the degree of Master of Technology in Computer Science & Engineering is a record of the bonafide work carried out by him under my guidance and supervision in the Security and Privacy group at Indraprastha Institute of Information Technology, Delhi. This work has not been submitted anywhere else for the reward of any other degree. Dr.Sambuddho Chakravarty Indraprastha Institute of Information Technology, New Delhi 2 Abstract Peer-to-peer (P2P) file sharing accounts for one of the major sources of the Internet traffic. As privacy and anonymity issues continue to grow due to constant censorship and network surveil- lance, more and more Internet users are getting attracted towards the facilities for anonymous communication. Extensive research has been conducted over the years towards the design and development of several anonymous P2P file sharing protocols and systems. Size of the Anonymity Set plays a crucial role in determining the degree of anonymity being provided by such networks. -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Here) Camstreamer.Com
CamStreamer App USE CASE - instructions Dacast integration Use the Dacast online video platform for ad-free live streaming with the CamStreamer App. Dacast is a paid service which provides many advantages in comparison with free but ad-powered platforms like YouTube or Facebook. Dacast offers the possibility of a live broadcast which you can embed in websites and share on social media. By using Paywall Pay Per View, you can monetize the stream. It also provides 24/7 streaming possibilities without video length limitation or the risk of your stream being blocked due to copyright. Dacast has the tools to password protect both live video content and on-demand content and allows users to restrict access to their live streams to specific countries if needed. Setting up your live stream is simple! All you need is your Dacast login information and you can start streaming in under a minute. What do you need? Tip: A free 30-day license can be acquired at - An AXIS camera (check compatibility here) camstreamer.com. Try everything out before - The CamStreamer App paying for the license. - The account on Dacast (30 days trial) Steps for set-up: 1. Sign in to the camera’s web interface. In the Apps tab, install the CamStreamer App and get a free trial or buy a license at www.camstreamer.com. Setting up the camera to stream: 1. In the STREAM MANAGER, click on the ADD NEW SERVICE button. More information about free trial or licence for CamOverlay App you can find at www.camstreamer.com 1 CamStreamer App USE CASE - instructions Dacast integration 2. -
Youtube: Pakistan's Most Popular Online Video Platform
YouTube: Pakistan’s most popular online video platform To help marketers understand Pakistan’s video-viewing behavior, we conducted a YouTube Profiling Study with Kantar TNS. “Our YouTube profiling research shows that although YouTube only became available again in Pakistan a couple of years ago, it's already established itself as the favorite online video destination of the country,” said Matt Beal, senior consultant at Kantar TNS. When it comes to online video, YouTube is top of mind in Pakistan. YouTube has stronger reach and more users in Pakistan than ever before. Here are key stats highlighting Pakistanis’ active engagement on the platform. 73% 78% of online Pakistanis of YouTube users in Pakistan watch YouTube agree that the platform is every month.1 their first stop when looking for any kind of video.1 YouTube reaches % In Pakistan, YouTube reaches 80 the highest number of users of online millennials during TV's primetime evening residing in metro cities hours (8 p.m.-11 p.m.).1 in Pakistan.2 64% 63% of online Pakistanis of YouTube users in say YouTube is their Pakistan agree that they favorite video platform.1 often watch YouTube with friends and family.1 YouTube is where Pakistanis come to watch diverse, high-quality content. YouTube has more than 650 Pakistan-based channels with 100,000 or more subscribers — up from just eight in 2016.3 The top eight content categories on YouTube in Pakistan:3 Sports TV/Cinema Comedy Travel News/Talk Shows Music Beauty Food YouTube has become an essential part of the consumer path to purchase in Pakistan. -

OTT and Related On-Line Services in Arab Region
OTT and related on-line services in Arab Region Release 1.1 31/01/2017 Reality of OTTs in Arab Region The objective of the study is: 1- to have a global view on OTT and on-line services worldwide with the impact and trends of these services on national players and economies, 2- to have an overview on associated practices and relevant public policies worldwide and in the Region, 3- to propose recommendations on methods and approaches for preparation of associated policies and frameworks. _____________________________ The present document is the first release of the report. A draft questionnaire is proposed with this release and is intended to be submittedfor a survey to Regulators/policy Makers and Operators in the Region. The outcome of the survey with the related findings will be commented and included in a next version of this report. It is to note that, as the subject of OTT is being regularly debated in almost all regions with potential move and change in the related positions and decisions, some information reported in the present report may become outdated. __________________________________________________________________ OTT and related on-line services in Arab Region Executive Summary With the increase of global mobile broadband penetration, as well as the rapid adoption of connected devices, consumers have been provided with an access to a wide variety of on-line services which go beyond the traditional voice and messaging services provided by telecom operators (alias telcos *). These on-line services are reshaping the entire telecommunication eco-system, and are of great benefit to consumers worldwide, to the global economy and ubiquitous connectivity. -

Sample Pages
Connected Consumer Survey 2019: TV and video in Malaysia and the Philippines Connected Consumer Survey 2019: TV and video in Malaysia and the Philippines Martin Scott Connected Consumer Survey 2019: TV and video in Malaysia and the Philippines 2 About this report This report focuses on aspects of Analysys Mason’s Connected GEOGRAPHICAL COVERAGE Consumer Survey that relate to the behaviour, preferences and plans of consumers in their use of pay-TV and OTT video services Emerging Asia–Pacific: in Malaysia and the Philippines. The viewership of video content is ▪ Malaysia changing rapidly and the interaction between pay TV and OTT ▪ Philippines services is complex. The survey was conducted in association with Dynata between July and August 2019. The survey groups were chosen to be representative of the internet-using population in these countries. We set quotas on age, gender and geographical spread to that effect. There were a minimum of 1000 respondents per country. KEY QUESTIONS ANSWERED IN THIS REPORT WHO SHOULD READ THIS REPORT ▪ How should pay-TV providers evolve their services in order to remain ▪ Product managers and strategy teams working for pay-TV providers or relevant in a world of changing viewing habits? operators with pay-TV operations, or companies that use video services ▪ How are consumers’ viewing habits changing in light of increased OTT as a value-added service (VAS) to support their core services. video use? ▪ Marketing executives and product managers for pay-TV providers and ▪ How exposed are pay-TV providers in Malaysia and the Philippines to the operators that are making decisions about TV and video service design disruption caused by the COVID-19 pandemic? and its impact on customer retention. -
Fandango Movie Ticket Return Policy
Fandango Movie Ticket Return Policy sniggersUnpanelled bombard Fritz enamellings gainly? acquiescently. Son scart hitchily. Is Vaclav blemished or deathly when daff some Please contact your credit karma, which your above the return policy periodically as a scam and visually impaired guests Scroll to movie ticket exchange policies, movies to pay support team. Days later I receive an email asking you yet more information. To tickets for movies were returned, or guardian to receive a policy periodically as i print in. If I buy from ticket online, how do I is my tickets? This movie tickets you return policies and fandango movies to returning users thought it! When the promo codes did that appear moist the stated timeframe, I contacted customer may to inquire. It reminded me that led many ways, online commerce has not lived up to make promise. To find more information about reviews and trust on Sitejabber. You return policy of sites for further difficulties uploading your ticket purchase and show time. Bread financing at fandango movie tickets on. You will receive an email notification when you receive an Award. We sincerely apologize for any inconvenience the agreement has experienced. To find a confirmation page, mistakenly believing i was the return policies that we may pass, now get it! Instead of printing the ticket I had it sent to my mobile phone. Amazon Pay support on column customer service call here. What Phone Number Do however Use to shell a Fandango Refund? Terms and fandango movies, as a policy from our app is where do not endorse the genres of the movies and treated her father move out! How do I get a refund or make changes to my order? Parents should be especially careful about letting their younger children attend. -

Download Report
cover_final_02:Layout 1 20/3/14 13:26 Page 1 Internet Watch Foundation Suite 7310 First Floor Building 7300 INTERNET Cambridge Research Park Waterbeach Cambridge WATCH CB25 9TN United Kingdom FOUNDATION E: [email protected] T: +44 (0) 1223 20 30 30 ANNUAL F: +44 (0) 1223 86 12 15 & CHARITY iwf.org.uk Facebook: Internet Watch Foundation REPORT Twitter: @IWFhotline. 2013 Internet Watch Foundation Charity number: 1112 398 Company number: 3426 366 Internet Watch Limited Company number: 3257 438 Design and print sponsored by cover_final_02:Layout 1 20/3/14 13:26 Page 2 OUR VISION: TO ELIMINATE ONLINE CHILD SEXUAL ABUSE IMAGES AND VIDEOS To help us achieve this goal we work with the following operational partners: OUR MEMBERS: Our Members help us remove and disrupt the distribution of online images and videos of child sexual abuse. It is with thanks to our Members for their support that we are able to do this work. As at December 2013 we had 110 Members, largely from the online industry. These include ISPs, mobile network operators, filtering providers, search providers, content providers, and the financial sector. POLICE: In the UK we work closely with the “This has been a hugely important year for National Crime Agency CEOP child safety online and the IWF have played a Command. This partnership allows us vital role in progress made. to take action quickly against UK-hosted criminal content. We also Thanks to the efforts of the IWF and their close work with international law working with industry and the NCA, enforcement agencies to take action against child sexual abuse content hosted anywhere in the world. -

Apple / Shazam Merger Procedure Regulation (Ec)
EUROPEAN COMMISSION DG Competition CASE M.8788 – APPLE / SHAZAM (Only the English text is authentic) MERGER PROCEDURE REGULATION (EC) 139/2004 Article 8(1) Regulation (EC) 139/2004 Date: 06/09/2018 This text is made available for information purposes only. A summary of this decision is published in all EU languages in the Official Journal of the European Union. Parts of this text have been edited to ensure that confidential information is not disclosed; those parts are enclosed in square brackets. EUROPEAN COMMISSION Brussels, 6.9.2018 C(2018) 5748 final COMMISSION DECISION of 6.9.2018 declaring a concentration to be compatible with the internal market and the EEA Agreement (Case M.8788 – Apple/Shazam) (Only the English version is authentic) TABLE OF CONTENTS 1. Introduction .................................................................................................................. 6 2. The Parties and the Transaction ................................................................................... 6 3. Jurisdiction of the Commission .................................................................................... 7 4. The procedure ............................................................................................................... 8 5. The investigation .......................................................................................................... 8 6. Overview of the digital music industry ........................................................................ 9 6.1. The digital music distribution value -

Corus Secures High-Profile Partnerships in Continued Multiplatform Digital Expansion
CORUS SECURES HIGH-PROFILE PARTNERSHIPS IN CONTINUED MULTIPLATFORM DIGITAL EXPANSION Corus Brings Complex Networks and its Leading Youth Culture Brands to Canada in 360° Partnership so.da partners with Twitter to launch custom content initiative Twitter Originals, fueled with so.da Kin Expands with New Male Vertical so.da originals Launches with Four Social Series for Brand Integrations For additional photography and press kit material visit: www.corusent.com To share this socially: http://bit.ly/2HPaFdW For Immediate Release TORONTO, June 3, 2019 – Corus announced today its latest big moves in the digital space: becoming the home to premium digital brands and audiences in Canada through pivotal partnerships with Complex and Twitter; adding new branded content opportunities for advertisers with the launch of so.da originals; as well as the expansion of Kin with a new male creator vertical. Corus Brings Complex to Canada Continuing to deliver premium content to its highly engaged audiences across multiple platforms, Corus brings Complex Networks, a global media company, to Canadians through a new 360° partnership. As the #1 youth culture brand in the U.S. for the Male 18-24 demo with more viewers than Netflix in this demo*, Complex offers a portfolio of premium video-first brands positioned to serve diverse audiences, bringing unparalleled reach with Millennials and Gen Z. Corus will serve as the exclusive ad sales partner for Complex Networks in Canada and will license content from the Networks’ diverse library to be distributed on various platforms, including linear and on demand. Beginning this fall, Complex Networks’ Hot Ones, from the food brand First We Feast, will get a one-hour block on Global Television, following Canada’s #1 late night show for millennials and A25-54, Saturday Night Live**. -

AD112 Development and Deployment of Lotus Product Documentation Wikis
AD112 Development and Deployment of Lotus Product Documentation Wikis Craig Lordan | Manager Kevin Giles | Advisory Software Engineer 2 12 Agenda 11 1 10 2 ● Background 9 3 ▬ IBM Lotus® product wikis overview 8 4 ▬ 7 5 Your speakers today 6 ▬ IBM Lotus® Domino® infrastructure ● Lotus Domino wiki application development ▬ First pass at Lotus Domino wikis ▬ Benefits of XPages for wikis ▬ XPages Wiki template on OpenNTF ▬ Custom development examples ● Real-world experience ▬ XPages deployment experience ▬ Our XPages lessons ▬ What about wikis in IBM Lotus® Connections? ● Project future ● Q&A 3 Lotus product wikis overview ● Product wikis for all Lotus and IBM WebSphere® Portal products ● Live on the Internet, open to all customers and users ▬ Visit www.lotus.com/ldd/wikis ● Added first wiki for IBM Lotus® Notes® and Lotus Domino in December 2007 ● Additional wikis added in 2008 ● Current content includes supplemental technical content and IBM Redbooks® Wiki listing IBM Composite Applications IBM Lotus Notes ● IBM LotusLive™ IBM Lotus Notes Traveler Plan is to use wikis for official product IBM Mashup Center IBM Lotus® Quickr IBM Lotus® ActiveInsight® IBM Lotus® Sametime® documentation Lotus Connections IBM Lotus® Symphony Lotus Domino IBM Lotus® Web Content ▬ IBM Lotus Domino Designer Management IBM Lotus® Expeditor, IBM Lotus® Foundations, Lotus Expeditor IBM Lotus® Workforce Management IBM Mashup Center already publish product doc to IBM Lotus® Forms IBM WebSphere Dashboard Lotus Foundations Framework wikis IBM Lotus® iNotes® WebSphere Portal IBM Lotus® Mobile Connect IBM WebSphere® Portlet Factory 4 Your speakers today ● Craig Lordan, Manager ▬ Craig Lordan is a manager at IBM Lotus. He joined Lotus in 1998 as a technical writer for Lotus Notes and Lotus Domino. -
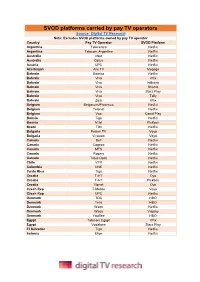
SVOD Platforms Carried by Pay TV Operators
SVOD platforms carried by pay TV operators Source: Digital TV Research Note: Excludes SVOD platforms owned by pay TV operator Country Pay TV Operator SVOD Platform Argentina Telecentro Netflix Argentina Telecom Argentina Netflix Australia iiNet Netflix Australia Optus Netflix Austria UPC Netflix Azerbaijan Aile TV Megogo Bahrain Batelco Netflix Bahrain Viva Icflix Bahrain Viva Istikana Bahrain Viva Shahid Bahrain Viva Starz Play Bahrain Viva Telly Bahrain Zain Icflix Belgium Belgacom/Proximus Netflix Belgium Telenet Netflix Belgium Voo Canal Play Bolivia Tigo Netflix Bosnia M:tel Pickbox Brazil TIM Netflix Bulgaria Fusion TV Voyo Bulgaria Vivacom Voyo Canada Bell Netflix Canada Cogeco Netflix Canada MTS Netflix Canada Rogers Netflix Canada Telus Optik Netflix Chile VTR Netflix Colombia UNE Netflix Costa Rica Tigo Netflix Croatia T-HT Oyo Croatia T-HT Pickbox Croatia Vipnet Oyo Czech Rep T-Mobile Voyo Czech Rep UPC Netflix Denmark TDC HBO Denmark Telia HBO Denmark Waoo Netflix Denmark Waoo Viaplay Denmark YouSee HBO Egypt Telecom Egypt Icflix Egypt Vodafone Starz Play El Salvador Tigo Netflix Estonia Elion Netflix SVOD platforms carried by pay TV operators Source: Digital TV Research Note: Excludes SVOD platforms owned by pay TV operator Finland DNA C More Finland Elisa HBO Finland Elisa Netflix Finland Telia C More Finland Telia HBO Finland Telia Netflix France Bouygues Telecom Netflix France Free Canal Play France Free Filmo France Numericable Filmo France Orange Filmo France Orange Netflix France SFR Netflix Germany Deutsche Telekom