―A Brief View of Computer Network Topology for Data Communication and Networking‖
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Network Topologies Topologies
Network Topologies Topologies Logical Topologies A logical topology describes how the hosts access the medium and communicate on the network. The two most common types of logical topologies are broadcast and token passing. In a broadcast topology, a host broadcasts a message to all hosts on the same network segment. There is no order that hosts must follow to transmit data. Messages are sent on a First In, First Out (FIFO) basis. Token passing controls network access by passing an electronic token sequentially to each host. If a host wants to transmit data, the host adds the data and a destination address to the token, which is a specially-formatted frame. The token then travels to another host with the destination address. The destination host takes the data out of the frame. If a host has no data to send, the token is passed to another host. Physical Topologies A physical topology defines the way in which computers, printers, and other devices are connected to a network. The figure provides six physical topologies. Bus In a bus topology, each computer connects to a common cable. The cable connects one computer to the next, like a bus line going through a city. The cable has a small cap installed at the end called a terminator. The terminator prevents signals from bouncing back and causing network errors. Ring In a ring topology, hosts are connected in a physical ring or circle. Because the ring topology has no beginning or end, the cable is not terminated. A token travels around the ring stopping at each host. -

Introducing Zigbee Theory and Practice Into Information and Computer Technology Disciplines
AC 2007-1072: INTRODUCING ZIGBEE THEORY AND PRACTICE INTO INFORMATION AND COMPUTER TECHNOLOGY DISCIPLINES Crystal Bateman, Brigham Young University Crystal Bateman is an Undergraduate Student at BYU studying Information Technology. Her academic interests include ubiquitous technologies and usability. She is currently finishing an honors thesis on using mobile ZigBee motes in a home environment, and enjoying life with her husband and two daughters Janell Armstrong, Brigham Young University Janell Armstrong is a Graduate Student in Information Technology at BYU. Her interests are in ZigBee and public key infrastructure. She has three years experience as a Teacher's Assistant. Student memberships include IEEE, IEEE-CS, ACM, SWE, ASEE. C. Richard Helps, Brigham Young University Richard Helps is the Program Chair of the Information Technology program at BYU and has been a faculty member in the School of Technology since 1986. His primary scholarly interests are in embedded and real-time computing and in technology education. He also has interests in human-computer interfacing. He has been involved in ABET accreditation for about 8 years and is a Commissioner of CAC-ABET and a CAC accreditation team chair. He spent ten years in industry designing industrial automation systems and in telecommunications. Professional memberships include IEEE, IEEE-CS, ACM, SIGITE, ASEE. Page 12.982.1 Page © American Society for Engineering Education, 2007 Introducing ZigBee Theory and Practice into Information and Computer Technology Disciplines Abstract As pervasive computing turns from the desktop model to the ubiquitous computing ideal, the development challenges become more complex than simply connecting a peripheral to a PC. A pervasive computing system has potentially hundreds of interconnected devices within a small area. -

13 Embedded Communication Protocols
13 Embedded Communication Protocols Distributed Embedded Systems Philip Koopman October 12, 2015 © Copyright 2000-2015, Philip Koopman Where Are We Now? Where we’ve been: •Design • Distributed system intro • Reviews & process • Testing Where we’re going today: • Intro to embedded networking – If you want to be distributed, you need to have a network! Where we’re going next: • CAN (a representative current network protocol) • Scheduling •… 2 Preview “Serial Bus” = “Embedded Network” = “Multiplexed Wire” ~= “Muxing” = “Bus” Getting Bits onto the wire • Physical interface • Bit encoding Classes of protocols • General operation • Tradeoffs (there is no one “best” protocol) • Wired vs. wireless “High Speed Bus” 3 Linear Network Topology BUS • Good fit to long skinny systems – elevators, assembly lines, etc... • Flexible - many protocol options • Break in the cable splits the bus • May be a poor choice for fiber optics due to problems with splitting/merging • Was prevalent for early desktop systems • Is used for most embedded control networks 4 Star Network Topologies Star • Can emulate bus functions – Easy to detect and isolate failures – Broken wire only affects one node – Good for fiber optics – Requires more wiring; common for Star current desktop systems • Broken hub is catastrophic • Gives a centralized location if needed – Can be good for isolating nodes that generate too much traffic Star topologies increasing in popularity • Bus topology has startup problems in some fault scenarios • Safety critical control networks moving -

Survey of Important Issues in UAV Communications Networks
1 Survey of Important Issues in UAV Communication Networks Lav Gupta*, Senior Member IEEE, Raj Jain, Fellow, IEEE, and Gabor Vaszkun technology that can be harnessed for military, public and civil Abstract—Unmanned Aerial Vehicles (UAVs) have enormous applications. Military use of UAVs is more than 25 years old potential in the public and civil domains. These are particularly primarily consisting of border surveillance, reconnaissance and useful in applications where human lives would otherwise be strike. Public use is by the public agencies such as police, endangered. Multi-UAV systems can collaboratively complete missions more efficiently and economically as compared to single public safety and transportation management. UAVs can UAV systems. However, there are many issues to be resolved provide timely disaster warnings and assist in speeding up before effective use of UAVs can be made to provide stable and rescue and recovery operations when the public communication reliable context-specific networks. Much of the work carried out in network gets crippled. They can carry medical supplies to areas the areas of Mobile Ad Hoc Networks (MANETs), and Vehicular rendered inaccessible. In situations like poisonous gas Ad Hoc Networks (VANETs) does not address the unique infiltration, wildfires and wild animal tracking UAVs could be characteristics of the UAV networks. UAV networks may vary from slow dynamic to dynamic; have intermittent links and fluid used to quickly envelope a large area without risking the safety topology. While it is believed that ad hoc mesh network would be of the personnel involved. most suitable for UAV networks yet the architecture of multi-UAV UAVs come networks has been an understudied area. -

Topological Optimisation of Artificial Neural Networks for Financial Asset
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by LSE Theses Online The London School of Economics and Political Science Topological Optimisation of Artificial Neural Networks for Financial Asset Forecasting Shiye (Shane) He A thesis submitted to the Department of Management of the London School of Economics for the degree of Doctor of Philosophy. April 2015, London 1 Declaration I certify that the thesis I have presented for examination for the MPhil/PhD degree of the London School of Economics and Political Science is solely my own work other than where I have clearly indicated that it is the work of others (in which case the extent of any work carried out jointly by me and any other person is clearly identified in it). The copyright of this thesis rests with the author. Quotation from it is permitted, provided that full acknowledgement is made. This thesis may not be reproduced without the prior written consent of the author. I warrant that this authorization does not, to the best of my belief, infringe the rights of any third party. 2 Abstract The classical Artificial Neural Network (ANN) has a complete feed-forward topology, which is useful in some contexts but is not suited to applications where both the inputs and targets have very low signal-to-noise ratios, e.g. financial forecasting problems. This is because this topology implies a very large number of parameters (i.e. the model contains too many degrees of freedom) that leads to over fitting of both signals and noise. -

Networking Solutions for Connecting Bluetooth Low Energy Devices - a Comparison
292 3 MATEC Web of Conferences , 0200 (2019) https://doi.org/10.1051/matecconf/201929202003 CSCC 2019 Networking solutions for connecting bluetooth low energy devices - a comparison 1,* 1 1 2 Mostafa Labib , Atef Ghalwash , Sarah Abdulkader , and Mohamed Elgazzar 1Faculty of Computers and Information, Helwan University, Egypt 2Vodafone Company, Egypt Abstract. The Bluetooth Low Energy (BLE) is an attractive solution for implementing low-cost, low power consumption, short-range wireless transmission technology and high flexibility wireless products,which working on standard coin-cell batteries for years. The original design of BLE is restricted to star topology networking, which limits network coverage and scalability. In contrast, other competing technologies like Wi-Fi and ZigBee overcome those constraints by supporting different topologies such as the tree and mesh network topologies. This paper presents a part of the researchers' efforts in designing solutions to enable BLE mesh networks and implements a tree network topology which is not supported in the standard BLE specifications. In addition, it discusses the advantages and drawbacks of the existing BLE network solutions. During analyzing the existing solutions, we highlight currently open issues such as flooding-based and routing-based solutions to allow end-to-end data transmission in a BLE mesh network and connecting BLE devices to the internet to support the Internet of Things (IoT). The approach proposed in this paper combines the default BLE star topology with the flooding based mesh topology to create a new hybrid network topology. The proposed approach can extend the network coverage without using any routing protocol. Keywords: Bluetooth Low Energy, Wireless Sensor Network, Industrial Wireless Mesh Network, BLE Mesh Network, Direct Acyclic Graph, Time Division Duplex, Time Division Multiple Access, Internet of Things. -

Comparison of Network Topologies for Optical Fiber Communication
International Journal of Engineering Research & Technology (IJERT) ISSN: 2278-0181 Vol. 1 Issue 10, December- 2012 Comparison Of Network Topologies For Optical Fiber Communication Mr. Bhupesh Bhatia Ms. Ashima Bhatnagar Bhatia Department of Electronics and Communication, Department of Computer Science, Guru Prem Sukh Memorial College of Engineering, Tecnia Institute of Advanced Studies, Delhi Delhi Ms. Rashmi Ishrawat Department of Computer Science, Tecnia Institute of Advanced Studies, Delhi Abstract advent of the Information age. Optical In this paper, the various network topologies technologies can cost effectively meet have been compared. The signal is analyzed as it corporate bandwidth needs today and passes through each node in each of the network tomorrow. Internet connections offering topology. There is no appreciable signal degradation in the ring network. Also there is bandwidth on demand, to fiber on the increase in Quality factor i.e. signal keeps on LAN. Fiber to the home can provide true improving as it passes through the successiveIJERT IJERTbroadband connectivity for nodes. For the bus topology, the quality of signal telecommuters as well as converged goes on decreasing with increase in the number multimedia offerings for consumers [2]. of nodes and the power penalty goes on increasing. For the star topology, it is observed These different communication networks that received power values of each node at a can be configured in a number of same distance from the hub are same and the topologies. These include a bus, with or performance is same. For the tree topology, it is without a backbone, a star network, a observed that the performance is almost identical ring network, which can be redundant to the performance of ring topology, as signal quality is improved as it passes through the and/ or self-healing, or some successive nodes of the hierarchy. -

Optimizing the Topology of Bluetooth Wireless Personal Area Networks Marco Ajmone Marsan, Carla F
Optimizing the Topology of Bluetooth Wireless Personal Area Networks Marco Ajmone Marsan, Carla F. Chiasserini, Antonio Nucci, Giuliana Carello, Luigi De Giovanni Abstract— In this paper, we address the problem of determin- ing an optimal topology for Bluetooth Wireless Personal Area Networks (BT-WPANs). In BT-WPANs, multiple communication channels are available, thanks to the use of a frequency hopping technique. The way network nodes are grouped to share the same channel, and which nodes are selected to bridge traffic from a channel to another, has a significant impact on the capacity and the throughput of the system, as well as the nodes’ battery life- time. The determination of an optimal topology is thus extremely important; nevertheless, to the best of our knowledge, this prob- lem is tackled here for the first time. Our optimization approach is based on a model derived from constraints that are specific to the BT-WPAN technology, but the level of abstraction of the model is such that it can be related to the slave slave & bridge more general field of ad hoc networking. By using a min-max for- mulation, we find the optimal topology that provides full network master master & bridge connectivity, fulfills the traffic requirements and the constraints posed by the system specification, and minimizes the traffic load of Fig. 1. BT-WPAN topology. the most congested node in the network, or equivalently its energy consumption. Results show that a topology optimized for some traffic requirements is also remarkably robust to changes in the traffic pattern. Due to the problem complexity, the optimal so- Master and slaves send and receive traffic alternatively, so as lution is attained in a centralized manner. -

A Framework for Wireless Broadband Network for Connecting the Unconnected
A Framework for Wireless Broadband Network for Connecting the Unconnected Meghna Khaturia, Prasanna Chaporkar and Abhay Karandikar Department of Electrical Engineering, Indian Institute of Technology Bombay, Mumbai-400076 Email: fmeghnak,chaporkar,[email protected] Abstract—A significant barrier in providing affordable rural providing broadband in rural areas of India. Ashwini [6] broadband is to connect the rural and remote places to the optical and Aravind [7] are some other examples of rural network Point of Presence (PoP) over a distances of few kilometers. A testbeds deployed in India. Hop-Scotch is a long distance Wi- lot of work has been done in the area of long distance Wi- Fi networks. However, these networks require tall towers and Fi network based in UK [8]. LinkNet is a 52 node wireless high gain (directional) antennas. Also, they work in unlicensed network deployed in Zambia [9]. Also, there has been a band which has Effective Isotropically Radiated Power (EIRP) substantial research interest in designing the long distance Wi- limit (e.g. 1 W in India) which restricts the network design. In Fi based mesh networks for rural areas [10]–[12]. All these this work, we propose a Long Term Evolution-Advanced (LTE- efforts are based on IEEE 802.11 standard [13] in unlicensed A) network operating in TV UHF to connect the remote areas to the optical PoP. In India, around 100 MHz of TV UHF band i.e. 2:4 GHz or 5:8 GHz. When working with these band IV (470-585 MHz) is unused at any location and can frequency bands over a long distance point to point link, be put to an effective use in these areas [1]. -

Spectral Analysis of the Adjacency Matrix of Random Geometric Graphs
Spectral Analysis of the Adjacency Matrix of Random Geometric Graphs Mounia Hamidouche?, Laura Cottatellucciy, Konstantin Avrachenkov ? Departement of Communication Systems, EURECOM, Campus SophiaTech, 06410 Biot, France y Department of Electrical, Electronics, and Communication Engineering, FAU, 51098 Erlangen, Germany Inria, 2004 Route des Lucioles, 06902 Valbonne, France [email protected], [email protected], [email protected]. Abstract—In this article, we analyze the limiting eigen- multivariate statistics of high-dimensional data. In this case, value distribution (LED) of random geometric graphs the coordinates of the nodes can represent the attributes of (RGGs). The RGG is constructed by uniformly distribut- the data. Then, the metric imposed by the RGG depicts the ing n nodes on the d-dimensional torus Td ≡ [0; 1]d and similarity between the data. connecting two nodes if their `p-distance, p 2 [1; 1] is at In this work, the RGG is constructed by considering a most rn. In particular, we study the LED of the adjacency finite set Xn of n nodes, x1; :::; xn; distributed uniformly and matrix of RGGs in the connectivity regime, in which independently on the d-dimensional torus Td ≡ [0; 1]d. We the average vertex degree scales as log (n) or faster, i.e., choose a torus instead of a cube in order to avoid boundary Ω (log(n)). In the connectivity regime and under some effects. Given a geographical distance, rn > 0, we form conditions on the radius rn, we show that the LED of a graph by connecting two nodes xi; xj 2 Xn if their `p- the adjacency matrix of RGGs converges to the LED of distance, p 2 [1; 1] is at most rn, i.e., kxi − xjkp ≤ rn, the adjacency matrix of a deterministic geometric graph where k:kp is the `p-metric defined as (DGG) with nodes in a grid as n goes to infinity. -

Assortativity of Links in Directed Networks
Assortativity of links in directed networks Mahendra Piraveenan1, Kon Shing Kenneth Chung1, and Shahadat Uddin1 1Centre for Complex Systems Research, Faculty of Engineering and IT, The University of Sydney, NSW 2006, Australia Abstract— Assortativity is the tendency in networks where many technological and biological networks are slightly nodes connect with other nodes similar to themselves. De- disassortative, while most social networks, predictably, tend gree assortativity can be quantified as a Pearson correlation. to be assortative in terms of degrees [3], [5]. Recent work However, it is insufficient to explain assortative or disassor- defined degree assortativity for directed networks in terms tative tendencies of individual links, which may be contrary of in-degrees and out-degrees, and showed that an ensemble to the overall tendency in the network. In this paper we of definitions are possible in this case [6], [7]. define and analyse link assortativity in the context of directed It could be argued, however, that the overall assortativity networks. Using synthesised and real world networks, we tendency of a network may not be reflected by individual show that the overall assortativity of a network may be due links of the network. For example, it is possible that in a to the number of assortative or disassortative links it has, social network, which is overall assortative, some people the strength of such links, or a combination of both factors, may maintain their ‘fan-clubs’. In this situation, people who which may be reinforcing or opposing each other. We also have a great number of friends may be connected to people show that in some directed networks, link assortativity can who are less famous, or even loners. -
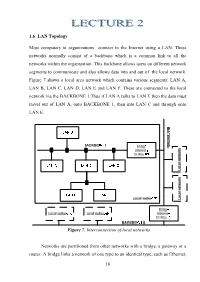
16 1.6 . LAN Topology Most Computers in Organizations Connect to the Internet Using a LAN. These Networks Normally Consist of A
1.6 . LAN Topology Most computers in organizations connect to the Internet using a LAN. These networks normally consist of a backbone which is a common link to all the networks within the organization. This backbone allows users on different network segments to communicate and also allows data into and out of the local network. Figure 7 shows a local area network which contains various segments: LAN A, LAN B, LAN C, LAN D, LAN E and LAN F. These are connected to the local network via the BACKBONE 1.Thus if LAN A talks to LAN E then the data must travel out of LAN A, onto BACKBONE 1, then into LAN C and through onto LAN E. Figure 7. Interconnection of local networks Networks are partitioned from other networks with a bridge, a gateway or a router. A bridge links a network of one type to an identical type, such as Ethernet, 16 or Token Ring to Token Ring. A gateway connects two dissimilar types of networks and routers operate in a similar way to gateways and can either connect to two similar or dissimilar networks. The key operation of a gateway, bridge or router is that they only allow data traffic through that is intended for another network, which is outside the connected network. This filters traffic and stops traffic, not intended for the network, from clogging-up the backbone. Most modern bridges, gateways and routers are intelligent and can automatically determine the topology of the network. Spanning-tree bridges have built-in intelligence and can communicate with other bridges.