Chapter 2. the Diplomatic Special Intelligence Section: Its Origins and History1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

WRAP Theses Shah 2016.Pdf
A Thesis Submitted for the Degree of PhD at the University of Warwick Permanent WRAP URL: http://wrap.warwick.ac.uk/81565 Copyright and reuse: This thesis is made available online and is protected by original copyright. Please scroll down to view the document itself. Please refer to the repository record for this item for information to help you to cite it. Our policy information is available from the repository home page. For more information, please contact the WRAP Team at: [email protected] warwick.ac.uk/lib-publications 1 2 ‘Secret Towns’: British Intelligence in Asia during the Cold War Nikita Shah A thesis submitted in partial fulfilment of the requirements for the degree of Doctor of Philosophy in Politics and International Studies Submitted March 2016 Department of Politics and International Studies University of Warwick 3 Table of Contents List of Abbreviations 1. Introduction 1 1.1 Chapter Outline 21 2. Methodology 25 2.1 Reading the Archive 25 2.2 A Lesson in Empire 31 2.3 Overcoming Archival Obstacles 38 3. Literature Review 49 3.1 Introduction 49 3.2 Definitional Debate – What is Intelligence? 51 3.3 The Special Relationship 63 3.4 The Special Intelligence Relationship in Asia 71 4. Historical Overview 80 4.1 The Special Intelligence Relationship in Asia 80 4.2 The Remnants of Empire 81 4.3 China, Hong Kong, and Taiwan 84 4.4 Burma 87 4.5 India 88 4.6 Indonesia 91 5. The Watchtower: British Intelligence in Hong Kong 95 5.1 Intelligence and Chaos in Hong Kong 101 5.2 Failed Networks and Blind Spots 106 5.3 British Intelligence and the Residue of Empire 112 4 5.4 Sino-Soviet Tensions and Espionage 128 5.5 The Special Intelligence Relationship in Hong Kong 132 6. -

Monday/Tuesday Playoff Schedule
2013 TUC MONDAY/TUESDAY PLAYOFF MASTER FIELD SCHEDULE Start End Hockey1 Hockey2 Hockey3 Hockey4 Hockey5 Ulti A Soccer 3A Soccer 3B Cricket E1 Cricket E2 Cricket N1 Cricket N2 Field X 8:00 9:15 MI13 MI14 TI13 TI14 TI15 TI16 MI1 MI2 MI3 MI4 MI15 MI16 9:20 10:35 MI17 MI18 TI17 TI18 TI19 TI20 MI5 MI6 10:40 11:55 MI19 MI20 MC1 MC2 MC3 MI21 MI7 MI8 12:00 1:15 MI9* TI21* TI22 TI23 TI24 MI10 MI11 MI12 1:20 2:35 MI22 MC4 MC6 MC5 MI23 TC1 MI24 MI25 2:40 3:55 TI1 TI2 MC7 TI3 MI26 TC2 TR1 TR2 MI27 4:00 5:15 MC8* TC3 MC10 MC9 TI4 TC4 TR3 TR4 5:20 6:35 TC5* TI5 TI6 TI7 TI8 TC6 TR5 TR6 6:40 7:55 TI9* TC7 TI10 TI11 TI12 TC8 TR8 TR7 Games are to 15 points Half time at 8 points Games are 1 hour and 15 minutes long Soft cap is 10 minutes before the end of game, +1 to highest score 2 Timeouts per team, per game NO TIMEOUTS AFTER SOFT CAP Footblocks not allowed, unless captains agree otherwise 2013 TUC Monday Competitive Playoffs - 1st to 7th Place 3rd Place Bracket Loser of MC4 Competitive Teams Winner of MC9 MC9 Allth Darth (1) Allth Darth (1) 3rd Place Slam Dunks (2) Loser of MC5 The Ligers (3) Winner of MC4 MC4 Krash Kart (4) Krash Kart (4) The El Guapo Sausage Party (5) MC1 Wonky Pooh (6) Winner of MC1 Disc Horde (7) The El Guapo Sausage Winner of MC8 Party (5) MC8 Slam Dunks (2) Champions Winner of MC2 MC2 Disc Horde (7) MC5 The Ligers (3) Winner of MC5 MC3 Winner of MC3 Wonky Pooh (6) Time Hockey3 Score Spirit Hockey4 Score Spirit Hockey5 Score Spirit Score Spirit 10:40 Krash Kart (4) Slam Dunks (2) The Ligers (3) to vs. -

Lucy Morgan Edwards to the University of Exeter As a Thesis for the Degree of Doctor of Philosophy in Politics by Publication, in March 2015
Western support to warlords in Afghanistan from 2001 - 2014 and its effect on Political Legitimacy Submitted by Lucy Morgan Edwards to the University of Exeter as a thesis for the degree of Doctor of Philosophy in Politics by Publication, in March 2015 This thesis is available for Library use on the understanding that it is copyright material and that no quotation from the thesis may be published without proper acknowledgement. I certifythat all the material in this thesis which is not my own work has been identified and that no material has previously been submitted or approved for the award of a degree by this or any other University. !tu ?"\J�� Signature. ... .......................L�Uv) ......... ...!} (/......................., ................................................ 0 1 ABSTRACT This is an integrative paper aiming to encapsulate the themes of my previously published work upon which this PhD is being assessed. This work; encompassing several papers and various chapters of my book are attached behind this essay. The research question, examines the effect of Western support to warlords on political legitimacy in the post 9/11 Afghan war. I contextualise the research question in terms of my critical engagement with the literature of strategists in Afghanistan during this time. Subsequently, I draw out themes in relation to the available literature on warlords, politics and security in Afghanistan. I highlight the value of thinking about these questions conceptually in terms of legitimacy. I then introduce the published work, summarising the focus of each paper or book chapter. Later, a ‘findings’ section addresses how the policy of supporting warlords has affected legitimacy through its impact on security and stability, the political settlement and ultimately whether Afghans choose to accept the Western-backed project in Afghanistan, or not. -
© in This Web Service Cambridge University Press
Cambridge University Press 978-1-107-00545-7 - Decoding Organization: Bletchley Park, Codebreaking and Organization Studies Christopher Grey Index More information Index Abernethy, Barbara 133 Bauman, Z. 6 Abwehr Enigma see Intelligence Enigma BBC 118 action nets 250 Beer, M. 42 Acton, Lord 26 Bellinger, James 126 Adler, P. 236 Bendix, R. 12 administration 55–57 Bennett, Ralph 66, 89, 210 staffing of 168 Beveridge Report 119 Admiralty 54, 63–65 billeting 55–56, 150–151, 155–156 Operational Intelligence Centre (OIC) 64 Birch, Frank 83, 162 age 161–163 classified documents 143 Air (Luftwaffe or GAF) Enigma 34, 63, 80, 84 on Intelligence Exchange (IE) 202, 203 Umkehrwalze D (UKD/Uncle Dick) on conflict 60, 65, 66–67 modification 201–202 on Denniston 93 air force (RAF) 54, 57–58 dispute with Saunders 66 Air Index 216–217, 232 on organization 54, 265 air intelligence 63 on pay 59 Air Ministry (AM), relations with Bletchley recruitment of 132 Park 63 on Travis 198 Aldrich, R. 44, 253–254 Bismarck, sinking of 115–116 Alexander, Hugh 84, 91, 159, 172, 189, Black, A. 221 230–231 Blacker, Carmen 196 friendship and cooperative working Blau, P. 7 184–185 Bletchley Park Recreational Club 138 and John Lewis experience 231 Bletchley Park Trust (BPT) 27 management ability 210 Bletchley Park Trust Archive (BPTA) 23 on morale 191 Blitz recruitment of 133 myth of 117 Uncle Dick Committee 201 spirit of 116 Allberry, Charles 207 Blunt, Antony 207 Alvesson, M. 261 bombe operations rooms American Academy of Management 42 factory methods in 188, 215 Andrew, C. -

Voluntary Interceptors Tribute at the RSGB National Radio Centre
by John Swartz, Voluntary WA9AQN Interceptors tribute at the RSGB National Radio Centre n an evening in 1979, thirty-four years after the end of World OWar II, television viewers in Britain learned of the existence of a cadre of quiet, unassuming operatives who carried out a secret mission. From 1939 throughout the years of the war, to all appearances leading ordinary civilian lives, they were ‘secret listeners’, otherwise known as Voluntary Interceptors (VIs). Officially, they were MI8(c), a part of the Radio Security Service originally within the administration of MI5. They were amateur radio operators and shortwave listening enthusiasts who were all proficient in Morse code. Their mission was secret – and intended to remain so for the rest of their lives. Records identifying them were destroyed at the end of the war. Present estimates of their Voluntary Interceptors tribute at the RSGB National Radio Centre. (Photo: Giles Read, G1MFG). numbers range from 1000 to 1700, and they were dispersed throughout Britain. About 800 wrote his story to provide greater recognition to approached by the intelligence establishment to have been identified in a new exhibit that has the work of his compatriots [3]. assist in assembling a corps of volunteer listeners quietly opened at the RSGB National Radio In 2003, Geoffrey Pidgeon, who had assembled to monitor the airwaves for signals from spies Centre, located in the grounds of Britain’s famous communications equipment at Whaddon Hall and foreign agents who might be transmitting wartime codebreaking centre, Bletchley Park. during the war, published The Secret Wireless to their controllers from within British territory. -

From Axis Surprises to Allied Victories from AFIO's the INTELLIGENCER
Association of Former Intelligence Officers From AFIO's The Intelligencer 7700 Leesburg Pike, Suite 324 Journal of U.S. Intelligence Studies Falls Church, Virginia 22043 Web: www.afio.com, E-mail: [email protected] Volume 22 • Number 3 • $15 single copy price Winter 2016-17 ©2017, AFIO The Bleak Years: 1939 – Mid-1942 GUIDE TO THE STUDY OF INTELLIGENCE The Axis powers repeatedly surprised Poland, Britain, France, and others, who were often blinded by preconceptions and biases, in both a strategic and tactical sense. When war broke out on September 1, 1939, the Polish leadership, ignoring their own intelligence, lacked an appreciation of German mili- tary capabilities: their cavalry horses were no match From Axis Surprises to Allied for German Panzers. British Prime Minister Neville Chamberlain misread Hitler’s intentions, unwilling to Victories accept the evidence at hand. This was the consequence of the low priority given to British intelligence in the The Impact of Intelligence in World War II period between wars.3 Near the end of the “Phony War” (September 3, 1939 – May 10, 1940) in the West, the Germans engi- By Peter C. Oleson neered strategic, tactical, and technological surprises. The first came in Scandinavia in early April 1940. s governments declassify old files and schol- ars examine the details of World War II, it is Norway Aapparent that intelligence had an important The April 9 German invasion of Norway (and impact on many battles and the length and cost of this Denmark) was a strategic surprise for the Norwegians catastrophic conflict. As Nigel West noted, “[c]hanges and British. -

Intelligence As Public Administration
Intelligence and the Machinery of Government: Conceptualising the Intelligence Community1 Dr. Philip H.J. Davies Director, Brunel Centre for Intelligence and Security Studies School of Social Sciences Brunel University Uxbridge, Middlesex UK UB8 3PH Biography Dr. Philip H.J. Davies is Director of the Brunel Centre for Intelligence and Security Studies at Brunel University, and Convenor of the Security and Intelligence Studies Group of the UK Political Studies Association. He is the author of MI6 and the Machinery of Spying (2004) and co-author of Spinning the Spies: Intelligence, Open Government and the Hutton Inquiry (2004) and The Open Side of Secrecy: Britain’s Intelligence and Security Committee (2006). He is currently completing a comparative study of national intelligence in Britain and the United States tentatively entitled They Come Not Single Spies: Intelligence and Government in Britain and the United States to be published by Praeger in 2010. Abstract This article argues that the failure to address intelligence agencies as public organizations part and parcel with the overt machinery of government constitutes a significant lacuna both in the specialist study of intelligence and the broader discipline of public administration studies. The role and status of intelligence institutions as aspects of the machinery of central government is examined, along with the prospects of certain key paradigms in the field for understanding those institutions are considered. Finally, the implications for the wider study of decision-making, policy and public management will be examined. Keywords Intelligence, security, core executive, public management, interdepartmentalism, interagency, public choice, neoinstitutionalism 1 The spy is as old as history, but intelligence agencies are new. -

Air Intelligence Symposium
Air Intelligence Symposium Bracknell Paper No 7 Sponsored jointly by the Royal Air Force Historical Society and the Royal Air Force Staff College, Bracknell ii AIR INTELLIGENCE Copyright ©1997 by the Royal Air Force Historical Society First Published in the UK in 1997 All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording or by any information storage and retrieval system, without the permission from the Publisher in writing. ISBN 0 9519824 5 1 Typeset and printed in Great Britain by Fotodirect Ltd, Brighton. Royal Air Force Historical Society AIR INTELLIGENCE iii Contents 1 Welcome by the Commandant 2 Introductory Remarks by Air Marshal Sir Frederick Sowrey 3 Introductory Remarks by the Chairman, Air Chief Marshal Sir Michael Armitage 4 The Organisation and Sources of RAF Intelligence Mr Sebastian Cox 5 RAF Scientific Intelligence Professor R V Jones 6 USAAF Intelligence and the European War Dr D Putney 7 A Luftwaffe View of the Intelligence War Dr Horsdt Boog 8 The Achievements of Air Intelligence Mr E Thomas 9 Synopsis of Afternoon Discussions 10 Strategic Air Intelligence Post-War Mr R Jackson 11 RB-45 Operations Squadron Leader J Crampton 12 Chairman’s Summing Up 13 Sir Frederick Sowrey iv AIR INTELLIGENCE AIR INTELLIGENCE 1 1. Welcome by the Commandant AVM M Van der Veen MA CEng FIEE Sir Michael Beetham, Air Chief Marshals, Distinguished Guests, Ladies and Gentlemen, I am very pleased to welcome so many members of the RAF Historical Society to Bracknell once more. -

2021 Game Schedule
Mooresville Baseball League - 2021 Game Schedule Baseball MINOR ROOKIE PEEWEE INSTRUCTIONAL MAJOR Softball STB 7-8U (CP) 9-10U (KP) 11-12U (S) Opening Day - April 17 May 17 - May 22 Diamond Diamond Date Day Time Date Day Time 1 2 3 4 5 6 1 2 3 4 5 6 9:00 IN1-IN2 IN3-IN8 MA1-MA2 MA3-MA5 IN4-IN7 17-May Mon 6:00 S1-S2 IN2-IN7 MA5-MA1 MA2-MA4 MI2 - MI5 11:00 MI2 - MI1 MI3 - MI8 MI4 - MI7 MI5 - MI6 STB1-STB2 18-May Tue 6:00 MI2 - MI1 MI3 - MI8 MI4 - MI7 MI5 - MI6 17-Apr Sat 1:00 PW1-PW2 PW3-PW10 PW4-PW9 PW5-PW8 PW6-PW7 19-May Wed 6:00 S2-S3 IN3-IN6 MA2-MA5 MA4-MA3 PW2-PW9 3:00 R1-R4 R2-R3 CP1-CP2 CP3-CP4 KP1-KP2 20-May Thu 6:00 MI3 - MI4 MI1 - MI7 MI8 - MI6 MI2 - MI5 5:00 KP3-KP4 IN5-IN6 STB3-STB4 STB5-STB6 21-May Fri 6:00 CP2-CP3 CP4-CP1 KP1-KP2 KP3-KP4 9:00 IN4-IN5 IN8-IN1 STB3-STB6 STB4-STB1 April 19 - April 24 11:00 R3-R1 R4-R2 STB2-STB5 Diamond 22-May Sat 1:00 PW3-PW8 PW1-PW10 PW5-PW6 PW4-PW7 Date Day Time 1 2 3 4 5 6 3:00 19-Apr Mon 6:00 S1-S2 R1-R4 MA3-MA2 MA4-MA1 5:00 20-Apr Tue 6:00 Cancel Cancel Cancel Cancel 21-Apr Wed 6:00 Cancel Cancel Cancel Cancel May 24 - May 29 22-Apr Thu 6:00 S2-S3 R2-R3 MA1-MA3 MA5-MA4 IN8-IN6 Diamond Date Day Time 23-Apr Fri 6:00 PW2-PW3 PW1-PW7 PW8-PW6 PW9-PW5 PW10-PW4 1 2 3 4 5 6 9:00 IN3-IN4 IN2-IN5 STB1-STB6 STB2-STB4 IN1-IN7 24-May Mon 6:00 S3-S1 KP2-KP3 MA1-MA2 MA3-MA5 STB2-STB4 11:00 R1-R2 R3-R4 STB3-STB5 PW7-PW8 PW5-PW10 25-May Tue 6:00 MI6 - MI2 MI7 - MI8 MI4 - MI1 MI5 - MI3 STB1-STB6 24-Apr Sat 1:00 CP3-CP1 CP2-CP4 PW3-PW1 PW4-PW2 26-May Wed 6:00 S1-S2 KP4-KP1 MA3-MA2 MA4-MA1 3:00 27-May Thu 6:00 -
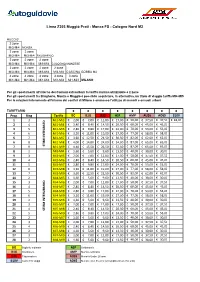
Polimetriche Per Linea Da ATM STIBM.Xlsx
Linea Z203 Muggiò Prati - Monza FS - Cologno Nord M2 MUGGIO' 2 zone Mi3-Mi4 MONZA 2 zone 2 zone Mi3-Mi4 Mi3-Mi4 BRUGHERIO 2 zone 2 zone 2 zone Mi3-Mi4 Mi3-Mi4 Mi3-Mi4 COLOGNO MONZESE 2 zone 2 zone 2 zone 2 zone Mi3-Mi4 Mi3-Mi4 Mi3-Mi4 Mi3-Mi4 CASCINA GOBBA M2 4 zone 4 zone 4 zone 3 zone 3 zone Mi1-Mi4 Mi1-Mi4 Mi1-Mi4 Mi1-Mi3 Mi1-Mi3 MILANO Per gli spostamenti all'interno dei Comuni extraurbani la tariffa minima utilizzabile è 2 zone Per gli spostamenti tra Brugherio, Monza e Muggiò è possibile acquistare, in alternativa, un titolo di viaggio tariffa Mi4-Mi5 Per le relazioni interamente all'interno dei confini di Milano è ammesso l'utilizzo di mensili e annuali urbani TARIFFARIO €€€€€€€€ Prog. Ring Tariffa BO B1G B3G ASP AMP AU26 AO65 B10V 1 3 Mi1-Mi3 € 2,00 € 7,00 € 12,00 € 17,00 € 50,00 € 37,50 € 37,50 € 18,00 2 4 Mi1-Mi4 € 2,40 € 8,40 € 14,50 € 20,50 € 60,00 € 45,00 € 45,00 3 5 Mi1-Mi5 € 2,80 € 9,80 € 17,00 € 24,00 € 70,00 € 53,00 € 53,00 4 6 Mi1-Mi6 € 3,20 € 11,00 € 19,00 € 27,00 € 77,00 € 58,00 € 58,00 5 7 Mi1-Mi7 € 3,60 € 12,50 € 21,50 € 30,50 € 82,00 € 62,00 € 62,00 6 8 Mi1-Mi8 € 4,00 € 14,00 € 24,00 € 34,00 € 87,00 € 65,00 € 65,00 7 9STIBM INTEGRATO Mi1-Mi9€ 4,40 € 15,50 € 26,50 € 37,50 € 87,00 € 65,00 € 65,00 8 2 MI3-MI4 € 1,60 € 5,60 € 9,60 € 13,50 € 40,00 € 30,00 € 30,00 9 3 MI3-MI5 € 2,00 € 7,00 € 12,00 € 17,00 € 50,00 € 37,50 € 37,50 10 4 MI3-MI6 € 2,40 € 8,40 € 14,50 € 20,50 € 60,00 € 45,00 € 45,00 11 5 MI3-MI7 € 2,80 € 9,80 € 17,00 € 24,00 € 70,00 € 53,00 € 53,00 12 6 MI3-MI8 € 3,20 € 11,00 € 19,00 € 27,00 € 77,00 € 58,00 -
Investigating the Diversity of the Terrestrial Invertebrate Fauna of Antarctica: a Closer Look at the Stereotydeus (Acari: Prostigmata) Genus
Investigating the diversity of the terrestrial invertebrate fauna of Antarctica: a closer look at the Stereotydeus (Acari: Prostigmata) genus Claudia Brunetti 1,*, Henk Siepel 2, Pietro Paolo Fanciulli 1, Francesco Nardi 1 and Antonio Carapelli 1 1 Department of Life Sciences, University of Siena, Via Aldo Moro 2, 53100 SI Siena, Italy; 2 Department of Animal Ecology and Physiology, Institute for Water and Wetland Research, Radboud University, Heyendaalseweg 135, 6525 AJ Nijmegen, The Netherlands * Corresponding author: [email protected] 1 Abstract: In the extreme Antarctic ecosystems, plants and invertebrates are confine to sparse and isolated ice-free refugia where they survived for millions of years and where they undergo differentiation and population divergence, potentially resulting in speciation. In invertebrates' populations, the gene flow is strongly affected and reduce by their limited dispersal abilities, their specific habitat requirements and the substantial geographical barriers. And thus, results in high genetic differentiation between clusters of individuals. Mites are surely the predominant invertebrate group of Continental Antarctica and the free-living genus Stereotydeus Berlese, 1901 (Acari: Prostigmata) is one of the most abundant along the coastal zones of Victoria Land and the Transantarctic Mountains. To examine the biodiversity and the phylogeographic distribution ranges of Stereotydeus spp. across Victoria Land, we conducted an integrated analysis of the genus through morphological, phylogenetic and population genetics studies. The results suggest a possible common evolutionary history in several isolated glacial refugia, with scarce gene flow even within populations probably resulting from inter/intra-specific events influenced by several abiotic/biotic factors. Keywords: Victoria Land; molecular phylogeny; biogeography; Acari; Stereotydeus spp. -

MBT FAQ Index
MBT FAQ Index *Words surrounded by quotation marks are defined in the MBT statute* A Accounting Methods Actual or Annual A8, A11, A31, C33, U28, M55 Cash or Accrual C32, C40, M16, M33, U17, U21 Accounts Receivable Factoring Companies B30, M54 “Active Shareholder” C3, C20 “Actively Solicits” Ap4, B11, F1, N2, N4, N5, N6, N7, N8, N10, N11, U12 Actual Method, Computation of Tax for First Taxable Year Less Than 12 Months A8, A11 Amended Returns C9, C13 Annual Method, Computation of Tax for First Taxable Year Less Than 12 Months A8, A11, A31 Annual Returns A6, A7, A10, A11, A14, A17, A20, Fi6 Apportionment Ap1, Ap2, Ap3, Ap5, M2, M5, N1, N4, N5, U3, U5 Arts and Culture Credit C15, C26 Associations (Condominiums, Homeowners and Timeshares) Mi29 B “Base Investment” Fi8 Book Tax Difference B5, B6, Mi9 Bottle Deposit Administration Credit C34, Mi33, M55 Brother-Sister Corporations U7, U9, U24, U25, U33, U34 Brownfield Rehabilitation Credit C7, C8, C9, C13, C24, C26, U22 “Business Activity” Ap1, Ap2, Ap5, B4, B7, B20, B21, B29, B30, M2, M10, M11, M40, M42, M52, M54 “Business Income” A22, A25, Ap2, B2, B3, B4, B7, B12, B14, B16, B18, B20, B21, B22, B23, B29, B30, M10, M11, M12, M13, M27, M38, M40, M42, M43, M44, M52, M54 Business Income Tax Base Administrative A14 Calculation A22, A25, A27, B10, B12, B19, B22, B27, B29, C14, C33, Mi20, M15, M27, M36, M38, M42, M55, N9 Included Ap2, B4, B8, B20, B21, B28, M10, M11, M40, M49, M54 Deduction B2, B3, B5, B6, B18, B27, Mi9, Mi10 Unitary Business Group U5, U27, U32 Business Loss, MBT B10, M15, M36, U27