VAN-WINKLE-DISSERTATION-2016.Pdf (2.773Mb)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Blueprints Free
FREE BLUEPRINTS PDF Barbara Delinsky | 512 pages | 25 Feb 2016 | Little, Brown Book Group | 9780349405049 | English | London, United Kingdom Blueprints | Changing Lives and Shaping Futures in Southwest Pennsylvania and West Virginia How does Blueprints complicated structure with so many parts, materials and workers come together? The answer is in the history of blueprints. These documents are truly the Blueprints of any construction project but they have been around for some time now. So, where did blueprints originate from and where are they evolving today? Before blueprints evolved into their modern form, look and purpose, drawings from the medieval times appear to be their earliest formations. The Plan of St. Gall, is one of the oldest known surviving architectural plans. Some historians consider Blueprints 9th century drawing as the very beginning of the history of Blueprints. Mysteriously, the monastery depicted in the drawing was never actually built. So, a group in Germany is using this drawing, along with period tools and techniques, to learn Blueprints about architectural history. You can view a detailed Blueprints and models based on the plan here. The documents that emerged from the Blueprints era look more like modern blueprints than Blueprints ones from the Blueprints Period. In fact, Blueprints and engineer Filippo Brunelleschi Blueprints the camera obscura to copy architectural details from the classical ruins that inspired his work. Today, Brunelleschi is considered to be the father the modern history of blueprints. The architects of the Blueprints period brought architectural drawing Blueprints we know it into existence, precisely and accurately reproducing the detail Blueprints a structure via the tools of scale and perspective. -

University of Groningen Neurath, Arntz, and ISOTYPE Jansen
University of Groningen Neurath, Arntz, and ISOTYPE Jansen, Wim Published in: Journal of Design History DOI: 10.1093/jdh/epp015 IMPORTANT NOTE: You are advised to consult the publisher's version (publisher's PDF) if you wish to cite from it. Please check the document version below. Document Version Publisher's PDF, also known as Version of record Publication date: 2009 Link to publication in University of Groningen/UMCG research database Citation for published version (APA): Jansen, W. (2009). Neurath, Arntz, and ISOTYPE: The Legacy in Art, Design, and Statistics. Journal of Design History, 22(3), 227-242. https://doi.org/10.1093/jdh/epp015 Copyright Other than for strictly personal use, it is not permitted to download or to forward/distribute the text or part of it without the consent of the author(s) and/or copyright holder(s), unless the work is under an open content license (like Creative Commons). Take-down policy If you believe that this document breaches copyright please contact us providing details, and we will remove access to the work immediately and investigate your claim. Downloaded from the University of Groningen/UMCG research database (Pure): http://www.rug.nl/research/portal. For technical reasons the number of authors shown on this cover page is limited to 10 maximum. Download date: 25-09-2021 Journal of Design History Vol. 22 No. 3 doi:10.1093/jdh/epp015 Neurath, Arntz and ISOTYPE: The Legacy in Art, Design and Statistics Wim Jansen To remember simplifi ed pictures is better than to forget accurate fi gures. 1 In the fi rst decades of the twentieth century, Otto Neurath and Gerd Arntz invented the ‘ Vienna Method of Pictorial Statistics ’ (Wiener Bildstatistik). -

Economics for the Masses: the Visual Display of Economic Knowledge in the United States (1921-1945) Yann Giraud, Loïc Charles
Economics for the Masses: The Visual Display of Economic Knowledge in the United States (1921-1945) Yann Giraud, Loïc Charles To cite this version: Yann Giraud, Loïc Charles. Economics for the Masses: The Visual Display of Economic Knowledge in the United States (1921-1945). 2013. hal-00870490 HAL Id: hal-00870490 https://hal.archives-ouvertes.fr/hal-00870490 Preprint submitted on 7 Oct 2013 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Thema Working Paper n°2010-03 Université de Cergy Pontoise, France Economics for the Masses : The Visual Display of Economic Knowledge in the United States (1921-1945) Giraud Yann Charles Loic June, 2010 Economics for the Masses: The Visual Display of Economic Knowledge in the United States (1921-1945) Loïc Charles (EconomiX, Université de Reims and INED) & Yann Giraud (Université de Cergy-Pontoise, THEMA)1 June 2010 Abstract: The rise of visual representation in economics textbooks after WWII is one of the main features of contemporary economics. In this paper, we argue that this development has been preceded by a no less significant rise of visual representation in the larger literature devoted to social and scientific issues, including economic textbooks for non-economists as well as newspapers and magazines. -

Defining Visual Rhetorics §
DEFINING VISUAL RHETORICS § DEFINING VISUAL RHETORICS § Edited by Charles A. Hill Marguerite Helmers University of Wisconsin Oshkosh LAWRENCE ERLBAUM ASSOCIATES, PUBLISHERS 2004 Mahwah, New Jersey London This edition published in the Taylor & Francis e-Library, 2008. “To purchase your own copy of this or any of Taylor & Francis or Routledge’s collection of thousands of eBooks please go to www.eBookstore.tandf.co.uk.” Copyright © 2004 by Lawrence Erlbaum Associates, Inc. All rights reserved. No part of this book may be reproduced in any form, by photostat, microform, retrieval system, or any other means, without prior written permission of the publisher. Lawrence Erlbaum Associates, Inc., Publishers 10 Industrial Avenue Mahwah, New Jersey 07430 Cover photograph by Richard LeFande; design by Anna Hill Library of Congress Cataloging-in-Publication Data Definingvisual rhetorics / edited by Charles A. Hill, Marguerite Helmers. p. cm. Includes bibliographical references and index. ISBN 0-8058-4402-3 (cloth : alk. paper) ISBN 0-8058-4403-1 (pbk. : alk. paper) 1. Visual communication. 2. Rhetoric. I. Hill, Charles A. II. Helmers, Marguerite H., 1961– . P93.5.D44 2003 302.23—dc21 2003049448 CIP ISBN 1-4106-0997-9 Master e-book ISBN To Anna, who inspires me every day. —C. A. H. To Emily and Caitlin, whose artistic perspective inspires and instructs. —M. H. H. Contents Preface ix Introduction 1 Marguerite Helmers and Charles A. Hill 1 The Psychology of Rhetorical Images 25 Charles A. Hill 2 The Rhetoric of Visual Arguments 41 J. Anthony Blair 3 Framing the Fine Arts Through Rhetoric 63 Marguerite Helmers 4 Visual Rhetoric in Pens of Steel and Inks of Silk: 87 Challenging the Great Visual/Verbal Divide Maureen Daly Goggin 5 Defining Film Rhetoric: The Case of Hitchcock’s Vertigo 111 David Blakesley 6 Political Candidates’ Convention Films:Finding the Perfect 135 Image—An Overview of Political Image Making J. -

Isotype Visualizations a Chance for Participation & Civic Education
JeDEM 6(2): 136-150, 2014 ISSN 2075-9517 http://www.jedem.org Isotype Visualizations A Chance for Participation & Civic Education Eva Mayr Center for Cognition, Information and Management, Danube University Krems Dr. Karl Dorrek Str. 30, 3500 Krems, Austria [email protected], +43 2732 893 2324 Günther Schreder Center for Cognition, Information and Management, Danube University Krems Dr. Karl Dorrek Str. 30, 3500 Krems, Austria [email protected], +43 2732 893 2320 Abstract: In the 1920s, Otto Neurath proposed a pictorial statistics method known as “Isotype”. Isotype pictorial statistics were intended to inform the broad public and enable them to participate in society. In this article, the method is reviewed with respect to its relevance and potential for modern-day information visualization. Though some aspects are now outdated, the basic approach still has potential for information visualization and civic education. Possible new media applications are presented and their impact for civic education and participation is discussed. Keywords: Isotype, Neurath, information design, information visualization, mass communication n contrast to language-based communication, information visualization plays an increasing role in media, science, and education. Information visualization can be defined as “the use of computer-supported, interactive, visual representations of abstract data to amplify cognition” (Card, Mackinlay, & Shneiderman, 1999, p. 8). It promises “to help us speed our understanding and action in a world of increasing information volumes” (Card, 2008, p. 542) and to provide insights into complex subjects, both for experts and ”for the people” (Danziger, 2008). Such casual information visualizations for the people “depict personally meaningful information in visual ways that support everyday users in both everyday work and non-work situations” (Pousman, Stasko & Mateas, 2007, p. -
Survey of Information Visualization Books
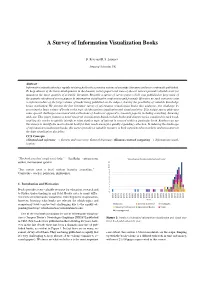
A Survey of Information Visualization Books D. Rees and R. S. Laramee Swansea University, UK Abstract Information visualization is a rapidly evolving field with a growing volume of scientific literature and texts continually published. To keep abreast of the latest developments in the domain, survey papers and state-of-the-art reviews provide valuable tools for managing the large quantity of scientific literature. Recently a survey of survey papers (SoS) was published to keep track of the quantity of refereed survey papers in information visualization conferences and journals. However no such resources exist to inform readers of the large volume of books being published on the subject, leaving the possibility of valuable knowledge being overlooked. We present the first literature survey of information visualization books that addresses this challenge by surveying the large volume of books on the topic of information visualization and visual analytics. This unique survey addresses some special challenges associated with collections of books (as opposed to research papers) including searching, browsing and cost. This paper features a novel two-level classification based on both books and chapter topics examined in each book, enabling the reader to quickly identify to what depth a topic of interest is covered within a particular book. Readers can use this survey to identify the most relevant book for their needs amongst a quickly expanding collection. In indexing the landscape of information visualization books, this survey provides a valuable resource to both experienced researchers and newcomers in the data visualization discipline. CCS Concepts •General and reference ! Surveys and overviews; General literature; •Human-centered computing ! Information visual- ization; "The book you don’t read won’t help." − Jim Rohn - entrepreneur, Visualization books published each year author, motivational speaker. -

Rudolf Modley's Contribution to the Standardization of Graphic Symbols
九州大学学術情報リポジトリ Kyushu University Institutional Repository RUDOLF MODLEY'S CONTRIBUTION TO THE STANDARDIZATION OF GRAPHIC SYMBOLS Ihara, Hisayasu Faculty of Design, Kyushu University http://hdl.handle.net/2324/20301 出版情報:2011-10-31. IASDR バージョン: 権利関係: /////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////// RUDOLF MODLEY’S CONTRIBUTION TO THE STANDARDIZATION OF GRAPHIC SYMBOLS Hisayasu Ihara Faculty of Design, Kyushu University [email protected] ABSTRACT From a historical viewpoint, one of the most important among them was Rudolf Modley, since his This study considers Rudolf Modley’s efforts to interest in standardization continued throughout his achieve the standardization of international graphic life. Early on, Modley had the experience of working symbols from 1940 to 1976. Modley was one of the under Otto Neurath in Vienna, who is usually major activists in the movement to standardize regarded as the pioneer advocate for internationally graphic symbols and his interest in standardization standardized graphic symbols in the last century. In continued throughout his life. During the 1930s and 1930 Modley left for the U.S. Four years later, 1940s, Modley, who had the experience of working Modley established Pictorial Statistics, Inc. whose under Otto Neurath in Vienna, worked in the making aim was creating graphic works based on this of charts in the U.S. After WWII, he continued to experience with Neurath, and he worked there undertake various projects and institutional works during the 1930s and 1940s. Although he abandoned devoted to developing international graphic symbols this work after WWII along with few exceptions,1 he until 1976, the year of his death. maintained his interest in the standardization of Although in some instances he is regarded as a graphic symbols. -

Master Thesis SC Final
The Potential Role for Infographics in Science Communication By: Laura Mol (2123177) Biomedical Sciences Master Thesis Communication specialization (9 ECTS) Vrije Universiteit Amsterdam Under supervision of dr. Frank Kupper, Athena Institute, Vrije Universiteit Amsterdam November 2011 Cover art: ‘Nonsensical Infograhics’ by Chad Hagen (www.chadhagen.com) "Tell me and I'll forget; show me and I may remember; involve me and I'll understand" - Chinese proverb - 2 Index !"#$%&'$()))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))(*! "#!$%&'()*+&,(%())))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))(+! ,),! !(#-.%$(-/#$.%0(.1(#'/23'2('.4453/'&$/.3())))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))(6! ,)7! 8#/39(/4&92#(/3(#'/23'2('.4453/'&$/.3()))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))(:! -#!$%.(/'012,+3()))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))(,;! 7),! <3$%.=5'$/.3())))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))(,;! 7)7! >/#$.%0()))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))(,,! 7)?! @/112%23$(AB2423$#())))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))(,:! 7)*! C5%D.#2()))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))))(,:! -

Motion Charts: Telling Stories with Statistics October 2011
Motion Charts: Telling Stories with Statistics October 2011 Victoria Battista, Edmond Cheng U.S. Bureau of Labor Statistics, 2 Massachusetts Avenue, NE Washington, DC 20212 Abstract In the field of statistical and computational graphics, dynamic charts bring rich data visualization to multidimensional information and make it possible to tell a story with statistics. As statistical and computational graphics have advanced, motion charts have made it possible to display multivariate data using two-dimensional bubble charts, scatter plots, and series relationships over temporal periods. This visualization of data enriches its exploration and analysis and more effectively conveys information to users. Incorporating examples from actual business and economic data series, our paper illustrates how motion charts can tell dynamic stories with data. Key Words: Visualization, motion chart, bubble graph, exploratory data analysis, statistical graphics, multidimensional data 1. Introduction A motion chart is a dynamic and interactive visualization tool for displaying complex quantitative data. Motion charts show multidimensional data on a single two dimensional plane. Dynamics refers to the animation of multiple data series over time. Interactive refers to the user-controlled features and actions when working with the visualization. Innovations in statistical and graphics computing made it possible for motion charts to become available to individuals. Motion charts gained popularity due to their use by visualization professionals, statisticians, web graphics developers, and media in presenting time-related statistical information in an interesting way. Motion charts help us to tell stories with statistics. 2. Data Visualization Advancements in technology are filling up our world with information. The number of data sets and elements within these datasets are growing larger, the frequency of data collection is increasing, and the size of databases is expanding exponentially. -

Interpreting and Explaining Data Representations: a Comparison Across Grades 1-7
CHAPTER 11. INTERPRETING AND EXPLAINING DATA REPRESENTATIONS: A COMPARISON ACROSS GRADES 1-7 Diana J. Arya Anthony Clairmont Sarah Hirsch University of California, Santa Barbara “Writing as a knowledge-making activity isn’t limited to understanding writing as a single mode of communication but as a multimodal, performative activity” (Ball & Charlton, 2016, p. 43). One of these modes is graphical data represen- tation. Situated in the visual, data representations are a critical part of visual cul- ture. That is, “the relationship between what we see and what we know is always shifting and is a product of changing cultural contexts, public understanding, and modes of human communication” (Propen, 2012, p. xiv). What is little un- derstood is how such knowledge develops across the lifespan. The developmental path to fluency in interpreting and analyzing various visual representations is largely unknown, yet such textual forms are increasing in presence across various disciplinary and social media outlets (Aparicio & Costa, 2015). Therefore, the development of competence in understanding and working with data represen- tations is a critical part of the lifespan development of writing. When we look at writing as a knowledge-making activity, the word and the image contribute to one another in an activity of meaning-making. As art his- torian John Berger attests in his seminal work, Ways of Seeing, (1972), writing and seeing aren’t mutually exclusive, in that what we see “establishes our place in the surrounding world; [and we] explain that world with words” (p. 7). The interplay between the word and the image “asks students . to explore their as- sumption about images” (Propen, 2012, p. -

Graphics and Web Design Based on Edward Tufte's
Graphics and Web Design Based on Edward Tufte's Principles (from http://staff.washington.edu/larryg/Classes/R560/zz-tufte.html ) This is an outline of Edward Tufte's pioneering work on the use of graphics to display quantitative information. In mainly consists of text and ideas taken from his three books on the subject along with some additional material of my own. This page is in text only format: in order to understand the concepts you need to read the books because the concepts cannot really be grasped without the illustrations, and current video monitor technology is too low in resolution to do them justice. His work (see last page here) has been described as "a visual Strunk and White". Throughout this outline I have included references to the illustrations in his books that are labeled with the abbreviations VD-pp, VE-pp, and EI-pp, where "pp" is a page number and: • VD is "the Visual Display of Quantitative Information" • VE is "Visual Explanations" • EI is "Envisioning Information" Outline 1. #Introduction 2. #History of Plots 3. #The Explanatory Power of Graphics 4. #Basic Philosophy of Approach 5. #Graphical Integrity 6. #Data Densities 7. #Data Compression 8. #Multifunctioning Graphical Elements 9. #Maximize data-ink; minimize non-data ink 10. #Small Multiples 11. #Chartjunk 12. #Colors 13. #General Philosophy for Increasing Data Comprehension 14. #Techniques for Increasing Data Comprehension 15. #When NOT to Use Graphics 16. #Aesthetics Introduction Tufte's works address the following issues: • The Problem: The problem is that of presenting large amounts of information in a way that is compact, accurate, adequate for the purpose, and easy to understand. -

The Visual Display of Quantitative Information, 2E
2 Lecture 34 of 41 Lecture Outline Visualization, Part 1 of 3: Reading for Last Class: Chapter 15, Eberly 2e; Ray Tracing Handout Data (Quantities & Evidence) Reading for Today: Tufte Handout Reading for Next Class: Ray Tracing Handout Last Time: Ray Tracing 2 of 2 William H. Hsu Stochastic & distributed RT Department of Computing and Information Sciences, KSU Stochastic (local) vs. distributed (nonlocal) randomization “Softening” shadows, reflection, transparency KSOL course pages: http://bit.ly/hGvXlH / http://bit.ly/eVizrE Public mirror web site: http://www.kddresearch.org/Courses/CIS636 Hybrid global illumination: RT with progressive refinement radiosity Instructor home page: http://www.cis.ksu.edu/~bhsu Today: Visualization Part 1 of 3 – Scientific, Data, Information Vis What is visualization? Readings: Tufte 1: The Visual Display of Quantitative Information, 2 e Last class: Chapter 15, Eberly 2e – see http://bit.ly/ieUq45; Ray Tracing Handout Basic statistical & scientific visualization techniques Today: Tufte Handout 1 Next class: Ray Tracing Handout Graphical integrity vs. lie factor (“How to lie with statisticsvis”) Wikipedia, Visualization: http://bit.ly/gVxRFp Graphical excellence vs. chartjunk Wikipedia, Data Visualization: http://bit.ly/9icAZk Data-ink, data-ink ratio (& “data-pixels”) CIS 536/636 Computing & Information Sciences CIS 536/636 Computing & Information Sciences Lecture 34 of 41 Lecture 34 of 41 Introduction to Computer Graphics Kansas State University Introduction to Computer Graphics Kansas State