A Study on Common Android Emulators and Anti- Forensic Message-Hiding Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cisco SCA BB Protocol Reference Guide
Cisco Service Control Application for Broadband Protocol Reference Guide Protocol Pack #60 August 02, 2018 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

Security System for Mobile Messaging Applications Pejman Dashtinejad
Security System for Mobile Messaging Applications Pejman Dashtinejad Master of Science Thesis Stockholm, Sweden TRITA–ICT–EX-2015:2 Introduction | 1 Security System for Mobile Messaging Applications Pejman Dashtinejad 8 January 2015 Master of Science Thesis Examiner Professor Sead Muftic Department of ICT KTH University SE-100 44 Stockholm, Sweden TRITA–ICT–EX-2015:2 Abstract | iii Abstract Instant messaging (IM) applications are one of the most popular applications for smartphones. The IMs have the capability of sending messages or initiating voice calls via Internet which makes it almost cost free for the users to communicate with each other. Unfortunately, like any other type of applications, majority of these applications are vulnerable to malicious attacks and have privacy issues. The motivation for this thesis is the need to identifying security services of an IM application and to design a secure system for any mobile messaging application. This research proposes an E2EE (End-to-End Encryption) approach which provides a secure IM application design which protects its users with better integrity, confidentiality and privacy. To achieve this goal a research is conducted to investigate current security features of popular messaging applications in the mobile market. A list of requirements for good security is generated and based on those requirements an architecture is designed. A demo is also implemented and evaluated. Keywords: Mobile, Application, messaging, Chat, Encryption, Security Acknowledgments | v Acknowledgments First and foremost, thank you God to give me another chance to complete my higher education and to learn enormous skills and knowledge through all these years of study at the university. -

Enterprise Edition
Secure Communication. Simplified. SAFECHATS Problem Most companies use popular insecure email and ⛔ messaging services to communicate confidential information P The information flow within the Company is ⛔ disorganized Metadata is exposed and available to third-party ⛔ services SAFECHATS Introducing SAFECHATS Ultra-secure communication solution P Designed with security in mind SAFECHATS Why SAFECHATS? ✔ Information is always end-to-end encrypted by default P ✔ All-in-one communication suite: • Text messaging (one-on-one and group chats) • Voice calls • File transfers (no size and file type limits) SAFECHATS How does SAFECHATS solve the problem? ✔ Customizable white label solution ✔ Integrates with existing softwareP infrastructure ✔ Enterprise-wide account and contact list management, supervised audited chats for compliance SAFECHATS What makes SAFECHATS different? ✔ Your own isolated cloud environment or on-premise deployment P ✔ Customizable solution allows to be compliant with internal corporate security policies ✔ No access to your phone number and contact list SAFECHATS Screenshot Protection ✔ Notifications on iOS P ✔ DRM protection on Android SAFECHATS Identity Verification ✔ Protection from man-in-the-middle attacksP ✔ SMP Protocol SAFECHATS Privacy Features ✔ Show / hide messages and files P ✔ Recall messages and files ✔ Self-destructing messages and files SAFECHATS Additional Protection ✔ History retention control P ✔ Application lock: • PIN-code • Pattern-lock on Android devices • Touch ID on iOS devices SAFECHATS How does SAFECHATS -

Policy Options and Regulatory Mechanisms for Managing Radicalization on the Internet
Policy options and regulatory mechanisms for managing radicalization on the Internet Paris, 30 September 2016 “[…] I firmly believe that in a free democratic society, freedom of speech and expression is one of the most prized freedoms which must be defended and upheld at any cost and this should be particularly so in the land of Voltaire. It is indeed unfortunate that in the world of today, when science and technology have advanced the frontiers of knowledge and mankind is beginning to realize that human happiness can be realized only through inter-dependence and cooperation, the threshold of tolerance should be going down. It is high time man should realize his spiritual dimension and replace bitterness and hatred by love and compassion, tolerance and forgiveness.” Justice Prafullachandra Bhagwati Dan Shefet (Individual Specialist) ACKNOWLEDGEMENTS The author wishes to thank the following for their support, valuable advice and input throughout the drafting of the Report: Dr. Indrajit Banerjee and his team in UNESCO’s Knowledge Societies Division The UNESCO Delegates and Ministries of Justice/Interior of countries that have participated in the Country Survey. Alexander Linden, Honorary advisor to the French Supreme Court Janice Duffy, Researcher, Australia Pavan Duggal, Supreme Court Lawyer, India Tom Høyem, Former Minister in Denmark under Poul Schlüter Francesca Musiani, Researcher at the CNRS Institute for Communication Sciences and Member of the French National Assembly’s Commission on the Law and Rights in the Digital Era Sami Mahbouli, Lawyer at The Tunisian Supreme Court and Columnist Sabine Leutheusser-Schnarrenberger, Former Minister of Justice under Angela Merkel Marc Randazza, First Amendment Attorney, United States Viswa Sadasivan, CEO of Strategic Moves (Consultancy agency in Singapore) and former member of the Singaporean Parliament Mr K. -
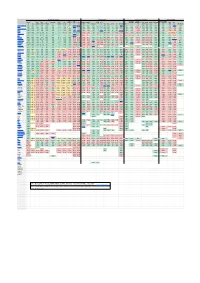
Digital Communications Protocols
Security & Privacy Compatibility Features & Usability Sustainability E2E E2E Offline Local Decentralized Active Open Open On Anonymous E2E E2E Default Audit FIDO1 Desktop Mobile Apple AOSP Messages messaging File Audio Video Phoneless or Federated Open IETF [1] TLS Client Server Premise [2] Private Group [3] [4] / U2F Web Web Android iOS [5] Win macOS Linux *BSD Terminal MDM [6] [7] [8] Share Call Call [9] [10] Spec [11] Introduced Element/Matrix TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE PARTIAL TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE 2014 XMPP TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE PARTIAL [12]TRUE FALSE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE [13] TRUE TRUE TRUE TRUE TRUE TRUE TRUE 1999 NextCloud Talk TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE TRUE TRUE FALSE TRUE TRUE TRUE TRUE TRUE FALSE FALSE 2018 Wire TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE TRUE FALSE TRUE TRUE FALSE TRUE TRUE TRUE TRUE PARTIAL TRUE TRUE FALSE TRUE TRUE TRUE TRUE FALSE FALSE FALSE 2014 Jami TRUE TRUE TRUE N/A [14] N/A TRUE TRUE FALSE [15] TRUE FALSE N/A [16] FALSE FALSE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE TRUE FALSE FALSE TRUE TRUE TRUE TRUE TRUE PARTIAL PARTIAL[17] [18] 2016 Briar [19] TRUE TRUE TRUE N/A [20] N/A TRUE TRUE TRUE TRUE TRUE N/A [21] FALSE FALSE TRUE FALSE TRUE FALSE FALSE FALSE FALSE FALSE FALSE TRUE TRUE FALSE FALSE FALSE FALSE TRUE FALSE FALSE 2016 Tox TRUE TRUE TRUE -

Security & Privacy for Mobile Phones
Security & Privacy FOR Mobile Phones Carybé, Lucas Helfstein July 4, 2017 Instituto DE Matemática E Estatística - USP What IS security? • That GRANTS THE INFORMATION YOU PROVIDE THE ASSURANCES above; • That ENSURES THAT EVERY INDIVIDUAL IN THIS SYSTEM KNOWS EACH other; • That TRIES TO KEEP THE ABOVE PROMISES forever. Security IS ... A System! • That ASSURES YOU THE INTEGRITY AND AUTHENTICITY OF AN INFORMATION AS WELL AS ITS authors; 1 • That ENSURES THAT EVERY INDIVIDUAL IN THIS SYSTEM KNOWS EACH other; • That TRIES TO KEEP THE ABOVE PROMISES forever. Security IS ... A System! • That ASSURES YOU THE INTEGRITY AND AUTHENTICITY OF AN INFORMATION AS WELL AS ITS authors; • That GRANTS THE INFORMATION YOU PROVIDE THE ASSURANCES above; 1 • That TRIES TO KEEP THE ABOVE PROMISES forever. Security IS ... A System! • That ASSURES YOU THE INTEGRITY AND AUTHENTICITY OF AN INFORMATION AS WELL AS ITS authors; • That GRANTS THE INFORMATION YOU PROVIDE THE ASSURANCES above; • That ENSURES THAT EVERY INDIVIDUAL IN THIS SYSTEM KNOWS EACH other; 1 Security IS ... A System! • That ASSURES YOU THE INTEGRITY AND AUTHENTICITY OF AN INFORMATION AS WELL AS ITS authors; • That GRANTS THE INFORMATION YOU PROVIDE THE ASSURANCES above; • That ENSURES THAT EVERY INDIVIDUAL IN THIS SYSTEM KNOWS EACH other; • That TRIES TO KEEP THE ABOVE PROMISES forever. 1 Security IS ... A System! Eve | | | Alice "Hi" <---------------> "Hi" Bob 2 Security IS ... Cryptography! Eve | | | Alice "Hi" <----"*****"------> "Hi" Bob 3 Security IS ... Impossible! The ONLY TRULY SECURE SYSTEM IS ONE THAT IS POWERED off, CAST IN A BLOCK OF CONCRETE AND SEALED IN A lead-lined ROOM WITH ARMED GUARDS - AND EVEN THEN I HAVE MY doubts. -

Protec3ng Messaging Other Than Email, Plus Network Link Protec3on
Protec'ng Messaging Other Than Email, plus Network Link Protec'on Joe St Sauver, Ph.D. [email protected] or [email protected] M3AAWG Senior Technical Advisor Scien@st, Farsight Security, Inc. Gold Ballroom, 1st Floor M3AAWG 36, San Francisco, California Wednesday Feb 17th, 2016, 15:30-16:30 hPps://www.stsauver.com/joe/crypto-other-than-email/ 1 Introduc'on • Today's session has two parts: – The first part will consider cryptographic privacy protecon for messaging other than email. – The second part will focus on cryptographic protecon of high speed internal links. • The common link between the two topics is that in each case, your op@ons are constrained by what the market offers. Today's goal is to help you understand why you want protec@on for these points of exposure, and how to select a solu@on. • Both of these topics are the subject of pending dra documents in the Pervasive Monitoring SIG. 2 I. Messaging Other Than Email 3 Messaging Other Than Email • M3AAWG has been working hard on protec@ng email against pervasive monitoring. • That's very important work, and protec@ng email privacy is a totally appropriate goal for M3AAWG. • Although M3AAWG has always had a strong focus on email, our charter, as the an@-Pervasive Monitoring SIG of the Messaging, Malware, and Mobile An-Abuse Working Group, includes, or should include, protec@ng mobile voice telephony and mobile applicaons (such as tex@ng/chat), too. • Arguably, for many users, secure mobile voice and secure text/ chat is as important, or even more important than email. -

Modern End-To-End Encrypted Messaging for the Desktop
Die approbierte Originalversion dieser Diplom-/ Masterarbeit ist in der Hauptbibliothek der Tech- nischen Universität Wien aufgestellt und zugänglich. http://www.ub.tuwien.ac.at The approved original version of this diploma or master thesis is available at the main library of the Vienna University of Technology. http://www.ub.tuwien.ac.at/eng Modern End-to-End Encrypted Messaging for the Desktop DIPLOMARBEIT zur Erlangung des akademischen Grades Diplom-Ingenieur im Rahmen des Studiums Software Engineering and Internet Computing eingereicht von Richard Bayerle Matrikelnummer 1025259 an der Fakultät für Informatik der Technischen Universität Wien Betreuung: Privatdozent Dipl.Ing. Mag. Dr. Edgar Weippl Mitwirkung: Dr. Martin Schmiedecker Wien, 2. Oktober 2017 Richard Bayerle Edgar Weippl Technische Universität Wien A-1040 Wien Karlsplatz 13 Tel. +43-1-58801-0 www.tuwien.ac.at Modern End-to-End Encrypted Messaging for the Desktop DIPLOMA THESIS submitted in partial fulfillment of the requirements for the degree of Diplom-Ingenieur in Software Engineering and Internet Computing by Richard Bayerle Registration Number 1025259 to the Faculty of Informatics at the TU Wien Advisor: Privatdozent Dipl.Ing. Mag. Dr. Edgar Weippl Assistance: Dr. Martin Schmiedecker Vienna, 2nd October, 2017 Richard Bayerle Edgar Weippl Technische Universität Wien A-1040 Wien Karlsplatz 13 Tel. +43-1-58801-0 www.tuwien.ac.at Erklärung zur Verfassung der Arbeit Richard Bayerle Seestraße 67 78315 Radolfzell am Bodensee Deutschland Hiermit erkläre ich, dass ich diese Arbeit selbständig verfasst habe, dass ich die verwen- deten Quellen und Hilfsmittel vollständig angegeben habe und dass ich die Stellen der Arbeit – einschließlich Tabellen, Karten und Abbildungen –, die anderen Werken oder dem Internet im Wortlaut oder dem Sinn nach entnommen sind, auf jeden Fall unter Angabe der Quelle als Entlehnung kenntlich gemacht habe. -

National Security Agency | Cybersecurity Information Selecting
National Security Agency | Cybersecurity Information Selecting and Safely Using Collaboration Services for Telework - UPDATE Summary During a global pandemic or other crisis contingency scenarios, many United States Government (USG) personnel must operate from home while continuing to perform critical national functions and support continuity of government services. With limited access to government furnished equipment (GFE) such as laptops and secure smartphones, the use of (not typically approved) commercial collaboration services on personal devices for limited government official use becomes necessary and unavoidable. We define collaboration services as those capabilities that allow the workforce to communicate via internet-enabled text, voice, and video, and can include the sharing of files and other mission content. Collaboration can occur between two people or widened to include a large group to support mission needs. This document provides a snapshot of best practices and criteria based on capabilities available at the time of publication and was coordinated with the Department of Homeland Security (DHS), which has released similar guidance: “Cybersecurity Recommendations for Federal Agencies Using Video Conferencing” [1] and “Guidance for Securing Video Conferencing” [2]. This NSA publication is designed to provide simple and actionable considerations for individual government users. The intent of this document is not meant to be exhaustive or based on formal testing, but rather be responsive to a growing demand amongst the federal government to allow its workforce to operate remotely using personal devices when deemed to be in the best interests of the health and welfare of its workforce and the nation. Recommendations in this document are likely to change as collaboration services evolve and also address known vulnerabilities and threats. -
Windows 64 Bit Bluestacks For
No Bluestacks For Mac Bluestacks For Mac Bluestacks No Mac Bluestacks For Mac Os Windows 64 Bit The installer automatically detects the Operating System your device is running and chooses the right version of BlueStacks. Bluestacks For Mac Recommended Choose from the Other BlueStacks Versions Bluestacks Mac will provide you with the opportunity to use Android applications on your Mac. When you are a dedicated Mac user you will know some of the best applications that are available over the Android platforms are not available for you guys. Bluestacks will make it possible for you to use all of these fantastic applications and more. BlueStacks is an American technology company that produces the BlueStacks App Player and other cloud-based cross-platform products. The BlueStacks App Player is designed to enable Android applications to run on PCs running Microsoft Windows and Apple's macOS.The company was founded in 2009 by Jay Vaishnav, Suman Saraf, and Rosen Sharma, former CTO at McAfee and a board member. Nox APP Player aims to provide the best experience for users to play Android. I have been trying to run multiple instance on my mac but realized that the instance manager is not available. Is this a feature that is not yet available to mac users? But i'd like to know atleast a tentative date for when Genshin Impact will be playable on Bluestacks. No pressure on the devs tho! Operating System 1 day ago The BlueStacks App Player lets you run apps designed for a mobile device, on your Mac or PC. -

Online Security for Independent Media and Civil Society Activists
Online Security for Independent Media and Civil Society Activists A white paper for SIDA’s October 2010 “Exile Media” conference Eric S Johnson (updated 13 Oct 2013) For activists who make it a priority to deliver news to citizens of countries which try to control the information to which their citizens have access, the internet has provided massive new opportunities. But those countries’ governments also realise ICTs’ potential and implement countermeasures to impede the delivery of independent news via the internet. This paper covers what exile media can or should do to protect itself, addressing three categories of issues: common computer security precautions, defense against targeted attacks, and circumventing cybercensorship, with a final note about overkill (aka FUD: fear, uncertainty, doubt). For each of the issues mentioned below, specific ex- amples from within the human rights or freedom of expression world can be provided where non-observance was cata- strophic, but most of those who suffered problems would rather not be named. [NB Snowden- gate changed little or nothing about these recommendations.] Common computer security: The best defense is a good … (aka “lock your doors”) The main threats to exile media’s successful use of ICTs—and solutions—are the same as for any other computer user: 1) Ensure all software automatically patches itself regularly against newly-discovered secu- rity flaws (e.g. to maintain up-to-date SSL certificate revocation lists). As with antivirus software, this may cost something; e.g. with Microsoft (Windows and Office), it may re- quire your software be legally purchased (or use the WSUS Offline Update tool, which helps in low-bandwidth environments). -

Download from Amazon Prime Video to Pc Download from Amazon Prime Video to Pc
download from amazon prime video to pc Download from amazon prime video to pc. Amazon Prime Video is an OTT platform that offers video streaming services with a growing library of high-quality original content and an extensive streaming catalog of films and TV shows. Originally, the platform served as a service to buy and stream TV shows and movies. With time, Amazon has also introduced the concept of online buffet-style streaming. Prime video offers ad-free streaming services. Video quality varies from SD to Ultra HD and HDR depending on the show and your system. If you are not subscribed to Prime membership, you can purchase or rent prime video content on a pay-per-title model. You can always switch to a standalone prime video membership for accessibility to the streaming service only. You can subscribe for a standalone Amazon Prime Video subscription that gives you access to the video content but would not involve other benefits like Amazon Kindle. Here is the list of subscription plans available for prime video: Standalone Membership: it costs $8.99 per month. You can subscribe for a standalone Amazon Video subscription for video content without other benefits like free two-day shipping, etc. Amazon Prime Membership: Amazon Prime subscription costs $12.99 per month or $119 a year. It includes prime video and additional benefits such as guaranteed two (one day if available) delivery, complimentary music streaming, a Twitch Prime subscription, Whole Foods deals, and many more. Rent or Buy: it’s a significant advantage offered by Amazon Prime Video.