Key Management
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Diffie-Hellman (1976) – RSA (1977) – More Recently: ID-Based Encryption (2001), Functional Encryption (2011)…
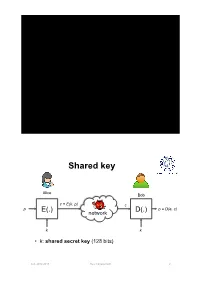
Key Management Shared key Alice Bob c = E(k, p) c p E(.) D(.) p = D(e, c) network k k • k: shared secret key (128 bits) A.A. 2012-2013 Key management 2 Pairwise keys • Each pair of users shares an long-term secret key Alice Bob • Properties • Every user stores (n -1) keys • The overall number of keys is O(n2) Carol Eve Dave A.A. 2012-2013 Key management 3 Pairwise keys • Pros – If a subject is compromised only its communications are compromised; • communications between two other subjects are not compromised • We cannot do any better! • Cons – Poor scalability: the number of keys is quadratic in the number of subjects – Poor scalability: a new member’s joining and a member’s leaving affect all current members A.A. 2012-2013 Key management 4 Trusted Third Party • Online Trusted Third Party (TTP) – Each user shares a long-term secret key with TTP TTP – Every user stores one key – The overall number of keys is n KA KB • TTP is a single point of failure – TTP must be always online A B – TTP knows all the keys • TTP can read all msg between Alice and Bob KAB • TTP can impersonate any party A.A. 2012-2013 Key management 5 Key distribution: a toy protocol Alice wants a shared key with Bob. Eavesdropping security only Bob (kB) Alice (kA) TTP “Alice wants key with Bob” choose E(KA, “A, B” || KAB) random kAB ticket ticket ← E(KB, “A, B” || KAB) kAB kAB Subject to replay attacks A.A. 2012-2013 Key management 6 Key distribution: toy protocol • Insecure against replay attacks (active adversary) – Attacker records session between Alice and merchant Bob • For example: an order – Attacker replays session to Bob • Bob thinks Alice is ordering another copy of the book A.A. -

Ansi/Scte 23-2 2017
ENGINEERING COMMITTEE Data Standards Subcommittee AMERICAN NATIONAL STANDARD ANSI/SCTE 23-2 2017 DOCSIS 1.1 Part 2: Baseline Privacy Plus Interface ANSI/SCTE 23-2 2017 NOTICE The Society of Cable Telecommunications Engineers (SCTE) Standards and Operational Practices (hereafter called “documents”) are intended to serve the public interest by providing specifications, test methods and procedures that promote uniformity of product, interchangeability, best practices and ultimately the long term reliability of broadband communications facilities. These documents shall not in any way preclude any member or non-member of SCTE from manufacturing or selling products not conforming to such documents, nor shall the existence of such standards preclude their voluntary use by those other than SCTE members. SCTE assumes no obligations or liability whatsoever to any party who may adopt the documents. Such adopting party assumes all risks associated with adoption of these documents, and accepts full responsibility for any damage and/or claims arising from the adoption of such documents. Attention is called to the possibility that implementation of this document may require the use of subject matter covered by patent rights. By publication of this document, no position is taken with respect to the existence or validity of any patent rights in connection therewith. SCTE shall not be responsible for identifying patents for which a license may be required or for conducting inquiries into the legal validity or scope of those patents that are brought to its attention. Patent holders who believe that they hold patents which are essential to the implementation of this document have been requested to provide information about those patents and any related licensing terms and conditions. -

AWS Key Management Service Cryptographic Details
AWS Key Management Service Cryptographic Details August 2016 Amazon Web Services – AWS KMS Cryptographic Details August 2016 © 2016, Amazon Web Services, Inc. or its affiliates. All rights reserved. Notices This document is provided for informational purposes only. It represents AWS’s current product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS’s products or services, each of which is provided “as is” without warranty of any kind, whether express or implied. This document does not create any warranties, representations, contractual commitments, conditions or assurances from AWS, its affiliates, suppliers or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers. Page 2 of 42 Amazon Web Services – AWS KMS Cryptographic Details August 2016 Contents Abstract 4 Introduction 4 Design Goals 5 Background 7 Cryptographic Primitives 7 Basic Concepts 9 Customer’s Key Hierarchy 11 Use Cases 13 Amazon EBS Volume Encryption 13 Envelope Encryption 14 Customer Master Keys 17 Imported Master Keys 19 Enable and Disable Key 22 Key Deletion 22 Rotate Customer Master Key 23 Customer Data Operations 23 Application-Specific Data Keys 24 Encrypt 26 Decrypt 26 Re-Encrypting an Encrypted Object 28 Internal Communication Security 29 HSA Security Boundary 29 Quorum-Signed Commands 30 Authenticated Sessions 31 Domains and the Domain State 32 Page 3 of 42 Amazon Web Services – AWS KMS Cryptographic Details August 2016 Domain Keys 33 Exported Domain Tokens 33 Managing Domain State 34 Durability Protection 36 References 38 Appendix - Abbreviations and Keys 40 Abbreviations 40 Keys 41 Contributors 42 Document Revisions 42 Abstract AWS Key Management Service (AWS KMS) provides cryptographic keys and operations scaled for the cloud. -

Dell EMC Unity: Data at Rest Encryption a Detailed Review
Technical White Paper Dell EMC Unity: Data at Rest Encryption A Detailed Review Abstract This white paper explains the Data at Rest Encryption feature, which provides controller-based encryption of data stored on Dell EMC™ Unity storage systems to protect against unauthorized access to lost or stolen drives or system. The encryption technology as well as its implementation on Dell EMC Unity storage systems are discussed. June 2021 H15090.6 Revisions Revisions Date Description May 2016 Initial release – Unity OE 4.0 July 2017 Updated for Unity OE 4.2 June 2021 Template and format updates. Updated for Unity OE 5.1 Acknowledgments Author: Ryan Poulin The information in this publication is provided “as is.” Dell Inc. makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose. Use, copying, and distribution of any software described in this publication requires an applicable software license. This document may contain certain words that are not consistent with Dell's current language guidelines. Dell plans to update the document over subsequent future releases to revise these words accordingly. This document may contain language from third party content that is not under Dell's control and is not consistent with Dell's current guidelines for Dell's own content. When such third party content is updated by the relevant third parties, this document will be revised accordingly. Copyright © 2016-2021 Dell Inc. or its subsidiaries. All Rights Reserved. Dell Technologies, Dell, EMC, Dell EMC and other trademarks are trademarks of Dell Inc. -

DOCSIS 3.0 Security Specification
Data-Over-Cable Service Interface Specifications DOCSIS 3.0 Security Specification CM-SP-SEC3.0-C01-171207 CLOSED Notice This DOCSIS® specification is the result of a cooperative effort undertaken at the direction of Cable Television Laboratories, Inc. for the benefit of the cable industry and its customers. You may download, copy, distribute, and reference the documents herein only for the purpose of developing products or services in accordance with such documents, and educational use. Except as granted by CableLabs® in a separate written license agreement, no license is granted to modify the documents herein (except via the Engineering Change process), or to use, copy, modify or distribute the documents for any other purpose. This document may contain references to other documents not owned or controlled by CableLabs. Use and understanding of this document may require access to such other documents. Designing, manufacturing, distributing, using, selling, or servicing products, or providing services, based on this document may require intellectual property licenses from third parties for technology referenced in this document. To the extent this document contains or refers to documents of third parties, you agree to abide by the terms of any licenses associated with such third-party documents, including open source licenses, if any. Cable Television Laboratories, Inc., 2006-2017 CM-SP-SEC3.0-C01-171207 Data-Over-Cable Service Interface Specifications DISCLAIMER This document is furnished on an "AS IS" basis and neither CableLabs nor its members provides any representation or warranty, express or implied, regarding the accuracy, completeness, noninfringement, or fitness for a particular purpose of this document, or any document referenced herein. -

A Framework for Designing Cryptographic Key Management Systems
NIST Special Publication 800-130 A Framework for Designing Cryptographic Key Management Systems Elaine Barker Miles Smid Dennis Branstad Santosh Chokhani C O M P U T E R S E C U R I T Y NIST Special Publication 800-130 A Framework for Designing Cryptographic Key Management Systems Elaine Barker Computer Security Division Information Technology Laboratory Miles Smid Orion Security Solutions Silver, Spring, MD Dennis Branstad NIST Consultant Austin, TX Santosh Chokhani Cygnacom McLean, VA August 2013 U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary of Commerce for Standards and Technology and Director SP 800-130 August 2013 Authority This publication has been developed by NIST to further its statutory responsibilities under the Federal Information Security Management Act (FISMA), Public Law (P.L.) 107-347. NIST is responsible for developing information security standards and guidelines, including minimum requirements for Federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate Federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as analyzed in Circular A-130, Appendix IV: Analysis of Key Sections. Supplemental information is provided in Circular A-130, Appendix III, Security of Federal Automated Information Resources. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on Federal agencies by the Secretary of Commerce under statutory authority. -

LEVERAGING VENAFI TRUSTFORCE and A10 THUNDER ADC to SIMPLIFY CERTIFICATE MANAGEMENT Automate Management and Security of the Entire Certificate Lifecycle Process
SOLUTION BRIEF LEVERAGING VENAFI TRUSTFORCE AND A10 THUNDER ADC TO SIMPLIFY CERTIFICATE MANAGEMENT Automate Management and Security of the Entire Certificate Lifecycle Process Applications of all types have migrated to the web and use Secure Sockets Layer (SSL) Challenge: and Transport Layer Security (TLS) encryption to secure user sessions. To authenticate Organizations need to not only manage sites, organizations rely on cryptographic keys and digital certificates to establish trust the lifecycle of all digital certificates but for countless business activities. Such electronic countermeasures safeguard transactions ensure that any vulnerabilities are found and prevent spoofed sites and snooping by malevolent hackers or other cyber criminals. and automatically rectified. The difficulty Users gain confidence in such applications, allowing their use to flourish with an of this undertaking is magnified when exponential increase in productivity. certificates are configured on various network infrastructure elements. However, the very trust that keys and certificates establish has become a source of attack. When organizations instinctively trust keys and certificates, cybercriminals can Solution: turn compromised ones against them. Worse, organizations often have limited visibility A10 Networks Thunder ADC line of into their vulnerabilities and a restricted ability to respond to breaches. Offenders are Application Delivery Controllers is able to successfully steal data while remaining undetected for months, or even years. fully interoperable with Venafi’s Trust These key and certificate weaknesses lead to significant security risks that demand Protection Platform. Together, this joint immediate action. solution enables control over all digital certificates present, while allowing full Organizations must secure their key and certificate portfolio and identify their remediation of any anomalies. -

Encryption Key Management Policy
STATE OF DELAWARE DEPARTMENT OF TECHNOLOGY AND INFORMATION 801 Silver Lake Blvd. Dover, Delaware 19904 Doc Ref Number: SE-KEY-001 Revision Number: 0 Document Type: Enterprise Policy Page: 1 of 6 Policy Title: Encryption Key Management Policy Synopsis: This policy provides ways to securely handle encryption keys in order to avoid the loss of data in State of Delaware organizations. Authority: Title 29 Chapter 90C Delaware Code, §9004C – General Powers, duties and functions of DTI “2) Create, implement and enforce statewide and agency technology solutions, policies, standards and guidelines, including as recommended by the Technology Investment Council on an ongoing basis and the CIO” Applicability: This Policy is applicable to all users of the State of Delaware communications and computing resources. DTI is an Executive Branch Agency and has no authority over the customers in Legislative and Judicial Branches, as well as School Districts, and other Federal and Local Government entities that use these resources. However, all users, including these entities, must agree to abide by all policies, standards promulgated by DTI as a condition of access and continued use of these resources. Effective Date: 9/29/2009 Expiration Date: None POC for Changes: Solomon Adote, Chief Security Officer Approval By: Secretary Jason Clarke, Chief Information Officer Approved On: 9/29/2009 Reviewed Date: 9/27/2019 “Delivering Technology that Innovates” STATE OF DELAWARE DEPARTMENT OF TECHNOLOGY AND INFORMATION 801 Silver Lake Blvd. Dover, Delaware 19904 Doc Ref Number: SE-KEY-001 Revision Number: 0 Document Type: Enterprise Policy Page: 2 of 7 Policy Title: Encryption Key Management Policy TABLE OF CONTENTS Section Page I. -

Key Management for Secure Storage
An Introduction to Key Management for Secure Storage Walt Hubis, LSI Corporation SNIA Legal Notice The material contained in this tutorial is copyrighted by the SNIA. Member companies and individuals may use this material in presentations and literature under the following conditions: Any slide or slides used must be reproduced without modification The SNIA must be acknowledged as source of any material used in the body of any document containing material from these presentations. This presentation is a project of the SNIA Education Committee. An Introduction to Key Management for Secure Storage 2 © 2008 Storage Networking Industry Association. All Rights Reserved. Abstract An Introduction to Key Management for Secure Storage As secure storage becomes more pervasive throughout the enterprise, the focus quickly moves from implementing encrypting storage devices to establishing effective key management policies. Without the proper generation, distribution, storage, and recovery of key material, valuable data will be eventually compromised. Worse, without proper management of key information, data can be completely lost. This session explores the fundamental issues and technologies that impact key management for disk, tape, array, and other storage devices. Major issues associated symmetric encryption keys are presented, along with practical advice on effective key management issues and practices. An Introduction to Key Management for Secure Storage 3 © 2008 Storage Networking Industry Association. All Rights Reserved. The Key Management Problem An Introduction to Key Management for Secure Storage 4 © 2008 Storage Networking Industry Association. All Rights Reserved. The Key Management Problem An Introduction to Key Management for Secure Storage 5 © 2008 Storage Networking Industry Association. All Rights Reserved. -

AWS Key Management Service Cryptographic Details
AWS Key Management Service Cryptographic Details August 2018 This paper has been archived. For the latest technical content about AWS KMS Cryptographic Details, see https://docs.aws.amazon.com/kms/latest/cryptographic- details/intro.html Archived Amazon Web Services – AWS KMS Cryptographic Details August 2018 © 2018, Amazon Web Services, Inc. or its affiliates. All rights reserved. Notices This document is provided for informational purposes only. It represents the current AWS product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document. Any use of AWS products or services is provided “as is” without warranty of any kind, whether express or implied. This document does not create any warranties, representations, contractual commitments, conditions or assurances from AWS, its affiliates, suppliers, or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers. Archived Page 2 of 42 Amazon Web Services – AWS KMS Cryptographic Details August 2018 Contents Abstract 4 Introduction 4 Design Goals 6 Background 7 Cryptographic Primitives 7 Basic Concepts 10 Customer’s Key Hierarchy 11 Use Cases 13 Amazon EBS Volume Encryption 13 Client-side Encryption 15 Customer Master Keys 17 Imported Master Keys 19 Enable and Disable Key 22 Key Deletion 22 -

Recommendation for Key Management, Part 1: General Publication Date(S) January 2016 Withdrawal Date May 4, 2020 Withdrawal Note SP 800-57 Part 1 Rev
Withdrawn NIST Technical Series Publication Warning Notice The attached publication has been withdrawn (archived), and is provided solely for historical purposes. It may have been superseded by another publication (indicated below). Withdrawn Publication Series/Number NIST Special Publication 800-57 Part 1 Revision 4 Title Recommendation for Key Management, Part 1: General Publication Date(s) January 2016 Withdrawal Date May 4, 2020 Withdrawal Note SP 800-57 Part 1 Rev. 4 is superseded in its entirety by the publication of SP 800-57 Part 1 Rev. 5. Superseding Publication(s) (if applicable) The attached publication has been superseded by the following publication(s): Series/Number NIST Special Publication 800-57 Part 1 Revision 5 Title Recommendation for Key Management: Part 1 – General Author(s) Elaine Barker Publication Date(s) May 2020 URL/DOI https://doi.org/10.6028/NIST.SP.800-57pt1r5 Additional Information (if applicable) Contact Computer Security Division (Information Technology Laboratory) Latest revision of the attached publication Related Information https://csrc.nist.gov/projects/key-management/key-management-guidelines https://csrc.nist.gov/publications/detail/sp/800-57-part-1/rev-5/final Withdrawal Announcement Link Date updated: May 4, 2020 NIST Special Publication 800-57 Part 1 Revision 4 Recommendation for Key Management Part 1: General Elaine Barker This publication is available free of charge from: http://dx.doi.org/10.6028/NIST.SP.800-57pt1r4 C O M P U T E R S E C U R I T Y NIST Special Publication 800-57 Part 1 Revision 4 Recommendation for Key Management Part 1: General Elaine Barker Computer Security Division Information Technology Laboratory This publication is available free of charge from: http://dx.doi.org/10.6028/NIST.SP.800-57pt1r4 January 2016 U.S. -

Example:The Diffie-Hellman Key Exchange
Extreme minimality: Implicitly Authenticated KE Protocols 1 A natural Authenticated DH Solution (ISO 9796) A B A, gx y x y B, g , SIGB(g ,g ,A) y x SIGA(g ,g ,B) Simple, but 3 messages plus signatures [and certificates] 2 The quest for Authenticated DH What is the inherent cost of authentication in Diffie-Hellman? In terms of Communication: number of messages, group elements, authentication information, actual message size Computation: algebraic operations and actual speed Security: What can we prove? How close can we get to the fundamental limits? And still prove security… 3 Implicitly Authenticated DH A A, gx B B, gy Authentication via session key computation No transmitted signatures, MAC values, etc Session key must involve long-term and ephemeral keys: x y K=F(PKA,PKB,SKA,SKB ,g ,g ,x,y) Ability to compute key authentication The simpler the trickier: many insecure proposals 4 (Abuse of) Notation Public key of A (resp. B) denoted A=ga (resp. B=gb) A A=ga, X=gx B B=gb, Y=gy 5 Some Ideas Can we really have a non-replayable 2-msg protocol? x x y y Remember AB: g , SIGA(g ,B), AB: g , SIGB(g ,A) insecurity Combining A, B, X, Y: K=H(gab, gxy): Open to known key and interleaving attacks K=H(gab, gxy, gx, gy) works but open to “KCI attacks” (a general weakness of protocols with gab ) We want that no attack except if learning pair (x,a) or (y,b) Idea: K = g(a+x)(b+y) (computed by A as (BY)a+x, by B as (AX)b+y) Doesn’t work: Attacker sends X*=gx*/A, B sends Y, K=(BY)x* (no need to know A) 6 MQV Idea: set K = g(a+dx)(b+ey) and define d, e so that attacker cannot control e and Y, or d and X MQV: d=half bits of X, e=half bits of Y Does not quite work But a simple variation does 7 The HMQV Protocol 8 The HMQV Protocol Basic DH + special key computation * Notation: G=<g> of prime order q; g in supergroup G’ (eg.