Recommendation for Key Management, Part 1: General Publication Date(S) January 2016 Withdrawal Date May 4, 2020 Withdrawal Note SP 800-57 Part 1 Rev
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cryptography
56 Protecting Information With Cryptography Chapter by Peter Reiher (UCLA) 56.1 Introduction In previous chapters, we’ve discussed clarifying your security goals, determining your security policies, using authentication mechanisms to identify principals, and using access control mechanisms to enforce poli- cies concerning which principals can access which computer resources in which ways. While we identified a number of shortcomings and prob- lems inherent in all of these elements of securing your system, if we re- gard those topics as covered, what’s left for the operating system to worry about, from a security perspective? Why isn’t that everything? There are a number of reasons why we need more. Of particular im- portance: not everything is controlled by the operating system. But per- haps you respond, you told me the operating system is all-powerful! Not really. It has substantial control over a limited domain – the hardware on which it runs, using the interfaces of which it is given control. It has no real control over what happens on other machines, nor what happens if one of its pieces of hardware is accessed via some mechanism outside the operating system’s control. But how can we expect the operating system to protect something when the system does not itself control access to that resource? The an- swer is to prepare the resource for trouble in advance. In essence, we assume that we are going to lose the data, or that an opponent will try to alter it improperly. And we take steps to ensure that such actions don’t cause us problems. -

Advanced Encryption Standard Real-World Alternatives
Outline Multiple Encryption Birthday Attack Advanced Encryption Standard Real-World Alternatives CPSC 367: Cryptography and Security Michael Fischer Lecture 7 February 5, 2019 Thanks to Ewa Syta for the slides on AES CPSC 367, Lecture 7 1/58 Outline Multiple Encryption Birthday Attack Advanced Encryption Standard Real-World Alternatives Multiple Encryption Composition Group property Birthday Attack Advanced Encryption Standard AES Real-World Issues Alternative Private Key Block Ciphers CPSC 367, Lecture 7 2/58 Outline Multiple Encryption Birthday Attack Advanced Encryption Standard Real-World Alternatives Multiple Encryption CPSC 367, Lecture 7 3/58 Outline Multiple Encryption Birthday Attack Advanced Encryption Standard Real-World Alternatives Composition Composition of cryptosystems Encrypting a message multiple times with the same or different ciphers and keys seems to make the cipher stronger, but that's not always the case. The security of the composition can be difficult to analyze. For example, with the one-time pad, the encryption and decryption functions Ek and Dk are the same. The composition Ek ◦ Ek is the identity function! CPSC 367, Lecture 7 4/58 Outline Multiple Encryption Birthday Attack Advanced Encryption Standard Real-World Alternatives Composition Composition within practical cryptosystems Practical symmetric cryptosystems such as DES and AES are built as a composition of simpler systems. Each component offers little security by itself, but when composed, the layers obscure the message to the point that it is difficult for an adversary to recover. The trick is to find ciphers that successfully hide useful information from a would-be attacker when used in concert. CPSC 367, Lecture 7 5/58 Outline Multiple Encryption Birthday Attack Advanced Encryption Standard Real-World Alternatives Composition Double Encryption Double encryption is when a cryptosystem is composed with itself. -

Implementations of Block Cipher SEED on Smartphone Operating Systems
SECURWARE 2011 : The Fifth International Conference on Emerging Security Information, Systems and Technologies Implementations of Block Cipher SEED on Smartphone Operating Systems HwanJin Lee, DongHoon Shin, and Hyun-Chul Jung Security R&D Team Korea Internet & Security Agency (KISA) Seoul, Korea {lhj79, dhshin, hcjung}@kisa.or.kr Abstract—As more and more people are using smartphones limited power and offers inferior performance compared to a these days, a great deal of important information, such as PC. Therefore, it is difficult to use an open cryptographic personal information and the important documents of library such as OpenSSL, which is designed for the PC corporations among other things, are being saved on environment, in a smartphone. We need to study on the way smartphones. Unlike a PC, people can access another person’s for the effective use of SEED in smartphone. smartphone without great difficulty, and there is a high This paper presents the results of implementing the block possibility of losing one’s smartphone. If smartphone is lost cipher SEED to a smartphone. The results of a comparison without encryption, important information can be exploited. In with open cryptographic libraries (OpenSSL, BouncyCastle) addition, the open cryptographic library for PCs cannot be will also be presented. The SEED is a block cipher used due to the limited performance of the smartphone. This established as an international standard ISO/IEC and the paper introduces the optimization implementation technique for the smartphone OS and the results of using that technique. Korean standard. Section 2 introduces the SEED and open In addition, the results of a speed comparison with the open cryptographic libraries; Section 3 introduces smartphone cryptographic library will be presented. -

Using Address Independent Seed Encryption and Bonsai Merkle Trees to Make Secure Processors OS- and Performance-Friendly ∗
Using Address Independent Seed Encryption and Bonsai Merkle Trees to Make Secure Processors OS- and Performance-Friendly ∗ Brian Rogers, Siddhartha Chhabra, Yan Solihin Milos Prvulovic Dept. of Electrical and Computer Engineering College of Computing North Carolina State University Georgia Institute of Technology {bmrogers, schhabr, solihin}@ncsu.edu [email protected] Abstract and feasible threat is physical or hardware attacks which involve placing a bus analyzer that snoops data communicated between the In today’s digital world, computer security issues have become processor chip and other chips [7, 8]. Although physical attacks increasingly important. In particular, researchers have proposed may be more difficult to perform than software-based attacks, they designs for secure processors which utilize hardware-based mem- are very powerful as they can bypass any software security protec- ory encryption and integrity verification to protect the privacy and tion employed in the system. The proliferation of mod-chips that integrity of computation even from sophisticated physical attacks. bypass Digital Rights Management protection in game systems has However, currently proposed schemes remain hampered by prob- demonstrated that given sufficient financial payoffs, physical attacks lems that make them impractical for use in today’s computer sys- are very realistic threats. tems: lack of virtual memory and Inter-Process Communication Recognizing these threats, computer architecture researchers support as well as excessive storage and performance overheads. have recently proposed various types of secure processor architec- In this paper, we propose 1) Address Independent Seed Encryption tures [4, 5, 13, 14, 16, 17, 18, 19, 20, 22, 23, 24, 25, 26]. Secure pro- (AISE), a counter-mode based memory encryption scheme using a cessors assume that off-chip communication is vulnerable to attack novel seed composition, and 2) Bonsai Merkle Trees (BMT), a novel and that the chip boundary provides a natural security boundary. -

PCI Assessment Evidence of PCI Policy Compliance
PCI Assessment Evidence of PCI Policy Compliance CONFIDENTIALITY NOTE: The information contained in this report document is for the Prepared for: exclusive use of the client specified above and may contain confidential, privileged and non-disclosable information. If the recipient of this report is not the client or Prospect or Customer addressee, such recipient is strictly prohibited from reading, photocopying, distributing or otherwise using this report or its contents in any way. Prepared by: Your Company Name Evidence of PCI Policy Compliance PCI ASSESSMENT Table of Contents 1 - Overview 1.1 - Security Officer 1.2 - Overall Risk 2 - PCI DSS Evidence of Compliance 2.1 - Install and maintain firewall to protect cardholder data 2.1.1.1 - Requirements for firewall at each Internet connections and between DMZ and internal network zone 2.1.1.2 - Business justification for use of all services, protocols and ports allowed 2.1.2 - Build firewall and router configurations that restrict connections between untrusted networks and the cardholder data environment 2.1.2.1 - Restrict inbound and outbound to that which is necessary for the cardholder data environment 2.1.2.3 - Do not allow unauthorized outbound traffic from the cardholder data environment to the Internet 2.1.2.4 - Implement stateful inspection (also known as dynamic packet filtering) 2.1.2.5 - Do not allow unauthorized outbound traffic from the cardholder data environment to the Internet 2.2 - Prohibition of vendor-supplied default password for systems and security parameters 2.2.1 -

Self-Encrypting Deception: Weaknesses in the Encryption of Solid State Drives
Self-encrypting deception: weaknesses in the encryption of solid state drives Carlo Meijer Bernard van Gastel Institute for Computing and Information Sciences School of Computer Science Radboud University Nijmegen Open University of the Netherlands [email protected] and Institute for Computing and Information Sciences Radboud University Nijmegen Bernard.vanGastel@{ou.nl,ru.nl} Abstract—We have analyzed the hardware full-disk encryption full-disk encryption. Full-disk encryption software, especially of several solid state drives (SSDs) by reverse engineering their those integrated in modern operating systems, may decide to firmware. These drives were produced by three manufacturers rely solely on hardware encryption in case it detects support between 2014 and 2018, and are both internal models using the SATA and NVMe interfaces (in a M.2 or 2.5" traditional form by the storage device. In case the decision is made to rely on factor) and external models using the USB interface. hardware encryption, typically software encryption is disabled. In theory, the security guarantees offered by hardware encryp- As a primary example, BitLocker, the full-disk encryption tion are similar to or better than software implementations. In software built into Microsoft Windows, switches off software reality, we found that many models using hardware encryption encryption and completely relies on hardware encryption by have critical security weaknesses due to specification, design, and implementation issues. For many models, these security default if the drive advertises support. weaknesses allow for complete recovery of the data without Contribution. This paper evaluates both internal and external knowledge of any secret (such as the password). -

FIPS 140-2 Non-Proprietary Security Policy Oracle Linux 7 NSS
FIPS 140-2 Non-Proprietary Security Policy Oracle Linux 7 NSS Cryptographic Module FIPS 140-2 Level 1 Validation Software Version: R7-4.0.0 Date: January 22nd, 2020 Document Version 2.3 © Oracle Corporation This document may be reproduced whole and intact including the Copyright notice. Title: Oracle Linux 7 NSS Cryptographic Module Security Policy Date: January 22nd, 2020 Author: Oracle Security Evaluations – Global Product Security Contributing Authors: Oracle Linux Engineering Oracle Corporation World Headquarters 500 Oracle Parkway Redwood Shores, CA 94065 U.S.A. Worldwide Inquiries: Phone: +1.650.506.7000 Fax: +1.650.506.7200 oracle.com Copyright © 2020, Oracle and/or its affiliates. All rights reserved. This document is provided for information purposes only and the contents hereof are subject to change without notice. This document is not warranted to be error-free, nor subject to any other warranties or conditions, whether expressed orally or implied in law, including implied warranties and conditions of merchantability or fitness for a particular purpose. Oracle specifically disclaim any liability with respect to this document and no contractual obligations are formed either directly or indirectly by this document. This document may reproduced or distributed whole and intact including this copyright notice. Oracle and Java are registered trademarks of Oracle and/or its affiliates. Other names may be trademarks of their respective owners. Oracle Linux 7 NSS Cryptographic Module Security Policy i TABLE OF CONTENTS Section Title -
Diffie-Hellman (1976) – RSA (1977) – More Recently: ID-Based Encryption (2001), Functional Encryption (2011)…
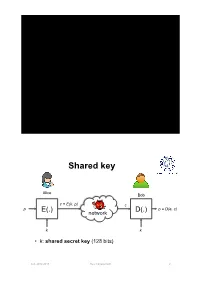
Key Management Shared key Alice Bob c = E(k, p) c p E(.) D(.) p = D(e, c) network k k • k: shared secret key (128 bits) A.A. 2012-2013 Key management 2 Pairwise keys • Each pair of users shares an long-term secret key Alice Bob • Properties • Every user stores (n -1) keys • The overall number of keys is O(n2) Carol Eve Dave A.A. 2012-2013 Key management 3 Pairwise keys • Pros – If a subject is compromised only its communications are compromised; • communications between two other subjects are not compromised • We cannot do any better! • Cons – Poor scalability: the number of keys is quadratic in the number of subjects – Poor scalability: a new member’s joining and a member’s leaving affect all current members A.A. 2012-2013 Key management 4 Trusted Third Party • Online Trusted Third Party (TTP) – Each user shares a long-term secret key with TTP TTP – Every user stores one key – The overall number of keys is n KA KB • TTP is a single point of failure – TTP must be always online A B – TTP knows all the keys • TTP can read all msg between Alice and Bob KAB • TTP can impersonate any party A.A. 2012-2013 Key management 5 Key distribution: a toy protocol Alice wants a shared key with Bob. Eavesdropping security only Bob (kB) Alice (kA) TTP “Alice wants key with Bob” choose E(KA, “A, B” || KAB) random kAB ticket ticket ← E(KB, “A, B” || KAB) kAB kAB Subject to replay attacks A.A. 2012-2013 Key management 6 Key distribution: toy protocol • Insecure against replay attacks (active adversary) – Attacker records session between Alice and merchant Bob • For example: an order – Attacker replays session to Bob • Bob thinks Alice is ordering another copy of the book A.A. -

Cryptographic Control Standard, Version
Nuclear Regulatory Commission Office of the Chief Information Officer Computer Security Standard Office Instruction: OCIO-CS-STD-2009 Office Instruction Title: Cryptographic Control Standard Revision Number: 2.0 Issuance: Date of last signature below Effective Date: October 1, 2017 Primary Contacts: Kathy Lyons-Burke, Senior Level Advisor for Information Security Responsible Organization: OCIO Summary of Changes: OCIO-CS-STD-2009, “Cryptographic Control Standard,” provides the minimum security requirements that must be applied to the Nuclear Regulatory Commission (NRC) systems which utilize cryptographic algorithms, protocols, and cryptographic modules to provide secure communication services. This update is based on the latest versions of the National Institute of Standards and Technology (NIST) Guidance and Federal Information Processing Standards (FIPS) publications, Committee on National Security System (CNSS) issuances, and National Security Agency (NSA) requirements. Training: Upon request ADAMS Accession No.: ML17024A095 Approvals Primary Office Owner Office of the Chief Information Officer Signature Date Enterprise Security Kathy Lyons-Burke 09/26/17 Architecture Working Group Chair CIO David Nelson /RA/ 09/26/17 CISO Jonathan Feibus 09/26/17 OCIO-CS-STD-2009 Page i TABLE OF CONTENTS 1 PURPOSE ............................................................................................................................. 1 2 INTRODUCTION .................................................................................................................. -

Ansi/Scte 23-2 2017
ENGINEERING COMMITTEE Data Standards Subcommittee AMERICAN NATIONAL STANDARD ANSI/SCTE 23-2 2017 DOCSIS 1.1 Part 2: Baseline Privacy Plus Interface ANSI/SCTE 23-2 2017 NOTICE The Society of Cable Telecommunications Engineers (SCTE) Standards and Operational Practices (hereafter called “documents”) are intended to serve the public interest by providing specifications, test methods and procedures that promote uniformity of product, interchangeability, best practices and ultimately the long term reliability of broadband communications facilities. These documents shall not in any way preclude any member or non-member of SCTE from manufacturing or selling products not conforming to such documents, nor shall the existence of such standards preclude their voluntary use by those other than SCTE members. SCTE assumes no obligations or liability whatsoever to any party who may adopt the documents. Such adopting party assumes all risks associated with adoption of these documents, and accepts full responsibility for any damage and/or claims arising from the adoption of such documents. Attention is called to the possibility that implementation of this document may require the use of subject matter covered by patent rights. By publication of this document, no position is taken with respect to the existence or validity of any patent rights in connection therewith. SCTE shall not be responsible for identifying patents for which a license may be required or for conducting inquiries into the legal validity or scope of those patents that are brought to its attention. Patent holders who believe that they hold patents which are essential to the implementation of this document have been requested to provide information about those patents and any related licensing terms and conditions. -

AWS Key Management Service Cryptographic Details
AWS Key Management Service Cryptographic Details August 2016 Amazon Web Services – AWS KMS Cryptographic Details August 2016 © 2016, Amazon Web Services, Inc. or its affiliates. All rights reserved. Notices This document is provided for informational purposes only. It represents AWS’s current product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS’s products or services, each of which is provided “as is” without warranty of any kind, whether express or implied. This document does not create any warranties, representations, contractual commitments, conditions or assurances from AWS, its affiliates, suppliers or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers. Page 2 of 42 Amazon Web Services – AWS KMS Cryptographic Details August 2016 Contents Abstract 4 Introduction 4 Design Goals 5 Background 7 Cryptographic Primitives 7 Basic Concepts 9 Customer’s Key Hierarchy 11 Use Cases 13 Amazon EBS Volume Encryption 13 Envelope Encryption 14 Customer Master Keys 17 Imported Master Keys 19 Enable and Disable Key 22 Key Deletion 22 Rotate Customer Master Key 23 Customer Data Operations 23 Application-Specific Data Keys 24 Encrypt 26 Decrypt 26 Re-Encrypting an Encrypted Object 28 Internal Communication Security 29 HSA Security Boundary 29 Quorum-Signed Commands 30 Authenticated Sessions 31 Domains and the Domain State 32 Page 3 of 42 Amazon Web Services – AWS KMS Cryptographic Details August 2016 Domain Keys 33 Exported Domain Tokens 33 Managing Domain State 34 Durability Protection 36 References 38 Appendix - Abbreviations and Keys 40 Abbreviations 40 Keys 41 Contributors 42 Document Revisions 42 Abstract AWS Key Management Service (AWS KMS) provides cryptographic keys and operations scaled for the cloud. -

Preliminary Analysis: SEED’S First Year
SEED Findings Summary stocktondemonstration.org Preliminary Analysis: SEED’s First Year AUTHORS: CONTRIBUTING RESEARCHERS: Dr. Stacia West, Mina Addo, Mae Carlson, Dr. Amy Castro Baker, Conway Homes Residents Council, Sukhi Samra, Pandora Crowder, Meagan Cusack, Stacy Elliott, Erin Coltrera Daniel Horn, Jenna Steckel, Tooma Zaghloul Preliminary Analysis: SEED's First Year Executive Summary “ Poverty is the biggest issue. Everything we deal with stems from that. There’s so many people working incredibly hard, and if life happens, there’s no bottom. “ —Michael D. Tubbs The Stockton Economic Empowerment Key Findings Include: Demonstration, or SEED, was the nation’s • Guaranteed income reduced income volatility, first mayor-led guaranteed income initiative. or the month-to-month income fluctuations Launched in February 2019 by former Mayor that households face. Michael D. Tubbs, SEED gave 125 Stocktonians $500 per month for 24 months. The cash was • Unconditional cash enabled recipients unconditional, with no strings attached and no to find full-time employment. work requirements. • Recipients of guaranteed income were This Randomized Control Trial (RCT) pilot is being healthier, showing less depression and anxiety evaluated by a team of independent researchers, and enhanced wellbeing. Dr. Stacia West of the University of Tennessee • The guaranteed income alleviated financial and Dr. Amy Castro Baker of the University of scarcity creating new opportunities for Pennsylvania, and funded by the Evidence for self-determination, choice, goal-setting, Action Program at the Robert Wood Johnson and risk-taking. Foundation. SEED sought to confront, address, and humanize Our primary research questions are the following: some of the most pressing and pernicious How does guaranteed income impact problems our country faces: inequality, income income volatility? How do changes in income volatility, and poverty.