Dell EMC Unity: Data at Rest Encryption a Detailed Review
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Operating System Boot from Fully Encrypted Device
Masaryk University Faculty of Informatics Operating system boot from fully encrypted device Bachelor’s Thesis Daniel Chromik Brno, Fall 2016 Replace this page with a copy of the official signed thesis assignment and the copy of the Statement of an Author. Declaration Hereby I declare that this paper is my original authorial work, which I have worked out by my own. All sources, references and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Daniel Chromik Advisor: ing. Milan Brož i Acknowledgement I would like to thank my advisor, Ing. Milan Brož, for his guidance and his patience of a saint. Another round of thanks I would like to send towards my family and friends for their support. ii Abstract The goal of this work is description of existing solutions for boot- ing Linux and Windows from fully encrypted devices with Secure Boot. Before that, though, early boot process and bootloaders are de- scribed. A simple Linux distribution is then set up to boot from a fully encrypted device. And lastly, existing Windows encryption solutions are described. iii Keywords boot process, Linux, Windows, disk encryption, GRUB 2, LUKS iv Contents 1 Introduction ............................1 1.1 Thesis goals ..........................1 1.2 Thesis structure ........................2 2 Boot Process Description ....................3 2.1 Early Boot Process ......................3 2.2 Firmware interfaces ......................4 2.2.1 BIOS – Basic Input/Output System . .4 2.2.2 UEFI – Unified Extended Firmware Interface .5 2.3 Partitioning tables ......................5 2.3.1 MBR – Master Boot Record . -

Crypto Wars of the 1990S
Danielle Kehl, Andi Wilson, and Kevin Bankston DOOMED TO REPEAT HISTORY? LESSONS FROM THE CRYPTO WARS OF THE 1990S CYBERSECURITY June 2015 | INITIATIVE © 2015 NEW AMERICA This report carries a Creative Commons license, which permits non-commercial re-use of New America content when proper attribution is provided. This means you are free to copy, display and distribute New America’s work, or in- clude our content in derivative works, under the following conditions: ATTRIBUTION. NONCOMMERCIAL. SHARE ALIKE. You must clearly attribute the work You may not use this work for If you alter, transform, or build to New America, and provide a link commercial purposes without upon this work, you may distribute back to www.newamerica.org. explicit prior permission from the resulting work only under a New America. license identical to this one. For the full legal code of this Creative Commons license, please visit creativecommons.org. If you have any questions about citing or reusing New America content, please contact us. AUTHORS Danielle Kehl, Senior Policy Analyst, Open Technology Institute Andi Wilson, Program Associate, Open Technology Institute Kevin Bankston, Director, Open Technology Institute ABOUT THE OPEN TECHNOLOGY INSTITUTE ACKNOWLEDGEMENTS The Open Technology Institute at New America is committed to freedom The authors would like to thank and social justice in the digital age. To achieve these goals, it intervenes Hal Abelson, Steven Bellovin, Jerry in traditional policy debates, builds technology, and deploys tools with Berman, Matt Blaze, Alan David- communities. OTI brings together a unique mix of technologists, policy son, Joseph Hall, Lance Hoffman, experts, lawyers, community organizers, and urban planners to examine the Seth Schoen, and Danny Weitzner impacts of technology and policy on people, commerce, and communities. -

CLOUDIQ DETAILED REVIEW a Proactive Monitoring and Analytics Application for Dell EMC™ Storage Systems
CLOUDIQ DETAILED REVIEW A Proactive Monitoring and Analytics Application for Dell EMC™ Storage Systems Efficiency Flash Health Scores Performance Notifications ABSTRACT This white paper introduces Dell EMC™ CloudIQ, a free, cloud-native application that lets you easily monitor, analyze, and troubleshoot your Dell EMC Unity, SC Series, XtremIO, and PowerMax/VMAX systems from anywhere and at any time. This paper provides a detailed description of how to use CloudIQ to proactively monitor and troubleshoot Dell EMC storage systems. January 2019 1 The information in this publication is provided “as is.” Dell Inc. makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose. Use, copying, and distribution of any software described in this publication requires an applicable software license. Copyright © 2018 Dell Inc. or its subsidiaries. All Rights Reserved. Dell EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be the property of their respective owners. Published in the USA [1/2019] [White Paper] [H15691.4] Dell EMC believes the information in this document is accurate as of its publication date. The information is subject to change without notice. TABLE OF CONTENTS EXECUTIVE SUMMARY ...........................................................................................................5 Audience .......................................................................................................................................... -

Self-Encrypting Deception: Weaknesses in the Encryption of Solid State Drives
Self-encrypting deception: weaknesses in the encryption of solid state drives Carlo Meijer Bernard van Gastel Institute for Computing and Information Sciences School of Computer Science Radboud University Nijmegen Open University of the Netherlands [email protected] and Institute for Computing and Information Sciences Radboud University Nijmegen Bernard.vanGastel@{ou.nl,ru.nl} Abstract—We have analyzed the hardware full-disk encryption full-disk encryption. Full-disk encryption software, especially of several solid state drives (SSDs) by reverse engineering their those integrated in modern operating systems, may decide to firmware. These drives were produced by three manufacturers rely solely on hardware encryption in case it detects support between 2014 and 2018, and are both internal models using the SATA and NVMe interfaces (in a M.2 or 2.5" traditional form by the storage device. In case the decision is made to rely on factor) and external models using the USB interface. hardware encryption, typically software encryption is disabled. In theory, the security guarantees offered by hardware encryp- As a primary example, BitLocker, the full-disk encryption tion are similar to or better than software implementations. In software built into Microsoft Windows, switches off software reality, we found that many models using hardware encryption encryption and completely relies on hardware encryption by have critical security weaknesses due to specification, design, and implementation issues. For many models, these security default if the drive advertises support. weaknesses allow for complete recovery of the data without Contribution. This paper evaluates both internal and external knowledge of any secret (such as the password). -

Zenworks 2017 Update 4 Troubleshooting Full Disk Encryption January 2019
ZENworks 2017 Update 4 Troubleshooting Full Disk Encryption January 2019 This document provides troubleshooting guidelines for common problems related to ZENworks Full Disk Encryption. If, after completing the troubleshooting steps, the problem is not resolved, you should contact Technical Support (https://www.novell.com/support/) for additional help. 1 Windows PE Emergency Recovery Disk (ERD) is not working Make sure you have installed the correct WAIK architecture (32-bit vs 64-bit) (Windows 7 only) If you manually created the ERD, use the PowerShell script provided in the Cool Solutions “Windows Powershell script to create a Windows PE emergency recovery disk for ZENworks Full Disk Encryption” article. Try creating the ERD using the ADK for Windows instead of Windows AIK. See “Creating a Windows PE Emergency Recovery Disk” in the ZENworks Full Disk Encryption Emergency Recovery Reference. Try burning the ERD to a DVD rather than a CD. 2 Issues with PBA login or boot sequence After pre-boot authentication occurs, the BIOS or UEFI settings must be correctly set for Windows. With unusual DMI hardware configurations, the standard ZENworks PBA boot method and Linux kernel configuration used to provide the BIOS settings, might not work, resulting in hardware that does not function correctly or is not recognized by Windows. Beginning in ZENworks 2017 Update 2, the Full Disk Encryption Agent includes DMI menu options to repair the boot sequence for issues relating to these DMI configurations. This menu is accessible by using the Ctrl + G keyboard command at a brief point when Full Disk Encryption is shown during a device restart. -
Diffie-Hellman (1976) – RSA (1977) – More Recently: ID-Based Encryption (2001), Functional Encryption (2011)…
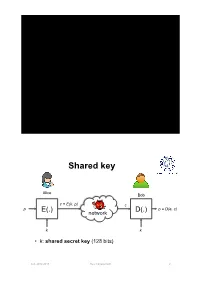
Key Management Shared key Alice Bob c = E(k, p) c p E(.) D(.) p = D(e, c) network k k • k: shared secret key (128 bits) A.A. 2012-2013 Key management 2 Pairwise keys • Each pair of users shares an long-term secret key Alice Bob • Properties • Every user stores (n -1) keys • The overall number of keys is O(n2) Carol Eve Dave A.A. 2012-2013 Key management 3 Pairwise keys • Pros – If a subject is compromised only its communications are compromised; • communications between two other subjects are not compromised • We cannot do any better! • Cons – Poor scalability: the number of keys is quadratic in the number of subjects – Poor scalability: a new member’s joining and a member’s leaving affect all current members A.A. 2012-2013 Key management 4 Trusted Third Party • Online Trusted Third Party (TTP) – Each user shares a long-term secret key with TTP TTP – Every user stores one key – The overall number of keys is n KA KB • TTP is a single point of failure – TTP must be always online A B – TTP knows all the keys • TTP can read all msg between Alice and Bob KAB • TTP can impersonate any party A.A. 2012-2013 Key management 5 Key distribution: a toy protocol Alice wants a shared key with Bob. Eavesdropping security only Bob (kB) Alice (kA) TTP “Alice wants key with Bob” choose E(KA, “A, B” || KAB) random kAB ticket ticket ← E(KB, “A, B” || KAB) kAB kAB Subject to replay attacks A.A. 2012-2013 Key management 6 Key distribution: toy protocol • Insecure against replay attacks (active adversary) – Attacker records session between Alice and merchant Bob • For example: an order – Attacker replays session to Bob • Bob thinks Alice is ordering another copy of the book A.A. -
Dell Emc Unity Hybrid Storage
SPECIFICATION SHEET DELL EMC UNITY HYBRID STORAGE The ultimate in simplicity & unifieD flash value The Dell EMC Unity™ HybriD-Flash proDuct line sets new stanDarDs for storage with compelling simplicity, moDern design, flexible deployments and affordable prices– to meet the neeDs of resource-constraineD IT professionals in large or small companies. If you are looking for rich features anD absolute simplicity in a small footprint, if you are cost-conscious anD need the best from the best, Dell EMC Unity HybriD Flash is for you. DesigneD for flash with rich Data services, it delivers flash performance with the cost advantage of disk. Architecture BaseD on the powerful new family of Intel E5-2600 processors, Dell EMC Unity HybriD storage systems implement an integrateD architecture for block, file, anD VMware VVols with concurrent support for native NAS, iSCSI, anD Fibre Channel protocols. Each system leverages Dual storage processors, full 12 Gb SAS back end connectivity and Dell EMC’s patenteD multicore architecteD operating environment to Deliver unparalleleD performance & efficiency. AdDitional storage capacity is aDDeD via Disk Array Enclosures (DAEs) and for additional performance, online controller upgrades are available. Physical Specifications 300 400 500 600 Min/Max Drives 5/150 5/250 5/500 5/1000 Array Enclosure There are 2 versions: A 2U Disk Processor Enclosure (DPE) with twenty five 2.5” drives and a 2U Disk Processor Enclosure with twelve 3.5” Drives. Drive Enclosure (DAE - All moDels support 2U twenty five drive trays for 2.5” drives, 3U fifteen drive trays for 3.5” drives, anD 3U eighty drive Disk Array Enclosure) trays for 2.5” drives Dell EMC Unity systems are powereD by 2 power supplies (PS) per DPE/DAE. -

Ansi/Scte 23-2 2017
ENGINEERING COMMITTEE Data Standards Subcommittee AMERICAN NATIONAL STANDARD ANSI/SCTE 23-2 2017 DOCSIS 1.1 Part 2: Baseline Privacy Plus Interface ANSI/SCTE 23-2 2017 NOTICE The Society of Cable Telecommunications Engineers (SCTE) Standards and Operational Practices (hereafter called “documents”) are intended to serve the public interest by providing specifications, test methods and procedures that promote uniformity of product, interchangeability, best practices and ultimately the long term reliability of broadband communications facilities. These documents shall not in any way preclude any member or non-member of SCTE from manufacturing or selling products not conforming to such documents, nor shall the existence of such standards preclude their voluntary use by those other than SCTE members. SCTE assumes no obligations or liability whatsoever to any party who may adopt the documents. Such adopting party assumes all risks associated with adoption of these documents, and accepts full responsibility for any damage and/or claims arising from the adoption of such documents. Attention is called to the possibility that implementation of this document may require the use of subject matter covered by patent rights. By publication of this document, no position is taken with respect to the existence or validity of any patent rights in connection therewith. SCTE shall not be responsible for identifying patents for which a license may be required or for conducting inquiries into the legal validity or scope of those patents that are brought to its attention. Patent holders who believe that they hold patents which are essential to the implementation of this document have been requested to provide information about those patents and any related licensing terms and conditions. -

Disk Encryption with 100Gbe Crypto Accelerator
Disk Encryption with 100GbE Crypto Accelerator Chelsio T6 vs. Intel AES-NI vs. Software Enabled Encryption Executive Summary Chelsio Crypto Accelerator is a co-processor designed specifically to perform computationally intensive cryptographic operations more efficiently than general-purpose CPUs. Servers with system load, comprising of cryptographic operations, see great performance improvement by offloading crypto operations on to the Chelsio Unified Wire adapter. Chelsio’s solution uses the standard crypto API framework provided by the operating system and enables the offloading of crypto operations to the adapter. This paper showcases the disk encryption acceleration capabilities of Chelsio T6 adapters by comparing its performance with Intel AES-NI and software encryption. Chelsio solution excels with 100Gbps Crypto rate performance for both encryption and decryption with less than 50% CPU usage. Chelsio’s T6 encryption solution assures complete data protection to datacenters, while providing substantial savings on CPU and memory. Chelsio Disk Encryption Offload The Terminator 6 (T6) ASIC from Chelsio Communications, Inc. is a sixth generation, high performance 1/10/25/40/50/100Gbps unified wire engine which offers crypto offload capability for AES and SHA variants. Chelsio’s disk encryption solution is a special case of data at rest protection where the storage media is a sector-addressable device. Chelsio offloads the AES-XTS mode, which is designed for encrypting data stored on hard disks where there is no additional space for an integrity field. AES-XTS builds on the security of AES by protecting the storage device from many dictionary and copy/paste attacks. Chelsio crypto driver registers with the kernel crypto framework with high priority and ensures that any disk encryption request is offloaded and processed by T6 adapter. -

Speeding up Linux Disk Encryption Ignat Korchagin @Ignatkn $ Whoami
Speeding Up Linux Disk Encryption Ignat Korchagin @ignatkn $ whoami ● Performance and security at Cloudflare ● Passionate about security and crypto ● Enjoy low level programming @ignatkn Encrypting data at rest The storage stack applications @ignatkn The storage stack applications filesystems @ignatkn The storage stack applications filesystems block subsystem @ignatkn The storage stack applications filesystems block subsystem storage hardware @ignatkn Encryption at rest layers applications filesystems block subsystem SED, OPAL storage hardware @ignatkn Encryption at rest layers applications filesystems LUKS/dm-crypt, BitLocker, FileVault block subsystem SED, OPAL storage hardware @ignatkn Encryption at rest layers applications ecryptfs, ext4 encryption or fscrypt filesystems LUKS/dm-crypt, BitLocker, FileVault block subsystem SED, OPAL storage hardware @ignatkn Encryption at rest layers DBMS, PGP, OpenSSL, Themis applications ecryptfs, ext4 encryption or fscrypt filesystems LUKS/dm-crypt, BitLocker, FileVault block subsystem SED, OPAL storage hardware @ignatkn Storage hardware encryption Pros: ● it’s there ● little configuration needed ● fully transparent to applications ● usually faster than other layers @ignatkn Storage hardware encryption Pros: ● it’s there ● little configuration needed ● fully transparent to applications ● usually faster than other layers Cons: ● no visibility into the implementation ● no auditability ● sometimes poor security https://support.microsoft.com/en-us/help/4516071/windows-10-update-kb4516071 @ignatkn Block -

AWS Key Management Service Cryptographic Details
AWS Key Management Service Cryptographic Details August 2016 Amazon Web Services – AWS KMS Cryptographic Details August 2016 © 2016, Amazon Web Services, Inc. or its affiliates. All rights reserved. Notices This document is provided for informational purposes only. It represents AWS’s current product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS’s products or services, each of which is provided “as is” without warranty of any kind, whether express or implied. This document does not create any warranties, representations, contractual commitments, conditions or assurances from AWS, its affiliates, suppliers or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers. Page 2 of 42 Amazon Web Services – AWS KMS Cryptographic Details August 2016 Contents Abstract 4 Introduction 4 Design Goals 5 Background 7 Cryptographic Primitives 7 Basic Concepts 9 Customer’s Key Hierarchy 11 Use Cases 13 Amazon EBS Volume Encryption 13 Envelope Encryption 14 Customer Master Keys 17 Imported Master Keys 19 Enable and Disable Key 22 Key Deletion 22 Rotate Customer Master Key 23 Customer Data Operations 23 Application-Specific Data Keys 24 Encrypt 26 Decrypt 26 Re-Encrypting an Encrypted Object 28 Internal Communication Security 29 HSA Security Boundary 29 Quorum-Signed Commands 30 Authenticated Sessions 31 Domains and the Domain State 32 Page 3 of 42 Amazon Web Services – AWS KMS Cryptographic Details August 2016 Domain Keys 33 Exported Domain Tokens 33 Managing Domain State 34 Durability Protection 36 References 38 Appendix - Abbreviations and Keys 40 Abbreviations 40 Keys 41 Contributors 42 Document Revisions 42 Abstract AWS Key Management Service (AWS KMS) provides cryptographic keys and operations scaled for the cloud. -

The Growing Impact of Full Disk Encryption on Digital Forensics
digital investigation 8 (2011) 129e134 Available online at www.sciencedirect.com journal homepage: www.elsevier.com/locate/diin The growing impact of full disk encryption on digital forensics Eoghan Casey a,*, Geoff Fellows b, Matthew Geiger c, Gerasimos Stellatos d a cmdLabs, 1101 E. 33rd Street, Suite C301, Baltimore, MD 21218, United States b LG Training Partnership, United Kingdom c CERT, United States d CACI International, United States article info abstract Article history: The increasing use of full disk encryption (FDE) can significantly hamper digital investi- Received 16 March 2011 gations, potentially preventing access to all digital evidence in a case. The practice of Received in revised form shutting down an evidential computer is not an acceptable technique when dealing with 17 September 2011 FDE or even volume encryption because it may result in all data on the device being Accepted 24 September 2011 rendered inaccessible for forensic examination. To address this challenge, there is a pressing need for more effective on-scene capabilities to detect and preserve encryption Keywords: prior to pulling the plug. In addition, to give digital investigators the best chance of Digital forensics obtaining decrypted data in the field, prosecutors need to prepare search warrants with Full disk encryption FDE in mind. This paper describes how FDE has hampered past investigations, and how Hard drive encryption circumventing FDE has benefited certain cases. This paper goes on to provide guidance for Volatile data gathering items at the crime scene that may be useful for accessing encrypted data, and for Memory forensics performing on-scene forensic acquisitions of live computer systems.