The Simple Guide to Encryption Key Management
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Public-Key Cryptography
Public Key Cryptography EJ Jung Basic Public Key Cryptography public key public key ? private key Alice Bob Given: Everybody knows Bob’s public key - How is this achieved in practice? Only Bob knows the corresponding private key Goals: 1. Alice wants to send a secret message to Bob 2. Bob wants to authenticate himself Requirements for Public-Key Crypto ! Key generation: computationally easy to generate a pair (public key PK, private key SK) • Computationally infeasible to determine private key PK given only public key PK ! Encryption: given plaintext M and public key PK, easy to compute ciphertext C=EPK(M) ! Decryption: given ciphertext C=EPK(M) and private key SK, easy to compute plaintext M • Infeasible to compute M from C without SK • Decrypt(SK,Encrypt(PK,M))=M Requirements for Public-Key Cryptography 1. Computationally easy for a party B to generate a pair (public key KUb, private key KRb) 2. Easy for sender to generate ciphertext: C = EKUb (M ) 3. Easy for the receiver to decrypt ciphertect using private key: M = DKRb (C) = DKRb[EKUb (M )] Henric Johnson 4 Requirements for Public-Key Cryptography 4. Computationally infeasible to determine private key (KRb) knowing public key (KUb) 5. Computationally infeasible to recover message M, knowing KUb and ciphertext C 6. Either of the two keys can be used for encryption, with the other used for decryption: M = DKRb[EKUb (M )] = DKUb[EKRb (M )] Henric Johnson 5 Public-Key Cryptographic Algorithms ! RSA and Diffie-Hellman ! RSA - Ron Rives, Adi Shamir and Len Adleman at MIT, in 1977. • RSA -

Public Key Cryptography And
PublicPublic KeyKey CryptographyCryptography andand RSARSA Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 [email protected] Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse571-11/ Washington University in St. Louis CSE571S ©2011 Raj Jain 9-1 OverviewOverview 1. Public Key Encryption 2. Symmetric vs. Public-Key 3. RSA Public Key Encryption 4. RSA Key Construction 5. Optimizing Private Key Operations 6. RSA Security These slides are based partly on Lawrie Brown’s slides supplied with William Stallings’s book “Cryptography and Network Security: Principles and Practice,” 5th Ed, 2011. Washington University in St. Louis CSE571S ©2011 Raj Jain 9-2 PublicPublic KeyKey EncryptionEncryption Invented in 1975 by Diffie and Hellman at Stanford Encrypted_Message = Encrypt(Key1, Message) Message = Decrypt(Key2, Encrypted_Message) Key1 Key2 Text Ciphertext Text Keys are interchangeable: Key2 Key1 Text Ciphertext Text One key is made public while the other is kept private Sender knows only public key of the receiver Asymmetric Washington University in St. Louis CSE571S ©2011 Raj Jain 9-3 PublicPublic KeyKey EncryptionEncryption ExampleExample Rivest, Shamir, and Adleman at MIT RSA: Encrypted_Message = m3 mod 187 Message = Encrypted_Message107 mod 187 Key1 = <3,187>, Key2 = <107,187> Message = 5 Encrypted Message = 53 = 125 Message = 125107 mod 187 = 5 = 125(64+32+8+2+1) mod 187 = {(12564 mod 187)(12532 mod 187)... (1252 mod 187)(125 mod 187)} mod 187 Washington University in -

The Order of Encryption and Authentication for Protecting Communications (Or: How Secure Is SSL?)?
The Order of Encryption and Authentication for Protecting Communications (Or: How Secure is SSL?)? Hugo Krawczyk?? Abstract. We study the question of how to generically compose sym- metric encryption and authentication when building \secure channels" for the protection of communications over insecure networks. We show that any secure channels protocol designed to work with any combina- tion of secure encryption (against chosen plaintext attacks) and secure MAC must use the encrypt-then-authenticate method. We demonstrate this by showing that the other common methods of composing encryp- tion and authentication, including the authenticate-then-encrypt method used in SSL, are not generically secure. We show an example of an en- cryption function that provides (Shannon's) perfect secrecy but when combined with any MAC function under the authenticate-then-encrypt method yields a totally insecure protocol (for example, ¯nding passwords or credit card numbers transmitted under the protection of such protocol becomes an easy task for an active attacker). The same applies to the encrypt-and-authenticate method used in SSH. On the positive side we show that the authenticate-then-encrypt method is secure if the encryption method in use is either CBC mode (with an underlying secure block cipher) or a stream cipher (that xor the data with a random or pseudorandom pad). Thus, while we show the generic security of SSL to be broken, the current practical implementations of the protocol that use the above modes of encryption are safe. 1 Introduction The most widespread application of cryptography in the Internet these days is for implementing a secure channel between two end points and then exchanging information over that channel. -

Online Payment Fraud Prevention Using Cryptographic Algorithm TDES
S. Aishwarya et al, International Journal of Computer Science and Mobile Computing, Vol.4 Issue.4, April- 2015, pg. 317-323 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology ISSN 2320–088X IJCSMC, Vol. 4, Issue. 4, April 2015, pg.317 – 323 RESEARCH ARTICLE Online Payment Fraud Prevention Using Cryptographic Algorithm TDES S. AISHWARYA1 K.DEVIKA RANI DHIVYA*2 III MSc (SS), Assistant Professor, Department of CA & SS, Department of CA & SS, Sri Krishna Arts and Science College, Sri Krishna Arts and Science College, Coimbatore, Tamil Nadu, Coimbatore, Tamil Nadu, India India ABSTRACT: Credit card is a small plastic card issued by a bank, building society, etc., allowing the holder to purchase goods or services on credit. Debit card is a card allowing the holder to transfer money electronically from their bank account when making a purchase. The use of credit cards and debit cards are increasing day by day. People are relying more on both cards nowadays than in the previous days. As credit cards and debit cards becomes the most popular mode of payment for both online as well as regular purchase, cases of fraud associated with it are also rising. In real life, fraudulent transactions are scattered with genuine transactions and simple pattern matching techniques are not often sufficient to detect those frauds accurately. In this project the process of Cryptography has been followed, it is one of the most important security technologies which used to secure the data transmission and the data itself. -

Ransomware Is Here: What You Can Do About It?
WHITEPAPER Ransomware is Here: What you can do about it? Overview Over the last few years, ransomware has emerged as one of the most devastating and costly attacks in the hacker arsenal. Cyber thieves are increasingly using this form of attack to target individuals, corporate entities and public sector organizations alike by holding your system or files for ransom. Unlike other forms of cyber theft that often involve stolen financial or healthcare information, ransomware cuts out the middleman. In cases where an attacker steals health or financial documents, they must sell them on to third parties to make money. As far as ransomware is concerned, the money comes directly from the victim. Ransomware is a quickly growing threat vector. According to the FBI’s Internet Crime Complaint center (IC3), infected users made complaints about ransomware 2,453 times in 2015—nearly double the figure for 2014. What’s more, these figures most likely represent only the tip of the iceberg, as many users pay their ransom without making a report to the authorities. A recent survey conducted by a Cyber Security Research Center at the University of Kent found that over 40% of those infected with CryptoLocker actually agreed to pay the ransom demanded, which is a big incentive for hackers to target more systems. Lastly, hackers are rapidly iterating both malware and distribution techniques. In early Q2 of 2016, a new variant of ransomware, known as CryptXXX, emerged on the scene. This program is packed in such a way that users and antivirus software may initially confuse it for a Windows DLL file. -

CS 255: Intro to Cryptography 1 Introduction 2 End-To-End
Programming Assignment 2 Winter 2021 CS 255: Intro to Cryptography Prof. Dan Boneh Due Monday, March 1st, 11:59pm 1 Introduction In this assignment, you are tasked with implementing a secure and efficient end-to-end encrypted chat client using the Double Ratchet Algorithm, a popular session setup protocol that powers real- world chat systems such as Signal and WhatsApp. As an additional challenge, assume you live in a country with government surveillance. Thereby, all messages sent are required to include the session key encrypted with a fixed public key issued by the government. In your implementation, you will make use of various cryptographic primitives we have discussed in class—notably, key exchange, public key encryption, digital signatures, and authenticated encryption. Because it is ill-advised to implement your own primitives in cryptography, you should use an established library: in this case, the Stanford Javascript Crypto Library (SJCL). We will provide starter code that contains a basic template, which you will be able to fill in to satisfy the functionality and security properties described below. 2 End-to-end Encrypted Chat Client 2.1 Implementation Details Your chat client will use the Double Ratchet Algorithm to provide end-to-end encrypted commu- nications with other clients. To evaluate your messaging client, we will check that two or more instances of your implementation it can communicate with each other properly. We feel that it is best to understand the Double Ratchet Algorithm straight from the source, so we ask that you read Sections 1, 2, and 3 of Signal’s published specification here: https://signal. -
Diffie-Hellman (1976) – RSA (1977) – More Recently: ID-Based Encryption (2001), Functional Encryption (2011)…
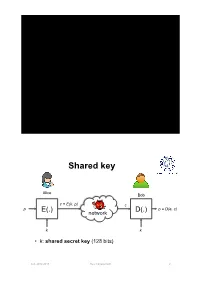
Key Management Shared key Alice Bob c = E(k, p) c p E(.) D(.) p = D(e, c) network k k • k: shared secret key (128 bits) A.A. 2012-2013 Key management 2 Pairwise keys • Each pair of users shares an long-term secret key Alice Bob • Properties • Every user stores (n -1) keys • The overall number of keys is O(n2) Carol Eve Dave A.A. 2012-2013 Key management 3 Pairwise keys • Pros – If a subject is compromised only its communications are compromised; • communications between two other subjects are not compromised • We cannot do any better! • Cons – Poor scalability: the number of keys is quadratic in the number of subjects – Poor scalability: a new member’s joining and a member’s leaving affect all current members A.A. 2012-2013 Key management 4 Trusted Third Party • Online Trusted Third Party (TTP) – Each user shares a long-term secret key with TTP TTP – Every user stores one key – The overall number of keys is n KA KB • TTP is a single point of failure – TTP must be always online A B – TTP knows all the keys • TTP can read all msg between Alice and Bob KAB • TTP can impersonate any party A.A. 2012-2013 Key management 5 Key distribution: a toy protocol Alice wants a shared key with Bob. Eavesdropping security only Bob (kB) Alice (kA) TTP “Alice wants key with Bob” choose E(KA, “A, B” || KAB) random kAB ticket ticket ← E(KB, “A, B” || KAB) kAB kAB Subject to replay attacks A.A. 2012-2013 Key management 6 Key distribution: toy protocol • Insecure against replay attacks (active adversary) – Attacker records session between Alice and merchant Bob • For example: an order – Attacker replays session to Bob • Bob thinks Alice is ordering another copy of the book A.A. -

Choosing Key Sizes for Cryptography
information security technical report 15 (2010) 21e27 available at www.sciencedirect.com www.compseconline.com/publications/prodinf.htm Choosing key sizes for cryptography Alexander W. Dent Information Security Group, University Of London, Royal Holloway, UK abstract After making the decision to use public-key cryptography, an organisation still has to make many important decisions before a practical system can be implemented. One of the more difficult challenges is to decide the length of the keys which are to be used within the system: longer keys provide more security but mean that the cryptographic operation will take more time to complete. The most common solution is to take advice from information security standards. This article will investigate the methodology that is used produce these standards and their meaning for an organisation who wishes to implement public-key cryptography. ª 2010 Elsevier Ltd. All rights reserved. 1. Introduction being compromised by an attacker). It also typically means a slower scheme. Most symmetric cryptographic schemes do The power of public-key cryptography is undeniable. It is not allow the use of keys of different lengths. If a designer astounding in its simplicity and its ability to provide solutions wishes to offer a symmetric scheme which provides different to many seemingly insurmountable organisational problems. security levels depending on the key size, then the designer However, the use of public-key cryptography in practice is has to construct distinct variants of a central design which rarely as simple as the concept first appears. First one has to make use of different pre-specified key lengths. -

Basics of Digital Signatures &
> DOCUMENT SIGNING > eID VALIDATION > SIGNATURE VERIFICATION > TIMESTAMPING & ARCHIVING > APPROVAL WORKFLOW Basics of Digital Signatures & PKI This document provides a quick background to PKI-based digital signatures and an overview of how the signature creation and verification processes work. It also describes how the cryptographic keys used for creating and verifying digital signatures are managed. 1. Background to Digital Signatures Digital signatures are essentially “enciphered data” created using cryptographic algorithms. The algorithms define how the enciphered data is created for a particular document or message. Standard digital signature algorithms exist so that no one needs to create these from scratch. Digital signature algorithms were first invented in the 1970’s and are based on a type of cryptography referred to as “Public Key Cryptography”. By far the most common digital signature algorithm is RSA (named after the inventors Rivest, Shamir and Adelman in 1978), by our estimates it is used in over 80% of the digital signatures being used around the world. This algorithm has been standardised (ISO, ANSI, IETF etc.) and been extensively analysed by the cryptographic research community and you can say with confidence that it has withstood the test of time, i.e. no one has been able to find an efficient way of cracking the RSA algorithm. Another more recent algorithm is ECDSA (Elliptic Curve Digital Signature Algorithm), which is likely to become popular over time. Digital signatures are used everywhere even when we are not actually aware, example uses include: Retail payment systems like MasterCard/Visa chip and pin, High-value interbank payment systems (CHAPS, BACS, SWIFT etc), e-Passports and e-ID cards, Logging on to SSL-enabled websites or connecting with corporate VPNs. -

Ansi/Scte 23-2 2017
ENGINEERING COMMITTEE Data Standards Subcommittee AMERICAN NATIONAL STANDARD ANSI/SCTE 23-2 2017 DOCSIS 1.1 Part 2: Baseline Privacy Plus Interface ANSI/SCTE 23-2 2017 NOTICE The Society of Cable Telecommunications Engineers (SCTE) Standards and Operational Practices (hereafter called “documents”) are intended to serve the public interest by providing specifications, test methods and procedures that promote uniformity of product, interchangeability, best practices and ultimately the long term reliability of broadband communications facilities. These documents shall not in any way preclude any member or non-member of SCTE from manufacturing or selling products not conforming to such documents, nor shall the existence of such standards preclude their voluntary use by those other than SCTE members. SCTE assumes no obligations or liability whatsoever to any party who may adopt the documents. Such adopting party assumes all risks associated with adoption of these documents, and accepts full responsibility for any damage and/or claims arising from the adoption of such documents. Attention is called to the possibility that implementation of this document may require the use of subject matter covered by patent rights. By publication of this document, no position is taken with respect to the existence or validity of any patent rights in connection therewith. SCTE shall not be responsible for identifying patents for which a license may be required or for conducting inquiries into the legal validity or scope of those patents that are brought to its attention. Patent holders who believe that they hold patents which are essential to the implementation of this document have been requested to provide information about those patents and any related licensing terms and conditions. -

Security, Encryption, and Certificates FAQ
Security, Encryption, and Certificates FAQ Overview In Security Center 5.4, several new capabilities will be added that further strengthen the security of the platform itself, as well as the privacy of data. The aim is to prevent unauthorized access to stored and transmitted messages and data, as well as prevent attacks through the use of stronger encryption and authentication mechanisms. With growing demand for privacy, new capabilities in Security Center 5.4 will strengthen Genetec’s position and overall value proposition. This FAQ addresses some of the most common questions in relation to the new capabilities of Security Center: Encryption, Authentication, and Digital Certificates. These concepts are first described in generic terms; the FAQ then outlines how these new measures are used within Security Center 5.4. Encryption vs. Authentication vs. Authorization What is the difference between encryption, authentication, and authorization? Encryption is used to encrypt data so that only authorized users can see it. Authentication determines whether an entity is who they claim to be, eg. in the case of an individual, it is usually based on a username/password combination. Authentication does not actually say anything about what someone is authorized to do or has the right to do. o Client-side authentication uses username/password combinations, tokens (dual authentication), and other techniques. o Server-side authentication uses certificates to identify trusted third parties. Authorization is the function of specifying the rights, eg. defining the access rights someone has over a set of recourses such as a private data, computing resources, or an application. When users log into a Security Center system, what they are allowed or authorized to do depends on the set of privileges assigned to them by administrators. -

AWS Key Management Service Cryptographic Details
AWS Key Management Service Cryptographic Details August 2016 Amazon Web Services – AWS KMS Cryptographic Details August 2016 © 2016, Amazon Web Services, Inc. or its affiliates. All rights reserved. Notices This document is provided for informational purposes only. It represents AWS’s current product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS’s products or services, each of which is provided “as is” without warranty of any kind, whether express or implied. This document does not create any warranties, representations, contractual commitments, conditions or assurances from AWS, its affiliates, suppliers or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers. Page 2 of 42 Amazon Web Services – AWS KMS Cryptographic Details August 2016 Contents Abstract 4 Introduction 4 Design Goals 5 Background 7 Cryptographic Primitives 7 Basic Concepts 9 Customer’s Key Hierarchy 11 Use Cases 13 Amazon EBS Volume Encryption 13 Envelope Encryption 14 Customer Master Keys 17 Imported Master Keys 19 Enable and Disable Key 22 Key Deletion 22 Rotate Customer Master Key 23 Customer Data Operations 23 Application-Specific Data Keys 24 Encrypt 26 Decrypt 26 Re-Encrypting an Encrypted Object 28 Internal Communication Security 29 HSA Security Boundary 29 Quorum-Signed Commands 30 Authenticated Sessions 31 Domains and the Domain State 32 Page 3 of 42 Amazon Web Services – AWS KMS Cryptographic Details August 2016 Domain Keys 33 Exported Domain Tokens 33 Managing Domain State 34 Durability Protection 36 References 38 Appendix - Abbreviations and Keys 40 Abbreviations 40 Keys 41 Contributors 42 Document Revisions 42 Abstract AWS Key Management Service (AWS KMS) provides cryptographic keys and operations scaled for the cloud.