Example:The Diffie-Hellman Key Exchange
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Authentication in Key-Exchange: Definitions, Relations and Composition
Authentication in Key-Exchange: Definitions, Relations and Composition Cyprien Delpech de Saint Guilhem1;2, Marc Fischlin3, and Bogdan Warinschi2 1 imec-COSIC, KU Leuven, Belgium 2 Dept Computer Science, University of Bristol, United Kingdom 3 Computer Science, Technische Universit¨atDarmstadt, Germany [email protected], [email protected], [email protected] Abstract. We present a systematic approach to define and study authentication notions in authenti- cated key-exchange protocols. We propose and use a flexible and expressive predicate-based definitional framework. Our definitions capture key and entity authentication, in both implicit and explicit vari- ants, as well as key and entity confirmation, for authenticated key-exchange protocols. In particular, we capture critical notions in the authentication space such as key-compromise impersonation resis- tance and security against unknown key-share attacks. We first discuss these definitions within the Bellare{Rogaway model and then extend them to Canetti{Krawczyk-style models. We then show two useful applications of our framework. First, we look at the authentication guarantees of three representative protocols to draw several useful lessons for protocol design. The core technical contribution of this paper is then to formally establish that composition of secure implicitly authenti- cated key-exchange with subsequent confirmation protocols yields explicit authentication guarantees. Without a formal separation of implicit and explicit authentication from secrecy, a proof of this folklore result could not have been established. 1 Introduction The commonly expected level of security for authenticated key-exchange (AKE) protocols comprises two aspects. Authentication provides guarantees on the identities of the parties involved in the protocol execution. -
Diffie-Hellman (1976) – RSA (1977) – More Recently: ID-Based Encryption (2001), Functional Encryption (2011)…
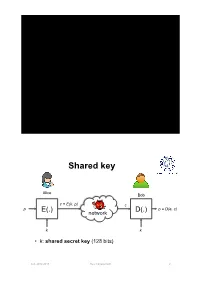
Key Management Shared key Alice Bob c = E(k, p) c p E(.) D(.) p = D(e, c) network k k • k: shared secret key (128 bits) A.A. 2012-2013 Key management 2 Pairwise keys • Each pair of users shares an long-term secret key Alice Bob • Properties • Every user stores (n -1) keys • The overall number of keys is O(n2) Carol Eve Dave A.A. 2012-2013 Key management 3 Pairwise keys • Pros – If a subject is compromised only its communications are compromised; • communications between two other subjects are not compromised • We cannot do any better! • Cons – Poor scalability: the number of keys is quadratic in the number of subjects – Poor scalability: a new member’s joining and a member’s leaving affect all current members A.A. 2012-2013 Key management 4 Trusted Third Party • Online Trusted Third Party (TTP) – Each user shares a long-term secret key with TTP TTP – Every user stores one key – The overall number of keys is n KA KB • TTP is a single point of failure – TTP must be always online A B – TTP knows all the keys • TTP can read all msg between Alice and Bob KAB • TTP can impersonate any party A.A. 2012-2013 Key management 5 Key distribution: a toy protocol Alice wants a shared key with Bob. Eavesdropping security only Bob (kB) Alice (kA) TTP “Alice wants key with Bob” choose E(KA, “A, B” || KAB) random kAB ticket ticket ← E(KB, “A, B” || KAB) kAB kAB Subject to replay attacks A.A. 2012-2013 Key management 6 Key distribution: toy protocol • Insecure against replay attacks (active adversary) – Attacker records session between Alice and merchant Bob • For example: an order – Attacker replays session to Bob • Bob thinks Alice is ordering another copy of the book A.A. -

2.3 Diffie–Hellman Key Exchange
2.3. Di±e{Hellman key exchange 65 q q q q q q 6 q qq q q q q q q 900 q q q q q q q qq q q q q q q q q q q q q q q q q 800 q q q qq q q q q q q q q q qq q q q q q q q q q q q 700 q q q q q q q q q q q q q q q q q q q q q q q q q q qq q 600 q q q q q q q q q q q q qq q q q q q q q q q q q q q q q q q qq q q q q q q q q 500 q qq q q q q q qq q q q q q qqq q q q q q q q q q q q q q qq q q q 400 q q q q q q q q q q q q q q q q q q q q q q q q q 300 q q q q q q q q q q q q q q q q q q qqqq qqq q q q q q q q q q q q 200 q q q q q q q q q q q q q q q q q q q q q q q q q q q q q q q q qq q q qq q q 100 q q q q q q q q q q q q q q q q q q q q q q q q q 0 q - 0 30 60 90 120 150 180 210 240 270 Figure 2.2: Powers 627i mod 941 for i = 1; 2; 3;::: any group and use the group law instead of multiplication. -

Ansi/Scte 23-2 2017
ENGINEERING COMMITTEE Data Standards Subcommittee AMERICAN NATIONAL STANDARD ANSI/SCTE 23-2 2017 DOCSIS 1.1 Part 2: Baseline Privacy Plus Interface ANSI/SCTE 23-2 2017 NOTICE The Society of Cable Telecommunications Engineers (SCTE) Standards and Operational Practices (hereafter called “documents”) are intended to serve the public interest by providing specifications, test methods and procedures that promote uniformity of product, interchangeability, best practices and ultimately the long term reliability of broadband communications facilities. These documents shall not in any way preclude any member or non-member of SCTE from manufacturing or selling products not conforming to such documents, nor shall the existence of such standards preclude their voluntary use by those other than SCTE members. SCTE assumes no obligations or liability whatsoever to any party who may adopt the documents. Such adopting party assumes all risks associated with adoption of these documents, and accepts full responsibility for any damage and/or claims arising from the adoption of such documents. Attention is called to the possibility that implementation of this document may require the use of subject matter covered by patent rights. By publication of this document, no position is taken with respect to the existence or validity of any patent rights in connection therewith. SCTE shall not be responsible for identifying patents for which a license may be required or for conducting inquiries into the legal validity or scope of those patents that are brought to its attention. Patent holders who believe that they hold patents which are essential to the implementation of this document have been requested to provide information about those patents and any related licensing terms and conditions. -

Elliptic Curves in Public Key Cryptography: the Diffie Hellman
Elliptic Curves in Public Key Cryptography: The Diffie Hellman Key Exchange Protocol and its relationship to the Elliptic Curve Discrete Logarithm Problem Public Key Cryptography Public key cryptography is a modern form of cryptography that allows different parties to exchange information securely over an insecure network, without having first to agree upon some secret key. The main use of public key cryptography is to provide information security in computer science, for example to transfer securely email, credit card details or other secret information between sender and recipient via the internet. There are three steps involved in transferring information securely from person A to person B over an insecure network. These are encryption of the original information, called the plaintext, transfer of the encrypted message, or ciphertext, and decryption of the ciphertext back into plaintext. Since the transfer of the ciphertext is over an insecure network, any spy has access to the ciphertext and thus potentially has access to the original information, provided he is able to decipher the message. Thus, a successful cryptosystem must be able encrypt the original message in such a way that only the intended receiver can decipher the ciphertext. The goal of public key cryptography is to make the problem of deciphering the encrypted message too difficult to do in a reasonable time (by say brute-force) unless certain key facts are known. Ideally, only the intended sender and receiver of a message should know these certain key facts. Any certain piece of information that is essential in order to decrypt a message is known as a key. -

AWS Key Management Service Cryptographic Details
AWS Key Management Service Cryptographic Details August 2016 Amazon Web Services – AWS KMS Cryptographic Details August 2016 © 2016, Amazon Web Services, Inc. or its affiliates. All rights reserved. Notices This document is provided for informational purposes only. It represents AWS’s current product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS’s products or services, each of which is provided “as is” without warranty of any kind, whether express or implied. This document does not create any warranties, representations, contractual commitments, conditions or assurances from AWS, its affiliates, suppliers or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers. Page 2 of 42 Amazon Web Services – AWS KMS Cryptographic Details August 2016 Contents Abstract 4 Introduction 4 Design Goals 5 Background 7 Cryptographic Primitives 7 Basic Concepts 9 Customer’s Key Hierarchy 11 Use Cases 13 Amazon EBS Volume Encryption 13 Envelope Encryption 14 Customer Master Keys 17 Imported Master Keys 19 Enable and Disable Key 22 Key Deletion 22 Rotate Customer Master Key 23 Customer Data Operations 23 Application-Specific Data Keys 24 Encrypt 26 Decrypt 26 Re-Encrypting an Encrypted Object 28 Internal Communication Security 29 HSA Security Boundary 29 Quorum-Signed Commands 30 Authenticated Sessions 31 Domains and the Domain State 32 Page 3 of 42 Amazon Web Services – AWS KMS Cryptographic Details August 2016 Domain Keys 33 Exported Domain Tokens 33 Managing Domain State 34 Durability Protection 36 References 38 Appendix - Abbreviations and Keys 40 Abbreviations 40 Keys 41 Contributors 42 Document Revisions 42 Abstract AWS Key Management Service (AWS KMS) provides cryptographic keys and operations scaled for the cloud. -

DRAFT Special Publication 800-56A, Recommendation for Pair-Wise Key
The attached DRAFT document (provided here for historical purposes) has been superseded by the following publication: Publication Number: NIST Special Publication (SP) 800-56A Revision 2 Title: Recommendation for Pair-Wise Key-Establishment Schemes Using Discrete Logarithm Cryptography Publication Date: 05/13/2013 • Final Publication: https://doi.org/10.6028/NIST.SP.800-56Ar2 (which links to http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-56Ar2.pdf). • Information on other NIST Computer Security Division publications and programs can be found at: http://csrc.nist.gov/ The following information was posted with the attached DRAFT document: Aug 20, 2012 SP 800-56 A Rev.1 DRAFT Recommendation for Pair-Wise Key-Establishment Schemes Using Discrete Logarithm Cryptography (Draft Revision) NIST announces the release of draft revision of Special Publication 800-56A, Recommendation for Pair-Wise Key Establishment Schemes Using Discrete Logarithm Cryptography. SP 800-56A specifies key-establishment schemes based on the discrete logarithm problem over finite fields and elliptic curves, including several variations of Diffie-Hellman and MQV key establishment schemes. The revision is made on the March 2007 version. The main changes are listed in Appendix D. Please submit comments to 56A2012rev-comments @ nist.gov with "Comments on SP 800-56A (Revision)" in the subject line. The comment period closes on October 31, 2012. NIST Special Publication 800-56A Recommendation for Pair-Wise August 2012 Key-Establishment Schemes Using Discrete Logarithm Cryptography (Draft Revision) Elaine Barker, Lily Chen, Miles Smid and Allen Roginsky C O M P U T E R S E C U R I T Y Abstract This Recommendation specifies key-establishment schemes based on the discrete logarithm problem over finite fields and elliptic curves, including several variations of Diffie-Hellman and MQV key establishment schemes. -

Guidelines on Cryptographic Algorithms Usage and Key Management
EPC342-08 Version 7.0 4 November 2017 [X] Public – [ ] Internal Use – [ ] Confidential – [ ] Strictest Confidence Distribution: Publicly available GUIDELINES ON CRYPTOGRAPHIC ALGORITHMS USAGE AND KEY MANAGEMENT Abstract This document defines guidelines on cryptographic algorithms usage and key management. Document Reference EPC342-08 Issue Version 7.0 Date of Issue 22 November 2017 Reason for Issue Maintenance of document Produced by EPC Authorised by EPC Document History This document was first produced by ECBS as TR 406, with its latest ECBS version published in September 2005. The document has been handed over to the EPC which is responsible for its yearly maintenance. DISCLAIMER: Whilst the European Payments Council (EPC) has used its best endeavours to make sure that all the information, data, documentation (including references) and other material in the present document are accurate and complete, it does not accept liability for any errors or omissions. EPC will not be liable for any claims or losses of any nature arising directly or indirectly from use of the information, data, documentation or other material in the present document. Conseil Européen des Paiements AISBL– Cours Saint-Michel 30A – B 1040 Brussels Tel: +32 2 733 35 33 – Fax: +32 2 736 49 88 Enterprise N° 0873.268.927 – www.epc-cep.eu – [email protected] © 2016 Copyright European Payments Council (EPC) AISBL: Reproduction for non-commercial purposes is authorised, with acknowledgement of the source Table of Content MANAGEMENT SUMMARY ............................................................. 5 1 INTRODUCTION .................................................................... 7 1.1 Scope of the document ...................................................... 7 1.2 Document structure .......................................................... 7 1.3 Recommendations ............................................................ 8 1.4 Implementation best practices ......................................... -

Dell EMC Unity: Data at Rest Encryption a Detailed Review
Technical White Paper Dell EMC Unity: Data at Rest Encryption A Detailed Review Abstract This white paper explains the Data at Rest Encryption feature, which provides controller-based encryption of data stored on Dell EMC™ Unity storage systems to protect against unauthorized access to lost or stolen drives or system. The encryption technology as well as its implementation on Dell EMC Unity storage systems are discussed. June 2021 H15090.6 Revisions Revisions Date Description May 2016 Initial release – Unity OE 4.0 July 2017 Updated for Unity OE 4.2 June 2021 Template and format updates. Updated for Unity OE 5.1 Acknowledgments Author: Ryan Poulin The information in this publication is provided “as is.” Dell Inc. makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose. Use, copying, and distribution of any software described in this publication requires an applicable software license. This document may contain certain words that are not consistent with Dell's current language guidelines. Dell plans to update the document over subsequent future releases to revise these words accordingly. This document may contain language from third party content that is not under Dell's control and is not consistent with Dell's current guidelines for Dell's own content. When such third party content is updated by the relevant third parties, this document will be revised accordingly. Copyright © 2016-2021 Dell Inc. or its subsidiaries. All Rights Reserved. Dell Technologies, Dell, EMC, Dell EMC and other trademarks are trademarks of Dell Inc. -

DOCSIS 3.0 Security Specification
Data-Over-Cable Service Interface Specifications DOCSIS 3.0 Security Specification CM-SP-SEC3.0-C01-171207 CLOSED Notice This DOCSIS® specification is the result of a cooperative effort undertaken at the direction of Cable Television Laboratories, Inc. for the benefit of the cable industry and its customers. You may download, copy, distribute, and reference the documents herein only for the purpose of developing products or services in accordance with such documents, and educational use. Except as granted by CableLabs® in a separate written license agreement, no license is granted to modify the documents herein (except via the Engineering Change process), or to use, copy, modify or distribute the documents for any other purpose. This document may contain references to other documents not owned or controlled by CableLabs. Use and understanding of this document may require access to such other documents. Designing, manufacturing, distributing, using, selling, or servicing products, or providing services, based on this document may require intellectual property licenses from third parties for technology referenced in this document. To the extent this document contains or refers to documents of third parties, you agree to abide by the terms of any licenses associated with such third-party documents, including open source licenses, if any. Cable Television Laboratories, Inc., 2006-2017 CM-SP-SEC3.0-C01-171207 Data-Over-Cable Service Interface Specifications DISCLAIMER This document is furnished on an "AS IS" basis and neither CableLabs nor its members provides any representation or warranty, express or implied, regarding the accuracy, completeness, noninfringement, or fitness for a particular purpose of this document, or any document referenced herein. -

Study on the Use of Cryptographic Techniques in Europe
Study on the use of cryptographic techniques in Europe [Deliverable – 2011-12-19] Updated on 2012-04-20 II Study on the use of cryptographic techniques in Europe Contributors to this report Authors: Edward Hamilton and Mischa Kriens of Analysys Mason Ltd Rodica Tirtea of ENISA Supervisor of the project: Rodica Tirtea of ENISA ENISA staff involved in the project: Demosthenes Ikonomou, Stefan Schiffner Agreements or Acknowledgements ENISA would like to thank the contributors and reviewers of this study. Study on the use of cryptographic techniques in Europe III About ENISA The European Network and Information Security Agency (ENISA) is a centre of network and information security expertise for the EU, its member states, the private sector and Europe’s citizens. ENISA works with these groups to develop advice and recommendations on good practice in information security. It assists EU member states in implementing relevant EU leg- islation and works to improve the resilience of Europe’s critical information infrastructure and networks. ENISA seeks to enhance existing expertise in EU member states by supporting the development of cross-border communities committed to improving network and information security throughout the EU. More information about ENISA and its work can be found at www.enisa.europa.eu. Contact details For contacting ENISA or for general enquiries on cryptography, please use the following de- tails: E-mail: [email protected] Internet: http://www.enisa.europa.eu Legal notice Notice must be taken that this publication represents the views and interpretations of the au- thors and editors, unless stated otherwise. This publication should not be construed to be a legal action of ENISA or the ENISA bodies unless adopted pursuant to the ENISA Regulation (EC) No 460/2004 as lastly amended by Regulation (EU) No 580/2011. -

A Framework for Designing Cryptographic Key Management Systems
NIST Special Publication 800-130 A Framework for Designing Cryptographic Key Management Systems Elaine Barker Miles Smid Dennis Branstad Santosh Chokhani C O M P U T E R S E C U R I T Y NIST Special Publication 800-130 A Framework for Designing Cryptographic Key Management Systems Elaine Barker Computer Security Division Information Technology Laboratory Miles Smid Orion Security Solutions Silver, Spring, MD Dennis Branstad NIST Consultant Austin, TX Santosh Chokhani Cygnacom McLean, VA August 2013 U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary of Commerce for Standards and Technology and Director SP 800-130 August 2013 Authority This publication has been developed by NIST to further its statutory responsibilities under the Federal Information Security Management Act (FISMA), Public Law (P.L.) 107-347. NIST is responsible for developing information security standards and guidelines, including minimum requirements for Federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate Federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as analyzed in Circular A-130, Appendix IV: Analysis of Key Sections. Supplemental information is provided in Circular A-130, Appendix III, Security of Federal Automated Information Resources. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on Federal agencies by the Secretary of Commerce under statutory authority.