IBM Security Access Manager for Mobile: Administration Guide Figures
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Dynamic and Interactive R Graphics for the Web: the Gridsvg Package
JSS Journal of Statistical Software MMMMMM YYYY, Volume VV, Issue II. http://www.jstatsoft.org/ Dynamic and Interactive R Graphics for the Web: The gridSVG Package Paul Murrell Simon Potter The Unversity of Auckland The Unversity of Auckland Abstract This article describes the gridSVG package, which provides functions to convert grid- based R graphics to an SVG format. The package also provides a function to associate hyperlinks with components of a plot, a function to animate components of a plot, a function to associate any SVG attribute with a component of a plot, and a function to add JavaScript code to a plot. The last two of these provides a basis for adding interactivity to the SVG version of the plot. Together these tools provide a way to generate dynamic and interactive R graphics for use in web pages. Keywords: world-wide web, graphics, R, SVG. 1. Introduction Interactive and dynamic plots within web pages are becomingly increasingly popular, as part of a general trend towards making data sets more open and accessible on the web, for example, GapMinder (Rosling 2008) and ManyEyes (Viegas, Wattenberg, van Ham, Kriss, and McKeon 2007). The R language and environment for statistical computing and graphics (R Development Core Team 2011) has many facilities for producing plots, and it can produce graphics formats that are suitable for including in web pages, but the core graphics facilities in R are largely focused on static plots. This article describes an R extension package, gridSVG, that is designed to embellish and transform a standard, static R plot and turn it into a dynamic and interactive plot that can be embedded in a web page. -

CSS Contenu / Mise En Forme 3 Séparer Contenu, Site Mise En Forme, Web Document Object Et Actions
Langages du Web 1 Langages du Web CSS Contenu / Mise en forme 3 Séparer contenu, Site mise en forme, Web Document Object et actions. DOM Model Cascading Style JS JavaScript Sheet CSS HyperText Markup Language HTML francois.piat@univ‐fcomte.fr CSS Cascading Style Sheet 4 Feuille de style en cascade : séparer contenu et forme. Pas d'attributs de mise en forme dans le code HTML CSS ≠ HTML. Un "mécanisme" avec sa propre syntaxe Contrôle précis de la mise en page et de la mise en forme Code HTML plus simple et plus court CCS 1 : décembre 1996 Propriétés de mise en forme et de rendu typographique CSS 2 : mai 1998 70 nouvelles propriétés (ex : positionnement à l'écran) Cascade : plusieurs de feuilles de styles mises en oeuvre CSS 2.1 : septembre 2009 ‐ Recommandation : 7 juin 2011 Supprime des parties de CSS 2 / corrections suivant les implémentations CSS 3 : en développement http://www.w3.org/Style/CSS/current‐work#roadmap francois.piat@univ‐fcomte.fr 2 Langages du Web CSS Contenu / Mise en forme 5 1994 1997 1999 2005 Maintenant JS JS HTML HTML CSS JS CSS HTML HTML JS HTML HTML "The Web technology stack is a complete mess." Ian Hickson – 08/01/2013 - http://html5doctor.com/interview-with-ian-hickson-html-editor/ francois.piat@univ‐fcomte.fr CSS Code CSS 6 h1 { background: url(images/trait.png) no‐repeat; color: #be7e11; font‐size: 28px; font‐weight: bold; width: 590px; } #bcContenu li .avatar { font: 16px/1.8 Arial, Verdana, sans‐serif; height: 50px; margin‐left: ‐60px; width: 50px; } francois.piat@univ‐fcomte.fr 3 Langages du -

Sunspec Plant Information Exchange
Document #: 12042 Status: DRAFT Version D6 SunSpec Plant Information Exchange SunSpec Alliance Interoperability Specification SunSpec Alliance Plant Extract Document Workgroup Brett Francis, Bob Fox, Ferdy Nagy, Paul Cobb, Michael Palmquist, Jose Gomez, Stephen Lapointe, John Nunneley, Terry Terasammal, Francisco Ancin, Beth McCanlies Draft 6 ABSTRACT The SunSpec Specification suite consists of the following documentation: - SunSpec Technology Overview - SunSpec Information Model Specifications - SunSpec Model Data Exchange - SunSpec Plant Information Exchange This is the Plant Information Exchange document. A Plant Information Exchange standard enables these functions: • A common monitoring extract format for asset analysis tools • A means to extract and send historic plant data between different monitoring systems • A way to report asset performance to financial partners, for plants managed by different monitoring systems Change History D-1: Initial (A) Draft – Brett Francis : 2012-May-23 D-1: B Draft – workgroup 2012-May-31 and 2012-June-7, Brett Francis : 2012-Jun-12 D-1: C Draft – Additional elements and grammar improvements – Brett Francis : 2012-Jun-13 D-1: D Draft – workgroup 2012-June-28 – plant, sunSpecMetadata and strings blocks D-1: E Draft – workgroup 2012-July-05 – intro update, participant block, enumerated types – Brett Francis : 2012-Jul-18 D-1: F Draft – John Nunneley input 2012-Aug-09 T-1: A – Promoted to TEST level 1.0 – John Nunneley 2012-Aug-09 T-1: B – General formatting, layout and grammar improvements – Brett Francis 2012-Sept-05 T-2:A – Incorporating feedback – 2012-MMM-dd V2-D1: Flesh out financial oversight use case and NREL requirements. 2013-Feb-14 V2-D2: Incorporate feedback. -

The New Font Project: TEX Gyre
Hans Hagen, Jerzy Ludwichowski, Volker Schaa NAJAAR 2006 47 The New Font Project: TEX Gyre Abstract metric and encoding files for each font. We look for- In this short presentation, we will introduce a new ward to an extended TFM format which will lift this re- project: the “lm-ization” of the free fonts that come striction and, in conjunction with OpenType, simplify with T X distributions. We will discuss the project E delivery and usage of fonts in TEX. objectives, timeline and cross-lug funding aspects. We especially look forward to assistance from pdfTEX users, because the pdfTEX team is working on the implementation on the support for OpenType Introduction fonts. An important consideration from Hans Hagen: “In The New Font Project is a brainchild of Hans Ha- the end, even Ghostscript will benefit, so I can even gen, triggered mainly by the very good reception imagine those fonts ending up in the Ghostscript dis- of the Latin Modern (LM) font project by the TEX tribution.” community. After consulting other LUG leaders, The idea of preparing such font families was sug- Bogusław Jackowski and Janusz M. Nowacki, aka gested by the pdfTEX development team. Their pro- “GUST type.foundry”, were asked to formulate the pro- posal triggered a lively discussion by an informal ject. group of representatives of several TEX user groups — The next section contains its outline, as prepared notably Karl Berry (TUG), Hans Hagen (NTG), Jerzy by Bogusław Jackowski and Janusz M. Nowacki. The Ludwichowski (GUST), Volker RW Schaa (DANTE)— remaining sections were written by us. who suggested that we should approach this project as a research, technical and implementation team, and Project outline promised their help in taking care of promotion, integ- ration, supervising and financing. -

OASIS AMQP Version 1.0
OASIS AMQP Version 1.0 Committee Specification Draft 01 / Public Review Draft 01 21 February 2012 Specification URIs This version: http://docs.oasis-open.org/amqp/core/v1.0/csprd01/amqp-core-overview-v1.0-csprd01.xml (Authoritative) http://docs.oasis-open.org/amqp/core/v1.0/csprd01/amqp-core-overview-v1.0-csprd01.html http://docs.oasis-open.org/amqp/core/v1.0/csprd01/amqp-core-complete-v1.0-csprd01.pdf Previous version: N/A Latest version: http://docs.oasis-open.org/amqp/core/v1.0/amqp-core-overview-v1.0.xml (Authoritative) http://docs.oasis-open.org/amqp/core/v1.0/amqp-core-overview-v1.0.html http://docs.oasis-open.org/amqp/core/v1.0/amqp-core-complete-v1.0.pdf Technical Committee: OASIS AMQP Technical Committee Chairs: Ram Jeyaraman ([email protected]), Microsoft Angus Telfer ([email protected]), INETCO Systems Editors: Robert Godfrey ([email protected]), JPMorgan Chase & Co. David Ingham ([email protected]), Microsoft Rafael Schloming ([email protected]), Red Hat Additional artifacts: This specification consists of the following documents: • Part 0: Overview - Overview of the AMQP specification [xml] [html] • Part 1: Types - AMQP type system and encoding [xml] [html] • Part 2: Transport - AMQP transport layer [xml] [html] • Part 3: Messaging - AMQP Messaging Layer [xml] [html] • Part 4: Transactions - AMQP Transactions Layer [xml] [html] • Part 5: Security - AMQP Security Layers [xml] [html] • XML Document Type Definition (DTD) Related work: This specification replaces or supersedes: • http://www.amqp.org/specification/1.0/amqp-org-download Abstract: The Advanced Message Queuing Protocol (AMQP) is an open internet protocol for business messaging. -
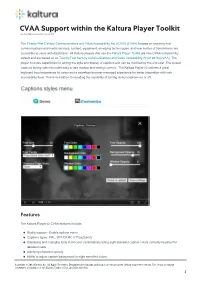
CVAA Support Within the Kaltura Player Toolkit Last Modified on 06/21/2020 4:25 Pm IDT
CVAA Support within the Kaltura Player Toolkit Last Modified on 06/21/2020 4:25 pm IDT The Twenty-First Century Communications and Video Accessibility Act of 2010 (CVAA) focuses on ensuring that communications and media services, content, equipment, emerging technologies, and new modes of transmission are accessible to users with disabilities. All Kaltura players that use the Kaltura Player Toolkit are now CVAA compliant by default and are based on on Twenty-First Century Communications and Video Accessibility Act of 2010 (CVAA). The player includes capabilities for editing the style and display of captions and can be modified by the end user. The closed captions styling editor includes easy to use markup and testing controls. The Kaltura Player v2 delivers a great keyboard input experience for users and a seamless browser-managed experience for better integration with web accessibility tools. This is in addition to including the capability of turning closed captions on or off. Features The Kaltura Player v2 CVAA features include: Studio support - Enable options menu Captions types: XML, SRT/DFXP, VTT(outband) Displaying and changing fonts in 64 color combinations using eight standard caption colors currently required for television sets. Adjusting character opacity Ability to adjust caption background in eight specified colors. Copyright ©️ 2019 Kaltura Inc. All Rights Reserved. Designated trademarks and brands are the property of their respective owners. Use of this document constitutes acceptance of the Kaltura Terms of Use and Privacy Policy. 1 Ability to adjust character edge (i.e., non, raised, depressed, uniform or drop shadow). Ability to adjust caption window color and opacity. -

The Ethics of Language Development
Winter 2016 Covers 4 and 1_Fall 2015 Covers 1 and 4 11/17/16 1:20 PM Page 1 L Winter , 2016 I S T E N I N G This issue: / J o u r n a l o f C o m m u n i c a t i o n E t h i c s The Ethics of , R e l i g i o Language n , a n d Development C u l t u r e V o l . 5 1 Volume 51 Number 1 Winter 2016 Covers 2 and 3_Fall 2013 Covers 2 and 3 11/17/16 1:20 PM Page 1 Journal of Communication Ethics, Religion, and Culture Editor ........................Janie M. Harden Fritz, Duquesne University Production Editor ......Craig T. Maier, Duquesne University Assistant Editor...........Joshua D. Hill, Duquesne University Consulting Editors ....Mark McVann, F.S.C., Saint Mary’s College of California Marilyn Nissim-Sabat, Lewis University Thomas E. Wren, Loyola University Chicago Assistant Production Editors ......................Matthew Mancino, Duquesne University Joshua D. Hill, Duquesne University Justin N. Bonanno, Duquesne University u The views expressed in the articles in Listening/Journal of Communication Ethics, Religion, and Culture remain those of the authors. Their publication does not constitute an endorsement, explicit or otherwise, by the editors. u Listening is published three times a year, in Winter, Spring, and Fall. All correspondence (including subscriptions) should be sent to the Editor, Listening/Journal of Communication Ethics, Religion, and Culture , Depart ment of Communication & Rhetorical Studies, Duquesne University, 600 Forbes Avenue, Pittsburgh, PA, 15282. Tel: (412) 396- 6558. -
Languages and GRIN-Global
Languages and GRIN-Global Revision Date June 11, 2015 This guide explains how to modify GRIN-Global to include languages other than English in the Curator Tool. These directions can also be used to edit the default English headings and descriptions. Change notes pertaining to this document are summarized in the appendix. Review the Table of Contents which contains links to the document’s topics. gg_language_guide_2015jun03.doc Page | 1 Contents GRIN-Global and Languages ................................................................................................................. 3 Overview ......................................................................................................................................... 3 Language-related Database Items in GRIN-Global ............................................................................ 3 Adding a Language to GRIN-Global ...................................................................................................... 5 Overview ......................................................................................................................................... 5 Language-Friendly Column Headings ................................................................................................... 6 Overview ......................................................................................................................................... 6 Storing Language-Friendly Column Heading Names at Two Levels .................................................... 6 Using the -

OMEGA CS Fonts
OMEGA CS Fonts A ACADEMY ENGRAVED ACCT AK REV C American Uncial Inl Accolade Bold American Uncial Shadow Accolade Light AMERICANA BOLD ACCT.AK.REV.C Accolade Light Ita Americana URW T Bol Accolade Med Americana URW T Reg Alcuin Caps URW T Bol Americana URW T Reg Ita Alcuin Caps URW T Lig Americana URW T Xtr Bol Alcuin Caps URW T Reg ANN. GROTESQUE ACCT.A.K.REV.C Alcuin Caps URW T Xtr Bol ANTIQUE OLIVE BOLD ACCT AK REV E Alcuin Discaps URW D Bol ANTIQUE OLIVE MED ACCT AK REV C Alcuin URW T Bol Antique Olive Nord Reg Ita Alcuin URW T Lig ARNOLD BOCKLIN ACCT.A.K.REV.D Alcuin URW T Reg Arnold Boecklin D Alcuin URW T Xtr Bol Arnold Boecklin Initials D Alternate Gothic No1 D Arnold Boecklin No2 Alternate Gothic No2 D Arnold Boecklin Outl Alternate Gothic No3 D ATH.SCRIPT CONN.ACCT.A.K.REV.D American Uncial D AVANT EXTRA BOLD ACCT. AK. REV G American Uncial Initials D AVANT GARDE ACCT. A.K. REV.K B BABYTEETH ACCT.AK REV B Baskerville T Bol Balloon Caps D Xtr Bol Baskerville T Med Balloon D Xtr Bol Baskerville T Med Ita Balloon Drop Shadow D Baskerville T Reg Balloon Outl P Xtr Bol Baskerville T Reg Ita Balloon P Xtr Bol Baskerville URW Bol Balloon URW Bold Baskerville URW BolNar Balloon URW Light Baskerville URW BolNarObl BASKERVILLE ACCT AK REV B Baskerville URW BolObl Baskerville AI Ad Weight Baskerville URW BolWid Baskerville AI Heavy Weight Baskerville URW BolWidObl Baskerville AI Over Weight Baskerville URW BolXtrNar BASKERVILLE BOLD ACCT.A.K.REV.F Baskerville URW BolXtrNarObl Baskerville Handcut Bold Baskerville URW BolXtrWid Baskerville -

Issue Table of Contents 2006, Number 1
The PracTeX Journal - TeX Users Group Journal home page General information Submit an item Download style files Copyright Contact us Issue Table of Contents 2006, Number 1 [Published 2006-02-18] Notices From the Editor: In this issue: Fonts Lance Carnes [whole issue page number 3] Feedback From Readers [6] Invitation to PracTeX'06 Robin Laakso [8] PracTeX Journal 2006-1 Whole Issue PDF The Editors Articles Typographic Opportunities Tamye Riggs [11] Font selection in LaTeX The most frequently asked questions Walter Schmidt [17] Mac OS X Fonts in pdfTeX Gerben C. Th. Wierda, Thomas A. Schmitz and Adam T. Lindsay [24] The MathTimeProfessional Fonts Or, How I Wasted the Last Twenty Years of my Life Mike Spivak [42] An exploration of the Latin Modern fonts Will Robertson [45] Chinese TeX: Using the CJK LaTeX Package, Unicode TrueType Fonts and PDFTeX under Windows Helmer Aslaksen [57] http://dw.tug.org/pracjourn/2006-1/wholeissue/toc.html (1 of 2)3/5/2006 7:24:41 AM The PracTeX Journal - TeX Users Group A Survey of Free Math Fonts for TeX and LaTeX Stephen Hartke [62] Columns Travels in TeX Land: Using the Lucida fonts David Walden [89] Ask Nelly: Which fonts can be accessed from the TeX Live distribution just using usepackage? What is the difference between Fonts and Typefaces? Which are the best fonts for typesetting math? The Editors [103] Distractions: Name-that-Font The Editors [106] http://dw.tug.org/pracjourn/2006-1/wholeissue/toc.html (2 of 2)3/5/2006 7:24:41 AM The PracTeX Journal - TeX Users Group Journal home page General information Submit an item Download style files Copyright Contact us From the Editor: In this issue: Fonts Lance Carnes G Comment on this paper G Send submission idea to editor In this issue: Fonts Next Issue Thanks Issue 2006-1 is the first issue of the PracTeX Journal's second year. -

Working-With-Mediawiki-Yaron-Koren.Pdf
Working with MediaWiki Yaron Koren 2 Working with MediaWiki by Yaron Koren Published by WikiWorks Press. Copyright ©2012 by Yaron Koren, except where otherwise noted. Chapter 17, “Semantic Forms”, includes significant content from the Semantic Forms homepage (https://www. mediawiki.org/wiki/Extension:Semantic_Forms), available under the Creative Commons BY-SA 3.0 license. All rights reserved. Library of Congress Control Number: 2012952489 ISBN: 978-0615720302 First edition, second printing: 2014 Ordering information for this book can be found at: http://workingwithmediawiki.com All printing of this book is handled by CreateSpace (https://createspace.com), a subsidiary of Amazon.com. Cover design by Grace Cheong (http://gracecheong.com). Contents 1 About MediaWiki 1 History of MediaWiki . 1 Community and support . 3 Available hosts . 4 2 Setting up MediaWiki 7 The MediaWiki environment . 7 Download . 7 Installing . 8 Setting the logo . 8 Changing the URL structure . 9 Updating MediaWiki . 9 3 Editing in MediaWiki 11 Tabs........................................................... 11 Creating and editing pages . 12 Page history . 14 Page diffs . 15 Undoing . 16 Blocking and rollbacks . 17 Deleting revisions . 17 Moving pages . 18 Deleting pages . 19 Edit conflicts . 20 4 MediaWiki syntax 21 Wikitext . 21 Interwiki links . 26 Including HTML . 26 Templates . 27 3 4 Contents Parser and tag functions . 30 Variables . 33 Behavior switches . 33 5 Content organization 35 Categories . 35 Namespaces . 38 Redirects . 41 Subpages and super-pages . 42 Special pages . 43 6 Communication 45 Talk pages . 45 LiquidThreads . 47 Echo & Flow . 48 Handling reader comments . 48 Chat........................................................... 49 Emailing users . 49 7 Images and files 51 Uploading . 51 Displaying images . 55 Image galleries . -

Prismtoken Thrift API 2019-01-16
Tel: +27 11 343 2000 | Fax: +27 11 442 5908 | Email: [email protected] Address: President Place, Johannesburg, South Africa PrismToken Thrift API 2019-01-16 Document number: PR-D2-1009 Rev 1.0.1 Release date: 2019-01-16 Prepared by: TrevorD Copyright: © 2019 Prism Payment Technologies Synopsis: Specifies the Application Programming Interface (API) for PrismToken. Company Confidential The information in this document is intended only for the person or the entity to which it is addressed and may contain confidential and/or privileged material. Any views, recreation, dissemination or other use of or taking of any action in reliance upon this information by persons or entities other than the intended recipient, is prohibited. Disclaimer Prism Payment Technologies makes no representations or warranties whether expressed or implied by or with respect to anything in this document, and shall not be liable for any implied warranties of merchantability or fitness for a particular purpose or for any indirect, special or consequential damages. Prism Payment Technologies (Pty) Ltd | Reg No. 1990/005062/07 Directors: H.G. Kotzé, N. Pillay, A.M.R. Smith (British)| Company Secretary: C.W. van Straaten www.prism.co.za PrismToken Thrift API (PR-D2-1009 Rev 1.0.1)| Page 2 Contents 1 Introduction ............................................................................... 4 1.1 PrismToken overview ............................................................................................................... 4 1.2 Thrift overview .........................................................................................................................