A Language Ifrofessional's Guide to the World Wide Web
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Origins of the Underline As Visual Representation of the Hyperlink on the Web: a Case Study in Skeuomorphism
The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Romano, John J. 2016. The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism. Master's thesis, Harvard Extension School. Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:33797379 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism John J Romano A Thesis in the Field of Visual Arts for the Degree of Master of Liberal Arts in Extension Studies Harvard University November 2016 Abstract This thesis investigates the process by which the underline came to be used as the default signifier of hyperlinks on the World Wide Web. Created in 1990 by Tim Berners- Lee, the web quickly became the most used hypertext system in the world, and most browsers default to indicating hyperlinks with an underline. To answer the question of why the underline was chosen over competing demarcation techniques, the thesis applies the methods of history of technology and sociology of technology. Before the invention of the web, the underline–also known as the vinculum–was used in many contexts in writing systems; collecting entities together to form a whole and ascribing additional meaning to the content. -

Maximum Internet Security: a Hackers Guide - Networking - Intrusion Detection
- Maximum Internet Security: A Hackers Guide - Networking - Intrusion Detection Exact Phrase All Words Search Tips Maximum Internet Security: A Hackers Guide Author: Publishing Sams Web Price: $49.99 US Publisher: Sams Featured Author ISBN: 1575212684 Benoît Marchal Publication Date: 6/25/97 Pages: 928 Benoît Marchal Table of Contents runs Pineapplesoft, a Save to MyInformIT consulting company that specializes in Internet applications — Now more than ever, it is imperative that users be able to protect their system particularly e-commerce, from hackers trashing their Web sites or stealing information. Written by a XML, and Java. In 1997, reformed hacker, this comprehensive resource identifies security holes in Ben co-founded the common computer and network systems, allowing system administrators to XML/EDI Group, a think discover faults inherent within their network- and work toward a solution to tank that promotes the use those problems. of XML in e-commerce applications. Table of Contents I Setting the Stage 1 -Why Did I Write This Book? 2 -How This Book Will Help You Featured Book 3 -Hackers and Crackers Sams Teach 4 -Just Who Can Be Hacked, Anyway? Yourself Shell II Understanding the Terrain Programming in 5 -Is Security a Futile Endeavor? 24 Hours 6 -A Brief Primer on TCP/IP 7 -Birth of a Network: The Internet Take control of your 8 -Internet Warfare systems by harnessing the power of the shell. III Tools 9 -Scanners 10 -Password Crackers 11 -Trojans 12 -Sniffers 13 -Techniques to Hide One's Identity 14 -Destructive Devices IV Platforms -

Previewserver-All Oses
USER DOCUMENTATION Preview Server – Voyager 8.0.0 CONFIDENTIAL INFORMATION The information herein is the property of Ex Libris Ltd. or its affiliates and any misuse or abuse will result in economic loss. DO NOT COPY UNLESS YOU HAVE BEEN GIVEN SPECIFIC WRITTEN AUTHORIZATION FROM EX LIBRIS LTD. This document is provided for limited and restricted purposes in accordance with a binding contract with Ex Libris Ltd. or an affiliate. The information herein includes trade secrets and is confidential. DISCLAIMER The information in this document will be subject to periodic change and updating. Please confirm that you have the most current documentation. There are no warranties of any kind, express or implied, provided in this documentation, other than those expressly agreed upon in the applicable Ex Libris contract. Any references in this document to non-Ex Libris Web sites are provided for convenience only and do not in any manner serve as an endorsement of those Web sites. The materials at those Web sites are not part of the materials for this Ex Libris product and Ex Libris has no liability for materials on those Web sites. Table of Contents 1 Introduction ...........................................................................................................................................................5 2 Preview Server Requirements .............................................................................................................................6 2.1 Browser Requirements ..................................................................................................................................6 -
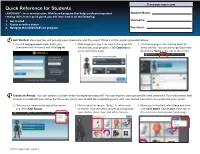
Quick Reference for Students LANGUAGE!® Live Is an Interactive, Web-Based Program That Helps You Learn Important Student Name: Reading Skills
ll.voyagersopris.com Quick Reference for Students LANGUAGE!® Live is an interactive, Web-based program that helps you learn important Student Name: reading skills. In this quick guide, you will learn how to do the following: 1. Get Started Username: 2. Create an online avatar 3. Navigate the LANGUAGE! Live program Password: Get Started. Your teacher will provide your Username and Password. Write it in the spaces provided above. 1. Go to ll.voyagersopris.com. Enter your 2. After logging in, you’ll see your training update 3. Your home page is the starting point for Username and Password, and click Log In! which tracks your progress. Click Continue to every activity. You can always get back here go to your home page. by clicking Home at the top of the screen. Create an Avatar. You can create a custom avatar to represent yourself. You can express your personality and creativity! Your classmates and teacher can identify you online by the avatar you have created. By completing each unit, you unlock new items to customize your avatar. 1. Click on your name at the top of the screen 2. Click on the first square, “Body,” to select male 3. When you’re finished, select Save and then and select Edit Avatar. or female. Click the other squares to personalize click Save Outfit. Click Home at the top of your clothes, shoes, hair, and other features. the screen to return to your home page. ©2015 Voyager Sopris Learning Quick Reference for Students Getting Started in LANGUAGE!® Live Navigate LANGUAGE! Live Your Home Page Lessons Sight Words Scorecard Click on Scorecard from the Class button at the top of the screen, and you can see When you click the blue button, or click When you click Play Sight Words (green your progress report. -

Personalizing Voyager Using Browser Extensions
University of Kentucky UKnowledge Library Presentations University of Kentucky Libraries 5-8-2015 Personalizing Voyager Using Browser Extensions Kathryn Lybarger University of Kentucky, [email protected] Right click to open a feedback form in a new tab to let us know how this document benefits oy u. Follow this and additional works at: https://uknowledge.uky.edu/libraries_present Part of the Cataloging and Metadata Commons Repository Citation Lybarger, Kathryn, "Personalizing Voyager Using Browser Extensions" (2015). Library Presentations. 128. https://uknowledge.uky.edu/libraries_present/128 This Presentation is brought to you for free and open access by the University of Kentucky Libraries at UKnowledge. It has been accepted for inclusion in Library Presentations by an authorized administrator of UKnowledge. For more information, please contact [email protected]. Personalizing Voyager using Browser Extensions Kathryn Lybarger @zemkat ELUNA 2015 #eluna2015 May 8, 2015 Personalizing Voyager As an institution, we have a fair amount of power over how Voyager’s OPAC looks Colors and fonts Which fields are searchable What displays in search results What displays in full record view … (anything really) Must find a balance Provide good access to most of our patrons Don’t clutter the interface needlessly But how about… Personalizing for particular groups of patrons? Personalizing for staff needs? Doing so quickly? Even temporarily? Web browser extensions Custom search bars Extensions Bookmarklets User scripts Browser -

Forensic Investigation of User's Web Activity on Google Chrome Using
IJCSNS International Journal of Computer Science and Network Security, VOL.16 No.9, September 2016 123 Forensic Investigation of User’s Web Activity on Google Chrome using various Forensic Tools Narmeen Shafqat, NUST, Pakistan Summary acknowledged browsers like Internet Explorer, Google Cyber Crimes are increasing day by day, ranging from Chrome, Mozilla Firefox, Safari, Opera etc. but should confidentiality violation to identity theft and much more. The also have hands on experience of less popular web web activity of the suspect, whether carried out on computer or browsers like Erwise, Arena, Cello, Netscape, iCab, smart device, is hence of particular interest to the forensics Cyberdog etc. Not only this, the forensic experts should investigator. Browser forensics i.e forensics of suspect’s browser also know how to find artifacts of interest from older history, saved passwords, cache, recent tabs opened etc. , therefore supply ample amount of information to the forensic versions of well-known web browsers; Internet Explorer, experts in case of any illegal involvement of the culprit in any Chrome and Mozilla Firefox atleast, because he might activity done on web browsers. Owing to the growing popularity experience a case where the suspected person is using and widespread use of the Google Chrome web browser, this older versions of these browsers. paper will forensically analyse the said browser in windows 8 According to StatCounter Global market share for the web environment, using various forensics tools and techniques, with browsers (2015), Google Chrome, Mozilla Firefox and the aim to reconstruct the web browsing activities of the suspect. Microsoft’s Internet Explorer make up 90% of the browser The working of Google Chrome in regular mode, private usage. -

Discontinued Browsers List
Discontinued Browsers List Look back into history at the fallen windows of yesteryear. Welcome to the dead pool. We include both officially discontinued, as well as those that have not updated. If you are interested in browsers that still work, try our big browser list. All links open in new windows. 1. Abaco (discontinued) http://lab-fgb.com/abaco 2. Acoo (last updated 2009) http://www.acoobrowser.com 3. Amaya (discontinued 2013) https://www.w3.org/Amaya 4. AOL Explorer (discontinued 2006) https://www.aol.com 5. AMosaic (discontinued in 2006) No website 6. Arachne (last updated 2013) http://www.glennmcc.org 7. Arena (discontinued in 1998) https://www.w3.org/Arena 8. Ariadna (discontinued in 1998) http://www.ariadna.ru 9. Arora (discontinued in 2011) https://github.com/Arora/arora 10. AWeb (last updated 2001) http://www.amitrix.com/aweb.html 11. Baidu (discontinued 2019) https://liulanqi.baidu.com 12. Beamrise (last updated 2014) http://www.sien.com 13. Beonex Communicator (discontinued in 2004) https://www.beonex.com 14. BlackHawk (last updated 2015) http://www.netgate.sk/blackhawk 15. Bolt (discontinued 2011) No website 16. Browse3d (last updated 2005) http://www.browse3d.com 17. Browzar (last updated 2013) http://www.browzar.com 18. Camino (discontinued in 2013) http://caminobrowser.org 19. Classilla (last updated 2014) https://www.floodgap.com/software/classilla 20. CometBird (discontinued 2015) http://www.cometbird.com 21. Conkeror (last updated 2016) http://conkeror.org 22. Crazy Browser (last updated 2013) No website 23. Deepnet Explorer (discontinued in 2006) http://www.deepnetexplorer.com 24. Enigma (last updated 2012) No website 25. -
![Web Technologies [R18a0517] Lecture Notes](https://docslib.b-cdn.net/cover/1694/web-technologies-r18a0517-lecture-notes-831694.webp)
Web Technologies [R18a0517] Lecture Notes
WEB TECHNOLOGIES [R18A0517] LECTURE NOTES B.TECH III YEAR – II SEM(R18) (2020-21) DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING MALLA REDDY COLLEGE OF ENGINEERING & TECHNOLOGY (Autonomous Institution – UGC, Govt. of India) Recognized under 2(f) and 12 (B) of UGC ACT 1956 (Affiliated to JNTUH, Hyderabad, Approved by AICTE - Accredited by NBA & NAAC – ‘A’ Grade - ISO 9001:2015 Certified) Maisammaguda, Dhulapally (Post Via. Hakimpet), Secunderabad – 500100, Telangana State, India III Year B. Tech. CSE –II Sem L T/P/D C 4 1/- / - 3 (R18A0517) WEB TECHNOLOGIES Objectives: Giving the students the insights of the Internet programming and how to design and implement complete applications over the web. It covers the notions of Web servers and Web Application Servers, Design Methodologies with concentration on Object-Oriented concepts, Client-Side Programming, Server-Side Programming, Active Server Pages, Database Connectivity to web applications, Adding Dynamic content to web applications, Programming Common Gateway Interfaces, Programming the User Interface for the web applications. UNIT I: Web Basics and Overview: Introduction to Internet, World Wide Web, Web Browsers, URL, MIME, HTTP, Web Programmers Tool box. HTML Common tags: List, Tables, images, forms, frames, Basics of CSS and types of CSS. Client-Side Programming (Java Script): Introduction to Java Script, declaring variables, functions, Event handlers (onclick, onsubmit, etc.,) and Form Validation. UNIT II: Server-Side Programming (PHP): Declaring Variables, Data types, Operators, Control structures, Functions, Reading data from web form controls like text buttons, radio buttons, list, etc., Handling File Uploads, Handling Sessions & Cookies. Introduction to XML: Document type definition, XML Schemas, Document Object model, Presenting XML , Introduction to XHTML, Using XML Processors: DOM and SAX. -

Avianca in Brazil
REFERENCE GUIDE 2015 STAR ALLIANCE WELCOMES AVIANCA IN BRAZIL FOR EMPLOYEES OF STAR ALLIANCE MEMBER CARRIERS 18th Edition, July 2015 WELCOME WELCOME TO THE 2015 EDITION OF THE STAR ALLIANCE REFERENCE GUIDE This edition includes baggage, airport and frequent flyer information for our newest member, Avianca in Brazil. Its flights, operated under the Avianca logo and the O6 two-letter code, add new unique destinations in the fast-growing Brazilian market. The addition of Avianca in Brazil brings the Star Alliance membership to 28 airlines. This guide is designed to provide a user-friendly tool that gives quick access to the information needed to deliver a smoother travel experience to international travellers. Information changes regularly, so please continue to consult your airline’s publications and information systems for changes and updates, as well as for operational information and procedures. We welcome your feedback at [email protected]. Thank you, Star Alliance Internal Communications 2 TABLE OF CONTENTS OVERVIEW AIRPORTS INFORMATION 68 Welcome 2 Priority Baggage Handling 69 Greetings from Avianca in Brazil 4 Free Checked Baggage Allowances 70 Vision / Mission 5 Special Checked Baggage 75 Facts & Figures 6 Carry-on Baggage Policy 133 Irregular Operations Handling 134 GENERAL INFORMATION 10 Interline E-Ticketing FAQ - Airports 139 Customer Benefits 11 Frequent Flyer Programmes 15 Reservation Call Centres 19 LOUNGE INFORMATION 141 Reservations Special Service Items 51 Lounge Access 142 Booking Class Alignment 53 Lounge Access Chart 148 Ticketing Procedures 60 Destinations with Lounges 151 Interline E-Ticket FAQ - Reservations 64 GDS Access Codes 67 MAJOR AIRPORT MAPS 173 World Time Zones 254 Star Alliance Services GmbH, Frankfurt Airport Centre, Main Lobby, D-60546 Frankfurt∕Main Vice-President, Director, Internal Editor Layout Photography Corporate Office Communication Garry Bridgewater, Rachel Niebergal, Ted Fahn, British Airports Authority Christian Klick Janet Northcote Sherana Productions Peridot Design Inc. -

Annex I: List of Internet Robots, Crawlers, Spiders, Etc. This Is A
Annex I: List of internet robots, crawlers, spiders, etc. This is a revised list published on 15/04/2016. Please note it is rationalised, removing some previously redundant entries (e.g. the text ‘bot’ – msnbot, awbot, bbot, turnitinbot, etc. – which is now collapsed down to a single entry ‘bot’). COUNTER welcomes updates and suggestions for this list from our community of users. bot spider crawl ^.?$ [^a]fish ^IDA$ ^ruby$ ^voyager\/ ^@ozilla\/\d ^ÆƽâºóµÄ$ ^ÆƽâºóµÄ$ alexa Alexandria(\s|\+)prototype(\s|\+)project AllenTrack almaden appie Arachmo architext aria2\/\d arks ^Array$ asterias atomz BDFetch Betsie biadu biglotron BingPreview bjaaland Blackboard[\+\s]Safeassign blaiz\-bee bloglines blogpulse boitho\.com\-dc bookmark\-manager Brutus\/AET bwh3_user_agent CakePHP celestial cfnetwork checkprivacy China\sLocal\sBrowse\s2\.6 cloakDetect coccoc\/1\.0 Code\sSample\sWeb\sClient ColdFusion combine contentmatch ContentSmartz core CoverScout curl\/7 cursor custo DataCha0s\/2\.0 daumoa ^\%?default\%?$ Dispatch\/\d docomo Download\+Master DSurf easydl EBSCO\sEJS\sContent\sServer ELinks\/ EmailSiphon EmailWolf EndNote EThOS\+\(British\+Library\) facebookexternalhit\/ favorg FDM(\s|\+)\d feedburner FeedFetcher feedreader ferret Fetch(\s|\+)API(\s|\+)Request findlinks ^FileDown$ ^Filter$ ^firefox$ ^FOCA Fulltext Funnelback GetRight geturl GLMSLinkAnalysis Goldfire(\s|\+)Server google grub gulliver gvfs\/ harvest heritrix holmes htdig htmlparser HttpComponents\/1.1 HTTPFetcher http.?client httpget httrack ia_archiver ichiro iktomi ilse -

Student Handbook 201 Emily Dickinson Elementary &
Lake Washington School District Lake Washington Parent & Student Handbook 201 Emily Dickinson Elementary & Explorer Commu9-2020 nity School Washington Achievement Award Winner Emily Dickinson Elementary • Explorer Community School 7040 208th Ave N.E. Redmond, WA 98053 Phone: (425) 836-4658 • Fax: (425) 836-4658 Safe Arrival Attendance Line: (425) 936-2531 Principal: Barbara Pridgeon Associate Principal: Heidi Lane Dickinson School Mascot: Dragons Dickinson School Colors: Green and Yellow Explorer School Mascot: Eagles Explorer School Colors: Blue and White 2019-20 Student Rights & Responsibilities - Updated 7/31/2019 | Page A1 Lake Washington School District Lake Washington EMILY DICKINSON ELEMENTARY DAILY SCHEDULE MONDAY, TUESDAY, THURSDAY, FRIDAY 9:00-9:15 Student Drop Off 9:15 AM Line-up Bell 9:20 AM Instruction Begins 3:50 PM School Ends 4:00 PM All Students Off Campus WEDNESDAY 9:00-9:15 Student Drop Off 9:15 AM Line-up Bell 9:20 AM Instruction Begins 2:20 PM School Ends 2:30 PM All Students Off Campus HALF-DAY (For Conferences/No Lunch Served) 9:05-9:15 Student Drop Off 9:20 AM Instruction Begins 12:20 PM School Ends 12:30 PM All Students Off Campus Recess and Lunches 11:40-12:05 K-2 Lunch 12:05-12:35 K-2 Recess 12:15-12:35 3-5 Lunch 12:35-1:05 3-5 Recess 12:15-12:35 Explorer Lunch 12:35-1:05 Explorer Recess 2019-20 Student Rights & Responsibilities - Updated 7/31/2019| Page A2 Lake Washington School District Lake Washington EXPLORER COMMUNITY SCHOOL DAILY SCHEDULE MONDAY, TUESDAY, THURSDAY, FRIDAY 8:50-9:00 Student Drop Off 9:05 -

Why Websites Can Change Without Warning
Why Websites Can Change Without Warning WHY WOULD MY WEBSITE LOOK DIFFERENT WITHOUT NOTICE? HISTORY: Your website is a series of files & databases. Websites used to be “static” because there were only a few ways to view them. Now we have a complex system, and telling your webmaster what device, operating system and browser is crucial, here’s why: TERMINOLOGY: You have a desktop or mobile “device”. Desktop computers and mobile devices have “operating systems” which are software. To see your website, you’ll pull up a “browser” which is also software, to surf the Internet. Your website is a series of files that needs to be 100% compatible with all devices, operating systems and browsers. Your website is built on WordPress and gets a weekly check up (sometimes more often) to see if any changes have occured. Your site could also be attacked with bad files, links, spam, comments and other annoying internet pests! Or other components will suddenly need updating which is nothing out of the ordinary. WHAT DOES IT LOOK LIKE IF SOMETHING HAS CHANGED? Any update to the following can make your website look differently: There are 85 operating systems (OS) that can update (without warning). And any of the most popular roughly 7 browsers also update regularly which can affect your site visually and other ways. (Lists below) Now, with an OS or browser update, your site’s 18 website components likely will need updating too. Once website updates are implemented, there are currently about 21 mobile devices, and 141 desktop devices that need to be viewed for compatibility.