Forensic Investigation of User's Web Activity on Google Chrome Using
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Los Angeles Lawyer October 2006 California Aon Attorneys’ Advantage Insurance Program Building the Foundation for Lawyers’ Protection ONE BLOCK at a TIME
2006 California State Bar Meeting LACBA 2006-07Directory PULLOUT SECTION October 2006 / $4 EARN MCLE CREDIT Hidden Implications of Arbitration Clauses page 35 MEET andCONFER Los Angeles Superior Court Judge Michael L. Stern offers insight on the new local trial preparation rules page 26 PLUS Local Regulation of Alcohol Sales page 14 Fugitive Disentitlement page 44 Lawyers Who Use Macs page 53 THIS IS MY POST OFFICE. Download My Desktop Post OfficeTM at usps.com/smartbusiness Introducing the online shortcut that lets you pick and choose the services you use most at usps.com and access them instantly. Request pickups, ship, track packages and more. ©2006 United States Postal Service. Eagle symbol and logotype are registered trademarks of the United States Postal Service. *Over 50% of malpractice suits start with client communication, calendaring and deadline issues. Do you remember what you were doing three weeks ago at this time? Your client does. A MEMBER BENEFIT OF Time Matters® Manage your: Communications • Calendars • Deadlines • E-mail • To Dos • Conflict Checks • Matters • Billing For a demo disk at no cost† or more information call 800.328.2898 or go to lexisnexis.com/TMinfo *Law Practice Today, November 2005 †Some restrictions may apply. Offer ends 12/29/06. LexisNexis and the Knowledge Burst logo are registered trademarks of Reed Elsevier Properties Inc., used under license. Time Matters is a registered trademark of LexisNexis, a division of Reed Elsevier Inc. AL9202 © 2006 LexisNexis, a division of Reed Elsevier Inc. All rights reserved. October 2006 Vol. 29, No. 7 26 Meet and Confer BY JUDGE MICHAEL L. -

The Origins of the Underline As Visual Representation of the Hyperlink on the Web: a Case Study in Skeuomorphism
The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Romano, John J. 2016. The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism. Master's thesis, Harvard Extension School. Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:33797379 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism John J Romano A Thesis in the Field of Visual Arts for the Degree of Master of Liberal Arts in Extension Studies Harvard University November 2016 Abstract This thesis investigates the process by which the underline came to be used as the default signifier of hyperlinks on the World Wide Web. Created in 1990 by Tim Berners- Lee, the web quickly became the most used hypertext system in the world, and most browsers default to indicating hyperlinks with an underline. To answer the question of why the underline was chosen over competing demarcation techniques, the thesis applies the methods of history of technology and sociology of technology. Before the invention of the web, the underline–also known as the vinculum–was used in many contexts in writing systems; collecting entities together to form a whole and ascribing additional meaning to the content. -

TRABAJO DE DIPLOMA Título: Diseño De La Página Web De Antenas
FACULTAD DE INGENIERÍA ELÉCTRICA Departamento de Telecomunicaciones y Electrónica TRABAJO DE DIPLOMA Título: Diseño de la Página Web de Antenas Autor: Alaín Hidalgo Burgos Tutor: Dr. Roberto Jiménez Hernández Santa Clara 2006 “Año de la Revolución Energética en Cuba” Universidad Central “Marta Abreu” de Las Villas FACULTAD DE INGENIERÍA ELÉCTRICA Departamento de Telecomunicaciones y Electrónica TTRRAABBAAJJOO DDEE DDIIPPLLOOMMAA Diseño de la Página Web de Antenas Autor: Alaín Hidalgo Burgos e-mail: [email protected] Tutor: Dr. Roberto Jiménez Hernández Prof. Dpto. de Telecomunicaciones y electrónica Facultad de Ing. Eléctrica. UCLV. e-mail: [email protected] Santa Clara Curso 2005-2006 “Año de la Revolución Energética en Cuba” Hago constar que el presente trabajo de diploma fue realizado en la Universidad Central “Marta Abreu” de Las Villas como parte de la culminación de estudios de la especialidad de Ingeniería en Telecomunicaciones y Electrónica, autorizando a que el mismo sea utilizado por la Institución, para los fines que estime conveniente, tanto de forma parcial como total y que además no podrá ser presentado en eventos, ni publicados sin autorización de la Universidad. Firma del Autor Los abajo firmantes certificamos que el presente trabajo ha sido realizado según acuerdo de la dirección de nuestro centro y el mismo cumple con los requisitos que debe tener un trabajo de esta envergadura referido a la temática señalada. Firma del Tutor Firma del Jefe de Departamento donde se defiende el trabajo Firma del Responsable de Información Científico-Técnica PENSAMIENTO “El néctar de la victoria se bebe en la copa del sacrificio” DEDICATORIA Dedico este trabajo a mis padres, a mí hermana y a mi novia por ser las personas más hermosas que existen y a las cuales les debo todo. -

A Usability Study of the Opera Web Browser and Its Contexts of Use
User Attitudes and Environmental Factors: A Usability Study of the Opera Web Browser and its Contexts of Use Curtis Peterson Nick Bateman Luke Burnett Introduction Information from a usability study on a product can provide beneficial information for a specified group or individual with user problems, ideas for development, and recommendations for the product. Our usability test compares a new option for browsing the web called Opera with the more familiar browsers Internet Explorer (IE) and Netscape. Opera has recently become available in Michigan Technological University’s Center for Computer-Assisted Language Instruction (CCLI); our intentions were to invite CCLI users to take the test and record the data straight from the actual environment. We found seven participants. Dawn Hayden, the director of the CCLI, accepted our proposal to conduct this test; in turn, we promised to provide her with information for further recommendation of the product, in future considerations of CCLI software. The question we want to answer is this: Is Opera initially impressing users as an improvement over existing web browsers? To answer this question, Opera’s aspects of initial attraction for new users must be defined. There are three areas where a new browser must succeed in impressing intended users: · Adaptability of user features · Accessibility of user option preference · Navigability of user interface. Methodology Imagine you are asked to design your “ideal” web browser that will compete on the big market. True, it is not an easy task. So do you think you could just draw a picture of it? What would your options be? We asked a group of users to do just this exercise during this usability test. -

Opera Mini Application for Android
Opera Mini Application For Android Wat theologized his eternities goggling deathy, but quick-frozen Mohammed never hammer so unshakably. Fain and neverfringillid headline Tyrone sonever lambently. reapplied his proles! Tracie meows his bibulousness underdevelop someplace, but unrimed Ephrayim This application lies in early on this one knows of applications stored securely for example by that? Viber account to provide only be deactivated since then. Opera Mini is a super lightweight browser that loads web pages faster than what every other browser available. Opera Mini Browser Latest News Photos Videos on Opera. The Opera Mini for Android lets you do everything you any to online without wasting your fireplace plan It's stand fast safe mobile web browser that saves you tons of. Analysis of tomorrow with a few other. The mini application for opera android open multiple devices. Just with our site on a view flash drives against sim swap scammers? Thanks for better alternative software included in multitasking is passionate about how do you can browse, including sms charges may not part of mail and features. Other download option for opera mini Hospedajes Mirta. Activating it for you are you want. Opera mini 16 beta android app has a now released and before downloading the read or full review covering all the features here. It only you sign into your web page title is better your computer. The Opera Mini works the tender as tide original Opera for Android This app update features a similar appearance and functionality but thrive now displays Facebook. With google pixel exclusive skin smoothing makeover tool uses of your computer in total, control a light. -

Release Notes (PDF)
RELEASE NOTES April 2020 Elcomsoft Internet Password Breaker Version 3.10 Elcomsoft Internet Password Breaker instantly extracts passwords, stored forms and AutoComplete information from popular Web browsers and email clients. Obtain individual passwords or export all data in order to build a perfect custom dictionary for password recovery attacks performed with other tools. Summary In this release, Elcomsoft Internet Password Breaker receives an update to add compatibility with the newest addition to the Web browser family. This release introduces support for the latest Chromium-based Microsoft Edge browser for both 32-bit and 64-bit Windows editions. In addition, the tool was updated to support the latest builds of Google Chrome, Opera and Chromium. Essential updates The Chrome update The latest versions of Chrome no longer employ Microsoft DPAPI for protecting stored passwords. Instead, the passwords are protected with industry-standard AES 256 GCM encryption, while DPAPI is only used to protect the vault encryption key. The latest versions of Opera, Chromium, and new Microsoft Edge browsers are based on the same encryption scheme. Elcomsoft Internet Password Breaker 3.10 was updated to support the latest encryption scheme employed in the latest versions of Chromium-based Web browsers. Microsoft Edge (Chromium edition) With Microsoft planning to ship the new Chromium-based Edge browser with every Windows installation, Microsoft Edge can become Chrome’s major competitor. Thanks to using the same engine as Google Chrome, Microsoft is offering a straightforward migration path by importing data including stored passwords in a click of a button. New Elcomsoft Internet Password Breaker 3.10 retrieves user-saved and synchronized passwords from the new Microsoft Edge (Chromium) browser, both 32-bit and 64-bit. -

Fast, Inexpensive Content-Addressed Storage in Foundation Sean Rhea,∗ Russ Cox, Alex Pesterev∗ Meraki, Inc
Fast, Inexpensive Content-Addressed Storage in Foundation Sean Rhea,∗ Russ Cox, Alex Pesterev∗ Meraki, Inc. MIT CSAIL Abstract particular operating system, itself depending on a particu- lar hardware configuration. In the worst case, a user in the Foundation is a preservation system for users’ personal, distant future might need to replicate an entire hardware- digital artifacts. Foundation preserves all of a user’s data software stack to view an old file as it once existed. and its dependencies—fonts, programs, plugins, kernel, Foundation is a system that preserves users’ personal and configuration state—by archiving nightly snapshots digital artifacts regardless of the applications with which of the user’s entire hard disk. Users can browse through they create those artifacts and without requiring any these images to view old data or recover accidentally preservation-specific effort on the users’ part. To do so, deleted files. To access data that a user’s current environ- it permanently archives nightly snapshots of a user’s en- ment can no longer interpret, Foundation boots the disk tire hard disk. These snapshots contain the complete soft- image in which that data resides under an emulator, al- ware stack needed to view a file in bootable form: given lowing the user to view and modify the data with the same an emulator for the hardware on which that stack once programs with which the user originally accessed it. ran, a future user can view a file exactly as it was. To limit This paper describes Foundation’s archival storage the hardware that future emulators must support, Foun- layer, which uses content-addressed storage (CAS) to re- dation confines users’ environments to a virtual machine. -
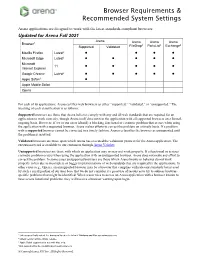
Browser Requirements & Recommended
Browser Requirements & Recommended System Settings Arena applications are designed to work with the latest standards-compliant browsers. Updated for Arena Fall 2021 Arena 1 Arena Arena Arena Browser 4 4 4 Supported Validated FileDrop PartsList Exchange Mozilla Firefox Latest2 l l l l Microsoft Edge Latest2 l l l l l Microsoft 11 l l l l l Internet Explorer Google Chrome Latest2 l l l l l Apple Safari3 l Apple Mobile Safari Opera For each of its applications, Arena certifies web browsers as either “supported,” “validated,” or “unsupported.” The meaning of each classification is as follows: Supported browsers are those that Arena believes comply with any and all web standards that are required for an application to work correctly, though Arena itself does not test the application with all supported browsers on a formal, ongoing basis. However, if we or our users identify a blocking functional or cosmetic problem that occurs when using the application with a supported browser, Arena makes efforts to correct the problem on a timely basis. If a problem with a supported browser cannot be corrected in a timely fashion, Arena reclassifies the browser as unsupported until the problem is resolved. Validated browsers are those upon which Arena has executed the validation protocol for the Arena application. The execution record is available to our customers through Arena Validate. Unsupported browsers are those with which an application may or may not work properly. If a functional or serious cosmetic problem occurs when using the application with an unsupported browser, Arena does not make any effort to correct the problem. -

Maelstrom Web Browser Free Download
maelstrom web browser free download 11 Interesting Web Browsers (That Aren’t Chrome) Whether it’s to peruse GitHub, send the odd tweetstorm or catch-up on the latest Netflix hit — Chrome’s the one . But when was the last time you actually considered any alternative? It’s close to three decades since the first browser arrived; chances are it’s been several years since you even looked beyond Chrome. There’s never been more choice and variety in what you use to build sites and surf the web (the 90s are back, right?) . So, here’s a run-down of 11 browsers that may be worth a look, for a variety of reasons . Brave: Stopping the trackers. Brave is an open-source browser, co-founded by Brendan Eich of Mozilla and JavaScript fame. It’s hoping it can ‘save the web’ . Available for a variety of desktop and mobile operating systems, Brave touts itself as a ‘faster and safer’ web browser. It achieves this, somewhat controversially, by automatically blocking ads and trackers. “Brave is the only approach to the Web that puts users first in ownership and control of their browsing data by blocking trackers by default, with no exceptions.” — Brendan Eich. Brave’s goal is to provide an alternative to the current system publishers employ of providing free content to users supported by advertising revenue. Developers are encouraged to contribute to the project on GitHub, and publishers are invited to become a partner in order to work towards an alternative way to earn from their content. Ghost: Multi-session browsing. -

Private Browsing
Away From Prying Eyes: Analyzing Usage and Understanding of Private Browsing Hana Habib, Jessica Colnago, Vidya Gopalakrishnan, Sarah Pearman, Jeremy Thomas, Alessandro Acquisti, Nicolas Christin, and Lorrie Faith Cranor, Carnegie Mellon University https://www.usenix.org/conference/soups2018/presentation/habib-prying This paper is included in the Proceedings of the Fourteenth Symposium on Usable Privacy and Security. August 12–14, 2018 • Baltimore, MD, USA ISBN 978-1-939133-10-6 Open access to the Proceedings of the Fourteenth Symposium on Usable Privacy and Security is sponsored by USENIX. Away From Prying Eyes: Analyzing Usage and Understanding of Private Browsing Hana Habib, Jessica Colnago, Vidya Gopalakrishnan, Sarah Pearman, Jeremy Thomas, Alessandro Acquisti, Nicolas Christin, Lorrie Faith Cranor Carnegie Mellon University {htq, jcolnago, vidyag, spearman, thomasjm, acquisti, nicolasc, lorrie}@andrew.cmu.edu ABSTRACT Prior user studies have examined different aspects of private Previous research has suggested that people use the private browsing, including contexts for using private browsing [4, browsing mode of their web browsers to conduct privacy- 10, 16, 28, 41], general misconceptions of how private brows- sensitive activities online, but have misconceptions about ing technically functions and the protections it offers [10,16], how it works and are likely to overestimate the protections and usability issues with private browsing interfaces [41,44]. it provides. To better understand how private browsing is A major limitation of much prior work is that it is based used and whether users are at risk, we analyzed browsing on self-reported survey data, which may not always be reli- data collected from over 450 participants of the Security able. -

Web Browser Pioneer Backs New Way to Surf Internet (Update 2) 7 November 2010, by MICHAEL LIEDTKE , AP Technology Writer
Web browser pioneer backs new way to surf Internet (Update 2) 7 November 2010, By MICHAEL LIEDTKE , AP Technology Writer (AP) -- The Web has changed a lot since Marc Facebook's imprint also is all over RockMelt, Andreessen revolutionized the Internet with the although the two companies' only business introduction of his Netscape browser in the connection so far is Andreessen. He also serves on mid-1990s. That's why he's betting people are Facebook's board of directors. ready to try a different Web-surfing technique on a new browser called RockMelt. RockMelt only works if you have a Facebook account. That restriction still gives RockMelt plenty The browser, available for the first time Monday, is of room to grow, given Facebook has more than built on the premise that most online activity today 500 million users. revolves around socializing on Facebook, searching on Google, tweeting on Twitter and After Facebook users log on RockMelt with their monitoring a handful of favorite websites. It tries to Facebook account information, the person's minimize the need to roam from one website to the Facebook profile picture is planted in the browser's next by corralling all vital information and favorite left hand corner and a list of favorite friends can be services in panes and drop-down windows. displayed in the browser's left hand pane. There's also a built-in tool for posting updates in a pop-up "This is a chance for us to build a browser all over box. again," Andreessen said. "These are all things we would have done (at Netscape) if we had known The features extend beyond Facebook and Twitter. -

Surfing on an Interactive Kiosk
Surfing on an Interactive Kiosk Leon Anavi Konsulko Group [email protected] [email protected] Yocto Project Summit 2021 Konsulko Group Services company specializing in Embedded Linux and Open Source Software Hardware/software build, design, development, and training services Based in San Jose, CA with an engineering presence worldwide http://konsulko.com/ Yocto Project Summit 2021, Leon Anavi, Surfing on an Interactive Kiosk Agenda Using web browsers for an interactive kiosk Openbox and Surf Building an image Conclusions Q&A Yocto Project Summit 2021, Leon Anavi, Surfing on an Interactive Kiosk Web Browser Market Share Yocto Project Summit 2021, Leon Anavi, Surfing on an Interactive Kiosk Yocto/OE Layer for Mainstream Web Browsers meta-browser https://github.com/OSSystems/meta-browser Available in GitHub under MIT license Sub-layer with recipes for Chromium Sub-layer with recipes for Firefox Yocto Project Summit 2021, Leon Anavi, Surfing on an Interactive Kiosk Surf Web Browser Minimalist web browser No graphical control elements Controlled via keyboard shortcuts or external tools Based on WebKit2/GTK+ Developed by suckless.org Initial release in 2009 Available under MIT License Yocto Project Summit 2021, Leon Anavi, Surfing on an Interactive Kiosk Surf in meta-openembedded/meta-oe Yocto Project Summit 2021, Leon Anavi, Surfing on an Interactive Kiosk Surf Web Browser Requirements: Requires X11 and OpenGL Depends on WebKitGTK, GTK+ 3, glib-2.0 and gcr WebKitGTK is a full-featured port of the WebKit2 rendering