Original Paper Written & Signed by William F
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

(U) a History of Secure Voice Codin~: Insights Drawn from the Career of One of Tile Earliest Practitioners of the Art of Speech Coding JOSEPH P
DOCID: 3860926 UNCLASSIFIED Cryptologic Quarter1y (U) A History of Secure Voice Codin~: Insights Drawn from the Career of One of tile Earliest Practitioners of the Art of Speech Coding JOSEPH P. CAMPBELL, JR., and RICHARD A. DEAN Editor's Note: This artrde Is basecl on one publlshecl In Dlgittl Signal Processing, July 1993, wfth permission ofthe authors. The history of speech coding is closely tied to tion of PCM. A "Buzz" /"Hiss" generator was used the career of Tom Tremain. He joined the as an exciter for the vocoder corresponding to the National Security Agency i~ 1959 as an Air Force voiced/unvoiced attribute of each 20-ms speech lieutenant assigned to duty at the Agency. Llttle segment. Balance of the "Buzz" /"Hiss" generator, did he know then that this assignment would or voicing, represented a major factor in the qual shape his career as well as' the future of speech ity of the speech. Early practitioners of speech coding. 1 coders, like Tom, can still be found today speak I . ing"Aaahhh" /"Sshhhhh" into voice coders to test Thomas E. Tremain was the U.S. govern- this balance. ment's senior speech scientist. He was a recog nized leader and an expert in speech science. From the time of SIGSALY until Tom arrived 1 Tom's work spanned five dife3des of state-of-the- at NSA, several generations of voice coders had art modem and speech co<;Iing innovations that been developed in conjunction with Bell Labs. are the basis of virtually e~ery U.S. and NATO The K0-6 voice coder, developed in 1949 and modem and speech coding standard. -

The First Devices to Secure Transmission of Voice Were Developed Just After World War I
F, 5 January Cabinet War Rooms SIGSALY The first devices to secure transmission of voice were developed just after World War I. They were substitution devices; they inverted frequencies. High frequencies were substituted for low frequencies and low frequencies were substituted for high frequencies. This was easy to do electronically. But, it was also easy to break. In fact, because much voice is in the middle frequencies and the middle frequencies are not changed much by inversion, it was sometimes possible to get a sense of the message just from the ciphertext. The A-3 scrambler … was based upon 1920s concepts. It divided the voice-frequency band into five subbands, inverted each of them, and then shifted the voice from one subband to another every 20 seconds. David Kahn Cryptology and the origin of spread spectrum In 1941, the United States was not at war although we were supporting the Allies, especially Britain, materially. The United States had a device to secure voice transmission called the A-3 Scrambler. This device used both substitution and transposition to encipher voice. Messages were chopped into small pieces, in each piece substitution was made by inverting frequencies, and the pieces were scrambled. This device was broken by the Germans during Fall 1941. The United States military was aware that the A-3 was not secure. On December 7, 1941, cryptanalysts in Washington, D.C., were in the process of breaking a long ciphertext from Tokyo to the Japanese embassy in Washington, D.C. William Friedman’s SIS team had earlier broken the Japanese diplomatic ciphers, but the naval ciphers had not yet been broken. -

TICOM: the Last Great Secret of World War II Randy Rezabek Version of Record First Published: 27 Jul 2012
This article was downloaded by: [Randy Rezabek] On: 28 July 2012, At: 18:04 Publisher: Routledge Informa Ltd Registered in England and Wales Registered Number: 1072954 Registered office: Mortimer House, 37-41 Mortimer Street, London W1T 3JH, UK Intelligence and National Security Publication details, including instructions for authors and subscription information: http://www.tandfonline.com/loi/fint20 TICOM: The Last Great Secret of World War II Randy Rezabek Version of record first published: 27 Jul 2012 To cite this article: Randy Rezabek (2012): TICOM: The Last Great Secret of World War II, Intelligence and National Security, 27:4, 513-530 To link to this article: http://dx.doi.org/10.1080/02684527.2012.688305 PLEASE SCROLL DOWN FOR ARTICLE Full terms and conditions of use: http://www.tandfonline.com/page/terms-and- conditions This article may be used for research, teaching, and private study purposes. Any substantial or systematic reproduction, redistribution, reselling, loan, sub-licensing, systematic supply, or distribution in any form to anyone is expressly forbidden. The publisher does not give any warranty express or implied or make any representation that the contents will be complete or accurate or up to date. The accuracy of any instructions, formulae, and drug doses should be independently verified with primary sources. The publisher shall not be liable for any loss, actions, claims, proceedings, demand, or costs or damages whatsoever or howsoever caused arising directly or indirectly in connection with or arising out of the use of this material. Intelligence and National Security Vol. 27, No. 4, 513–530, August 2012 TICOM: The Last Great Secret of World War II RANDY REZABEK* ABSTRACT Recent releases from the National Security Agency reveal details of TICOM, the mysterious 1945 operation targeting Germany’s cryptologic secrets. -
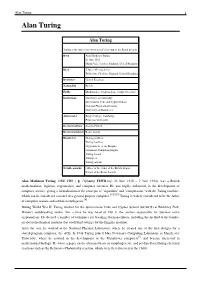
Alan Turing 1 Alan Turing
Alan Turing 1 Alan Turing Alan Turing Turing at the time of his election to Fellowship of the Royal Society. Born Alan Mathison Turing 23 June 1912 Maida Vale, London, England, United Kingdom Died 7 June 1954 (aged 41) Wilmslow, Cheshire, England, United Kingdom Residence United Kingdom Nationality British Fields Mathematics, Cryptanalysis, Computer science Institutions University of Cambridge Government Code and Cypher School National Physical Laboratory University of Manchester Alma mater King's College, Cambridge Princeton University Doctoral advisor Alonzo Church Doctoral students Robin Gandy Known for Halting problem Turing machine Cryptanalysis of the Enigma Automatic Computing Engine Turing Award Turing test Turing patterns Notable awards Officer of the Order of the British Empire Fellow of the Royal Society Alan Mathison Turing, OBE, FRS ( /ˈtjʊərɪŋ/ TEWR-ing; 23 June 1912 – 7 June 1954), was a British mathematician, logician, cryptanalyst, and computer scientist. He was highly influential in the development of computer science, giving a formalisation of the concepts of "algorithm" and "computation" with the Turing machine, which can be considered a model of a general purpose computer.[1][2][3] Turing is widely considered to be the father of computer science and artificial intelligence.[4] During World War II, Turing worked for the Government Code and Cypher School (GC&CS) at Bletchley Park, Britain's codebreaking centre. For a time he was head of Hut 8, the section responsible for German naval cryptanalysis. He devised a number of techniques for breaking German ciphers, including the method of the bombe, an electromechanical machine that could find settings for the Enigma machine. -

Gold Lock 3G White Paper
Gold Lock EnterpriseTM White Paper Military Grade Protection Using Gold Lock Enterprise™ White Paper Hybrid Secure Telephone Encryption: The Best of Both Worlds In today's global information-based economy, the ability to communicate confidential information securely is an absolute business necessity. Advances in technology have enabled instantaneous, reliable transmission of voice and data. However, secure telecommunications has remained a challenge. Until quite recently, the technology used to encode communications so that only the intended recipient can understand it – called cryptography – has lagged behind the capabilities of clever codebreakers. In the last few decades, codes based on “trapdoor” mathematical functions1 – functions that are easy to calculate, but hard to invert – have made highly secure communications possible. Indeed, today's encryption methods are far more secure than the abilities of codebreakers to decrypt messages. This document will present an overview of the following topics: Corporate espionage as it relates to mobile devices The history of secure phones Internet-based telecommunications technologies (Voice over Internet Protocol, or VoIP) Threats against secure mobile telecommunications Cryptographic methods used in mobile telecommunications today This document is not intended as a technical or mathematical treatment of cryptography, although references are provided for those interested in the subject. Instead, it discusses business requirements for secure wireless communications, and the optimal solutions that meet these requirements. A brief overview of cryptography will show that there have been two primary types of systems, referred to as asymmetric and symmetric. Each type of system has advantages and disadvantages. This paper will demonstrate that a hybrid system is the ideal implementation of wireless cryptography. -

Rachel Lundberg in a Wartime Situation, Speed of Communication
Rachel Lundberg In a wartime situation, speed of communication is drastically important. As the setting of World War II brought many new methods of encipherment into play, this became especially clear. The efficiency with which a message could be enciphered and transmitted was in direct correlation with the method’s usefulness. The quickest way to transmit messages, of course, was by telephone, but telephone scramblers were usually not very secure. By the end of 1941, the Allies were beginning to suspect that the A-3, their primary telephone scrambler, had been broken. In fact, the German organization in charge of monitoring telecommunications, the Deutsche Reichspost, had been cracking it for several months, and was even capable of deciphering A-3 transmissions in real time (Weadon, Boone and Peterson). It was clear to the Allies that they needed a new way of protecting their telephone messages. In 1942, Bell Telephone Laboratories stepped up to the challenge. The project was led by A. B. Clark, the researcher who originally patented the companding (compressing and expanding of waveforms) technique that would prove vital to Bell Labs’ efforts (Weadon). Clark was assisted by Alan Turing, the British mathematician, during his trip to the United States to work on Naval Enigma, demonstrating that the Allies’ policy of pooling their resources was beneficial to their efforts in cryptography (Copeland and Proudfoot). Clark called his machine “the Green Hornet” because the buzzing sound of an enciphered message resembled the theme song of the popular radio show of the 1930s. However, this nickname would eventually be abandoned and the machine would be officially called “SIGSALY,” which was not an acronym, but merely a “cover” name (Weadon). -

Jewel Theatre Audience Guide Addendum: Alan Turing Biography
Jewel Theatre Audience Guide Addendum: Alan Turing Biography directed by Kirsten Brandt by Susan Myer Silton, Dramaturg © 2019 ALAN TURING The outline of the following overview of Turing’s life is largely based on his biography on Alchetron.com (https://alchetron.com/Alan-Turing), a “social encyclopedia” developed by Alchetron Technologies. It has been embellished with additional information from sources such as Andrew Hodges’ books, Alan Turing: The Enigma (1983) and Turing (1997) as well as his website, https://www.turing.org.uk. The following books have also provided additional information: Prof: Alan Turing Decoded (2015) by Dermot Turing, who is Alan’s nephew by way of his only sibling, John; The Turing Guide by B. Jack Copeland, Jonathan Bowen, Mark Sprevak, and Robin Wilson (2017); and Alan M. Turing, written by his mother, Sara, shortly after he died. The latter was republished in 2012 as Alan M. Turing – Centenary Edition with an Afterword entitled “My Brother Alan” by John Turing. The essay was added when it was discovered among John’s writings following his death. The republication also includes a new Foreword by Martin Davis, an American mathematician known for his model of post-Turing machines. Extended biographies of Christopher Morcom, Dillwyn Knox, Joan Clarke (the character of Pat Green in the play) and Sara Turing, which are provided as Addendums to this Guide, provide additional information about Alan. Beginnings Alan Mathison Turing was an English computer scientist, mathematician, logician, cryptanalyst, philosopher and theoretical biologist. He was born in a nursing home in Maida Vale, a tony residential district of London, England on June 23, 1912. -

An Analysis of Factors That Have Influenced the Ve Olution of Information Assurance from World War I Through Vietnam to the Present
Air Force Institute of Technology AFIT Scholar Theses and Dissertations Student Graduate Works 3-17-2004 An Analysis of Factors That Have Influenced the vE olution of Information Assurance from World War I through Vietnam to the Present Kelvin B. Scott Follow this and additional works at: https://scholar.afit.edu/etd Part of the Management Information Systems Commons Recommended Citation Scott, Kelvin B., "An Analysis of Factors That Have Influenced the vE olution of Information Assurance from World War I through Vietnam to the Present" (2004). Theses and Dissertations. 4102. https://scholar.afit.edu/etd/4102 This Thesis is brought to you for free and open access by the Student Graduate Works at AFIT Scholar. It has been accepted for inclusion in Theses and Dissertations by an authorized administrator of AFIT Scholar. For more information, please contact [email protected]. AN ANALYSIS OF FACTORS THAT HAVE INFLUENCED THE EVOLUTION OF INFORMATION ASSURANCE FROM WORLD WAR I THROUGH VIETNAM TO THE PRESENT THESIS Kelvin B. Scott, Gunnery Sergeant, USMC AFIT/GIR/ENV/04M-22 DEPARTMENT OF THE AIR FORCE AIR UNIVERSITY AIR FORCE INSTITUTE OF TECHNOLOGY Wright-Patterson Air Force Base, Ohio APPROVED FOR PUBLIC RELEASE; DISTRIBUTION UNLIMITED The views expressed in this thesis are those of the author and do not reflect the official policy or position of the United States Marine Corps, United States Air Force, Department of Defense, or the United States Government. AFIT/GIR/ENV/04M-22 AN ANALYSIS OF FACTORS THAT HAVE INFLUENCED THE EVOLUTION OF INFORMATION ASSURANCE FROM WORLD WAR I THROUGH VIETNAM TO THE PRESENT THESIS Presented to the Faculty Department of Systems and Engineering Management Graduate School of Engineering and Management Air Force Institute of Technology Air University Air Education and Training Command In Partial Fulfillment of the Requirements for the Degree of Master of Science in Information Resource Management Kelvin B. -
One-To-Cloud One-Time Pad Data Encryption: Introducing Virtual Prototyping with Pspice
Technological University Dublin ARROW@TU Dublin Conference papers School of Electrical and Electronic Engineering 2017-06-20 One-to-Cloud One-Time Pad Data Encryption: Introducing Virtual Prototyping with PSpice Paul Tobin Technological University Dublin, [email protected] Lee Tobin University College Dublin, [email protected] Roberto Gandia Blanquer DR Flowcode, [email protected] See next page for additional authors Follow this and additional works at: https://arrow.tudublin.ie/engscheleart Part of the Computer and Systems Architecture Commons, Data Storage Systems Commons, Digital Circuits Commons, Digital Communications and Networking Commons, Electrical and Computer Engineering Commons, Hardware Systems Commons, and the Other Computer Engineering Commons Recommended Citation Tobin, P. et al. (2017) One-to-Cloud One-Time Pad Data encryption: Introducing Virtual Prototyping with PSpice. ISSC 2017 Institute of Technology, Tralee and Cork Institute of Technology, June 20--21. This Conference Paper is brought to you for free and open access by the School of Electrical and Electronic Engineering at ARROW@TU Dublin. It has been accepted for inclusion in Conference papers by an authorized administrator of ARROW@TU Dublin. For more information, please contact [email protected], [email protected]. This work is licensed under a Creative Commons Attribution-Noncommercial-Share Alike 4.0 License Authors Paul Tobin, Lee Tobin, Roberto Gandia Blanquer DR, Michael McKeever, and Jonathan Blackledge This conference paper is available at ARROW@TU Dublin: https://arrow.tudublin.ie/engscheleart/252 ISSC 2017 Institute of Technology, Tralee and Cork Institute of Technology, June 20{21 One-to-Cloud One-Time Pad Data encryption: Introducing Virtual Prototyping with PSpice P. -

The Origins of Dsp and Compression
__________________________________ Audio Engineering Society Convention Paper 6930 Presented at the 121st Convention 2006 October 5–8 San Francisco, CA, USA This convention paper has been reproduced from the author's advance manuscript, without editing, corrections, or consideration by the Review Board. The AES takes no responsibility for the contents. Additional papers may be obtained by sending request and remittance to Audio Engineering Society, 60 East 42nd Street, New York, New York 10165-2520, USA; also see www.aes.org. All rights reserved. Reproduction of this paper, or any portion thereof, is not permitted without direct permission from the Journal of the Audio Engineering Society. __________________________________ THE ORIGINS OF DSP AND COMPRESSION: Some Pale Gleams From The Past; A Historical Perspective On Early Speech Synthesis And Scramblers, And The Foundations Of Digital Audio Jon D. Paul Vice President, Scientific Conversion, Inc. Curator, Crypto-Museum California, USA [email protected] ABSTRACT This paper explores the history that led to modern day DSP and Audio Compression. The roots of modern digital audio sprang from Dudley's 1928 VOCODER, and the WWII era SIGSALY speech scrambler. We highlight these key inventions, detail their hardware and block diagrams, describe how they functioned, and illustrate their relationship to modern day DSP and compression algorithms. INTRODUCTION Bell Telephone Laboratories’ (BTL) SIGSALY secure communications system marked the invention The origins of modern digital audio can be traced to of a number of techniques that lie at the foundation of this first electronic speech synthesizer in 1928 and to virtually all DSP and signal processing for coding a secure speech scrambler used during WWII. -
The History of Cracking the ENIGMA Machine
From Poznań to Bletchley Park : the history of cracking the ENIGMA machine: Marie-José Durand-Richard1 Philippe Guillot2 INTRODUCTION During World War II, the Allies could read many of the German ciphered messages they intercepted in plain text almost immediately, providing them with an advantage that had a significant impact on the course of the conflict. Movies such as Enigma (1999) and The Imitation Game (2015), highlight the success of the work of the British at Bletchley Park, and particularly the work of the mathematician Alan Madison Turing (1912-1954). But Turing did not work alone on breaking the Enigma code at Bletchley Park, and it is much less well-known that during the 1930s, the Poles had already accomplished the feat of making transparent the enciphered communications between the German army and its General Staff. So, the history of breaking the Enigma code is rather more complicated than is shown in such hagiographic movies. In this perspective, this paper focuses on the various skills at work in cracking the Enigma machine. In the period from 1932 to 1942, both the French and the British considered military intelligence would be more essential than mathematical cryptanalysis in overcoming the problem. However, their political and geographical situation stimulated the Poles to coordinate their technical, mathematical and political capabilities. Cyclometers, Bombas and perforated sheets were produced to help them overcome complications gradually introduced by the German armies in their Enigma ciphering methods. As early as 1936, the British codebreaker A. Dillwyn (Dilly) Knox (1884-1943) started a manual cryptanalysis of the commercial Enigma code at the Government Code and Cipher School (GC&CS) and succeeded in breaking the code of its Spanish and Italian versions in 1937. -
The Center for Cryptologic History Calendar
CCH 2021 THE CENTER FOR CRYPTOLOGIC HISTORY CALENDAR The Autoscritcher was an attempt by the army during World War II to develop an electronic machine to replace the electromechanical bombe in analyzing communications enciphered on the German ENIGMA machine. The Autoscritcher, while a good concept and despite the use of electronic components, was still slower than the bombe. Winter wonderland along Rockenbach Road, 2016. The road leads from the NSA buildings through Fort Meade. Normally, the road is lined with overflow parking spaces for Agency employees. However, in wintertime, it is one of the few convenient dumping sites for snow from the regular parking lots after heavy storms. JANUARY 2021 Sunday Monday Tuesday Wednesday Thursday Friday Saturday 1 2 Lt. Gen. Gordon Blake, USAF, NSA Office of Policy first became DIRNSA, 1962 mandated use of term “Service Cryptologic Element,” 1980 U.S. Army Intelligence and Security Command (INSCOM) established, 1977 New Year’s Day 3 4 5 6 7 8 9 NARA assigned Record Group Major General Gordon Blake Lieutenant (later Captain) Jerzy Rozycki, a Polish Cipher 457 (now “Records of the named Commander, Air Force Laurance Safford named OIC, Bureau mathematician who National Security Agency”) to Security Service, 1957 Navy Cryptographic Branch, helped break ENIGMA, died in a declassified NSA records, 1977 1924 ship sunk off France, 1942 Louis Tordella, longest serving D/DIR (1958-1974), died, 1996 10 11 12 13 14 15 16 First History Today article on NSA BRUSA Agreement–U.S.-UK General Order No. 9 authorized Daily Page, 2003 COMINT relationships during publication of a new War World War II, 1944 Department Telegraphic Code, 1898 Brigadier General Bernard Ardisana, USAF, NSA’s first Operation DESERT STORM Assistant Deputy Director of began, 1991 Operations, died on active duty, 1978 17 18 19 20 21 22 23 Alfred Vail, co-inventor of the Encoded Zimmermann Telegram National Security Decision Intelligence chiefs of U.S.