One Time Pad and the Short Key Dream
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Historical Ciphers • A
ECE 646 - Lecture 6 Required Reading • W. Stallings, Cryptography and Network Security, Chapter 2, Classical Encryption Techniques Historical Ciphers • A. Menezes et al., Handbook of Applied Cryptography, Chapter 7.3 Classical ciphers and historical development Why (not) to study historical ciphers? Secret Writing AGAINST FOR Steganography Cryptography (hidden messages) (encrypted messages) Not similar to Basic components became modern ciphers a part of modern ciphers Under special circumstances modern ciphers can be Substitution Transposition Long abandoned Ciphers reduced to historical ciphers Transformations (change the order Influence on world events of letters) Codes Substitution The only ciphers you Ciphers can break! (replace words) (replace letters) Selected world events affected by cryptology Mary, Queen of Scots 1586 - trial of Mary Queen of Scots - substitution cipher • Scottish Queen, a cousin of Elisabeth I of England • Forced to flee Scotland by uprising against 1917 - Zimmermann telegram, America enters World War I her and her husband • Treated as a candidate to the throne of England by many British Catholics unhappy about 1939-1945 Battle of England, Battle of Atlantic, D-day - a reign of Elisabeth I, a Protestant ENIGMA machine cipher • Imprisoned by Elisabeth for 19 years • Involved in several plots to assassinate Elisabeth 1944 – world’s first computer, Colossus - • Put on trial for treason by a court of about German Lorenz machine cipher 40 noblemen, including Catholics, after being implicated in the Babington Plot by her own 1950s – operation Venona – breaking ciphers of soviet spies letters sent from prison to her co-conspirators stealing secrets of the U.S. atomic bomb in the encrypted form – one-time pad 1 Mary, Queen of Scots – cont. -

Polish Mathematicians Finding Patterns in Enigma Messages
Fall 2006 Chris Christensen MAT/CSC 483 Machine Ciphers Polyalphabetic ciphers are good ways to destroy the usefulness of frequency analysis. Implementation can be a problem, however. The key to a polyalphabetic cipher specifies the order of the ciphers that will be used during encryption. Ideally there would be as many ciphers as there are letters in the plaintext message and the ordering of the ciphers would be random – an one-time pad. More commonly, some rotation among a small number of ciphers is prescribed. But, rotating among a small number of ciphers leads to a period, which a cryptanalyst can exploit. Rotating among a “large” number of ciphers might work, but that is hard to do by hand – there is a high probability of encryption errors. Maybe, a machine. During World War II, all the Allied and Axis countries used machine ciphers. The United States had SIGABA, Britain had TypeX, Japan had “Purple,” and Germany (and Italy) had Enigma. SIGABA http://en.wikipedia.org/wiki/SIGABA 1 A TypeX machine at Bletchley Park. 2 From the 1920s until the 1970s, cryptology was dominated by machine ciphers. What the machine ciphers typically did was provide a mechanical way to rotate among a large number of ciphers. The rotation was not random, but the large number of ciphers that were available could prevent depth from occurring within messages and (if the machines were used properly) among messages. We will examine Enigma, which was broken by Polish mathematicians in the 1930s and by the British during World War II. The Japanese Purple machine, which was used to transmit diplomatic messages, was broken by William Friedman’s cryptanalysts. -

The the Enigma Enigma Machinemachine
TheThe EnigmaEnigma MachineMachine History of Computing December 6, 2006 Mike Koss Invention of Enigma ! Invented by Arthur Scherbius, 1918 ! Adopted by German Navy, 1926 ! Modified military version, 1930 ! Two Additional rotors added, 1938 How Enigma Works Scrambling Letters ! Each letter on the keyboard is connected to a lamp letter that depends on the wiring and position of the rotors in the machine. ! Right rotor turns before each letter. How to Use an Enigma ! Daily Setup – Secret settings distributed in code books. ! Encoding/Decoding a Message Setup: Select (3) Rotors ! We’ll use I-II-III Setup: Rotor Ring Settings ! We’ll use A-A-A (or 1-1-1). Rotor Construction Setup: Plugboard Settings ! We won’t use any for our example (6 to 10 plugs were typical). Setup: Initial Rotor Position ! We’ll use “M-I-T” (or 13-9-20). Encoding: Pick a “Message Key” ! Select a 3-letter key (or indicator) “at random” (left to the operator) for this message only. ! Say, I choose “M-C-K” (or 13-3-11 if wheels are printed with numbers rather than letters). Encoding: Transmit the Indicator ! Germans would transmit the indicator by encoding it using the initial (daily) rotor position…and they sent it TWICE to make sure it was received properly. ! E.g., I would begin my message with “MCK MCK”. ! Encoded with the daily setting, this becomes: “NWD SHE”. Encoding: Reset Rotors ! Now set our rotors do our chosen message key “M-C-K” (13-3-11). ! Type body of message: “ENIGMA REVEALED” encodes to “QMJIDO MZWZJFJR”. -

Original Paper Written & Signed by William F
/ I / I p. I I _., • CRYPTOGRAPHIC EQUIP~lliNT FOR EITHER -SINGLE-ORIGINATOR OR MULTI-ORIGINATOR COMMUNICATION 1. a. Progress in the cryptologic field-during the.past fevT yea.,:s has .led to a basic change in cryptologic philosophy, a change Which has already oeen recognized by and is of im., portant interest to the ASA. b. The t1~ust vrhich 'has heretofore been placed in the ordinary types of crypto-systems, the solution of which depends upon, or is directly or indirectly correlated with, the number of tests that have to be made to exhaust a multiplicity of , / hypotheses based upon keying possibilities, is daily decreasing. The beginning of this decreasing confidence i~ the degree of cryptographic security potentially offered by a vast number of permutations and combinations available of keying possibilities can be traced back to the advent of the application of ~abu~ lating machinery to the solution of cryptanalytic problems. _ Later, when specially designed cryptanalytic machines employ- ing electrical relays came to be constructed and applied, success fully to these problems, a real blow was struck at our former concepts of cryptographi·c security. And, now, the assurance that electronic cryptanalytic machinery can be a·pplied to ~?Peed up the solution 9f complex cryptographic systems is tend ing· slm1ly to undermine what faith was left in the systems or crypto-mechanisms currently considered as being the best there are, those using rotors with complicated stepping controls .. , ·· . c.- To sum this up, it can be said that, save for orie exception, cryptologic theory and practice during the past 'quar,ter of a c~ntury serves only to corroborat.E? the theoretical validity of·the century-old dictum first enunciated by Edgar Allan Poe: "Yet it may be r·oundly asserted that ht1.man ingenuity cannot concoct a cipher which human ingenuity cannot solve.11 2. -

(U) a History of Secure Voice Codin~: Insights Drawn from the Career of One of Tile Earliest Practitioners of the Art of Speech Coding JOSEPH P
DOCID: 3860926 UNCLASSIFIED Cryptologic Quarter1y (U) A History of Secure Voice Codin~: Insights Drawn from the Career of One of tile Earliest Practitioners of the Art of Speech Coding JOSEPH P. CAMPBELL, JR., and RICHARD A. DEAN Editor's Note: This artrde Is basecl on one publlshecl In Dlgittl Signal Processing, July 1993, wfth permission ofthe authors. The history of speech coding is closely tied to tion of PCM. A "Buzz" /"Hiss" generator was used the career of Tom Tremain. He joined the as an exciter for the vocoder corresponding to the National Security Agency i~ 1959 as an Air Force voiced/unvoiced attribute of each 20-ms speech lieutenant assigned to duty at the Agency. Llttle segment. Balance of the "Buzz" /"Hiss" generator, did he know then that this assignment would or voicing, represented a major factor in the qual shape his career as well as' the future of speech ity of the speech. Early practitioners of speech coding. 1 coders, like Tom, can still be found today speak I . ing"Aaahhh" /"Sshhhhh" into voice coders to test Thomas E. Tremain was the U.S. govern- this balance. ment's senior speech scientist. He was a recog nized leader and an expert in speech science. From the time of SIGSALY until Tom arrived 1 Tom's work spanned five dife3des of state-of-the- at NSA, several generations of voice coders had art modem and speech co<;Iing innovations that been developed in conjunction with Bell Labs. are the basis of virtually e~ery U.S. and NATO The K0-6 voice coder, developed in 1949 and modem and speech coding standard. -

The First Devices to Secure Transmission of Voice Were Developed Just After World War I
F, 5 January Cabinet War Rooms SIGSALY The first devices to secure transmission of voice were developed just after World War I. They were substitution devices; they inverted frequencies. High frequencies were substituted for low frequencies and low frequencies were substituted for high frequencies. This was easy to do electronically. But, it was also easy to break. In fact, because much voice is in the middle frequencies and the middle frequencies are not changed much by inversion, it was sometimes possible to get a sense of the message just from the ciphertext. The A-3 scrambler … was based upon 1920s concepts. It divided the voice-frequency band into five subbands, inverted each of them, and then shifted the voice from one subband to another every 20 seconds. David Kahn Cryptology and the origin of spread spectrum In 1941, the United States was not at war although we were supporting the Allies, especially Britain, materially. The United States had a device to secure voice transmission called the A-3 Scrambler. This device used both substitution and transposition to encipher voice. Messages were chopped into small pieces, in each piece substitution was made by inverting frequencies, and the pieces were scrambled. This device was broken by the Germans during Fall 1941. The United States military was aware that the A-3 was not secure. On December 7, 1941, cryptanalysts in Washington, D.C., were in the process of breaking a long ciphertext from Tokyo to the Japanese embassy in Washington, D.C. William Friedman’s SIS team had earlier broken the Japanese diplomatic ciphers, but the naval ciphers had not yet been broken. -

The Mathematics of the Enigma Machine Student: Emily Yale Supervisor: Dr Tariq Jarad
The Mathematics of the Enigma Machine Student: Emily Yale Supervisor: Dr Tariq Jarad The Enigma Machine is a mechanical encryption device used mainly by the German Forces during WWII to turn plaintext into complex ciphertext, the same machine could be used to do the reverse (Trappe and Washington, 2006). Invented by the German engineer Arthur Scherbius at the end of World War I the cipher it produced was marketed as ‘unbreakable’ (Trappe and Washington, 2006). Adopted by the German military forces, it worked by layering a number of substitution ciphers that were decided by an excess of 1.589x1021 machine settings. With help from Polish and French mathematicians, the cryptographer named Alan Turing created a machine known as the ‘Bombe’ which helped to reduce the time taken to ‘break’ an Enigma cipher (Imperial War Museums, 2015). The report this poster is based on focuses on the mathematics of the Enigma machine as well as the methods used to find the settings for a piece of ciphertext. Advantages and disadvantages of the Enigma code will be explored, alternative cipher machines are considered. Aims and Objective Bombe (Group Theory) • A brief insight into Cryptography The Bombe was a machine that could be used to find the key to an • The history of the Enigma Machine Enigma cipher. It was modelled on the Polish machine, Bomba, which • The mechanism of the Enigma Machine could also do same before Enigma was enhanced. Bombe could find the • The mathematics of the Bombe settings on an Enigma machine that had been used to encrypt a • Understanding Group Theory ciphertext. -

TICOM: the Last Great Secret of World War II Randy Rezabek Version of Record First Published: 27 Jul 2012
This article was downloaded by: [Randy Rezabek] On: 28 July 2012, At: 18:04 Publisher: Routledge Informa Ltd Registered in England and Wales Registered Number: 1072954 Registered office: Mortimer House, 37-41 Mortimer Street, London W1T 3JH, UK Intelligence and National Security Publication details, including instructions for authors and subscription information: http://www.tandfonline.com/loi/fint20 TICOM: The Last Great Secret of World War II Randy Rezabek Version of record first published: 27 Jul 2012 To cite this article: Randy Rezabek (2012): TICOM: The Last Great Secret of World War II, Intelligence and National Security, 27:4, 513-530 To link to this article: http://dx.doi.org/10.1080/02684527.2012.688305 PLEASE SCROLL DOWN FOR ARTICLE Full terms and conditions of use: http://www.tandfonline.com/page/terms-and- conditions This article may be used for research, teaching, and private study purposes. Any substantial or systematic reproduction, redistribution, reselling, loan, sub-licensing, systematic supply, or distribution in any form to anyone is expressly forbidden. The publisher does not give any warranty express or implied or make any representation that the contents will be complete or accurate or up to date. The accuracy of any instructions, formulae, and drug doses should be independently verified with primary sources. The publisher shall not be liable for any loss, actions, claims, proceedings, demand, or costs or damages whatsoever or howsoever caused arising directly or indirectly in connection with or arising out of the use of this material. Intelligence and National Security Vol. 27, No. 4, 513–530, August 2012 TICOM: The Last Great Secret of World War II RANDY REZABEK* ABSTRACT Recent releases from the National Security Agency reveal details of TICOM, the mysterious 1945 operation targeting Germany’s cryptologic secrets. -

Gendering Decryption - Decrypting Gender
1 Gendering decryption - decrypting gender The gender discourse of labour at Bletchley Park 1939-1945 Photograph taken from Smith 2011. Spring 2013 MA thesis (30 hp) Author: Annie Burman Supervisor: Mikael Byström Seminar leader: Torkel Jansson Date of seminar: 4 June 2013 2 Abstract Ever since the British efforts to break Axis codes and ciphers during the Second World War were declassified in the 1970s, the subject of Government Code and Cipher School, the organisation responsible, Bletchley Park, its wartime headquarters, and the impact of the intelligence on the war has fascinated both historians and the general public. However, little attention has been paid to Bletchley Park as a war station where three-quarters of the personnel was female. The purpose of this thesis is to explore the gender discourse of labour at Bletchley Park and how it relates to the wider context of wartime Britain. This is done through the theoretical concepts of gendering (the assignation of a gender to a job, task or object), horizontal gender segregation (the custom of assigning men and women different jobs) and vertical gender segregation (the state where men hold more prestigious positions in the hierarchy than women). The primary sources are interviews, letters and memoirs by female veterans of Bletchley Park, kept in Bletchley Park Trust Archive and the Imperial War Museum’s collections, and printed accounts, in total two monographs and five articles. Surviving official documents from Bletchley Park, now kept in the National Archives, are also utilised. Using accounts created by female veterans themselves as the main source material allows for women’s perspectives to be acknowledged and examined. -

A Complete Bibliography of Publications in Cryptologia
A Complete Bibliography of Publications in Cryptologia Nelson H. F. Beebe University of Utah Department of Mathematics, 110 LCB 155 S 1400 E RM 233 Salt Lake City, UT 84112-0090 USA Tel: +1 801 581 5254 FAX: +1 801 581 4148 E-mail: [email protected], [email protected], [email protected] (Internet) WWW URL: http://www.math.utah.edu/~beebe/ 04 September 2021 Version 3.64 Title word cross-reference 10016-8810 [?, ?]. 1221 [?]. 125 [?]. 15.00/$23.60.0 [?]. 15th [?, ?]. 16th [?]. 17-18 [?]. 18 [?]. 180-4 [?]. 1812 [?]. 18th (t; m)[?]. (t; n)[?, ?]. $10.00 [?]. $12.00 [?, ?, ?, ?, ?]. 18th-Century [?]. 1930s [?]. [?]. 128 [?]. $139.99 [?]. $15.00 [?]. $16.95 1939 [?]. 1940 [?, ?]. 1940s [?]. 1941 [?]. [?]. $16.96 [?]. $18.95 [?]. $24.00 [?]. 1942 [?]. 1943 [?]. 1945 [?, ?, ?, ?, ?]. $24.00/$34 [?]. $24.95 [?, ?]. $26.95 [?]. 1946 [?, ?]. 1950s [?]. 1970s [?]. 1980s [?]. $29.95 [?]. $30.95 [?]. $39 [?]. $43.39 [?]. 1989 [?]. 19th [?, ?]. $45.00 [?]. $5.95 [?]. $54.00 [?]. $54.95 [?]. $54.99 [?]. $6.50 [?]. $6.95 [?]. $69.00 2 [?, ?]. 200/220 [?]. 2000 [?]. 2004 [?, ?]. [?]. $69.95 [?]. $75.00 [?]. $89.95 [?]. th 2008 [?]. 2009 [?]. 2011 [?]. 2013 [?, ?]. [?]. A [?]. A3 [?, ?]. χ [?]. H [?]. k [?, ?]. M 2014 [?]. 2017 [?]. 2019 [?]. 20755-6886 [?, ?]. M 3 [?]. n [?, ?, ?]. [?]. 209 [?, ?, ?, ?, ?, ?]. 20th [?]. 21 [?]. 22 [?]. 220 [?]. 24-Hour [?, ?, ?]. 25 [?, ?]. -Bit [?]. -out-of- [?, ?]. -tests [?]. 25.00/$39.30 [?]. 25.00/839.30 [?]. 25A1 [?]. 25B [?]. 26 [?, ?]. 28147 [?]. 28147-89 000 [?]. 01Q [?, ?]. [?]. 285 [?]. 294 [?]. 2in [?, ?]. 2nd [?, ?, ?, ?]. 1 [?, ?, ?, ?]. 1-4398-1763-4 [?]. 1/2in [?, ?]. 10 [?]. 100 [?]. 10011-4211 [?]. 3 [?, ?, ?, ?]. 3/4in [?, ?]. 30 [?]. 310 1 2 [?, ?, ?, ?, ?, ?, ?]. 312 [?]. 325 [?]. 3336 [?, ?, ?, ?, ?, ?]. affine [?]. [?]. 35 [?]. 36 [?]. 3rd [?]. Afluisterstation [?, ?]. After [?]. Aftermath [?]. Again [?, ?]. Against 4 [?]. 40 [?]. 44 [?]. 45 [?]. 45th [?]. 47 [?]. [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. Age 4in [?, ?]. [?, ?]. Agencies [?]. Agency [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. -
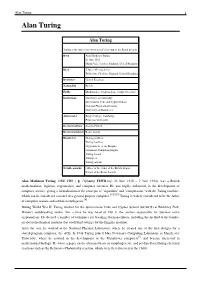
Alan Turing 1 Alan Turing
Alan Turing 1 Alan Turing Alan Turing Turing at the time of his election to Fellowship of the Royal Society. Born Alan Mathison Turing 23 June 1912 Maida Vale, London, England, United Kingdom Died 7 June 1954 (aged 41) Wilmslow, Cheshire, England, United Kingdom Residence United Kingdom Nationality British Fields Mathematics, Cryptanalysis, Computer science Institutions University of Cambridge Government Code and Cypher School National Physical Laboratory University of Manchester Alma mater King's College, Cambridge Princeton University Doctoral advisor Alonzo Church Doctoral students Robin Gandy Known for Halting problem Turing machine Cryptanalysis of the Enigma Automatic Computing Engine Turing Award Turing test Turing patterns Notable awards Officer of the Order of the British Empire Fellow of the Royal Society Alan Mathison Turing, OBE, FRS ( /ˈtjʊərɪŋ/ TEWR-ing; 23 June 1912 – 7 June 1954), was a British mathematician, logician, cryptanalyst, and computer scientist. He was highly influential in the development of computer science, giving a formalisation of the concepts of "algorithm" and "computation" with the Turing machine, which can be considered a model of a general purpose computer.[1][2][3] Turing is widely considered to be the father of computer science and artificial intelligence.[4] During World War II, Turing worked for the Government Code and Cypher School (GC&CS) at Bletchley Park, Britain's codebreaking centre. For a time he was head of Hut 8, the section responsible for German naval cryptanalysis. He devised a number of techniques for breaking German ciphers, including the method of the bombe, an electromechanical machine that could find settings for the Enigma machine. -

Breaking Enigma Samantha Briasco-Stewart, Kathryn Hendrickson, and Jeremy Wright
Breaking Enigma Samantha Briasco-Stewart, Kathryn Hendrickson, and Jeremy Wright 1 Introduction 2 2 The Enigma Machine 2 2.1 Encryption and Decryption Process 3 2.2 Enigma Weaknesses 4 2.2.1 Encrypting the Key Twice 4 2.2.2 Cillies 5 2.2.3 The Enigma Machine Itself 5 3 Zygalski Sheets 6 3.1 Using Zygalski Sheets 6 3.2 Programmatic Replication 7 3.3 Weaknesses/Problems 7 4 The Bombe 8 4.1 The Bombe In Code 10 4.1.1 Making Menus 10 4.1.2 Running Menus through the Bombe 10 4.1.3 Checking Stops 11 4.1.4 Creating Messages 11 4.1.5 Automating the Process 11 5 Conclusion 13 References 14 1 Introduction To keep radio communications secure during World War II, forces on both sides of the war relied on encryption. The main encryption scheme used by the German military for most of World War II employed the use of an Enigma machine. As such, Britain employed a large number of codebreakers and analysts to work towards breaking the Enigma-created codes, using many different methods. In this paper, we lay out information we learned while researching these methods, as well as describe our attempts at programatically recreating two methods: Zygalski sheets and the Bombe. 2 The Enigma Machine The Enigma machine was invented at the end of World War I, by a German engineer named Arthur Scherbius. It was commercially available in the 1920s before being adopted by the German military, among others, around the beginning of World War II.