(U) a History of Secure Voice Codin~: Insights Drawn from the Career of One of Tile Earliest Practitioners of the Art of Speech Coding JOSEPH P
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Corp Bro Inside Layout
Message from the Director, NSA The National Security Agency’s rich legacy of cryptologic success serves not only as a reminder of our past triumphs, but also as an inspiration for our future. Harry Truman, the man responsible for signing the legislation that brought our Agency into existence, was once quoted as saying, “There is nothing new in the world except the history you do not know.” Like all truisms, it is only partially accurate. Each generation of Americans must at some point deal with unforeseen problems and issues that transcend the status quo. Most would agree that the challenges faced by NSA in today’s war against terrorism are far different from those of World War II, Vietnam, or Desert Storm. Even so, President Truman was correct in his assertion that there is much to be learned from the past. The history of the National Security Agency has in many respects been based on and characterized by feats of intellectual brilliance. Pioneers like William Friedman, Frank Rowlett, Dr. Louis Tordella, and Agnes Meyer Driscoll, to name but a few, were able to build on past successes and do whatever was necessary to meet the challenges of their time. We should not forget, however, that NSA’s success is due not just to the efforts of the well- known legends of the cryptologic past, but also to the dedicated work of thousands of men and women whose names will never be noted in any history book. History tells us that both genius and hard work are required to ensure success. -

Using PSTN Encryption HC-2203 Over BGAN Version 1 3 September 2009
Using PSTN Encryption HC-2203 over BGAN Version 1 3 September 2009 inmarsat.com/bgan Whilst the information has been prepared by Inmarsat in good faith, and all reasonable efforts have been made to ensure its accuracy, Inmarsat makes no warranty or representation as to the accuracy, completeness or fitness for purpose or use of the information. Inmarsat shall not be liable for any loss or damage of any kind, including indirect or consequential loss, arising from use of the information and all warranties and conditions, whether express or implied by statute, common law or otherwise, are hereby excluded to the extent permitted by English law. INMARSAT is a trademark of the International Mobile Satellite Organisation, Inmarsat LOGO is a trademark of Inmarsat (IP) Company Limited. Both trademarks are licensed to Inmarsat Global Limited. © Inmarsat Global Limited 2009. All rights reserved. Contents 1 Overview 1 1.1 PSTN encryption explained 1 2 Typical users 1 3 Key features 1 4 Benefits to BGAN users 1 5 Setting up 1 5.1 Setting up HC-2203 PSTN Encryption 1 5.2 About your BGAN SIM card subscription 1 5.3 Setting up the EXPLORER 500/527 and EXPLORER 700 1 5.4 Setting up the Hughes 9201 or Hughes 9250 terminal 1 6 Technical specifications 1 7 General data 1 8 Further details and support 1 1 Overview Inmarsat BGAN offers the same telephony services as its predecessor system GAN, namely Standard Voice (compressed), ISDN Data and the Audio 3.1kHz service which can be used for fax and data communication. -

Original Paper Written & Signed by William F
/ I / I p. I I _., • CRYPTOGRAPHIC EQUIP~lliNT FOR EITHER -SINGLE-ORIGINATOR OR MULTI-ORIGINATOR COMMUNICATION 1. a. Progress in the cryptologic field-during the.past fevT yea.,:s has .led to a basic change in cryptologic philosophy, a change Which has already oeen recognized by and is of im., portant interest to the ASA. b. The t1~ust vrhich 'has heretofore been placed in the ordinary types of crypto-systems, the solution of which depends upon, or is directly or indirectly correlated with, the number of tests that have to be made to exhaust a multiplicity of , / hypotheses based upon keying possibilities, is daily decreasing. The beginning of this decreasing confidence i~ the degree of cryptographic security potentially offered by a vast number of permutations and combinations available of keying possibilities can be traced back to the advent of the application of ~abu~ lating machinery to the solution of cryptanalytic problems. _ Later, when specially designed cryptanalytic machines employ- ing electrical relays came to be constructed and applied, success fully to these problems, a real blow was struck at our former concepts of cryptographi·c security. And, now, the assurance that electronic cryptanalytic machinery can be a·pplied to ~?Peed up the solution 9f complex cryptographic systems is tend ing· slm1ly to undermine what faith was left in the systems or crypto-mechanisms currently considered as being the best there are, those using rotors with complicated stepping controls .. , ·· . c.- To sum this up, it can be said that, save for orie exception, cryptologic theory and practice during the past 'quar,ter of a c~ntury serves only to corroborat.E? the theoretical validity of·the century-old dictum first enunciated by Edgar Allan Poe: "Yet it may be r·oundly asserted that ht1.man ingenuity cannot concoct a cipher which human ingenuity cannot solve.11 2. -

Encryption of Voice, Data and Video (Vdv) for Secure Terrestrial and Satellite Communications
Dimov Stojce Ilcev / International Journal of New Technologies in Science and Engineering Vol. 2, Issue. 4,October 2015, ISSN 2349-0780 ENCRYPTION OF VOICE, DATA AND VIDEO (VDV) FOR SECURE TERRESTRIAL AND SATELLITE COMMUNICATIONS Stojce Dimov Ilcev Durban University of Technology (DUT), 133 Bencorrum, 183 Prince Street, Durban, South Africa Abstract: This paper introduces the Voice, Data and Video (VDV) encryption as protection shield for secure terrestrial and satellite communication systems deploying special hardware and software scrambling solutions against government or private surveillance and spying. The encryption covers fixed, personal and mobile (cellular) solutions including computer, fax and telex messaging modes for commercial and military applications. Keywords: Encryption, VDV/NSA, DES/AES, RSA/IBE I. INTRODUCTION Secure communication is when two entities are communicating and do not want a third party to listen in or to communicate in a way not susceptible to eavesdropping or interception. It includes means by which people can share mutual information with varying degrees of certainty that third parties cannot intercept what was said, heard, sent and saw. Other than spoken face-to-face communication with no possible eavesdropper, it is probably safe to say that no communication is guaranteed secure in this sense, although practical obstacles such as legislation, resources, technical issues (interception and encryption), and the sheer volume of communication serve to limit surveillance. In cryptography, encryption is the process of encoding voice (speech and fax), data (messages or text) and video (TV, videoconference and images) in such a way that only authorized parties can listen, read or see it properly. Encryption does not of itself prevent interception, but denies the speech, message and image content to the interceptor. -

Model 90Si Secure Fax Gateway User's Guide
Model 90si Secure Fax Gateway User's Guide GateWay Fax Systems, Inc. Secure Fax Products Virginia, USA Tel: 804-796-1900 Toll-Free: 877-951-9800 Fax: 804-796-1116 E-Mail: [email protected] Web: www.gwfs.com Help Line: 877-951-9814 Revision 4.7 3/27/2013 GateWay Fax Systems, inc. Model 90si Secure Fax Gateway User's Guide 90si Quick Reference Guide Your 90si comes from the factory set for the Secure Only mode, whereby the commercial (COTS) fax connects to the 90si’s FAX jack (the other two phone jacks remain empty) and the 90si’s RS-232 Data cable connects to the Secure Data port of your crypto device. In this configuration the COTS fax can only be used for classified transac- tions with the crypto in Secure Data Mode. Connecting the COTS fax, 90si and Crypto This diagram shows the default (and recommended) factory configuration for the 90si. Shown are the rear panel of the 90si, Secure Telephone, Commercial-Off-The-Shelf (COTS) fax and the outside telepone line connection. Although there are other 90si configurations, this one will work right out of the box. See Section 2.3, Choose a Configuration, for others. 90si Secure Fax Gateway Rear Panel FAX Commercial-Off-The-Shelf Fax Machine 5VDC Power LINE (Set to Auto-Answer on 1 Ring) Supply "Red" Data Port "Secure" Secure Telephone PSTN Phone Line / Crypto (Set to Async 9.6kbps) Telephone Wall Jack Transmitting a Secure Fax Step Procedure 1. Place a call on your secure telephone / crypto. 2. Place it in secure data mode and set the handset on the table 3. -

The First Devices to Secure Transmission of Voice Were Developed Just After World War I
F, 5 January Cabinet War Rooms SIGSALY The first devices to secure transmission of voice were developed just after World War I. They were substitution devices; they inverted frequencies. High frequencies were substituted for low frequencies and low frequencies were substituted for high frequencies. This was easy to do electronically. But, it was also easy to break. In fact, because much voice is in the middle frequencies and the middle frequencies are not changed much by inversion, it was sometimes possible to get a sense of the message just from the ciphertext. The A-3 scrambler … was based upon 1920s concepts. It divided the voice-frequency band into five subbands, inverted each of them, and then shifted the voice from one subband to another every 20 seconds. David Kahn Cryptology and the origin of spread spectrum In 1941, the United States was not at war although we were supporting the Allies, especially Britain, materially. The United States had a device to secure voice transmission called the A-3 Scrambler. This device used both substitution and transposition to encipher voice. Messages were chopped into small pieces, in each piece substitution was made by inverting frequencies, and the pieces were scrambled. This device was broken by the Germans during Fall 1941. The United States military was aware that the A-3 was not secure. On December 7, 1941, cryptanalysts in Washington, D.C., were in the process of breaking a long ciphertext from Tokyo to the Japanese embassy in Washington, D.C. William Friedman’s SIS team had earlier broken the Japanese diplomatic ciphers, but the naval ciphers had not yet been broken. -

NSIAD-86-7 Concerns Regarding the National Security Agency Secure Telephone Program
1 II UNITED STATES GENE& ACCGWT~NGOFFICE WASHINGTON, D.C. 2Q548 NATIONAL SECURITY AND IMIERNATIONAL AFFAlRS DlVlS1ON OCf 15 1985 IIIll IIll,ll~~ B-220762 128229 The Honorable Glenn English Chairman, Subcommittee on Government Information, Justice, and Agriculture ' Committee on Government Operations House of Representatives Dear Mr. Chairman: Subject: Concerns Regarding the National Security Agency Secure Telephone Program (GAO/NSIAD-86-7) On September 24, 1984, you requested that we evaluate the use of TEMPEST and similar technologies--such as secure telephones-- for the protection of national security information. As requested by your office on July 26, 1985, this letter identifies the major issues regarding secure telephones that we have identified to date. The STU-II is the secure telephone in use today. These telephones are to be replaced by lower cost STU-III telephones. Development contracts for the STU-III telephones were awarded 'in March 1985 to AT&T, Motorola, and RCA to develop an easy to use, low cost (target price about $2,000) secure telephone, deliverable by early 1987. Current plans are to award production contracts to all three contractors (if they successfully develop a product) in March 1986, with deliveries to begin in April 1987. The number of units awarded to each contractor will depend on their price and degree of success in performance tests. A contract has also been awarded to GTE Sylvania for systems integration and testing. The total cost to the government for this developmental effort is about $82 million. This program is very unique because, in addition to having applicability to national security information, this secure telephone will also have a commercial market, that is, banks, brokerage firms, and other businesses interested in securing (395037) B-220762 their communications. -

TCC-Encryption.Pdf
GLOBAL SECURE COMMUNICATIONS EXPERTISE For more than 50 years, TCC has specialized in designing, With our solid reputation, TCC has established many long- manufacturing, marketing and supporting superior-grade term relationships around the globe, while our large base of secure communications systems and customized solutions international representatives, direct sales force, and technical that protect highly sensitive voice, data and video information field staff give each customer personalized service and support. transmitted over a wide range of networks. Communications With a commitment to excellence, TCC has been ISO 9001 security is an essential part of a cybersecurity strategy. certified since 1995 for its stringent company-wide quality TCC’s solutions are optimized for cryptographic strength, management system and processes. Today, government performance and ease of use, supporting our CipherONE® entities, military agencies and corporate enterprises in over Optimized Network Encryption best-in-class criteria. 115 countries have selected TCC to protect their mission- critical communications. UNIVERSAL RADIO ENCRYPTION AND SECURE VOICE CONFERENCING TCC’s DSP 9000 military radio encryption systems, and on existing voice networks — no infrastructure changes are the HSE 6000 squad radio headset and telephone encryptor required. Our best-in-class systems deliver strong communi- for public safety special operations are interoperable systems cations security while maintaining excellent voice quality and providing end-to-end secure communications for air, land, crypto-synchronization even in the harshest field and network sea and office. Additionally, with X-NCrypt™ Cross Network environments. Our products are also easy to use, deploy and Cryptography, TCC’s solution enables multiparty secure voice manage. conferencing across and between radio and telephone networks. -

TICOM: the Last Great Secret of World War II Randy Rezabek Version of Record First Published: 27 Jul 2012
This article was downloaded by: [Randy Rezabek] On: 28 July 2012, At: 18:04 Publisher: Routledge Informa Ltd Registered in England and Wales Registered Number: 1072954 Registered office: Mortimer House, 37-41 Mortimer Street, London W1T 3JH, UK Intelligence and National Security Publication details, including instructions for authors and subscription information: http://www.tandfonline.com/loi/fint20 TICOM: The Last Great Secret of World War II Randy Rezabek Version of record first published: 27 Jul 2012 To cite this article: Randy Rezabek (2012): TICOM: The Last Great Secret of World War II, Intelligence and National Security, 27:4, 513-530 To link to this article: http://dx.doi.org/10.1080/02684527.2012.688305 PLEASE SCROLL DOWN FOR ARTICLE Full terms and conditions of use: http://www.tandfonline.com/page/terms-and- conditions This article may be used for research, teaching, and private study purposes. Any substantial or systematic reproduction, redistribution, reselling, loan, sub-licensing, systematic supply, or distribution in any form to anyone is expressly forbidden. The publisher does not give any warranty express or implied or make any representation that the contents will be complete or accurate or up to date. The accuracy of any instructions, formulae, and drug doses should be independently verified with primary sources. The publisher shall not be liable for any loss, actions, claims, proceedings, demand, or costs or damages whatsoever or howsoever caused arising directly or indirectly in connection with or arising out of the use of this material. Intelligence and National Security Vol. 27, No. 4, 513–530, August 2012 TICOM: The Last Great Secret of World War II RANDY REZABEK* ABSTRACT Recent releases from the National Security Agency reveal details of TICOM, the mysterious 1945 operation targeting Germany’s cryptologic secrets. -

Brent 2 Secure Telephone
>Professional Communications >Telecom Operators >Avionics CNI >Military & Space BRENT 2 SECURE TELEPHONE BRENT 2 is a secure ISDN (Integrated Services Digital Network) telephone, which protects voice and data up to and including TOP SECRET and all UK caveats. It is an upgrade to the current BRENT and meets requirements for both secure and non-secure telephony. BRENT 2 has been designed to operate over EURO ISDN (CCITT I.420) and connects directly to the public ISDN, or to Private Branch Exchanges (PBXs) with I.420 connection. FEATURES > Dial-through operation via the new RED ISDN S0 bus using both 64 kbit/s channels independently > BRENT and BRENT 2 are totally interoperable > BRENT 2 offers all the features of the original BRENT, but > ETSI EURO ISDN (BT ISDN2e) BRI compliant with the addition of a RED S0 bus, providing transparent > DTMF signalling connection to EURO ISDN. This allows independent dial > BRENT 2 meets NATO TEMPEST through operation for each of the two ISDN channels standard AMSG 720 and has been evaluated by SECAN > The RED S0 bus can be used to provide transparent and approved by the Military Committee for the processing secure dial-up connectivity between LANs. (figure 1, of NATO information of all classifications overleaf) > Operation of BRENT 2 in the UK or approved countries is BRENT 2’s user-friendly operation allows secure calls to be enabled using a UK or National established automatically when a Secure Telephone Key (STK) > User Group Secure Telephone Key (STK) is inserted in each telephone. The unique user STK provides > BRENT 2 uses the Supplementary Services of ISDN to secure call authentication and ensures low key management enable, for example, the interconnection of several data overhead. -

Brent 2 Secure Telephone Designed by CESG Is Launched
SECURITY FEATURES TECHNICAL FEATURES • Self-synchronising cryptographic algorithm • ISDN interface to public and private BRENT 2 Secure Telephone developed and approved by CESG networks via basic access standard • Crypto and key management features ETSI I.420 proprietary to HMG • EURO ISDN & BT ISDN2e compliant • Unique encryption variables generated • RED ISDN S0 bus automatically between phones for each • RED data port interface to X.21 at 64 call kbit/s (independent of voice channel) • UK and National User Group STKs • External 115/230V AC mains power supply • STK User Groups of unlimited size can be unit (standard) requested • Erasure of all crypto data on removal of APPROVALS STK • CESG certified for protectively marked • With the STK removed, the unit is not traffic of the highest levels with all caveats protectively marked, but is treated as a • TEMPEST approved to AMSG 720B and valuable item and must be accounted for to BTR/01/202(4) • Call Bypass Monitor • BABT, EMC and safety tested and • Tamper resistant construction approved for use in benign office environments BRENT 2 is a CESG-designed secure ISDN (Integrated Services Digital Network) telephone which protects voice and data up to TOP 1 SECRET and all UK caveats. It is an upgrade 0 0 to the current BRENT and meets requirements for both secure and non-secure telephony. 0 1 1 Communication 0 Encryption For information on procurement of BRENT 2, please contact: For more information on any aspect of CESG’s work, please contact: 0 Marconi Secure Systems Ltd 2 Wavertree Boulevard Customer Support Office 1 Wavertree Technology Park Communications-Electronics Security Group 1 Liverpool PO Box 144 0 0 L7 9PE Cheltenham. -
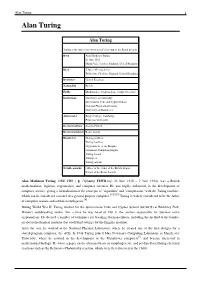
Alan Turing 1 Alan Turing
Alan Turing 1 Alan Turing Alan Turing Turing at the time of his election to Fellowship of the Royal Society. Born Alan Mathison Turing 23 June 1912 Maida Vale, London, England, United Kingdom Died 7 June 1954 (aged 41) Wilmslow, Cheshire, England, United Kingdom Residence United Kingdom Nationality British Fields Mathematics, Cryptanalysis, Computer science Institutions University of Cambridge Government Code and Cypher School National Physical Laboratory University of Manchester Alma mater King's College, Cambridge Princeton University Doctoral advisor Alonzo Church Doctoral students Robin Gandy Known for Halting problem Turing machine Cryptanalysis of the Enigma Automatic Computing Engine Turing Award Turing test Turing patterns Notable awards Officer of the Order of the British Empire Fellow of the Royal Society Alan Mathison Turing, OBE, FRS ( /ˈtjʊərɪŋ/ TEWR-ing; 23 June 1912 – 7 June 1954), was a British mathematician, logician, cryptanalyst, and computer scientist. He was highly influential in the development of computer science, giving a formalisation of the concepts of "algorithm" and "computation" with the Turing machine, which can be considered a model of a general purpose computer.[1][2][3] Turing is widely considered to be the father of computer science and artificial intelligence.[4] During World War II, Turing worked for the Government Code and Cypher School (GC&CS) at Bletchley Park, Britain's codebreaking centre. For a time he was head of Hut 8, the section responsible for German naval cryptanalysis. He devised a number of techniques for breaking German ciphers, including the method of the bombe, an electromechanical machine that could find settings for the Enigma machine.