The Edge-Bandwidth Minimization Problem
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

1 Introduction and Terminology
A Survey of Solved Problems and Applications on Bandwidth, Edgesum and Pro le of Graphs Yung-Ling Lai National Chiayi Teacher College Chiayi, Taiwan, R.O.C. Kenneth Williams Western Michigan University Abstract This pap er provides a survey of results on the exact bandwidth, edge- sum, and pro le of graphs. A bibliographyof work in these areas is pro- vided. The emphasis is on comp osite graphs. This may be regarded as an up date of the original survey of solved bandwidth problems by Chinn, Chvatalova, Dewdney, and Gibbs[10] in 1982. Also several of the applica- tion areas involving these graph parameters are describ ed. 1 Intro duction and terminology For a graph G, V (G) denotes the set of vertices of G and E (G) denotes the set of edges of G. Let G = (V; E ) be a graph on n vertices. A 1-1 mapping f : V ! f1; 2;:::;ng is called a proper numbering of G. The bandwidth B (G) of aproper f numbering f of G is the number B (G)= maxfjf (u) f (v )j : uv 2 E g; f and the bandwidth B(G) of G is the number B (G)= minfB (G): f is a prop er numb ering of Gg: f A prop er numb ering f is called a bandwidth numbering of G if B (G)=B (G). f For example, Figure 1 shows bandwidth numb erings for the graphs P ;C ;K 4 5 1;4 and K . In general, B (P ) = 1, B (C ) = 2, B (K ) = dn=2e and B (K ) = 2;3 n n 1;n m;n m + dn=2e1form n. -
Parental Testing in Graph Theory?
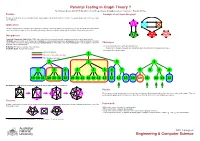
Parental Testing in Graph Theory ? By S Narjess Afzaly,∗ ANU CSIT Algorithm & Data Group, [email protected]. Supervisor: Brendan McKay.∗ Problem A sample of an irreducible graph To make a complete list of non-isomorphic simple quartic graphs with the given number of vertices. In a quartic graph, each vertex has exactly four neighbours. Applications Finding counterexamples, verifying some conjectures or refining some proofs whether in graph theory or in any other field where the problem can be modelled as a graph such as: chemistry, web mining, national security, the railway map, the electrical circuit and neural science. Our approach Canonical Construction Path (McKay 1998): A general method to recursively generate combinatorial objects in which larger objects, (Children), are constructed out of smaller ones, (Parents), by some well-defined operation, (extension), and avoiding constructing isomorphic copies at each construction step by defining a unique genuine parent for each graph. Hence a generated graph is only accepted if it has been Challenges extended from its genuine parent. • To avoid isomorphic copies when generating the list: Reduction: The inverse operation of the extension. Irreducible graph: A graph with no parent. The definition of the genuine parent can substantially affect the efficiency of the generation process. • Generating all irreducible graphs. Genuine parent 1 Has an isomorphic sibling Not genuine parent 2 2 3 4 5 5 6 5 5 6 6 7 5 8 9 6 10 10 11 10 10 11 12 10 10 11 10 10 11 12 12 12 13 10 10 11 10 13 12 Our Reduction: Deleting a vertex and adding two extra disjoint edges between its neighbours. -

Fast Generation of Planar Graphs (Expanded Version)
Fast generation of planar graphs (expanded version) Gunnar Brinkmann∗ Brendan D. McKay† Department of Applied Mathematics Department of Computer Science and Computer Science Australian National University Ghent University Canberra ACT 0200, Australia B-9000 Ghent, Belgium [email protected] [email protected] Abstract The program plantri is the fastest isomorph-free generator of many classes of planar graphs, including triangulations, quadrangulations, and convex polytopes. Many applications in the natural sciences as well as in mathematics have appeared. This paper describes plantri’s principles of operation, the basis for its efficiency, and the recursive algorithms behind many of its capabilities. In addition, we give many counts of isomorphism classes of planar graphs compiled using plantri. These include triangulations, quadrangulations, convex polytopes, several classes of cubic and quartic graphs, and triangulations of disks. This paper is an expanded version of the paper “Fast generation of planar graphs” to appeared in MATCH. The difference is that this version has substantially more tables. 1 Introduction The program plantri can rapidly generate many classes of graphs embedded in the plane. Since it was first made available, plantri has been used as a tool for research of many types. We give only a partial list, beginning with masters theses [37, 40] and PhD theses [32, 42]. Applications have appeared in chemistry [8, 21, 28, 39, 44], in crystallography [19], in physics [25], and in various areas of mathematics [1, 2, 7, 20, 22, 24, 41]. ∗Research supported in part by the Australian National University. †Research supported by the Australian Research Council. 1 The purpose of this paper is to describe the facilities of plantri and to explain in general terms the method of operation. -

On Bounding the Bandwidth of Graphs with Symmetry
On bounding the bandwidth of graphs with symmetry E.R. van Dam∗ R. Sotirovy Abstract We derive a new lower bound for the bandwidth of a graph that is based on a new lower bound for the minimum cut problem. Our new semidefinite program- ming relaxation of the minimum cut problem is obtained by strengthening the known semidefinite programming relaxation for the quadratic assignment problem (or for the graph partition problem) by fixing two vertices in the graph; one on each side of the cut. This fixing results in several smaller subproblems that need to be solved to obtain the new bound. In order to efficiently solve these subproblems we exploit symmetry in the data; that is, both symmetry in the min-cut problem and symmetry in the graphs. To obtain upper bounds for the bandwidth of graphs with symmetry, we de- velop a heuristic approach based on the well-known reverse Cuthill-McKee algorithm, and that improves significantly its performance on the tested graphs. Our approaches result in the best known lower and upper bounds for the bandwidth of all graphs un- der consideration, i.e., Hamming graphs, 3-dimensional generalized Hamming graphs, Johnson graphs, and Kneser graphs, with up to 216 vertices. Keywords: bandwidth, minimum cut, semidefinite programming, Hamming graphs, John- son graphs, Kneser graphs 1 Introduction For (undirected) graphs, the bandwidth problem (BP) is the problem of labeling the vertices of a given graph with distinct integers such that the maximum difference between the labels of adjacent vertices is minimal. Determining the bandwidth is NP-hard (see [35]) and it remains NP-hard even if it is restricted to trees with maximum degree three (see [17]) or to caterpillars with hair length three (see [34]). -

Smallest Cubic and Quartic Graphs with a Given Number of Cutpoints and Bridges Gary Chartrand
Old Dominion University ODU Digital Commons Mathematics & Statistics Faculty Publications Mathematics & Statistics 1982 Smallest Cubic and Quartic Graphs With a Given Number of Cutpoints and Bridges Gary Chartrand Farrokh Saba John K. Cooper Jr. Frank Harary Curtiss E. Wall Old Dominion University Follow this and additional works at: https://digitalcommons.odu.edu/mathstat_fac_pubs Part of the Mathematics Commons Repository Citation Chartrand, Gary; Saba, Farrokh; Cooper, John K. Jr.; Harary, Frank; and Wall, Curtiss E., "Smallest Cubic and Quartic Graphs With a Given Number of Cutpoints and Bridges" (1982). Mathematics & Statistics Faculty Publications. 76. https://digitalcommons.odu.edu/mathstat_fac_pubs/76 Original Publication Citation Chartrand, G., Saba, F., Cooper, J. K., Harary, F., & Wall, C. E. (1982). Smallest cubic and quartic graphs with a given number of cutpoints and bridges. International Journal of Mathematics and Mathematical Sciences, 5(1), 41-48. doi:10.1155/s0161171282000052 This Article is brought to you for free and open access by the Mathematics & Statistics at ODU Digital Commons. It has been accepted for inclusion in Mathematics & Statistics Faculty Publications by an authorized administrator of ODU Digital Commons. For more information, please contact [email protected]. I nternat. J. Math. & Math. Sci. Vol. 5 No. (1982)41-48 41 SMALLEST CUBIC AND QUARTIC GRAPHS WITH A GIVEN NUMBER OF CUTPOINTS AND BRIDGES GARY CHARTRAND and FARROKH SABA Department of Mathematics, Western Michigan University Kalamazoo, Michigan 49008 U. S .A. JOHN K. COOPER, JR. Department of Mathematics, Eastern Michigan University Ypsilanti, Michigan 48197 U.S.A. FRANK HARARY Department of Mathematics, University of Michigan Ann Arbor, Michigan 48104 U.S.A. -

Exact and Approximate Bandwidth
Exact and Approximate Bandwidth Marek Cygan and Marcin Pilipczuk Dept. of Mathematics, Computer Science and Mechanics, University of Warsaw, Poland {cygan,malcin}@mimuw.edu.pl Abstract. In this paper we gather several improvements in the field of exact and approximate exponential-time algorithms for the BANDWIDTH problem. For graphs with treewidth t we present a O(nO(t)2n) exact algorithm. Moreover for the same class of graphs we introduce a subexponential constant-approximation scheme – for anyα>0 there exists a (1 + α)-approximation algorithm running in O(exp(c(t + n/α)logn)) time where c is a universal constant. These re- sults seem interesting since Unger has proved that BANDWIDTH does not belong to AP X even when the input graph is a tree (assuming P = NP). So some- what surprisingly, despite Unger’s result it turns out that not only a subexponen- tial constant approximation is possible but also a subexponential approximation scheme exists. Furthermore, for any positive integer r,wepresenta(4r − 1)- approximation algorithm that solves BANDWIDTH for an arbitrary input graph ∗ n in O (2 r ) time and polynomial space.1 Finally we improve the currently best known exact algorithm for arbitrary graphs with a O(4.473n ) time and space algorithm. In the algorithms for the small treewidth we develop a technique based on the Fast Fourier Transform, parallel to the Fast Subset Convolution techniques introduced by Bj¨orklund et al. This technique can be also used as a simple method of finding a chromatic number of all subgraphs of a given graph in O∗(2n) time and space, what matches the best known results. -

Distance-Two Colorings of Barnette Graphs
CCCG 2018, Winnipeg, Canada, August 8{10, 2018 Distance-Two Colorings of Barnette Graphs Tom´asFeder∗ Pavol Helly Carlos Subiz Abstract that the conjectures hold on the intersection of the two classes, i.e., that tri-connected cubic planar graphs with Barnette identified two interesting classes of cubic poly- all face sizes 4 or 6 are Hamiltonian. When all faces hedral graphs for which he conjectured the existence of have sizes 5 or 6, this was a longstanding open prob- a Hamiltonian cycle. Goodey proved the conjecture for lem, especially since these graphs (tri-connected cubic the intersection of the two classes. We examine these planar graphs with all face sizes 5 or 6) are the popu- classes from the point of view of distance-two color- lar fullerene graphs [8]. The second conjecture has now ings. A distance-two r-coloring of a graph G is an as- been affirmatively resolved in full [18]. For the first con- signment of r colors to the vertices of G so that any jecture, two of the present authors have shown in [10] two vertices at distance at most two have different col- that if the conjecture is false, then the Hamiltonicity ors. Note that a cubic graph needs at least four colors. problem for tri-connected cubic planar graphs is NP- The distance-two four-coloring problem for cubic planar complete. In view of these results and conjectures, in graphs is known to be NP-complete. We claim the prob- this paper we call bipartite tri-connected cubic planar lem remains NP-complete for tri-connected bipartite graphs type-one Barnette graphs; we call cubic plane cubic planar graphs, which we call type-one Barnette graphs with all face sizes 3; 4; 5 or 6 type-two Barnette graphs, since they are the first class identified by Bar- graphs; and finally we call cubic plane graphs with all nette. -

Energy Landscapes for the Self-Assembly of Supramolecular Polyhedra
JNonlinearSci DOI 10.1007/s00332-016-9286-9 Energy Landscapes for the Self-Assembly of Supramolecular Polyhedra Emily R. Russell1 Govind Menon2 · Received: 16 June 2015 / Accepted: 23 January 2016 ©SpringerScience+BusinessMediaNewYork2016 Abstract We develop a mathematical model for the energy landscape of polyhedral supramolecular cages recently synthesized by self-assembly (Sun et al. in Science 328:1144–1147, 2010). Our model includes two essential features of the experiment: (1) geometry of the organic ligands and metallic ions; and (2) combinatorics. The molecular geometry is used to introduce an energy that favors square-planar vertices 2 (modeling Pd + ions) and bent edges with one of two preferred opening angles (model- ing boomerang-shaped ligands of two types). The combinatorics of the model involve two-colorings of edges of polyhedra with four-valent vertices. The set of such two- colorings, quotiented by the octahedral symmetry group, has a natural graph structure and is called the combinatorial configuration space. The energy landscape of our model is the energy of each state in the combinatorial configuration space. The challenge in the computation of the energy landscape is a combinatorial explosion in the number of two-colorings of edges. We describe sampling methods based on the symmetries Communicated by Robert V. Kohn. ERR acknowledges the support and hospitality of the Institute for Computational and Experimental Research in Mathematics (ICERM) at Brown University, where she was a postdoctoral fellow while carrying out this work. GM acknowledges partial support from NSF grant DMS 14-11278. This research was conducted using computational resources at the Center for Computation and Visualization, Brown University. -

Counting Subgraphs Via Homomorphisms∗
Counting Subgraphs via Homomorphisms∗ Omid Aminiy Fedor V. Fominz Saket Saurabhx Abstract We introduce a generic approach for counting subgraphs in a graph. The main idea is to relate counting subgraphs to counting graph homomorphisms. This approach provides new algorithms and unifies several well known results in algorithms and combinatorics includ- ing the recent algorithm of Bj¨orklund,Husfeldt and Koivisto for computing the chromatic polynomial, the classical algorithm of Kohn, Gottlieb, Kohn, and Karp for counting Hamil- tonian cycles, Ryser's formula for counting perfect matchings of a bipartite graph, and color coding based algorithms of Alon, Yuster, and Zwick. By combining our method with known combinatorial bounds, ideas from succinct data structures, partition functions and the color coding technique, we obtain the following new results: • The number of optimal bandwidth permutations of a graph on n vertices excluding n+o(n) a fixed graph as a minor can be computedp in time O(2 ); in particular in time O(2nn3) for trees and in time 2n+O( n) for planar graphs. • Counting all maximum planar subgraphs, subgraphs of bounded genus, or more gen- erally subgraphs excluding a fixed graph M as a minor can be done in 2O(n) time. • Counting all subtrees with a given maximum degree (a generalization of counting Hamiltonian paths) of a given graph can be done in time 2O(n). • A generalization of Ryser's formula: Let G be a graph with an independent set of size `. Then the number of perfect matchings in G can be found in time O(2n−`n3). -

Quartic Planar Graphs
Quartic planar graphs Jane Tan October 2018 A thesis submitted for the degree of Bachelor of Philosophy (Honours) of the Australian National University Declaration The work in this thesis is my own except where otherwise stated. Jane Tan Acknowledgements First, I'd like to thank my supervisors, Brendan McKay and Scott Morrison. Brendan { your guidance has been invaluable. I'm so grateful for all of the exciting problems you've introduced me to, and that you're still putting up with me a full two years after you agreed to take me on \just for one semester". And Scott { thank you for your help with editing, your calming presence, and for sharing the good chalk. I would also like to thank all of the lecturers at the MSI who have been so generous with their time and from whom I have learnt so much. Special thanks to Vigleik, Joan and Andrew for teaching fantastic reading courses and supervising me in projects over the years. Thanks also go to all of the honours students, even the cookie monster and the elusive north-siders. It's been great fun sharing our shiny new office! Last but not least, thank you to my family for always being on the phone. v Abstract In this thesis, we explore three problems concerning quartic planar graphs. The first is on recursive structures; we prove generation theorems for several interest- ing subclasses of quartic planar graphs and their duals, building on previous work which has largely been focussed on the simple or nonplanar cases. The second problem is on the existence of locally self-avoiding Eulerian circuits. -

Exploring Multistability in Prismatic Metamaterials Through Local Actuation
ARTICLE https://doi.org/10.1038/s41467-019-13319-7 OPEN Exploring multistability in prismatic metamaterials through local actuation Agustin Iniguez-Rabago 1, Yun Li 1 & Johannes T.B. Overvelde 1* Metamaterials are artificial materials that derive their unusual properties from their periodic architecture. Some metamaterials can deform their internal structure to switch between different properties. However, the precise control of these deformations remains a challenge, 1234567890():,; as these structures often exhibit non-linear mechanical behavior. We introduce a compu- tational and experimental strategy to explore the folding behavior of a range of 3D prismatic building blocks that exhibit controllable multifunctionality. By applying local actuation pat- terns, we are able to explore and visualize their complex mechanical behavior. We find a vast and discrete set of mechanically stable configurations, that arise from local minima in their elastic energy. Additionally these building blocks can be assembled into metamaterials that exhibit similar behavior. The mechanical principles on which the multistable behavior is based are scale-independent, making our designs candidates for e.g., reconfigurable acoustic wave guides, microelectronic mechanical systems and energy storage systems. 1 AMOLF, Science Park 104, 1098 XG Amsterdam, Netherlands. *email: [email protected] NATURE COMMUNICATIONS | (2019) 10:5577 | https://doi.org/10.1038/s41467-019-13319-7 | www.nature.com/naturecommunications 1 ARTICLE NATURE COMMUNICATIONS | https://doi.org/10.1038/s41467-019-13319-7 n the search for materials with exotic properties, researchers polyhedron in the direction normal to the corresponding face have recently started to explore the design of their mesoscopic (Fig. 1). When assuming rigid origami29 (i.e., the structure can I 1 architecture . -

G-Graphs: a New Representation of Groups
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Elsevier - Publisher Connector Journal of Symbolic Computation 42 (2007) 549–560 www.elsevier.com/locate/jsc G-graphs: A new representation of groups Alain Brettoa,∗, Alain Faisantb, Luc Gilliberta a Universite´ de Caen, GREYC CNRS UMR-6072. Campus 2, Bd Marechal Juin BP 5186, 14032 Caen cedex, France b Universite´ Jean Monnet LARAL 23 rue Paul Michelon, 42023 Saint-Etienne cedex 2, France Received 31 October 2004; accepted 8 August 2006 Available online 5 March 2007 Abstract An important part of computer science is focused on the links that can be established between group theory and graph theory and graphs. CAYLEY graphs, that establish such a link, are useful in a lot of areas of sciences. This paper introduces a new type of graph associated with a group, the G-graphs, and presents many of their properties. We show that various characteristics of a group can be seen on its associated G-graph. We also present an implementation of the algorithm constructing these new graphs, an implementation that will lead to some experimental results. Finally we show that many classical graphs are G-graphs. The relations between G-graphs and CAYLEY graphs are also studied. c 2007 Elsevier Ltd. All rights reserved. Keywords: Computational group theory; Graph representation of a group; Cayley graphs; G-graphs 1. Introduction Group theory can be considered as the study of symmetry. A group is basically the collection of symmetries of some object preserving some of its structure; therefore many sciences have to deal with groups.