Journal of Theoretical and Applied Informtion Technology December 2019 | Vol
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

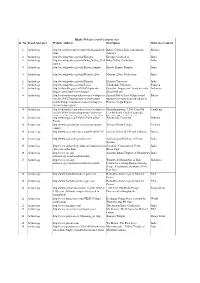
3.Hindu Websites Sorted Country Wise
Hindu Websites sorted Country wise Sl. Reference Country Broad catergory Website Address Description No. 1 Afghanistan Dynasty http://en.wikipedia.org/wiki/Hindushahi Hindu Shahi Dynasty Afghanistan, Pakistan 2 Afghanistan Dynasty http://en.wikipedia.org/wiki/Jayapala King Jayapala -Hindu Shahi Dynasty Afghanistan, Pakistan 3 Afghanistan Dynasty http://www.afghanhindu.com/history.asp The Hindu Shahi Dynasty (870 C.E. - 1015 C.E.) 4 Afghanistan History http://hindutemples- Hindu Roots of Afghanistan whthappendtothem.blogspot.com/ (Gandhar pradesh) 5 Afghanistan History http://www.hindunet.org/hindu_history/mode Hindu Kush rn/hindu_kush.html 6 Afghanistan Information http://afghanhindu.wordpress.com/ Afghan Hindus 7 Afghanistan Information http://afghanhindusandsikhs.yuku.com/ Hindus of Afaganistan 8 Afghanistan Information http://www.afghanhindu.com/vedic.asp Afghanistan and It's Vedic Culture 9 Afghanistan Information http://www.afghanhindu.de.vu/ Hindus of Afaganistan 10 Afghanistan Organisation http://www.afghanhindu.info/ Afghan Hindus 11 Afghanistan Organisation http://www.asamai.com/ Afghan Hindu Asociation 12 Afghanistan Temple http://en.wikipedia.org/wiki/Hindu_Temples_ Hindu Temples of Kabul of_Kabul 13 Afghanistan Temples Database http://www.athithy.com/index.php?module=p Hindu Temples of Afaganistan luspoints&id=851&action=pluspoint&title=H indu%20Temples%20in%20Afghanistan%20. html 14 Argentina Ayurveda http://www.augurhostel.com/ Augur Hostel Yoga & Ayurveda 15 Argentina Festival http://www.indembarg.org.ar/en/ Festival of -
2.Hindu Websites Sorted Category Wise
Hindu Websites sorted Category wise Sl. No. Broad catergory Website Address Description Reference Country 1 Archaelogy http://aryaculture.tripod.com/vedicdharma/id10. India's Cultural Link with Ancient Mexico html America 2 Archaelogy http://en.wikipedia.org/wiki/Harappa Harappa Civilisation India 3 Archaelogy http://en.wikipedia.org/wiki/Indus_Valley_Civil Indus Valley Civilisation India ization 4 Archaelogy http://en.wikipedia.org/wiki/Kiradu_temples Kiradu Barmer Temples India 5 Archaelogy http://en.wikipedia.org/wiki/Mohenjo_Daro Mohenjo_Daro Civilisation India 6 Archaelogy http://en.wikipedia.org/wiki/Nalanda Nalanda University India 7 Archaelogy http://en.wikipedia.org/wiki/Taxila Takshashila University Pakistan 8 Archaelogy http://selians.blogspot.in/2010/01/ganesha- Ganesha, ‘lingga yoni’ found at newly Indonesia lingga-yoni-found-at-newly.html discovered site 9 Archaelogy http://vedicarcheologicaldiscoveries.wordpress.c Ancient Idol of Lord Vishnu found Russia om/2012/05/27/ancient-idol-of-lord-vishnu- during excavation in an old village in found-during-excavation-in-an-old-village-in- Russia’s Volga Region russias-volga-region/ 10 Archaelogy http://vedicarcheologicaldiscoveries.wordpress.c Mahendraparvata, 1,200-Year-Old Cambodia om/2013/06/15/mahendraparvata-1200-year- Lost Medieval City In Cambodia, old-lost-medieval-city-in-cambodia-unearthed- Unearthed By Archaeologists 11 Archaelogy http://wikimapia.org/7359843/Takshashila- Takshashila University Pakistan Taxila 12 Archaelogy http://www.agamahindu.com/vietnam-hindu- Vietnam -

The Balinese Calendar System: from Its Epistemological Perspective to Axiological Practices
International Journal of Linguistics, Literature and Culture Available online at https://sloap.org/journals/index.php/ijllc/ Vol. 4, No. 3, May 2018, pages: 24~37 ISSN: 2455-8028 https://sloap.org/journals/index.php/ijllc/article/view/173 The Balinese Calendar System: From Its Epistemological Perspective to Axiological Practices Gede Ginaya a Article history: Abstract Received: 10 December 2017 Calendars are the order of days and dates used as guidelines for human life Revised: 10 April 2018 activities periodically. Balinese calendar system of the Saka and Pawukon is Approved: 20 April 2018 very important in the socio-cultural life of the Balinese people who firmly Published: 2 May 2018 hold a concept of harmonious life. They believe that this universe will be harmonious when humans can maintain good relations with God, fellow human beings, and the universe in a balanced way. This study aims at Keywords: investigating the Balinese calendar system from its underlying-philosophical Saka calendar; perspective as well as utilized-daily practices among the Hindu Balinese life. Pawukon calendar; The theory used to undertake this study is semiotics by providing a sustained Balinese calendar system; and rigorous relation between the signifier (sign) and signified (meaning). By applying a descriptive qualitative research, the data was collected through literature study of the Balinese calendar library and in-depth interviews with some stakeholders of the Balinese customary community, such as priests, and Balinese calendar practitioners and observers including the writer’s direct practices. The data that has been classified is analyzed by a qualitative descriptive method with an inductive-methodological paradigm which is setting up the discussion from particular principles to the general in order to obtain a conclusion. -

Multi Parameter Design in AIML Framework for Balinese Calendar Knowledge Access
KSII TRANSACTIONS ON INTERNET AND INFORMATION SYSTEMS VOL. 14, NO. 1, Jan. 2020 114 Copyright ⓒ 2020 KSII Multi Parameter Design in AIML Framework for Balinese Calendar Knowledge Access I Made Sukarsa1*, Putu Wira Buana1, Urip Yogantara1 1 Department of Information Technology, Udayana University, Bali, Indonesia [e-mail: [email protected]] * Corresponding author : I Made Sukarsa Received July 4, 2019; revised Septebmer 10, 2019; accepted October 10, 2019; published January 31, 2020 Abstract Balinese calendar is defined as a unique calendar system for combining solar-based and lunar-based system and assuming local system. It is considered as guidance of Balinese societies’ activities management, starting from meeting arrangement, wedding ceremony, to religious ceremonies. Practically, it has developed in the form of printed Balinese calendar and electronic Balinese calendar, either web or mobile application. The core of the function is to find out the day with its various characteristics in the Balinese Calendar. In general, society usually asks the religious leader to find out the day in detail. The technology of NLP combined with models of pattern discoveries supports the arrangement of the interaction model in searching the good day in Balinese Calendar to equip the conventional searching system in the previous applications. This study will design a dialog model with AIML method in multi-parameter basis; therefore, the users will be dynamically able to use the searching content in various ways by chatting in similar with consulting to a religious leader. This model will be applied in a chatbot basis service in telegram machine. The addition of the context recognition section into 4 paterns has been successfully improve the ability of AIML to recognize input patterns with many criteria. -
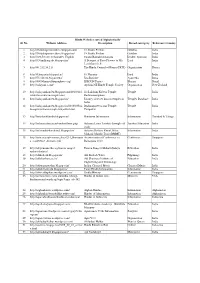
1.Hindu Websites Sorted Alphabetically
Hindu Websites sorted Alphabetically Sl. No. Website Address Description Broad catergory Reference Country 1 http://18shaktipeetasofdevi.blogspot.com/ 18 Shakti Peethas Goddess India 2 http://18shaktipeetasofdevi.blogspot.in/ 18 Shakti Peethas Goddess India 3 http://199.59.148.11/Gurudev_English Swami Ramakrishnanada Leader- Spiritual India 4 http://330milliongods.blogspot.in/ A Bouquet of Rose Flowers to My Lord India Lord Ganesh Ji 5 http://41.212.34.21/ The Hindu Council of Kenya (HCK) Organisation Kenya 6 http://63nayanar.blogspot.in/ 63 Nayanar Lord India 7 http://75.126.84.8/ayurveda/ Jiva Institute Ayurveda India 8 http://8000drumsoftheprophecy.org/ ISKCON Payers Bhajan Brazil 9 http://aalayam.co.nz/ Ayalam NZ Hindu Temple Society Organisation New Zealand 10 http://aalayamkanden.blogspot.com/2010/11/s Sri Lakshmi Kubera Temple, Temple India ri-lakshmi-kubera-temple.html Rathinamangalam 11 http://aalayamkanden.blogspot.in/ Journey of lesser known temples in Temples Database India India 12 http://aalayamkanden.blogspot.in/2010/10/bra Brahmapureeswarar Temple, Temple India hmapureeswarar-temple-tirupattur.html Tirupattur 13 http://accidentalhindu.blogspot.in/ Hinduism Information Information Trinidad & Tobago 14 http://acharya.iitm.ac.in/sanskrit/tutor.php Acharya Learn Sanskrit through self Sanskrit Education India study 15 http://acharyakishorekunal.blogspot.in/ Acharya Kishore Kunal, Bihar Information India Mahavir Mandir Trust (BMMT) 16 http://acm.org.sg/resource_docs/214_Ramayan An international Conference on Conference Singapore -

Blanjong: an Ancient Port Site in Southern Bali, Indonesia (Doi
I Wayan Ardika (2009): Blanjong: An Ancient Port Site in Southern Bali, Indonesia. In: El- friede Hermann, Karin Klenke und Michael Dickhardt (Hg.): Form, Macht, Differenz. Motive und Felder ethnologischen Forschens. Göttingen: Universitätsverlag Göttingen, 251–258. Doi: 10.17875/gup2020-1289 Blanjong: An Ancient Port Site in Southern Bali, Indonesia I Wa y a n Ardika The archeology of Bali is not only a vast and interesting field, but also an area of recent fruitful interdisciplinary research between Brigitta Hauser-Schäublin and myself, which resulted in the book “Burials, Texts and Rituals. Ethnoarcheaological Investiga- tions in Northern Bali, Indonesia” (Hauser-Schäublin and Ardika 2008). Our studies focused on the villages of Sembiran and Julah in northern Bali, which were harbour and trading centers for over 1000 years in transmarine trade between India and China. In this contribution I will concentrate on Blanjong, an archaeological port site in south- ern Bali, and its economic and political importance. Inscriptional Evidence for Dating the Site Blanjong is located in the tourist area of Sanur in southern Bali. Upon the discovery of a stone inscription at Blanjong, the area has attracted the attention of historians, and especially epigraphists from the 1930s onwards. The inscription is written in two types of scripts (biscript) and two languages (bilingual). One side (side A) of the inscription was written in the Nagari script with Old Balinese language and the other side (side B) was written in Kawi style script with Sanskrit language. According to Stutterheim (1934), the appearance of a Nagari script and the San- skrit language in the inscription of Blanjong suggests that North Indian cultures had 252 I Wayan Ardika already been influencing Bali in the 10th century AD. -

The Philosophical Meaning of Nyepi Celebration in Bali from the Context of Maintaining Natural Sustainability and Social Harmony
International Journal of Civil Engineering and Technology (IJCIET) Volume 9, Issue 8, August 2018, pp. 1250–1254, Article ID: IJCIET_09_08_125 Available online at http://iaeme.com/Home/issue/IJCIET?Volume=9&Issue=8 ISSN Print: 0976-6308 and ISSN Online: 0976-6316 © IAEME Publication Scopus Indexed THE PHILOSOPHICAL MEANING OF NYEPI CELEBRATION IN BALI FROM THE CONTEXT OF MAINTAINING NATURAL SUSTAINABILITY AND SOCIAL HARMONY Ni Nyoman Juwita Arsawati, A.A.A.N. Sri Rahayu Gorda, Putu Eva Ditayani Antari Universitas Pendidikan Nasional, Faculty of Law, Denpasar, Bali ABSTRACT Nyepi is holiday and festival of Hindus in Bali that are well-known in national and international level. Nyepi is well-known as the day of silence to celebrate the new year of Balinese saka calendar. Celebrations In wider perspective, the celebration of Nyepi which is one of real actions of the people of Bali for keeping the nature, cleaning air and controlling environmental pollution. The celebration include amati geni (do not light a fire), amati karya (not doing the activity), amati lelungan (not traveling), and amati lelanguan (not doing the entertainment). Hindus stop daily activities, with aims to provide opportunity for nature to do the rehabilitation. On that basis , the celebration of Nyepi is considered as one of the efforts to save nature and the environment, because it is a concept based on the Vedas who is very concerned about nature. Moreover, Nyepi is regarded as an effort to maintain social harmony. Key words: Nyepi, philosophical meaning, natural sustainability, social harmony. Cite this Article: Ni Nyoman Juwita Arsawati, A.A.A.N. -

Kalender Saka Bali” Pada Sistem Operasi Machintos
MERPATI VOL. 3, NO. 2, AGUSTUS 2015 ISSN: 2252-3006 Pengembangan Aplikasi “Kalender Saka Bali” pada Sistem Operasi Machintos I Putu Cahya Prawira, Gusti Made Arya Sasmita, I Putu Agung Bayupati Jurusan Teknologi Informasi, Fakultas Teknik, Universitas Udayana e-mail : [email protected], [email protected], [email protected] Abstrak Kalender Saka Bali merupakan sistem penanggalan yang digunakan oleh orang Hindu di pulau Bali pada umumnya. Pembuatan kalender Saka pada perangkat Machintos (MAC) dapat mempermudah para pengguna Machintos (MAC) untuk mencari, menentukan dan mempelajari bagaimana cara menentukan hari baik dalam upacara agama. Medote dynamic looping digunakan dalam perhitungan kalender Saka Bali agar sesuai dengan perhitungan Parisada Hindu Dharma Indonesia (PHDI). Berdasarkan pengujian, aplikasi ini sesuai dengan Kalender Bali cetak yang sesuai dengan perhitungan PHDI. Pengujian juga dilakukan terhadap fitur-fitur aplikasi kalender Saka Bali ini menggunakan beberapa kalender Bali yang sudah ada. Berdasarkan pengujian, kelebihan aplikasi yaitu dapat melakukan pencarian otonan, pencarian hari raya, pencarian event, pembuatan event, reminder custom, event private, ala ayuning dewasa, pawukuan, wewaran, paringkelan, purnama, tilem, dan sasih. Kekurangan aplikasi ini yaitu tidak dapat melakukan ramalan, konversi dan hanya dapat dijalankan pada komputer dengan sistem operasi Machintos. Kata kunci: Kalender Saka Bali, Machintos, Parisada Hindu Dharma Indonesia, Dynamic Looping Abstract Balinese Saka calendar is the calendar system used by Hindus on the island of Bali in general. Making the Saka calendar on the device Macintosh (MAC) can facilitate the users of Macintosh (MAC) to locate, identify and learn how to determine a good day in a religious ceremony. Looping dynamic methods now used in the calculation of Balinese Saka calendar to fit with the calculation of the Hindu Association of Indonesia (PHDI). -

Pablo Guerra Editor Utopía: 500 Años
Utopía Pablo Guerra Editor Utopía: 500 años Utopia: 500 Years Resumen Utopía: 500 años, tiene como objetivo homenajear la obra más emblemática de Tomás Moro por medio de diecisiete capítulos que analizan luces y sombras, texto y contexto, historia, actualidad y futuro del pensamiento utópico. Sin duda, la voz utopía, acuñada por el humanista cristiano y renacentista Tomás Moro en 1516, ha ocupado un lugar privilegiado en el mundo académico, filosófico e ideológico a lo largo de cinco siglos. El texto que aquí presentamos está organizado en cuatro ejes: “Utopía, análisis de la obra”, “El pensamiento utópico en el marco de la historia de las ideas”, “Géneros literarios utópico y distópico” y “Vigencia del pensamiento utópico”. A través de estos ejes, y con enfoque multidisciplinario, se reúnen las contribuciones de autores de las tres Américas, Europa y Oceanía. En con- clusión, esta es una obra colectiva que aúna la perspectiva histórica, literaria, sociológica, filosófica y humanista que ayudará a discernir con espíritu pluralista los aportes que las utopías han generado en las sociedades contemporáneas. Palabras clave: distopía, filosofía, historia de las ideas, literatura social, Tomás Moro, utopía. Abstract Utopia: 500 Years aims to honor the most emblematic work of Thomas More through se- venteen chapters that analyze the strengths and weaknesses; text and context; and history, present, and future of utopian thought. The word “utopia,” coined by the Christian and Renaissance humanist Thomas More in 1516, has inarguably enjoyed a privileged status in the academic, philosophical, and ideological spheres for over five centuries. The book presented here is organized into four sections: “Utopia, an analysis,” “Utopian thought in the context of the history of ideas,” “Utopian and dystopian literary genres,” and “The relevance of utopian thought.” With these core ideas and the adoption of a multidisciplinary approach, contributions from authors from North, Central, and South America; Europe; and Oceania come together. -

Gregorian Calendar - Wikipedia
12/2/2018 Gregorian calendar - Wikipedia Gregorian calendar The Gregorian calendar is internationally the most widely used civil calendar.[1][2][Note 1] It is named after Pope Gregory 2018 in various calendars XIII, who introduced it in October 1582. Gregorian 2018 [3] It was a refinement to the Julian calendar involving an approximately 0.002% correction in the length of the calendar calendar MMXVIII year. The motivation for the reform was to stop the drift of the calendar with respect to the equinoxes and solstices— Ab urbe 2771 particularly the northern vernal equinox, which helps set the date for Easter. Transition to the Gregorian calendar would condita restore the holiday to the time of the year in which it was celebrated when introduced by the early Church. The reform was Armenian 1467 adopted initially by the Catholic countries of Europe. Protestants and Eastern Orthodox countries continued to use the calendar ԹՎ ՌՆԿԷ traditional Julian calendar and adopted the Gregorian reform, one by one, after a time, at least for civil purposes and for the sake of convenience in international trade. The last European country to adopt the reform was Greece, in 1923. Many (but Assyrian 6768 not all) countries that have traditionally used the Julian calendar, or the Islamic or other religious calendars, have come to calendar adopt the Gregorian calendar for civil purposes. Bahá'í 174–175 calendar The Gregorian reform contained two parts: a reform of the Julian calendar as used prior to Pope Gregory XIII's time, and a reform of the lunar cycle used by the Church with the Julian calendar to calculate the date of Easter. -

Program PDF Version
Table of Contents Conference contacts 2 Conference at a Glance 3 Welcome Note 4 Plenary Session 5 International Program Boards 6 - 7 Proceedings 8 General Information 9 Conference Founder, General Chair Emeritus and Parallel Sessions 10 - 104 Scientific Advisor Sunday 19 July 2020, 17:00-21:30 10 - 25 Gavriel Salvendy Purdue University, USA Monday 20 July 2020, 09:00-13:30 26 - 41 Tsinghua University, P.R. China Tuesday 21 July 2020, 10:00-14:30 42 - 57 and University of Central Florida, USA Wednesday 22 July 2020, 11:00-15:30 58 - 72 Thursday 23 July 2020, 14:00- 18:30 73 - 88 General Chair Friday 24 July 2020, 17:00 – 21:30 89 - 104 Constantine Stephanidis University of Crete and ICS-FORTH, Greece Note: The times indicated are in Email: [email protected] “Central European Summer Time - CEST (Copenhagen)” Conference Administration Email: [email protected] Posters Program Administration Email: [email protected] Sunday, 19 July - Friday, 24 July 2020 106 - 126 Registration Administration Email: [email protected] Student Volunteer Administration Email: [email protected] Communications Chair, Exhibition Chair, HCI International News Editor Abbas Moallem Charles W. Davidson College of Engineering San Jose State University, USA Email: [email protected] 2 l HCI International 2013 TABLE OF CONTENTS Conference at a Glance Conference Program Overview The times indicated are in “Central European Summer Time - CEST (Copenhagen)” You can check and calculate your local time, using an online time conversion tool, such as -

Calendar Knowledge Access
KSII TRANSACTIONS ON INTERNET AND INFORMATION SYSTEMS VOL. 14, NO. 1, Jan. 2020 114 Copyright ⓒ 2020 KSII Multi Parameter Design in AIML Framework for Balinese Calendar Knowledge Access I Made Sukarsa1*, Putu Wira Buana1, Urip Yogantara1 1 Department of Information Technology, Udayana University, Bali, Indonesia 1 Department of Information System, Bali State Polytechnic, Bali, Indonesia [e-mail: [email protected]] * Corresponding author : I Made Sukarsa Received July 4, 2019; revised Septebmer 10, 2019; accepted October 10, 2019; published January 31, 2020 Abstract Balinese calendar is defined as a unique calendar system for combining solar-based and lunar-based system and assuming local system. It is considered as guidance of Balinese societies’ activities management, starting from meeting arrangement, wedding ceremony, to religious ceremonies. Practically, it has developed in the form of printed Balinese calendar and electronic Balinese calendar, either web or mobile application. The core of the function is to find out the day with its various characteristics in the Balinese Calendar. In general, society usually asks the religious leader to find out the day in detail. The technology of NLP combined with models of pattern discoveries supports the arrangement of the interaction model in searching the good day in Balinese Calendar to equip the conventional searching system in the previous applications. This study will design a dialog model with AIML method in multi-parameter basis; therefore, the users will be dynamically able to use the searching content in various ways by chatting in similar with consulting to a religious leader. This model will be applied in a chatbot basis service in telegram machine.