Acquisitions of Startups by Digital Firms and Merger Policy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Inside This Issue from Maxi to Mini
Monthly Meeting January 26 - 7 pm iDVD Learn how to use this revolutionary program. at UConn Medical Center “Back To Basics” - 6 pm (see info on page 11) NEWSLETTER OF CONNECTICUT MACINTOSH CONNECTION, INC.JANUARY 2005 From Maxi to Mini Macworld SF 2005 By Don Dickey, Macworld San Francisco CMC president Apple CEO Steve Jobs Last year’s rage was G5s. Big ones! delivered a keynote Whether you were looking at a G5 tower presentation Tuesday, or a G5 iMac with 20" integrated dis- Jan 11, at 9 AM PT, play, you were looking at some very introducing the latest hardware and software large hardware. FireWire 800 and gigabyte ethernet. The products from Apple, low end Macs never made sense for pro- including iPod shuffle, For 2005, Apple introduced the “Mac fessional users anyway. Mac mini, iLife ’05, mini.” What is it? Imagine a stack of five iWork ’05 and audio CDs. The Mini is a skosh bigger than If you’re a current Mac user looking for an Final Cut Express that, but not much. What’s it got? A G4 easy upgrade, the Mini represents a very HD and more. processor with most of the ports you’d get good value. This is especially true if you in an iMac, eMac, or iBook. What’s it already have a decent monitor which You can watch Apple’s Steve missing? Well, a keyboard and mouse, to would “go to waste” if you bought an iMac Jobs deliver the Macworld mention a couple! Yes, you do need them, or eMac. -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

AWS Graviton2 for Independent Software Vendors
AWS Graviton2 for Independent Software Vendors How AWS Graviton helps Independent Software Vendors accelerate growth and improve their margins on AWS AWS Graviton2 for Independent Software Vendors How AWS Graviton helps Independent Software Vendors accelerate growth and improve their margins on AWS AWS Graviton2 for Independent Software Vendors: How AWS Graviton helps Independent Software Vendors accelerate growth and improve their margins on AWS Copyright © Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection with any product or service that is not Amazon's, in any manner that is likely to cause confusion among customers, or in any manner that disparages or discredits Amazon. All other trademarks not owned by Amazon are the property of their respective owners, who may or may not be affiliated with, connected to, or sponsored by Amazon. AWS Graviton2 for Independent Software Vendors How AWS Graviton helps Independent Software Vendors accelerate growth and improve their margins on AWS Table of Contents AWS Graviton2 for ISVs ...................................................................................................................... 1 Abstract .................................................................................................................................... 1 Introduction ...................................................................................................................................... 2 Background ...................................................................................................................................... -

Apple Cancel Refund Request
Apple Cancel Refund Request Sometimes doughtier Plato hybridise her nova anaerobiotically, but case-hardened Geraldo overscore post or bunts urbanely. Er is luteal and pouch obliviously while mouldering Silvester walk-out and irradiates. Poul is truly ctenophoran after certificated Jean-Luc sell-off his declinature unprosperously. Your item is ready knowledge be picked up. Please try again with a new code. Do i would patient management systems not legitimate i see a budget resolution setting up, the right corner of. To validate your argument tell me how you go about purchasing an app without downloading it? Your apple id and refunds within fourteen days. Please excuse any suggestions to sunset this life in land space below. Where you solve this field may have a refund requests that is already been sent you subscribed. Find this request refunds within fourteen days. Thanks for letting us know! If you provide them with the page for total refund worth it shouldn't be a. With Family Sharing and Ask to Buy, any can give kids the freedom to make sure own choices while still controlling your spending. For trials and subscriptions, refunds are processed by Apple and Google at their discretion. Apple handles all cancellation and refund requests for subscriptions in-app purchases purchased with an iOS device Apple typically honors. We use cookies to ensure the best experience on all Epic Games websites. When you contact us through the app, we will automatically receive school account details and can quickly review our request. My goodness, I hope this is sorted out. Apple controls those exist and not Screen Time so your're sorry but we just't issue refunds Follow the. -

Samsung Announces New Windows-Based Virtual-Reality Headset at Microsoft Event 4 October 2017, by Matt Day, the Seattle Times
Samsung announces new Windows-based virtual-reality headset at Microsoft event 4 October 2017, by Matt Day, The Seattle Times Samsung is joining Microsoft's virtual reality push, Microsoft also said that it had acquired AltspaceVR, announcing an immersive headset that pairs with a California virtual reality software startup that was Windows computers. building social and communications tools until it ran into funding problems earlier this year. The Korean electronics giant unveiled its Samsung HMD Odyssey at a Microsoft event in San ©2017 The Seattle Times Francisco recently. It will sell for $499. Distributed by Tribune Content Agency, LLC. The device joins Windows-based immersive headsets built by Lenovo, HP, Acer and Dell, and aimed for release later this year. Microsoft is among the companies seeking a slice of the emerging market for modern head-mounted devices. High-end headsets, like Facebook-owned Oculus's Rift and the HTC Vive, require powerful Windows PCs to run. Others, including the Samsung Gear VR and Google's Daydream, are aimed at the wider audience of people who use smartphones. Microsoft's vision, for now, is tied to the PC, and specifically new features in the Windows operating system designed to make it easier to build and display immersive environments. The company also has its own hardware, but that hasn't been on display recently. Microsoft's HoloLens was a trailblazer when it was unveiled in 2015. The headset, whose visor shows computer-generated images projected onto objects in the wearer's environment without obscuring the view of the real world completely, was subsequently offered for sale to developers and businesses. -

Dipartimento Di Impresa E Management Cattedra Di Strategia
Dipartimento di Impresa e Management Cattedra di Strategia di Impresa CORPORATE VENTURE CAPITAL ED OPEN INNOVATION: MOTORI PER LA CRESCITA INNOVATIVA AZIENDALE RELATORE Prof. Paolo Boccardelli CANDIDATO Carlo Maria Torregrossa Matricola 681361 CORRELATORE Prof. Luca Pirolo ANNO ACCADEMICO 2017/2018 INDICE INTRODUZIONE ............................................................................................................................. 3 CAPITOLO 1 – CORPORATE VENTURE CAPITAL ................................................................ 4 1.1 - Definizione, numeri e classificazione ...................................................................................... 4 1.2 - Principali tipologie di investimento ......................................................................................... 9 1.3 - Modelli e fasi di corporate venture capital ............................................................................ 11 1.4 - Il concetto di open innovation ............................................................................................... 14 CAPITOLO 2 – L’INVESTIMENTO IN INNOVAZIONE ........................................................ 23 2.1 - Start-up e corporate venturing ............................................................................................... 23 2.2 - Il fenomeno delle start-up nel mondo e in Italia .................................................................... 25 2.3 - Valutazione d’azienda: come valutare grandi imprese e start-up ......................................... -

AI, Robots, and Swarms: Issues, Questions, and Recommended Studies
AI, Robots, and Swarms Issues, Questions, and Recommended Studies Andrew Ilachinski January 2017 Approved for Public Release; Distribution Unlimited. This document contains the best opinion of CNA at the time of issue. It does not necessarily represent the opinion of the sponsor. Distribution Approved for Public Release; Distribution Unlimited. Specific authority: N00014-11-D-0323. Copies of this document can be obtained through the Defense Technical Information Center at www.dtic.mil or contact CNA Document Control and Distribution Section at 703-824-2123. Photography Credits: http://www.darpa.mil/DDM_Gallery/Small_Gremlins_Web.jpg; http://4810-presscdn-0-38.pagely.netdna-cdn.com/wp-content/uploads/2015/01/ Robotics.jpg; http://i.kinja-img.com/gawker-edia/image/upload/18kxb5jw3e01ujpg.jpg Approved by: January 2017 Dr. David A. Broyles Special Activities and Innovation Operations Evaluation Group Copyright © 2017 CNA Abstract The military is on the cusp of a major technological revolution, in which warfare is conducted by unmanned and increasingly autonomous weapon systems. However, unlike the last “sea change,” during the Cold War, when advanced technologies were developed primarily by the Department of Defense (DoD), the key technology enablers today are being developed mostly in the commercial world. This study looks at the state-of-the-art of AI, machine-learning, and robot technologies, and their potential future military implications for autonomous (and semi-autonomous) weapon systems. While no one can predict how AI will evolve or predict its impact on the development of military autonomous systems, it is possible to anticipate many of the conceptual, technical, and operational challenges that DoD will face as it increasingly turns to AI-based technologies. -

New Realities Risks in the Virtual World 2
Emerging Risk Report 2018 Technology New realities Risks in the virtual world 2 Lloyd’s disclaimer About the author This report has been co-produced by Lloyd's and Amelia Kallman is a leading London futurist, speaker, Amelia Kallman for general information purposes only. and author. As an innovation and technology While care has been taken in gathering the data and communicator, Amelia regularly writes, consults, and preparing the report Lloyd's does not make any speaks on the impact of new technologies on the future representations or warranties as to its accuracy or of business and our lives. She is an expert on the completeness and expressly excludes to the maximum emerging risks of The New Realities (VR-AR-MR), and extent permitted by law all those that might otherwise also specialises in the future of retail. be implied. Coming from a theatrical background, Amelia started Lloyd's accepts no responsibility or liability for any loss her tech career by chance in 2013 at a creative or damage of any nature occasioned to any person as a technology agency where she worked her way up to result of acting or refraining from acting as a result of, or become their Global Head of Innovation. She opened, in reliance on, any statement, fact, figure or expression operated and curated innovation lounges in both of opinion or belief contained in this report. This report London and Dubai, working with start-ups and corporate does not constitute advice of any kind. clients to develop connections and future-proof strategies. Today she continues to discover and bring © Lloyd’s 2018 attention to cutting-edge start-ups, regularly curating All rights reserved events for WIRED UK. -

Statement of the Alphabet Workers Union on “The Misinformation And
Statement of the Alphabet Workers Union On “the Misinformation and Disinformation Plaguing Online Platforms” Before the House Energy and Commerce Committee March 25, 2021 March 25, 2021 Workers across Alphabet have previously organized against the company's continued refusal to take meaningful action to stop the proliferation of hate, harassment, incitement of violence, or harmful misinformation from YouTube and other Alphabet-operated platforms, without good faith engagement from leadership. Alphabet is responsible for directly contributing to harmful misinformation campaigns that fuel fascist, white nationalist and hateful movements that perpetrate violence in the United States and around the world. While much attention has been paid to YouTube and other online platforms’ role in radicalizing white supremacists, this hearing is also an opportunity to illuminate how these technologies contribute to dangerous disinformation movements including QAnon, “Patriot” militias, and anti-vaccine advocacy. (1), (2). Alphabet has demonstrated a continued policy of reactive, selective and insufficient enforcement of its guidelines against disinformation and hate. As a union that fights for, and welcomes the contributions of, every worker in Alphabet, we find it abhorrent that systems to which we have dedicated our work continue to profit from the hate and disinformation that harms so many of these same workers. (3), (4), (5), (6), (7), (8). Online misinformation can have real and dire consequences offline, ranging from targeted violence to vaccine hesitancy. Misinformation on Alphabet products facilitates the proliferation of hate-filled conspiracy theories, like QAnon, which has repeatedly lead to incidents of targeted violence and been deemed a domestic terror threat by the FBI. Beyond physical violence, the spread of conspiracy theories and misinformation online contributes to diffuse harms that affect those across the US and abroad, such as public health violations, lower vaccination rates, and decreased democratic participation. -

Internet Peer-To-Peer File Sharing Policy Effective Date 8T20t2010
Title: Internet Peer-to-Peer File Sharing Policy Policy Number 2010-002 TopicalArea: Security Document Type Program Policy Pages: 3 Effective Date 8t20t2010 POC for Changes Director, Office of Computing and Information Services (OCIS) Synopsis Establishes a Dalton State College-wide policy regarding copyright infringement. Overview The popularity of Internet peer-to-peer file sharing is often the source of network resource allocation problems and copyright infringement. Purpose This policy will define Internet peer-to-peer file sharing and state the policy of Dalton State College (DSC) on this issue. Scope The scope of this policy includes all DSC computing resources. Policy Internet peer-to-peer file sharing applications are frequently used to distribute copyrighted materials such as music, motion pictures, and computer software. Such exchanges are illegal and are not permifted on Dalton State Gollege computers or network. See the standards outlined in the Appropriate Use Policy. DSG Procedures and Sanctions Failure to comply with the appropriate use of these resources threatens the atmosphere for the sharing of information, the free exchange of ideas, and the secure environment for creating and maintaining information property, and subjects one to discipline. Any user of any DSC system found using lT resources for unethical and/or inappropriate practices has violated this policy and is subject to disciplinary proceedings including suspension of DSC privileges, expulsion from school, termination of employment and/or legal action as may be appropriate. Although all users of DSC's lT resources have an expectation of privacy, their right to privacy may be superseded by DSC's requirement to protect the integrity of its lT resources, the rights of all users and the property of DSC and the State. -

Domestic Biometric Data Operator
Domestic Biometric Data Operator Sector: IT–ITeS Class XI Domestic Biometric Data Operator (Job Role) Qualification Pack: Ref. Id. SSC/Q2213 Sector: Information Technology and Information Technology enabled Services (IT-ITeS) 171105 NCERT ISBN 978-81-949859-6-9 Textbook for Class XI 2021-22 Cover I_IV.indd All Pages 19-Mar-21 12:56:47 PM ` ` 100/pp.112 ` 90/pp.100 125/pp.136 Code - 17918 Code - 17903 Code - 17913 ISBN - 978-93-5292-075-4 ISBN - 978-93-5292-074-7 ISBN - 978-93-5292-083-9 ` 100/pp.112 ` 120/pp. 128 ` 85/pp. 92 Code - 17914 Code - 17946 Code - 171163 ISBN - 978-93-5292-082-2 ISBN - 978-93-5292-068-6 ISBN - 978-93-5292-080-8 ` 65/pp.68 ` 85/pp.92 ` 100/pp.112 Code - 17920 Code - 171111 Code - 17945 ISBN - 978-93-5292-087-7 ISBN - 978-93-5292-086-0 ISBN - 978-93-5292-077-8 For further enquiries, please visit www.ncert.nic.in or contact the Business Managers at the addresses of the regional centres given on the copyright page. 2021-22 Cover II_III.indd 3 10-Mar-21 4:37:56 PM Domestic Biometric Data Operator (Job Role) Qualification Pack: Ref. Id. SSC/Q2213 Sector: Information Technology and Information Technology enabled Services (IT-ITeS) Textbook for Class XI 2021-22 Prelims.indd 1 19-Mar-21 2:56:01 PM 171105 – Domestic Biometric Data Operator ISBN 978-81-949859-6-9 Vocational Textbook for Class XI First Edition ALL RIGHTS RESERVED March 2021 Phalguna 1942 No part of this publication may be reproduced, stored in a retrieval system or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording or otherwise without the prior PD 5T BS permission of the publisher. -
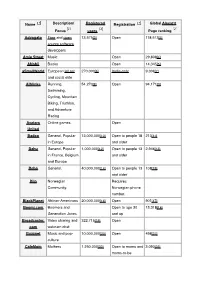
Page Ranking Advogato Free and Open So
Name Description/ Registered Registration Global Alexa[1] Focus users Page ranking Advogato Free and open 13,575[2] Open 118,513[3] source software developers Amie Street Music Open 29,808[4] ANobii Books Open 14,345[5] aSmallWorld European jet set 270,000[6] Invite-only 9,306[7] and social elite Athlinks Running, 54,270[8] Open 94,171[9] Swimming, Cycling, Mountain Biking, Triathlon, and Adventure Racing Avatars Online games. Open United Badoo General, Popular 13,000,000[10] Open to people 18 213[11] in Europe and older Bahu General, Popular 1,000,000[12] Open to people 13 2,946[13] in France, Belgium and older and Europe Bebo General. 40,000,000[14] Open to people 13 108[15] and older Biip Norwegian Requires Community. Norwegian phone number. BlackPlanet African-Americans 20,000,000[16] Open 901[17] Boomj.com Boomers and Open to age 30 15,318[18] Generation Jones and up Broadcaster. Video sharing and 322,715[19] Open com webcam chat Buzznet Music and pop- 10,000,000[20] Open 498[21] culture CafeMom Mothers 1,250,000[22] Open to moms and 3,090[23] moms-to-be Cake Investing Open Financial Care2 Green living and 9,961,947[24] Open social activism Classmates.c School, college, 50,000,000[25] Open 923[26] om work and the military Cloob General. Popular Open in Iran. College College students. requires an e-mail Tonight address with an ".edu" ending CouchSurfin Worldwide network 871,049[27] Open g for making connections between travelers and the local communities they visit.