JP 2-01.1, Joint Tactics, Techniques, and Procedures for Intelligence
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cryptography
Cryptography From Wikipedia, the free encyclopedia Jump to: navigation, search "Secret code" redirects here. For the Aya Kamiki album, see Secret Code. German Lorenz cipher machine, used in World War II to encrypt very-high-level general staff messages Cryptography (or cryptology; from Greek κρυπτός, kryptos, "hidden, secret"; and γράφ, gráph, "writing", or -λογία, -logia, respectively)[1] is the practice and study of hiding information. Modern cryptography intersects the disciplines of mathematics, computer science, and engineering. Applications of cryptography include ATM cards, computer passwords, and electronic commerce. Cryptology prior to the modern age was almost synonymous with encryption, the conversion of information from a readable state to nonsense. The sender retained the ability to decrypt the information and therefore avoid unwanted persons being able to read it. Since WWI and the advent of the computer, the methods used to carry out cryptology have become increasingly complex and its application more widespread. Alongside the advancement in cryptology-related technology, the practice has raised a number of legal issues, some of which remain unresolved. Contents [hide] • 1 Terminology • 2 History of cryptography and cryptanalysis o 2.1 Classic cryptography o 2.2 The computer era • 3 Modern cryptography o 3.1 Symmetric-key cryptography o 3.2 Public-key cryptography o 3.3 Cryptanalysis o 3.4 Cryptographic primitives o 3.5 Cryptosystems • 4 Legal issues o 4.1 Prohibitions o 4.2 Export controls o 4.3 NSA involvement o 4.4 Digital rights management • 5 See also • 6 References • 7 Further reading • 8 External links [edit] Terminology Until modern times cryptography referred almost exclusively to encryption, which is the process of converting ordinary information (plaintext) into unintelligible gibberish (i.e., ciphertext).[2] Decryption is the reverse, in other words, moving from the unintelligible ciphertext back to plaintext. -

Zerohack Zer0pwn Youranonnews Yevgeniy Anikin Yes Men
Zerohack Zer0Pwn YourAnonNews Yevgeniy Anikin Yes Men YamaTough Xtreme x-Leader xenu xen0nymous www.oem.com.mx www.nytimes.com/pages/world/asia/index.html www.informador.com.mx www.futuregov.asia www.cronica.com.mx www.asiapacificsecuritymagazine.com Worm Wolfy Withdrawal* WillyFoReal Wikileaks IRC 88.80.16.13/9999 IRC Channel WikiLeaks WiiSpellWhy whitekidney Wells Fargo weed WallRoad w0rmware Vulnerability Vladislav Khorokhorin Visa Inc. Virus Virgin Islands "Viewpointe Archive Services, LLC" Versability Verizon Venezuela Vegas Vatican City USB US Trust US Bankcorp Uruguay Uran0n unusedcrayon United Kingdom UnicormCr3w unfittoprint unelected.org UndisclosedAnon Ukraine UGNazi ua_musti_1905 U.S. Bankcorp TYLER Turkey trosec113 Trojan Horse Trojan Trivette TriCk Tribalzer0 Transnistria transaction Traitor traffic court Tradecraft Trade Secrets "Total System Services, Inc." Topiary Top Secret Tom Stracener TibitXimer Thumb Drive Thomson Reuters TheWikiBoat thepeoplescause the_infecti0n The Unknowns The UnderTaker The Syrian electronic army The Jokerhack Thailand ThaCosmo th3j35t3r testeux1 TEST Telecomix TehWongZ Teddy Bigglesworth TeaMp0isoN TeamHav0k Team Ghost Shell Team Digi7al tdl4 taxes TARP tango down Tampa Tammy Shapiro Taiwan Tabu T0x1c t0wN T.A.R.P. Syrian Electronic Army syndiv Symantec Corporation Switzerland Swingers Club SWIFT Sweden Swan SwaggSec Swagg Security "SunGard Data Systems, Inc." Stuxnet Stringer Streamroller Stole* Sterlok SteelAnne st0rm SQLi Spyware Spying Spydevilz Spy Camera Sposed Spook Spoofing Splendide -

Intelligence and Net Assessment
GW-5 Intelligence 6/28/2016 Page 1 Chapter Five: Intelligence and Net Assessment Like command and control and battle management, the lessons to be drawn from intelligence during the Gulf War are not only valuable in themselves, they lay the ground work for understanding many of the other aspects and lessons of the war. This is particularly true when intelligence is broadened to cover net assessment, and intelligence- related policy. A narrow definition of the role of intelligence not only gives intelligence responsibility for actions and priorities that were often beyond its control, it ignores critical problems and issues that need to be transformed into lessons for the future. Any such, analysis, however, must be shaped by the fact that the Gulf War was in many ways a war between a Coalition that could "see" and an Iraq that was "blind." The COALITION had a near monopoly of sophisticated intelligence, reconnaissance, near real time analysis capability, and secure communication and dissemination assets. In addition, the Coalition could secure its territory against most Iraqi over flights and incursions, while Iraq effectively had "open skies," with basic intelligence problems greatly reinforced by the rigidities in its strategy and tactics, decision making, and command and control process.1 This war between the "seeing" and the "blind" shaped each side's ability to understand the other's military actions and capabilities throughout Desert Shield. It affected every aspect of battle management during Desert Storm, including such basic military functions as targeting. Superior intelligence played a key role in every aspect of Coalition operations, in giving Coalition forces superior effectiveness, in allowing the Coalition to react to Iraq, in achieving surprise and a superior tempo of operations, and in reducing Coalition casualties. -

JP 2-02 National Intelligence Support to Joint Operations
Joint Pub 2-02 National Intelligence Support to Joint Operations 28 September 1998 PREFACE 1. Scope from organizing the force and executing the mission in a manner the JFC deems most This joint publication describes national appropriate to ensure unity of effort in the intelligence organizations and their support accomplishment of the overall mission. to joint military operations. Also addressed is the special support and augmentation 3. Application available for joint operations by national joint elements such as the Military Intelligence a. Doctrine and guidance established in this Board, the National Military Joint Intelligence publication apply to the commanders and Center, and National Intelligence Support intelligence staff of combatant commands, Teams. This joint publication covers Service subordinate unified commands, joint task forces, intelligence organizations and centers, as combat support agencies, and subordinate well as nonmilitary agencies and components of these commands. These nongovernmental organizations. The principles and guidance also may apply when recommended target audience for this joint significant forces of one Service are attached to publication is commanders and intelligence forces of another Service or when significant staffs of combatant commands, subordinate forces of one Service support forces of another unified commands, joint task forces, combat Service. support agencies, and supporting Service components. b. The guidance in this publication is authoritative; as such, this doctrine (or JTTP) 2. Purpose will be followed except when, in the judgment of the commander, exceptional circumstances This publication has been prepared under dictate otherwise. If conflicts arise between the the direction of the Chairman of the Joint contents of this publication and the contents of Chiefs of Staff. -

ATP 3-90.15. Site Exploitation
ATP 3-90.15 SITE EXPLOITATION July 2015 DISTRIBUTION RESTRICTION. Approved for public release; distribution is unlimited. This publication supersedes ATTP 3-90.15, 8 July 2010. Headquarters, Department of the Army This publication is available at Army Knowledge Online (https://armypubs.us.army.mil/doctrine/index.html). To receive publishing updates, please subscribe at http://www.apd.army.mil/AdminPubs/new_subscribe.asp *ATP 3-90.15 Army Techniques Publication Headquarters No. 3-90.15 Department of the Army Washington, DC, 28 July 2015 Site Exploitation Contents Page PREFACE...............................................................................................................v INTRODUCTION ..................................................................................................vii Chapter 1 SITE EXPLOITATION ........................................................................................ 1-1 Introduction to Site Exploitation .......................................................................... 1-1 Considerations for Effective Site Exploitation..................................................... 1-6 Site Exploitation in the Operational Environment ............................................... 1-7 Chapter 2 SITE EXPLOITATION PLANNING .................................................................... 2-1 Planning Concepts in Site Exploitation ............................................................... 2-1 Information Collection ........................................................................................ -

NIU-Factbook-2013.Pdf
WLEDGE IS ENL O I N G H K T ENMEN T NATIONALNI INTELLIGENCEU U N I V E R S I T Y FACTBOOK ACADEMIC 2013 YEAR 2014 National Intelligence University FACTBOOK Academic Year 2013–2014 PREPARED BY: Director, Institutional Effectiveness National Intelligence University Joint Base Anacostia-Bolling 200 MacDill Blvd., Washington, DC 20340 1 National Intelligence University FACTBOOK Academic Year 2013–2014 Table of Contents Introduction and History ................................................................................................................... 3 Mission ............................................................................................................................................ 5 Mission Source Document ................................................................................................................. 5 Vision ............................................................................................................................................... 6 Strategic Goals .................................................................................................................................. 6 NIU Organization .............................................................................................................................. 6 NIU Board of Visitors ......................................................................................................................... 6 NIU Leadership ................................................................................................................................ -

Report of Investigation on Allegations Related to the Dod's Decision To
INTEGRITY EFFICIENCY ACCOUNTABILITY EXCELLENCE Mission Our mission is to provide independent, relevant, and timely oversight of the Department of Defense that supports the warfighter; promotes accountability, integrity, and efficiency; advises the Secretary of Defense and Congress; and informs the public. Vision Our vision is to be a model oversight organization in the Federal Government by leading change, speaking truth, and promoting excellence—a diverse organization, working together as one professional team, recognized as leaders in our field. Fraud, Waste, & Abuse HOTLINE Department of Defense dodig.mil/hotline|800.424.9098 For more information about whistleblower protection, please see the inside back cover. Table of Contents I. INTRODUCTION ................................................................................................................. 1 II. OVERVIEW OF ALLEGATIONS AND THE DoD OIG INVESTIGATION .................... 4 A. Background and Specific Allegations ............................................................................ 4 B. The DoD OIG Investigation ............................................................................................ 7 III. BACKGROUND ................................................................................................................... 9 A. EUCOM Mission ............................................................................................................ 9 B. AFRICOM Mission ..................................................................................................... -

FACTBOOK Academic Year 2011-2012
National Intelligence University FACTBOOK Academic Year 2011-2012 PREPARED BY: Director, Institutional Effectiveness National Intelligence University Joint Base Anacostia-Bolling 200 MacDill Blvd. Washington, D.C. 20340 FACTBOOK 2011-2012 National Intelligence University FACTBOOK Academic Year 2011-2012 Table of Contents Introduction And History .......................................................................................................................... 1 Mission and Mission Source Document .................................................................................................... 2 Vision ........................................................................................................................................................ 3 Strategic Goals .......................................................................................................................................... 3 NIU Organization ..................................................................................................................................... 4 NIU Board of Visitors ................................................................................................................................ 4 NIU Leadership ......................................................................................................................................... 4 The NIU Faculty ........................................................................................................................................ 7 Faculty & Staff -

Understanding the Globalization of Intelligence Also by Adam D.M
Understanding the Globalization of Intelligence Also by Adam D.M. Svendsen Intelligence Cooperation and the War on Terror: Anglo-American Security Relations after 9/11 The Professionalization of Intelligence Cooperation: Fashioning Method out of Mayhem Understanding the Globalization of Intelligence Adam D.M. Svendsen Intelligence and Defence Strategist, Educator and Researcher © Adam D.M. Svendsen 2012 Softcover reprint of the hardcover 1st edition 2012 All rights reserved. No reproduction, copy or transmission of this publication may be made without written permission. No portion of this publication may be reproduced, copied or transmitted save with written permission or in accordance with the provisions of the Copyright, Designs and Patents Act 1988, or under the terms of any licence permitting limited copying issued by the Copyright Licensing Agency, Saffron House, 6–10 Kirby Street, London EC1N 8TS. Any person who does any unauthorized act in relation to this publication may be liable to criminal prosecution and civil claims for damages. The author has asserted his right to be identified as the author of this work in accordance with the Copyright, Designs and Patents Act 1988. First published 2012 by PALGRAVE MACMILLAN Palgrave Macmillan in the UK is an imprint of Macmillan Publishers Limited, registered in England, company number 785998, of Houndmills, Basingstoke, Hampshire RG21 6XS. Palgrave Macmillan in the US is a division of St Martin’s Press LLC, 175 Fifth Avenue, New York, NY 10010. Palgrave Macmillan is the global academic imprint of the above companies and has companies and representatives throughout the world. Palgrave® and Macmillan® are registered trademarks in the United States, the United Kingdom, Europe and other countries. -

JP 2-0, "Doctrine for Intelligence Support to Joint Operations"
Joint Publication 2-0 Doctrine for Intelligence Support to Joint Operations 9 March 2000 Intelligence plays a vital role in the conduct of successful joint operations. Proper employment of collection and analysis assets is essential if joint force commanders are to gain and maintain information superiority. Without accurate intelligence, our joint forces will lose the essential advantages of surprise, operational security, and flexibility. We must also be cognizant of the changing roles and missions facing the Armed Forces of the United States and ensure that intelligence planning keeps pace with the full range of military operations. The future battlefield will demand high levels of joint interoperability and force enhancement, and the value of intelligence support as an exploitable multiplier cannot be overstated. Joint force commanders, planners, and warfighters at all levels are encouraged to become thoroughly familiar with the doctrine in this publication and use it as a tool for meeting the Nation’s future challenges. HENRY H. SHELTON Chairman of the Joint Chiefs of Staff PREFACE 1. Scope 3. Application This publication is the keystone document a. Doctrine and guidance established in of the intelligence support to joint operations this publication apply to the commanders series. It describes doctrine for intelligence of combatant commands, subunified support to interagency, joint, and commands, joint task forces, and subordinate multinational operations. components of these commands. These principles and guidance also may apply when 2. Purpose significant forces of one Service are attached to forces of another Service or when This publication has been prepared under significant forces of one Service support the direction of the Chairman of the Joint forces of another Service. -
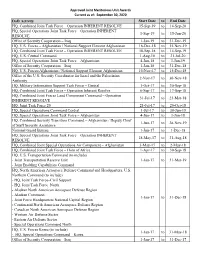
Approved Joint Meritorious Unit Awards Current As Of
Approved Joint Meritorious Unit Awards Current as of: September 30, 2020 DoD Activity Start Date to End Date HQ, Combined Joint Task Force – Operation INHERENT RESOLVE 15-Sep-19 to 14-Sep-20 HQ, Special Operations Joint Task Force – Operation INHERENT 1-Sep-19 to 15-Jun-20 RESOLVE Office of Security Cooperation – Iraq 1-Jan-19 to 31-Dec-19 HQ, U.S. Forces – Afghanistan / National Support Element Afghanistan 16-Dec-18 to 15-Nov-19 HQ, Combined Joint Task Force – Operation INHERENT RESOLVE 18-Sep-18 to 14-Sep-19 HQ, U.S. Central Command 1-Aug-18 to 31-Jul-20 HQ, Special Operations Joint Task Force – Afghanistan 4-Jun-18 to 3-Jun-19 Office of Security Cooperation – Iraq 1-Jan-18 to 31-Dec-18 HQ, U.S. Forces-Afghanistan / National Support Element Afghanistan 16-Nov-17 to 15-Dec-18 Office of the U.S. Security Coordinator for Israel and the Palestinian 2-Nov-17 to 30-Nov-18 Authority HQ, Military Information Support Task Force – Central 1-Oct-17 to 30-Sep-18 HQ, Combined Joint Task Force – Operation Inherent Resolve 6-Sep-17 to 17-Sep-18 HQ, Combined Joint Forces Land Component Command – Operation 31-Jul-17 to 23-Mar-18 INHERENT RESOLVE HQ, Joint Task Force 20 21-Jul-17 to 20-Oct-18 HQ, Special Operations Command Central 1-Jul-17 to 30-Jun-19 HQ, Special Operations Joint Task Force – Afghanistan 4-Jun-17 to 3-Jun-18 HQ, Combined Security Transition Command – Afghanistan / Deputy Chief 1-Jun-17 to 28-Nov-19 of Staff Security Assistance National Guard Bureau 1-Jun-17 to 1-Dec-18 HQ, Special Operations Joint Task Force – Operation INHERENT 18-May-17 to 31-Aug-18 RESOLVE HQ, Combined Joint Special Operations Air Component – Afghanistan 3-May-17 to 2-May-18 HQ, Combined Joint Task Force – Horn of Africa 1-Apr-17 to 30-Sep-18 HQ, U.S. -

Template for CDC Units
Unit 2. Intelligence Organization and Mission 2-1. Intelligence Community............................................................................................................ 2–2 006. Historical background........................................................................................................................2–2 007. National intelligence organizations ...................................................................................................2–3 008. Departmental intelligence elements (non-Department of Defense)...................................................2–9 009. Department of Defense intelligence organizations ..........................................................................2–16 010. Joint intelligence responsibilities.....................................................................................................2–32 011. Intelligence in multinational operations...........................................................................................2–34 012. Air Force intelligence mission, responsibilities, and organizations.................................................2–36 2-2. Intelligence Disciplines............................................................................................................ 2–58 013. Types, components, and sources of intelligence..............................................................................2–58 LL of the business of war, and indeed all of the business of life, is to endeavour to find out what you don’t know by what you do; that’s