JP 2-0, "Doctrine for Intelligence Support to Joint Operations"
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

JP 2-02 National Intelligence Support to Joint Operations
Joint Pub 2-02 National Intelligence Support to Joint Operations 28 September 1998 PREFACE 1. Scope from organizing the force and executing the mission in a manner the JFC deems most This joint publication describes national appropriate to ensure unity of effort in the intelligence organizations and their support accomplishment of the overall mission. to joint military operations. Also addressed is the special support and augmentation 3. Application available for joint operations by national joint elements such as the Military Intelligence a. Doctrine and guidance established in this Board, the National Military Joint Intelligence publication apply to the commanders and Center, and National Intelligence Support intelligence staff of combatant commands, Teams. This joint publication covers Service subordinate unified commands, joint task forces, intelligence organizations and centers, as combat support agencies, and subordinate well as nonmilitary agencies and components of these commands. These nongovernmental organizations. The principles and guidance also may apply when recommended target audience for this joint significant forces of one Service are attached to publication is commanders and intelligence forces of another Service or when significant staffs of combatant commands, subordinate forces of one Service support forces of another unified commands, joint task forces, combat Service. support agencies, and supporting Service components. b. The guidance in this publication is authoritative; as such, this doctrine (or JTTP) 2. Purpose will be followed except when, in the judgment of the commander, exceptional circumstances This publication has been prepared under dictate otherwise. If conflicts arise between the the direction of the Chairman of the Joint contents of this publication and the contents of Chiefs of Staff. -

ATP 3-90.15. Site Exploitation
ATP 3-90.15 SITE EXPLOITATION July 2015 DISTRIBUTION RESTRICTION. Approved for public release; distribution is unlimited. This publication supersedes ATTP 3-90.15, 8 July 2010. Headquarters, Department of the Army This publication is available at Army Knowledge Online (https://armypubs.us.army.mil/doctrine/index.html). To receive publishing updates, please subscribe at http://www.apd.army.mil/AdminPubs/new_subscribe.asp *ATP 3-90.15 Army Techniques Publication Headquarters No. 3-90.15 Department of the Army Washington, DC, 28 July 2015 Site Exploitation Contents Page PREFACE...............................................................................................................v INTRODUCTION ..................................................................................................vii Chapter 1 SITE EXPLOITATION ........................................................................................ 1-1 Introduction to Site Exploitation .......................................................................... 1-1 Considerations for Effective Site Exploitation..................................................... 1-6 Site Exploitation in the Operational Environment ............................................... 1-7 Chapter 2 SITE EXPLOITATION PLANNING .................................................................... 2-1 Planning Concepts in Site Exploitation ............................................................... 2-1 Information Collection ........................................................................................ -

NIU-Factbook-2013.Pdf
WLEDGE IS ENL O I N G H K T ENMEN T NATIONALNI INTELLIGENCEU U N I V E R S I T Y FACTBOOK ACADEMIC 2013 YEAR 2014 National Intelligence University FACTBOOK Academic Year 2013–2014 PREPARED BY: Director, Institutional Effectiveness National Intelligence University Joint Base Anacostia-Bolling 200 MacDill Blvd., Washington, DC 20340 1 National Intelligence University FACTBOOK Academic Year 2013–2014 Table of Contents Introduction and History ................................................................................................................... 3 Mission ............................................................................................................................................ 5 Mission Source Document ................................................................................................................. 5 Vision ............................................................................................................................................... 6 Strategic Goals .................................................................................................................................. 6 NIU Organization .............................................................................................................................. 6 NIU Board of Visitors ......................................................................................................................... 6 NIU Leadership ................................................................................................................................ -

Report of Investigation on Allegations Related to the Dod's Decision To
INTEGRITY EFFICIENCY ACCOUNTABILITY EXCELLENCE Mission Our mission is to provide independent, relevant, and timely oversight of the Department of Defense that supports the warfighter; promotes accountability, integrity, and efficiency; advises the Secretary of Defense and Congress; and informs the public. Vision Our vision is to be a model oversight organization in the Federal Government by leading change, speaking truth, and promoting excellence—a diverse organization, working together as one professional team, recognized as leaders in our field. Fraud, Waste, & Abuse HOTLINE Department of Defense dodig.mil/hotline|800.424.9098 For more information about whistleblower protection, please see the inside back cover. Table of Contents I. INTRODUCTION ................................................................................................................. 1 II. OVERVIEW OF ALLEGATIONS AND THE DoD OIG INVESTIGATION .................... 4 A. Background and Specific Allegations ............................................................................ 4 B. The DoD OIG Investigation ............................................................................................ 7 III. BACKGROUND ................................................................................................................... 9 A. EUCOM Mission ............................................................................................................ 9 B. AFRICOM Mission ..................................................................................................... -

FACTBOOK Academic Year 2011-2012
National Intelligence University FACTBOOK Academic Year 2011-2012 PREPARED BY: Director, Institutional Effectiveness National Intelligence University Joint Base Anacostia-Bolling 200 MacDill Blvd. Washington, D.C. 20340 FACTBOOK 2011-2012 National Intelligence University FACTBOOK Academic Year 2011-2012 Table of Contents Introduction And History .......................................................................................................................... 1 Mission and Mission Source Document .................................................................................................... 2 Vision ........................................................................................................................................................ 3 Strategic Goals .......................................................................................................................................... 3 NIU Organization ..................................................................................................................................... 4 NIU Board of Visitors ................................................................................................................................ 4 NIU Leadership ......................................................................................................................................... 4 The NIU Faculty ........................................................................................................................................ 7 Faculty & Staff -

Understanding the Globalization of Intelligence Also by Adam D.M
Understanding the Globalization of Intelligence Also by Adam D.M. Svendsen Intelligence Cooperation and the War on Terror: Anglo-American Security Relations after 9/11 The Professionalization of Intelligence Cooperation: Fashioning Method out of Mayhem Understanding the Globalization of Intelligence Adam D.M. Svendsen Intelligence and Defence Strategist, Educator and Researcher © Adam D.M. Svendsen 2012 Softcover reprint of the hardcover 1st edition 2012 All rights reserved. No reproduction, copy or transmission of this publication may be made without written permission. No portion of this publication may be reproduced, copied or transmitted save with written permission or in accordance with the provisions of the Copyright, Designs and Patents Act 1988, or under the terms of any licence permitting limited copying issued by the Copyright Licensing Agency, Saffron House, 6–10 Kirby Street, London EC1N 8TS. Any person who does any unauthorized act in relation to this publication may be liable to criminal prosecution and civil claims for damages. The author has asserted his right to be identified as the author of this work in accordance with the Copyright, Designs and Patents Act 1988. First published 2012 by PALGRAVE MACMILLAN Palgrave Macmillan in the UK is an imprint of Macmillan Publishers Limited, registered in England, company number 785998, of Houndmills, Basingstoke, Hampshire RG21 6XS. Palgrave Macmillan in the US is a division of St Martin’s Press LLC, 175 Fifth Avenue, New York, NY 10010. Palgrave Macmillan is the global academic imprint of the above companies and has companies and representatives throughout the world. Palgrave® and Macmillan® are registered trademarks in the United States, the United Kingdom, Europe and other countries. -
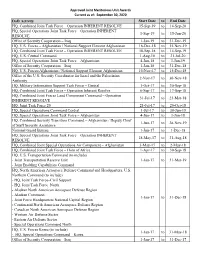
Approved Joint Meritorious Unit Awards Current As Of
Approved Joint Meritorious Unit Awards Current as of: September 30, 2020 DoD Activity Start Date to End Date HQ, Combined Joint Task Force – Operation INHERENT RESOLVE 15-Sep-19 to 14-Sep-20 HQ, Special Operations Joint Task Force – Operation INHERENT 1-Sep-19 to 15-Jun-20 RESOLVE Office of Security Cooperation – Iraq 1-Jan-19 to 31-Dec-19 HQ, U.S. Forces – Afghanistan / National Support Element Afghanistan 16-Dec-18 to 15-Nov-19 HQ, Combined Joint Task Force – Operation INHERENT RESOLVE 18-Sep-18 to 14-Sep-19 HQ, U.S. Central Command 1-Aug-18 to 31-Jul-20 HQ, Special Operations Joint Task Force – Afghanistan 4-Jun-18 to 3-Jun-19 Office of Security Cooperation – Iraq 1-Jan-18 to 31-Dec-18 HQ, U.S. Forces-Afghanistan / National Support Element Afghanistan 16-Nov-17 to 15-Dec-18 Office of the U.S. Security Coordinator for Israel and the Palestinian 2-Nov-17 to 30-Nov-18 Authority HQ, Military Information Support Task Force – Central 1-Oct-17 to 30-Sep-18 HQ, Combined Joint Task Force – Operation Inherent Resolve 6-Sep-17 to 17-Sep-18 HQ, Combined Joint Forces Land Component Command – Operation 31-Jul-17 to 23-Mar-18 INHERENT RESOLVE HQ, Joint Task Force 20 21-Jul-17 to 20-Oct-18 HQ, Special Operations Command Central 1-Jul-17 to 30-Jun-19 HQ, Special Operations Joint Task Force – Afghanistan 4-Jun-17 to 3-Jun-18 HQ, Combined Security Transition Command – Afghanistan / Deputy Chief 1-Jun-17 to 28-Nov-19 of Staff Security Assistance National Guard Bureau 1-Jun-17 to 1-Dec-18 HQ, Special Operations Joint Task Force – Operation INHERENT 18-May-17 to 31-Aug-18 RESOLVE HQ, Combined Joint Special Operations Air Component – Afghanistan 3-May-17 to 2-May-18 HQ, Combined Joint Task Force – Horn of Africa 1-Apr-17 to 30-Sep-18 HQ, U.S. -

Template for CDC Units
Unit 2. Intelligence Organization and Mission 2-1. Intelligence Community............................................................................................................ 2–2 006. Historical background........................................................................................................................2–2 007. National intelligence organizations ...................................................................................................2–3 008. Departmental intelligence elements (non-Department of Defense)...................................................2–9 009. Department of Defense intelligence organizations ..........................................................................2–16 010. Joint intelligence responsibilities.....................................................................................................2–32 011. Intelligence in multinational operations...........................................................................................2–34 012. Air Force intelligence mission, responsibilities, and organizations.................................................2–36 2-2. Intelligence Disciplines............................................................................................................ 2–58 013. Types, components, and sources of intelligence..............................................................................2–58 LL of the business of war, and indeed all of the business of life, is to endeavour to find out what you don’t know by what you do; that’s -

Joint Publication 1-02, Department of Defense Dictionary of Military and Associated Terms
Joint Publication 1-02 Department of Defense Dictionary of Military and Associated Terms 8 November 2010 (As Amended Through 15 February 2016) As Amended Through 15 February 2016 PREFACE 1. Scope The Joint Publication (JP) 1-02, Department of Defense Dictionary of Military and Associated Terms, sets forth standard US military and associated terminology to encompass the joint activity of the Armed Forces of the United States. These military and associated terms, together with their definitions, constitute approved Department of Defense (DOD) terminology for general use by all DOD components. 2. Purpose This publication supplements standard English-language dictionaries and standardizes military and associated terminology to improve communication and mutual understanding within DOD, with other federal agencies, and among the United States and its allies. 3. Application This publication applies to the Office of the Secretary of Defense, the Services, the Joint Staff, combatant commands, DOD agencies, and all other DOD components. It is the primary terminology source when preparing correspondence, to include policy, strategy, doctrine, and planning documents. Criteria for inclusion of terminology in JP 1-02 is enumerated in Department of Defense Instruction 5025.12, Standardization of Military and Associated Terminology, and Chairman of the Joint Chiefs of Staff Instruction (CJCSI) 5705.01, Standardization of Military and Associated Terminology. 4. Publication Format This edition of JP 1-02 has been published in two basic parts: a. Terms and definitions. These are annotated with the source publication. b. Abbreviations and acronyms. The source publication establishes the authoritative context for proper understanding and management of the associated term. 5. JP 1-02 Online Availability and Update Schedule JP 1-02 is accessible online as a searchable database and in PDF format at the following Internet address: http://www.dtic.mil/doctrine/dod_dictionary and at the following NIPRNET i Preface As Amended Through 15 February 2016 address: https://jdeis.js.mil/jdeis/. -

Wikipedia Subcorpora Tool (Wist) a Tool for Creating Customized Document Collections for Training Unsupervised Models of Lexical Semantics
Wikipedia Subcorpora Tool (WiST) A tool for creating customized document collections for training unsupervised models of lexical semantics Natalia Derbentseva Peter Kwantes DRDC – Toronto Research Centre Simon Dennis University of Newcastle Benjamin Stone Ohio State University Defence Research and Development Canada Scientific Report DRDC-RDDC-2016-R100 June 2016 IMPORTANT INFORMATIVE STATEMENTS This work was sponsored by the Influence Activities Task Force (IATF) and was conducted under project 15AH of the Command and Control thrust (5a). Template in use: (2010) SR Advanced Template_EN (051115).dotm © Her Majesty the Queen in Right of Canada, as represented by the Minister of National Defence, 2016 © Sa Majesté la Reine (en droit du Canada), telle que représentée par le ministre de la Défense nationale, 2016 Abstract One of the most important advances in cognitive science over the past 20 years is the invention of computer models that can form semantic representations for words by analysing the patterns with which words are used in documents. Generally speaking, the models need to be ‘trained’ on tens of thousands of documents to form representations that are recognizable as the meaning or ‘gist’ of a term or document. Because the models derive meaning from words’ usage across contexts/documents, the ways that words are used will drive the meaning. In this report, we describe the Wikipedia Subcorpora Tool (WiST), a tool for creating custom document corpora for the purpose of training models of lexical semantics. The tool is unique in that it allows the user to control the kinds of documents that comprise a corpus. For example, one might want to train a model to be an expert on medical topics, so the user can use the WiST to select a collection of medical documents on which to train the model. -

1 Table 1. Joint Meritorious Unit Award – Approved Dod Activities
Table 1. Joint Meritorious Unit Award – Approved DoD Activities The following table lists, by DoD activity and inclusive dates, the approved Joint Meritorious Unit Awards. DoD Activity Inclusive Dates Electronic Warfare During Close Air Support Joint Test Force 15 Mar 76 – 30 Sep 82 Armed Forces Institute of Pathology, Washington, DC 22 Mar 77 – 3 Sep 86 Atlantic Command Electronic Intelligence Center 1 Jan 79 – 31 Dec 83 4477th Test and Evaluation Squadron (USAF) 1 Feb 79 – 1 Feb 84 Joint Deployment Agency 1 May 79 – 14 Apr 87 U.S. Defense Attaché Office, San Salvador, El Salvador 1 Oct 79 – 30 Apr 81 Joint Communications Support Element, U.S. Readiness Command 1 Nov 79 – 31 Dec 83 Defense Language Institute English Language Center 1 Jan 80 – 30 Jun 83 Intelligence Center Pacific 1 Sep 80 – 21 Mar 83 Joint Special Operations Support Element, U.S. Readiness 30 Sep 80 – 30 Sep 84 Command Joint United States Military Mission for Aid to Turkey, United 18 Dec 80 – 30 Jun 86 States European Command United States Military Liaison Mission to CINC, Group of Soviet 1 Jan 81 – 31 Mar 85 Forces in Germany (EUCOM) United States Military Group El Salvador (1st Award) 1 Jan 81 – 7 Jun 85 Defense Nuclear Agency 1 Jul 81 – 30 Jun 84 Commander in Chief, Allied Forces Southern Europe Band 1 Oct 81 – 31 Mar 83 U.S. Liaison Office Morocco 1 Oct 81 – 30 Jun 83 Office of Military Cooperation Cairo, Egypt 1 Oct 81 – 30 Sep 83 U.S. Defense Attaché Office Nicosia, Cyprus 1 Jun 82 – 31 Dec 83 Defense Mapping Agency 1 Jun 82 – 1 Jun 84 U.S. -

JP 2-01.1, Joint Tactics, Techniques, and Procedures for Intelligence
Joint Publication 2-01.1 Joint Tactics, Techniques, and Procedures for Intelligence Support to Targeting 9 January 2003 PREFACE 1. Scope This publication provides joint tactics, techniques, and procedures (JTTP) for joint intelligence organizations to implement the fundamental principles of Joint Publication (JP) 2-0, Doctrine for Intelligence Support to Joint Operations, supporting the doctrinal guidance of JP 3-60, Joint Doctrine for Targeting, across the range of military operations. This JTTP publication describes the relationships and procedures necessary for intelligence support to joint targeting (including the operations and intelligence relationships) and roles and responsibilities at the national, combatant command, subordinate joint force, and component levels. This publication describes intelligence processes and procedures supporting the joint force commander (JFC) throughout all phases of the targeting cycle. 2. Purpose This publication has been prepared under the direction of the Chairman of the Joint Chiefs of Staff. It sets forth doctrine and selected JTTP to govern the joint activities and performance of the Armed Forces of the United States in joint operations and provides the doctrinal basis for US military involvement in multinational and interagency operations. It provides military guidance for the exercise of authority by combatant commanders and other JFCs and prescribes doctrine and selected tactics, techniques, and procedures for joint operations and training. It provides military guidance for use by the Armed Forces in preparing their appropriate plans. It is not the intent of this publication to restrict the authority of the JFC from organizing the force and executing the mission in a manner the JFC deems most appropriate to ensure unity of effort in the accomplishment of the overall mission.