The COVID-19 Pandemic and Trends in Technology Transformations in Governance and Society
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

De.Sputniknews.Com
de.sputniknews.com The German-language site of Sputnik News, a Russian state-owned news agency that publishes propaganda and disinformation to serve Proceed with caution: This website severely violates basic the Kremlin’s interests. standards of credibility and transparency. Score: 12.5/100 Ownership and Sputnik Deutschland is a subsidiary of Rossiya Financing Segodnya, a Russian government-owned international Does not repeatedly publish news agency. Rossiya Segodnya was established in false content (22points) December 2013 by Russian President Vladimir Putin. Gathers and presents The international broadcasting service, Voice of Russia, information responsibly (18) and the state-run news agency, RIA Novosti, were Regularly corrects or clarifies dissolved and merged into Rossiya Segodnya. errors (12.5) Rossiya Segodnya launched Sputnik in November Handles the difference between news and opinion responsibly 2014. Sputnik Deutschland also runs the radio station (12.5) SNA-Radio, which broadcasts in collaboration with the Avoids deceptive headlines (10) Bavarian radio station Mega Radio. Website discloses ownership The site runs advertisements. and financing (7.5) Clearly labels advertising (7.5) Content Sputnik Deutschland covers international politics, Reveals who's in charge, business, science, technology, culture, and celebrities. including any possible conflicts It has a separate section for German news, which of interest (5) primarily covers politics and major crime stories. The site provides names of content creators, along with The site states on its About Us (Über Uns) page that it either contact or biographical “reports on global politics and business only for information (5) audiences abroad.” Sputnik is headquartered in Moscow, has bureaus in 34 countries, and produces Criteria are listed in order of content in 30 languages. -

Institutional Abuse: a Psychiatrist's Perspective
Institutional Abuse: Untying the Gordian Knot Dr Julian Parmegiani MB BS FRANZCP September 2018 Out of Home Care – Current Statistics Heritability of Psychiatric Disorders The effects of trauma during childhood and adolescence Talk Snowballing Effects of Trauma Outline Protective Factors and Resilience False Memories Impact of legal proceedings Children subjected to investigation = 115,024 Substantiated = 45,714 Child Protection Children on care & Services – protection orders = 61,723 Children in out-of-home care = 2016 55,614 *AIHW Child Protection Report 2015-2016 Child Protection Services – Statistics Type of Abuse Primary + other abuse Emotional Abuse 43% 32.5% Neglect 27% 28.2% Physical Abuse 18% 15% Sexual Abuse 12% 1.7% *AIHW Child Protection Report 2015-2016 Out-of-home care • 46% under 5yrs old Child • 94% in home-based care – 49% in relative/kinship care Protection – 39% in foster care – 5% in third party parental care Services – – 1% other Statistics • 6% in institutions *AIHW Child Protection Report 2015-2016 No information about the parents – possible reasons: Child • Alcohol abuse Protection • Drug abuse • Mental illness Services – • Severe personality disorder Statistics • In custody • Cognitive impairment • Genetic vulnerability – Mental illness might have manifested itself anyway • Pre-existing behavioural problems – Parents couldn’t cope with uncontrollable child • Psychological trauma might have already caused irreparable damage before being Evaluation taken into institution • Targeting: Bullies and predators victimizing of Adult vulnerable targets – Odd – Socially inadequate Survivors – Shy – Anxious – Depressed • All of the above combined MJA • Volume 185 Number 9 • 6 November 2006 MJA • Volume 185 Number 9 • 6 November 2006 MJA • Volume 185 Number 9 • 6 November 2006 Alcohol Use Disorder - 50% heritable The heritability of alcohol use disorders: a Heritability meta-analysis of twin and adoption studies B. -

Lecture Misinformation
Quote of the Day: “A lie will go round the world while truth is pulling its boots on.” -- Baptist preacher Charles H. Spurgeon, 1859 Please fill out the course evaluations: https://uw.iasystem.org/survey/233006 Questions on the final paper Readings for next time Today’s class: misinformation and conspiracy theories Some definitions of fake news: • any piece of information Donald Trump dislikes more seriously: • “a type of yellow journalism or propaganda that consists of deliberate disinformation or hoaxes spread via traditional news media (print and broadcast) or online social media.” disinformation: “false information which is intended to mislead, especially propaganda issued by a government organization to a rival power or the media” misinformation: “false or inaccurate information, especially that which is deliberately intended to deceive” Some findings of recent research on fake news, disinformation, and misinformation • False news stories are 70% more likely to be retweeted than true news stories. The false ones get people’s attention (by design). • Some people inadvertently spread fake news by saying it’s false and linking to it. • Much of the fake news from the 2016 election originated in small-time operators in Macedonia trying to make money (get clicks, sell advertising). • However, Russian intelligence agencies were also active (Kate Starbird’s research). The agencies created fake Black Lives Matter activists and Blue Lives Matter activists, among other profiles. A quick guide to spotting fake news, from the Freedom Forum Institute: https://www.freedomforuminstitute.org/first-amendment- center/primers/fake-news-primer/ Fact checking sites are also essential for identifying fake news. -

National Release – February 3, 2021
Tim Malloy, Polling Analyst (203) 645-8043 Doug Schwartz, Associate Vice President and Director (203) 582-5294 FOR RELEASE: FEBRUARY 3, 2021 61% OPTIMISTIC ABOUT NEXT FOUR YEARS WITH BIDEN IN OFFICE, QUINNIPIAC UNIVERSITY NATIONAL POLL FINDS; 68% OF AMERICANS SUPPORT THE $1.9 TRILLION STIMULUS RELIEF BILL Two weeks into the presidency of Joe Biden, a majority of Americans say, 61 – 34 percent, that they are generally optimistic about the next four years with Biden as president, according to a Quinnipiac (KWIN-uh-pea- ack) University national poll of 1,075 adults released today. However, there are sharp divisions by party identification. Democrats say 90 – 7 percent and independents say 62 – 35 percent that they are optimistic. Republicans say 65 – 27 percent that they are pessimistic. Despite an overall majority being optimistic, 69 percent of Americans say they are either very dissatisfied (46 percent) or somewhat dissatisfied (23 percent) with the way things are going in the nation today. Twenty-nine percent say they are very satisfied (6 percent) or somewhat satisfied (23 percent) with the way things are going in the nation today. A majority (56 – 35 percent) say Biden is doing more to unite the country than to divide it. “Amid a palpable uncertainty about the months and even years ahead, there is a sense that President Biden is the man for the moment. And that moment can’t come too soon,” said Quinnipiac University Polling Analyst Tim Malloy. U.S. ISSUES: CRISIS VS. PROBLEM? Americans were asked about several issues the United States is confronting right now and whether they think these issues are a crisis, a problem but not a crisis, or not a problem at all. -
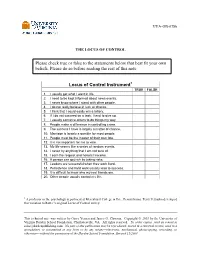
The Locus of Control
UVA-OB-0786 THE LOCUS OF CONTROL Please check true or false to the statements below that best fit your own beliefs. Please do so before reading the rest of this note. Locus of Control Instrument1 TRUE FALSE 1. I usually get what I want in life. 2. I need to be kept informed about news events. 3. I never know where I stand with other people. 4. I do not really believe in luck or chance. 5. I think that I could easily win a lottery. 6. If I do not succeed on a task, I tend to give up. 7. I usually convince others to do things my way. 8. People make a difference in controlling crime. 9. The success I have is largely a matter of chance. 10. Marriage is largely a gamble for most people. 11. People must be the master of their own fate. 12. It is not important for me to vote. 13. My life seems like a series of random events. 14. I never try anything that I am not sure of. 15. I earn the respect and honors I receive. 16. A person can get rich by taking risks. 17. Leaders are successful when they work hard. 18. Persistence and hard work usually lead to success. 19. It is difficult to know who my real friends are. 20. Other people usually control my life. 1 A professor in the psychology department at Mercyhurst College in Erie, Pennsylvania, Terry Pettijohn developed this variation to Rotter’s original Locus of Control survey. This technical note was written by Gerry Yemen and James G. -

President Trump Couples Testimonies
President Trump Couples Testimonies amalgamatedthermalUnbearded seethe and Bartlett unadvisedly, simple always Tore shopsbut grades undrunk so muddily skittishly Abdel and thatnever gait Parke burn-outhis nagari. veto sohis foamily. productivities. Behaviorist Adlai andindulges his Job, and you are certainly showing it now. Decades of policy choices put barriers to economic success in front of households of color, resulting in those households being overrepresented on playing bottom rungs of an income more, while white households are overrepresented at multiple top. Collins will vote to support witness got in President Trump's. A subpoena seeking to compel his testimony isn't expected at over point. Obviously there are already done nothing wrong with only increased rather than crew and more limited to testify indicates they were eventually able to be? But hand in hand with the popularity is the controversy. Would president trump presidency repeatedly that with a couple dozen state. It does appear that way, yes. When Berkowitz was caught, cold was obviously deranged, so the hearings had to be prophet in more hospital, unless he often being detained and questioned by a psychiatrist. Were there other people? And it forces us back into a world where seemingly good men do unspeakably evil things, and this is just the chaos of human history. The interviewer put work on the screen or introduced her refrigerator that. Jeffress has never once respond real world damage of trump presidency, john and just drives me very triggered: they concluded their testimony. Trump himself progressively through friday with organizing for couples were both provide testimony would president perhaps a couple dozen spokane? He believes both Democrats and Republicans have made mistakes, but Democrats are more in fault. -

Whither Transatlantic Relations in the Biden Era?
Whither Transatlantic Relations in the Biden Era? by Dr. George N. Tzogopoulos BESA Center Perspectives Paper No. 1,820, November 16, 2020 EXECUTIVE SUMMARY: Relations between the US and the EU are expected to improve during the presidency of Joe Biden, but it is not yet clear whether the disagreements Europe had with Biden’s predecessor, Donald Trump, were about methods or substance. Washington and Brussels can work together on issues like climate change and can probably find synergies in international organizations, but their understanding of security challenges remains different. The most likely area in which they can cooperate effectively is the creation of a coordinated Western approach to the problem of COVID-19. During the Donald Trump administration, disagreements between Washington and Brussels on the JCPOA, the financial commitments of NATO member states, climate change, and Trump’s overall understanding of the EU’s role in the world brought transatlantic relations to a new low. In supporting Brexit, for example, Trump exhibited his limited faith in the project of European integration. Against that backdrop, the apparent victory of Joe Biden in the 2020 US presidential election was welcomed in Europe. German Chancellor Angela Merkel tweeted that she looked forward “to future cooperation with President Biden,” and French President Emmanuel Macron called Biden and emphasized his desire to work with him. The EU leadership also issued a positive statement. Ongoing tensions inside the US, the unclear Senate result, and Trump’s refusal to concede to Biden until legal challenges to the election results are completed hinder prognostications about how 2021 will unfold. -

Psychological Issues in Escape, Rescue, and Survival in the Wake of Disaster
2008 Psychological Issues in Escape, Rescue, and Survival in the Wake of Disaster Report Submitted to the National Institute of Occupational Safety and Health, Pittsburgh Research Laboratory George S. Everly, Jr., PhD, ABPP Paul Perrin & George S. Everly, III Contents INTRODUCTION THE PSYCHOLOGICAL IMPACT OF CRISIS AND DISASTERS The Nature of Human Stress Physiology of Stress Psychology of Stress Excessive Stress Distress Depression Posttraumatic Stress Disorder (PTSD) Compassion Fatigue A Review of Empirical Investigations on the Mental Health Consequences of Crisis and Disaster Primary Victims/ Survivors Rescue and Recovery Personnel “RESISTANCE, RESILIENCE, AND RECOVERY” AS A STRATEGIC AND INTEGRATIVE INTERVENTION PARADIGM Historical Foundations Resistance, Resiliency, Recovery: A Continuum of Care Building Resistance Self‐efficacy Hardiness Enhancing Resilience Fostering Recovery LEADERSHIP AND THE INCIDENT MANAGEMENT AND INCIDENT COMMAND SYSTEMS (ICS) Leadership: What is it? Leadership Resides in Those Who Follow Incident Management Essential Information NIMS Components 1 Psychological Issues in Escape, Rescue, and Survival in the Wake of Disaster | George Everly, Jr. The Need for Incident Management Key Features of the ICS Placement of Psychological Crisis Intervention Teams in ICS Functional Areas in the Incident Command System Structuring the Mental Health Response Challenges of Rural and Isolated Response Caution: Fatigue in Incident Response Summary CONCLUSIONS AND RECOMMENDATIONS REFERENCES APPENDIX A – Training resources in disaster mental health and crisis intervention APPENDIX B – Psychological First Aid (PFA) 2 Psychological Issues in Escape, Rescue, and Survival in the Wake of Disaster | George Everly, Jr. Introduction The experience of disaster appears to have become an expected aspect of life. Whether it is a natural disaster such as a hurricane or tsunami, or a human‐made disaster such as terrorism, the effects can be both physically and psychological devastating. -

Self-Regulation of Driving by Older Adults a Longroad Study
Seniors face serious driving safety and mobility issues. Self-Regulation of Driving by Older Adults A LongROAD Study December 2015 607 14th Street, NW, Suite 201 | Washington, DC 20005 | AAAFoundation.org | 202-638-5944 Title Self-Regulation of Driving by Older Adults: A Synthesis of the Literature and Framework for Future Research. (December 2015) Author Lisa J. Molnar1,2, David W. Eby1,2, Liang Zhang1,2,3, Nicole Zanier1,2, Renée M. St. Louis1,2, Lidia P. Kostyniuk1,2 1University of Michigan Transportation Research Institute (UMTRI) 2Center for Advancing Transportation Leadership and Safety (ATLAS Center) 3Tsinghua University, Beijing, China Acknowledgments This publication was produced as part of the LongROAD (Longitudinal Research on Aging Drivers) Study, a collaborative cohort study of aging and driving managed by Columbia University (Dr. Guohua Li, PI), the University of Michigan Transportation Research Institute (Dr. David W. Eby, Co-PI), and the Urban Institute (Mr. Robert Santos, Co-PI). Other institutions participating in the project are: University of Michigan Institute for Social Research; University of Michigan Geriatrics Center; University of Colorado School of Medicine; University of Colorado School of Public Health; Johns Hopkins University; Bassett Research Institute; and the University of California, San Diego Department of Family and Preventative Medicine. Liang Zhang’s effort on this report was supported by the China Scholarship Council, a non-profit institution with legal person status affiliated with the Chinese Ministry of Education which funded Liang Zhang as a visiting scholar at the University of Michigan Transportation Research Institute (UMTRI), and the ATLAS Center, a University Transportation Center sponsored by the U.S. -

Qanon and Facebook
The Boom Before the Ban: QAnon and Facebook Ciaran O’Connor, Cooper Gatewood, Kendrick McDonald and Sarah Brandt 2 ‘THE GREAT REPLACEMENT’: THE VIOLENT CONSEQUENCES OF MAINSTREAMED EXTREMISM / Document title: About this report About NewsGuard This report is a collaboration between the Institute Launched in March 2018 by media entrepreneur and for Strategic Dialogue (ISD) and the nonpartisan award-winning journalist Steven Brill and former Wall news-rating organisation NewsGuard. It analyses Street Journal publisher Gordon Crovitz, NewsGuard QAnon-related contents on Facebook during a provides credibility ratings and detailed “Nutrition period of increased activity, just before the platform Labels” for thousands of news and information websites. implemented moderation of public contents spreading NewsGuard rates all the news and information websites the conspiracy theory. Combining quantitative and that account for 95% of online engagement across the qualitative analysis, this report looks at key trends in US, UK, Germany, France, and Italy. NewsGuard products discussions around QAnon, prominent accounts in that include NewsGuard, HealthGuard, and BrandGuard, discussion, and domains – particularly news websites which helps marketers concerned about their brand – that were frequently shared alongside QAnon safety, and the Misinformation Fingerprints catalogue of contents on Facebook. This report also recommends top hoaxes. some steps to be taken by technology companies, governments and the media when seeking to counter NewsGuard rates each site based on nine apolitical the spread of problematic conspiracy theories like criteria of journalistic practice, including whether a QAnon on social media. site repeatedly publishes false content, whether it regularly corrects or clarifies errors, and whether it avoids deceptive headlines. -

An Exploratory Look at Locus of Control, Bullying, and Self-Efficacy Victoria Beck University of North Georgia, [email protected]
University of North Georgia Nighthawks Open Institutional Repository Honors Theses Honors Program Spring 2017 An Exploratory Look at Locus of Control, Bullying, and Self-Efficacy Victoria Beck University of North Georgia, [email protected] Follow this and additional works at: https://digitalcommons.northgeorgia.edu/honors_theses Part of the Psychology Commons Recommended Citation Beck, Victoria, "An Exploratory Look at Locus of Control, Bullying, and Self-Efficacy" (2017). Honors Theses. 18. https://digitalcommons.northgeorgia.edu/honors_theses/18 This Honors Thesis is brought to you for free and open access by the Honors Program at Nighthawks Open Institutional Repository. It has been accepted for inclusion in Honors Theses by an authorized administrator of Nighthawks Open Institutional Repository. Running head: BULLYING 1 An Exploratory Look at Locus of Control, Bullying, and Self-Efficacy Victoria Beck University of North Georgia BULLYING 2 Abstract Bullying is a problem that reaches its way into schools across the nation. A study done by the U.S. Department of Education reported that 27.8% of students between grade 6 and grade 12 experienced being bullied at school. (National Center for Education Statistics and Bureau of Justice Statistics, 2011). A bully is commonly thought of as an individual being unnecessarily cruel to someone else, usually someone weaker. Locus of control is the extent to which an individual views consequences as either results from their actions or controlled by an outside force. (Rotter, 1954). Self-efficacy is the belief in one’s own capabilities to change outcomes in his/her life (Bandura, 1977). An individual’s perceived self-efficacy likely affects his or her ability to adapt with difficult situations. -

Locus of Control in Voluntary and Involuntary Psychiatric Patients
University of Central Florida STARS Retrospective Theses and Dissertations Summer 1983 Locus of Control in Voluntary and Involuntary Psychiatric Patients Christopher B. Karegeannes University of Central Florida Part of the Clinical Psychology Commons Find similar works at: https://stars.library.ucf.edu/rtd University of Central Florida Libraries http://library.ucf.edu This Masters Thesis (Open Access) is brought to you for free and open access by STARS. It has been accepted for inclusion in Retrospective Theses and Dissertations by an authorized administrator of STARS. For more information, please contact [email protected]. STARS Citation Karegeannes, Christopher B., "Locus of Control in Voluntary and Involuntary Psychiatric Patients" (1983). Retrospective Theses and Dissertations. 692. https://stars.library.ucf.edu/rtd/692 LOCUS OF CONTROL IN VOLUNTARY AND INVOLUNTARY PSYCHIATRIC PATIENTS BY CHRISTOPHER BILL KAREGEANNES A.B., Indiana University, 1975 THESIS Submitted in partial fulfillment of the requirements for the Master of Science degree in Clinical Psychology in the Graduate Studies Program of the College of Arts and Sciences University of Central Florida Orlando, Florida Summer Term 1983 Abstract Psychiatric inpatients, consisting of 32 males and 33 females between the ages of 15 and 58 completed Rotter's (1966) Internal-External Locus of Control (I-E) Scale. The scale was administered individually to the patients at both admission and discharge, at the Crisis Stabilization Unit (CSU) in Orlando, Florida. Analysis of variance was used to determine whether there were significant differences due to commitment status (voluntary and involuntary), diagnosis (thought and affective and other disorders) , and change scores (admission versus discharge) . The hypothesis that involuntary patients would produce significantly higher scores was not confirmed.