Trends in the Threat Landscape
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

الجريمة اإللكرتونية يف املجتمع الخليجي وكيفية مواجهتها Cybercrimes in the Gulf Society and How to Tackle Them
مسابقة جائزة اﻷمير نايف بن عبدالعزيز للبحوث اﻷمنية لعام )2015م( الجريمة اﻹلكرتونية يف املجتمع الخليجي وكيفية مواجهتها Cybercrimes in the Gulf Society and How to Tackle Them إعـــــداد رامـــــــــــــي وحـــــــــــــيـد مـنـصــــــــــور باحـــــــث إســـتراتيجي في الشــــــئون اﻷمـــنـــية واﻻقتصـــــــــاد الســــــــياسـي -1- أ ت جملس التعاون لدول اخلليج العربية. اﻷمانة العامة 10 ج إ الجريمة اﻹلكترونية في المجتمع الخليجي وكيفية مواجهتها= cybercrimes in the Gulf:Society and how to tackle them إعداد رامي وحيد منصور ، البحرين . ـ الرياض : جملس التعاون لدول اخلليج العربية ، اﻷمانة العامة؛ 2016م. 286 ص ؛ 24 سم الرقم املوحد ملطبوعات اجمللس : 0531 / 091 / ح / ك/ 2016م. اجلرائم اﻹلكرتونية / / جرائم املعلومات / / شبكات احلواسيب / / القوانني واللوائح / / اجملتمع / مكافحة اجلرائم / / اجلرائم احلاسوبية / / دول جملس التعاون لدول اخلليج العربية. -2- قائمة املحتويات قائمة احملتويات .......................................................................................................... 3 قائمــة اﻷشــكال ........................................................................................................10 مقدمــة الباحــث ........................................................................................................15 مقدمة الدراســة .........................................................................................................21 الفصل التمهيدي )اﻹطار النظري للدراسة( موضوع الدراســة ...................................................................................................... 29 إشــكاليات الدراســة ................................................................................................ -

Understanding and Analyzing Malicious Domain Take-Downs
Cracking the Wall of Confinement: Understanding and Analyzing Malicious Domain Take-downs Eihal Alowaisheq1,2, Peng Wang1, Sumayah Alrwais2, Xiaojing Liao1, XiaoFeng Wang1, Tasneem Alowaisheq1,2, Xianghang Mi1, Siyuan Tang1, and Baojun Liu3 1Indiana University, Bloomington. fealowais, pw7, xliao, xw7, talowais, xm, [email protected] 2King Saud University, Riyadh, Saudi Arabia. [email protected] 3Tsinghua University, [email protected] Abstract—Take-down operations aim to disrupt cybercrime “clean”, i.e., no longer involved in any malicious activities. involving malicious domains. In the past decade, many successful Challenges in understanding domain take-downs. Although take-down operations have been reported, including those against the Conficker worm, and most recently, against VPNFilter. domain seizures are addressed in ICANN guidelines [55] Although it plays an important role in fighting cybercrime, the and in other public articles [14, 31, 38], there is a lack of domain take-down procedure is still surprisingly opaque. There prominent and comprehensive understanding of the process. seems to be no in-depth understanding about how the take-down In-depth exploration is of critical importance for combating operation works and whether there is due diligence to ensure its cybercrime but is by no means trivial. The domain take-down security and reliability. process is rather opaque and quite complicated. In particular, In this paper, we report the first systematic study on domain it involves several steps (complaint submission, take-down takedown. Our study was made possible via a large collection execution, and release, see SectionII). It also involves multiple of data, including various sinkhole feeds and blacklists, passive parties (authorities, registries, and registrars), and multiple DNS data spanning six years, and historical WHOIS informa- domain management elements (DNS, WHOIS, and registry tion. -

Department of Homeland Security Daily Open Source Infrastructure
Daily Open Source Infrastructure Report 15 May 2012 Top Stories • Three former General Electric Co. bankers were convicted May 11 of defrauding cities and the U.S. Internal Revenue Service in a bid-rigging scheme involving hundreds of millions of dollars in municipal bonds. – Bloomberg (See item 10) • Police arrested three high school students accused of setting a massive fire that destroyed part of a high school in Woodburn, Oregon. – Associated Press (See item 38) • DHS issued a bulletin May 10 warning about a previously undisclosed, critical vulnerability in Movicon 11, software used to manage machines used in the manufacturing, energy, and water sectors. – Threatpost (See item 52) • Sheriff’s detectives in Fresno County, California, arrested a man they believe is responsible for stealing miles of phone wire that caused phone service to cut out for many customers. – KSFN 30 Fresno (See item 54) • Authorities were trying to trace the source of a food-borne outbreak that sickened up to 150 people who attended a party and food fair at a Buddhist monastery in Carmel, New York. – Melville Newsday (See item 56) • Seven businesses in downtown Mariposa, California, burned to the ground the weekend of May 12 in a fire that caused about $1 million in structural damage. – Bellingham Herald (See item 60) • Firefighters battled several wildfires in Arizona, May 14, including one that was human- caused, more than 4.5 square miles in size, and forced residents from their homes. – Associated Press (See item 61) - 1 - Fast Jump Menu PRODUCTION INDUSTRIES -

Zerohack Zer0pwn Youranonnews Yevgeniy Anikin Yes Men
Zerohack Zer0Pwn YourAnonNews Yevgeniy Anikin Yes Men YamaTough Xtreme x-Leader xenu xen0nymous www.oem.com.mx www.nytimes.com/pages/world/asia/index.html www.informador.com.mx www.futuregov.asia www.cronica.com.mx www.asiapacificsecuritymagazine.com Worm Wolfy Withdrawal* WillyFoReal Wikileaks IRC 88.80.16.13/9999 IRC Channel WikiLeaks WiiSpellWhy whitekidney Wells Fargo weed WallRoad w0rmware Vulnerability Vladislav Khorokhorin Visa Inc. Virus Virgin Islands "Viewpointe Archive Services, LLC" Versability Verizon Venezuela Vegas Vatican City USB US Trust US Bankcorp Uruguay Uran0n unusedcrayon United Kingdom UnicormCr3w unfittoprint unelected.org UndisclosedAnon Ukraine UGNazi ua_musti_1905 U.S. Bankcorp TYLER Turkey trosec113 Trojan Horse Trojan Trivette TriCk Tribalzer0 Transnistria transaction Traitor traffic court Tradecraft Trade Secrets "Total System Services, Inc." Topiary Top Secret Tom Stracener TibitXimer Thumb Drive Thomson Reuters TheWikiBoat thepeoplescause the_infecti0n The Unknowns The UnderTaker The Syrian electronic army The Jokerhack Thailand ThaCosmo th3j35t3r testeux1 TEST Telecomix TehWongZ Teddy Bigglesworth TeaMp0isoN TeamHav0k Team Ghost Shell Team Digi7al tdl4 taxes TARP tango down Tampa Tammy Shapiro Taiwan Tabu T0x1c t0wN T.A.R.P. Syrian Electronic Army syndiv Symantec Corporation Switzerland Swingers Club SWIFT Sweden Swan SwaggSec Swagg Security "SunGard Data Systems, Inc." Stuxnet Stringer Streamroller Stole* Sterlok SteelAnne st0rm SQLi Spyware Spying Spydevilz Spy Camera Sposed Spook Spoofing Splendide -

North Dakota Homeland Security Anit-Terrorism Summary
UNCLASSIFIED NORTH DAKOTA HOMELAND SECURITY ANIT-TERRORISM SUMMARY The North Dakota Open Source Anti-Terrorism Summary is a product of the North Dakota State and Local Intelligence Center (NDSLIC). It provides open source news articles and information on terrorism, crime, and potential destructive or damaging acts of nature or unintentional acts. Articles are placed in the Anti-Terrorism Summary to provide situational awareness for local law enforcement, first responders, government officials, and private/public infrastructure owners. UNCLASSIFIED UNCLASSIFIED NDSLIC Disclaimer The Anti-Terrorism Summary is a non-commercial publication intended to educate and inform. Further reproduction or redistribution is subject to original copyright restrictions. NDSLIC provides no warranty of ownership of the copyright, or accuracy with respect to the original source material. QUICK LINKS North Dakota Energy Regional Food and Agriculture National Government Sector (including Schools and Universities) International Information Technology and Banking and Finance Industry Telecommunications Chemical and Hazardous Materials National Monuments and Icons Sector Postal and Shipping Commercial Facilities Public Health Communications Sector Transportation Critical Manufacturing Water and Dams Defense Industrial Base Sector North Dakota Homeland Security Emergency Services Contacts UNCLASSIFIED UNCLASSIFIED North Dakota Water project to provide high-quality water to NW ND. A $110 million pipeline project will bring high-quality drinking water to areas of northwest North Dakota that desperately need it, officials said May 15. The Western Area Water Supply Project pipeline between Crosby and Wildrose will bring high-quality, treated drinking water from the Missouri River to residents of Burke, Divide, McKenzie, Mountrail, and Williams counties where water quality is poor and in short supply. -

*CYBER CRIME Electronic 2012
2012/3 The South African Cyber Threat Barometer A strategic public-private partnership (PPP) initiative to combat cybercrime in SA. Foreword Africa is considered to be the cradle of mankind. There is evidence that some of the earliest people lived in southern Africa. The hunter-gatherer San roamed widely over the area and the pastoral KhoiKhoi wandered in the well- watered parts where grazing was available. Tribes from central Africa moved southwards into the eastern and central parts of the area known today as South Africa. Milestones in South African history: 1652 - Dutch Settlers arrive under the leadership of Jan van Riebeeck 1795 - British occupation of the Cape 1800 onwards - the Zulu kingdom under King Shaka rises to power 1835 - The Great Trek - Dutch and other settlers leave the Cape colony 1879 - Anglo-Zulu War 1880 - First Anglo-Boer War 1899 - Second Anglo-Boer War I am referring to the scourge of 1912 - The African National Congress (ANC) is founded cybercriminal activity that is rapidly 1961 - South Africa becomes a republic becoming a global concern and one 1990 - Mandela is freed after 27 years in prison and that we as Africans need to prioritise. opposition groups are unbanned We hope this project and proposed 1994 - South Africa's first democratic election initiatives will go a long way towards "rallying the troops" to urgently South Africa has journeyed through many great obstacles address the growing cyber threat facing to become a nation whose dream of unity and common our country. purpose is within grasp of all its people. We must not lose sight of this dream. -

Hacktivisten
HACKTIVISTEN Abschlussbericht zum Projektteil der Hellfeldbeforschung Bundeskriminalamt Kriminalistisches Institut Forschungs- und Beratungsstelle Cybercrime KI 16 0 Wendy Füllgraf KI 16 Forschungs- und Beratungsstelle Cybercrime Bundeskriminalamt 65173 Wiesbaden [email protected] 1 0 Abbildungsverzeichnis __________________________________________________ IV 1 Einleitung _____________________________________________________________ 1 2 Projektbeschreibung _____________________________________________________ 3 2.1 Hintergrund ____________________________________________________________ 3 2.2 Projektziele _____________________________________________________________ 3 3 Methoden _____________________________________________________________ 5 3.1 Angemessenheit der Methode am Forschungsgegenstand _______________________ 5 3.2 Sekundäranalyse ________________________________________________________ 6 3.2.1 Materialerhebung _____________________________________________________________ 6 3.2.2 Auswertung __________________________________________________________________ 8 3.3 Fallanalyse _____________________________________________________________ 9 3.3.1 Datenerhebung _______________________________________________________________ 9 3.3.2 Auswertung _________________________________________________________________ 12 3.4 Expertenarbeitstreffen___________________________________________________ 13 3.4.1 Inhalte und Ablauf ____________________________________________________________ 13 3.4.2 Phänomenbezug der Teilnehmer _________________________________________________ -
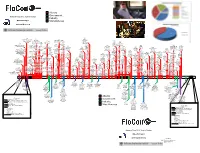
Network Flow 2012: Year in Review Industry @Geowarnagiris Miscellaneous [email protected]
Attacks Government Network Flow 2012: Year in Review Industry @GeoWarnagiris Miscellaneous [email protected] 6/7 1/17 2/4 4/1 Last.fm Justin Beiber’s web site 403 NASA Utah Dept. of Heath warns 40M hacked 200 accts 2/26 8/3 usernames and 500K personal records users to 8/9 dumped 2/10 UN (UNEP) Mat passwds posted 4/16 change pass Utah cia.gov DB leaked Honan’s 1/15 2/3 US Gov & LE computerized taken 3/31 digital life zappos.com customer Conf call re: Anon DDoS 6/6 1.5M 7/19 signs hacked 9/21 12/4 12/21 down 2/26 PBS hacked 4/29 destroyed details accessed between FBI and eHarmony $80K in Nike 8/21 USDA Swiss National Council on Wikileaks publishes 4/12 Yahoo and 5/28 9/18 10/25 Scotland Yard leaked passwd merchandise 8/9 Moscow defaced security agency Foreign 1/12 2/8 Stratfor emails 3/30 Another AOL email Flame 8/2 US Bank Israeli National 11/23 hashes stolen via Battle.net Court web warns of large Relations AlienVault releases Westboro Baptist 3/12 GlobalPayments FBI/MI6 breached announced MLB DDoSes network Some 2/2 dumped web site bug hacked site hacked 9/4 secret data leak poisoned details of Sykipot trojan taken down BBC announce call Facebook begin 9/26 disconnects GoDaddy Susan G. Komen for 5/26 Bitfloor 11/8 variant targeting 2/14 Persian breach 50k - leaked - 2 6/5 hijacked by Telvent 10/11 from civilian DNS hijacked 12/3 the Cure hacked U. -

A Case Study Analysis of Knightsec and the Steubenville Rape Case
2014 Proceedings of the Conference for Information Systems Applied Research ISSN: 2167-1508 Baltimore, Maryland USA v7 n3306 _________________________________________________ A Case Study Analysis of KnightSec and the Steubenville Rape Case William Stanley Pendergrass [email protected] School of Science, Technology, Engineering and Mathematics American Public University System Charles Town, WV 25414, United States of America Michelle Wright [email protected] Faculty of Social Studies Masaryk University Brno, 60200, Czech Republic Abstract The Anonymous hacktivist movement began in earnest in 2008 with Operation Chanology. Over the years and through various operations and through various factions, Anonymous has espoused freedom of information and become an advocate for individuals’ rights and protections. In late 2012, an Anonymous member KY Anonymous began a series of operations under the banner of KnightSec. These Justice Operations went after many individuals and groups but culminated with operations in support of a victim of a rape and against the rapists from Steubenville, Ohio. Using Case Study analysis of collected news articles, blogs, social media accounts and such, an analysis of the KnightSec movement was conducted. Though the movement eventually collapsed, valuable lessons of social media use by many participatory parties were concluded. Social media, an integral part of all actors in the events, was the facilitator for nearly all communications as well as archivist for all actions, legal, illegal and those in between. Keywords: KnightSec, Steubenville Rape Case, Anonymous, Operation RollRedRoll, Occupy Steubenville, Westboro Baptist Church, Trent Mays, Ma’lik Richmond 1. INTRODUCTION offline. They might even show acts of kindness and generosity (Wright & Li, 2011). -

The Day of the Cyber Wolf
Regis University ePublications at Regis University All Regis University Theses Fall 2014 The aD y of the Cyber Wolf Ryan K. Buch Regis University Follow this and additional works at: https://epublications.regis.edu/theses Part of the Criminology and Criminal Justice Commons Recommended Citation Buch, Ryan K., "The aD y of the Cyber Wolf" (2014). All Regis University Theses. 210. https://epublications.regis.edu/theses/210 This Thesis - Open Access is brought to you for free and open access by ePublications at Regis University. It has been accepted for inclusion in All Regis University Theses by an authorized administrator of ePublications at Regis University. For more information, please contact [email protected]. Regis University College for Professional Studies Graduate Programs Final Project/Thesis Disclaimer Use of the materials available in the Regis University Thesis Collection (“Collection”) is limited and restricted to those users who agree to comply with the following terms of use. Regis University reserves the right to deny access to the Collection to any person who violates these terms of use or who seeks to or does alter, avoid or supersede the functional conditions, restrictions and limitations of the Collection. The site may be used only for lawful purposes. The user is solely responsible for knowing and adhering to any and all applicable laws, rules, and regulations relating or pertaining to use of the Collection. All content in this Collection is owned by and subject to the exclusive control of Regis University and the authors of the materials. It is available only for research purposes and may not be used in violation of copyright laws or for unlawful purposes. -

Mcafee Threats Report: Second Quarter 2012
Report McAfee Threats Report: Second Quarter 2012 By McAfee Labs Table of Contents Mobile Threats 4 Malware Threats 6 Signed malware 10 Ransomware holds data hostage 12 Messaging Threats 12 Botnet Breakdowns 15 Spam Seeks to Deceive via social engineering 19 Network Threats 20 Web Threats 23 Cybercrime 27 Bulletproof hosting 27 Actions against cybercriminals 29 Hacktivism 30 About the Authors 31 About McAfee Labs 31 About McAfee 31 2 McAfee Threats Report: Second Quarter 2012 Laozi, often called Lao Tzu, was a philosopher of ancient China. Author of the Tao Te Ching, according to tradition he lived in the sixth century BCE yet his insights remain valuable today. Looking at the ever- evolving threats landscape, he might say “My mind tells me to give up, but my heart won’t let me.” The threat landscape is indeed a battlefield. Maybe Sunzi, also known as Sun Tzu and another philosopher of ancient China, said it best with “Invincibility lies in defense; the possibility of victory in the attack.” We have learned much about malware and various threats over the years but they seem to grow and reach new heights each quarter. Whether malware and other cyberthreats are successful depends on many interconnected factors. Sunzi also noted “He who is prudent and lies in wait for an enemy who is not will be victorious.” Sounds like the answer lies in preparedness. Looking at the second quarter of 2012, the key things that stood out were the emergence of mobile (Android) “drive-by downloads” as a new attack vector, the use of Twitter for control of mobile botnets, and the appearance of mobile “ransomware” as the newest way of extracting funds from unsuspecting victims. -

Book and Is Not Responsible for the Web: Content of the External Sources, Including External Websites Referenced in This Publication
2020 12th International Conference on Cyber Conflict 20/20 Vision: The Next Decade T. Jančárková, L. Lindström, M. Signoretti, I. Tolga, G. Visky (Eds.) 2020 12TH INTERNATIONAL CONFERENCE ON CYBER CONFLicT 20/20 VISION: THE NEXT DECADE Copyright © 2020 by NATO CCDCOE Publications. All rights reserved. IEEE Catalog Number: CFP2026N-PRT ISBN (print): 978-9949-9904-6-7 ISBN (pdf): 978-9949-9904-7-4 COPYRIGHT AND REPRINT PERMissiONS No part of this publication may be reprinted, reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior written permission of the NATO Cooperative Cyber Defence Centre of Excellence ([email protected]). This restriction does not apply to making digital or hard copies of this publication for internal use within NATO, or for personal or educational use when for non-profit or non-commercial purposes, providing that copies bear this notice and a full citation on the first page as follows: [Article author(s)], [full article title] 2020 12th International Conference on Cyber Conflict 20/20 Vision: The Next Decade T. Jančárková, L. Lindström, M. Signoretti, I. Tolga, G. Visky (Eds.) 2020 © NATO CCDCOE Publications NATO CCDCOE Publications LEGAL NOTICE: This publication contains the opinions of the respective authors only. They do not Filtri tee 12, 10132 Tallinn, Estonia necessarily reflect the policy or the opinion of NATO Phone: +372 717 6800 CCDCOE, NATO, or any agency or any government. NATO CCDCOE may not be held responsible for Fax: +372 717 6308 any loss or harm arising from the use of information E-mail: [email protected] contained in this book and is not responsible for the Web: www.ccdcoe.org content of the external sources, including external websites referenced in this publication.