*CYBER CRIME Electronic 2012
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Anchoring the African Internet Ecosystem
Anchoring the African Internet Ecosystem Anchoring the African Internet Ecosystem: Lessons from Kenya and Nigeria’s Internet Exchange Point Growth By Michael Kende June 2020 CC BY-NC-SA 4.0 internetsociety.org 1 Anchoring the African Internet Ecosystem Table of contents 3 Executive summary 6 Background: A vision for Africa 8 Introduction: How to get there from here 13 Success stories: Kenya and Nigeria today 18 Results that stand the test of time 20 Change factors: Replicable steps toward measurable outcomes 27 Market gaps 29 Recommendations 33 Conclusions 34 Annex A: Kenya Internet Exchange Point 35 Annex B: Internet Exchange Point of Nigeria 36 Annex C: Acknowledgments 37 Annex D: Glossary of terms 38 Annex E: List of figures and tables CC BY-NC-SA 4.0 internetsociety.org 2 Anchoring the African Internet Ecosystem Executive summary In 2010, the Internet Society’s team in Africa set an The rapid pace of Internet ecosystem ambitious goal that 80% of African Internet traffic development in both Kenya and Nigeria since would be locally accessible by 2020. 2012 underscores the critical role that IXPs Internet Exchange Points (IXPs) are key to realizing and the accompanying infrastructure play in this goal in that they enable local traffic exchange and the establishment of strong and sustainable access to content. To document this role, in 2012, the Internet ecosystems. Internet Society commissioned a study to identify and quantify the significant benefits of two leading African This development produces significant day-to-day IXPs at the time: KIXP in Kenya and IXPN in Nigeria. value—the present COVID-19 crisis magnifies one such The Internet Society is pleased to publish this update benefit in the smooth accommodation of sudden of the original study. -

الجريمة اإللكرتونية يف املجتمع الخليجي وكيفية مواجهتها Cybercrimes in the Gulf Society and How to Tackle Them
مسابقة جائزة اﻷمير نايف بن عبدالعزيز للبحوث اﻷمنية لعام )2015م( الجريمة اﻹلكرتونية يف املجتمع الخليجي وكيفية مواجهتها Cybercrimes in the Gulf Society and How to Tackle Them إعـــــداد رامـــــــــــــي وحـــــــــــــيـد مـنـصــــــــــور باحـــــــث إســـتراتيجي في الشــــــئون اﻷمـــنـــية واﻻقتصـــــــــاد الســــــــياسـي -1- أ ت جملس التعاون لدول اخلليج العربية. اﻷمانة العامة 10 ج إ الجريمة اﻹلكترونية في المجتمع الخليجي وكيفية مواجهتها= cybercrimes in the Gulf:Society and how to tackle them إعداد رامي وحيد منصور ، البحرين . ـ الرياض : جملس التعاون لدول اخلليج العربية ، اﻷمانة العامة؛ 2016م. 286 ص ؛ 24 سم الرقم املوحد ملطبوعات اجمللس : 0531 / 091 / ح / ك/ 2016م. اجلرائم اﻹلكرتونية / / جرائم املعلومات / / شبكات احلواسيب / / القوانني واللوائح / / اجملتمع / مكافحة اجلرائم / / اجلرائم احلاسوبية / / دول جملس التعاون لدول اخلليج العربية. -2- قائمة املحتويات قائمة احملتويات .......................................................................................................... 3 قائمــة اﻷشــكال ........................................................................................................10 مقدمــة الباحــث ........................................................................................................15 مقدمة الدراســة .........................................................................................................21 الفصل التمهيدي )اﻹطار النظري للدراسة( موضوع الدراســة ...................................................................................................... 29 إشــكاليات الدراســة ................................................................................................ -

Annual Meeting
Volume 97 | Number 5 Volume VOLUME 97 NOVEMBER 2017 NUMBER 5 SUPPLEMENT SIXTY-SIXTH ANNUAL MEETING November 5–9, 2017 The Baltimore Convention Center | Baltimore, Maryland USA The American Journal of Tropical Medicine and Hygiene The American Journal of Tropical astmh.org ajtmh.org #TropMed17 Supplement to The American Journal of Tropical Medicine and Hygiene ASTMH FP Cover 17.indd 1-3 10/11/17 1:48 PM Welcome to TropMed17, our yearly assembly for stimulating research, clinical advances, special lectures, guests and bonus events. Our keynote speaker this year is Dr. Paul Farmer, Co-founder and Chief Strategist of Partners In Health (PIH). In addition, Dr. Anthony Fauci, Director of the National Institute of Allergy and Infectious Diseases, will deliver a plenary session Thursday, November 9. Other highlighted speakers include Dr. Scott O’Neill, who will deliver the Fred L. Soper Lecture; Dr. Claudio F. Lanata, the Vincenzo Marcolongo Memorial Lecture; and Dr. Jane Cardosa, the Commemorative Fund Lecture. We are pleased to announce that this year’s offerings extend beyond communicating top-rated science to direct service to the global community and a number of novel events: • Get a Shot. Give a Shot.® Through Walgreens’ Get a Shot. Give a Shot.® campaign, you can not only receive your free flu shot, but also provide a lifesaving vaccine to a child in need via the UN Foundation’s Shot@Life campaign. • Under the Net. Walk in the shoes of a young girl living in a refugee camp through the virtual reality experience presented by UN Foundation’s Nothing But Nets campaign. -

Corporate Presentation
1 Contents Company snapshot 4 Macro overview 5 Redefining our strategy 8 Our growth potential 12 Financial highlights 28 FY 2020 highlights 34 2 Disclaimer This document has been prepared by Telecom Egypt (the “Company”) solely for the use at the analyst/investor presentation, held in connection with the Company. The information contained in this document has not been independently verified. This document contains statements related to our future business and financial performance and future events or developments involving Telecom Egypt that may constitute forward-looking statements. Such statements are based on the current expectations and certain assumptions of Telecom Egypt's management, of which many are beyond Telecom Egypt's control. Such assumptions are subject to a number of risks and uncertainties. Should any of these risks or uncertainties materialize, or should underlying expectations not occur or assumptions prove incorrect, actual results may (negatively or positively) vary materially from those described explicitly or implicitly in the relevant forward-looking statement. Telecom Egypt neither intends, nor assumes any obligation, to update or revise these forward-looking statements in light of developments, which differ from those anticipated. This document does not constitute an offer or invitation to sell or issue, or any solicitation of any offer to purchase or subscribe for, any shares of the Company and neither it nor any part of it shall form the basis of, or be relied upon in connection with, any contract or commitment whatsoever. This presentation has been made to you solely for information purposes and is subject to amendment. This presentation (or any part of it) may not be reproduced or redistributed, passed on, or the contents otherwise divulged, directly or indirectly, to any other person or published in whole or in part for any purpose without the prior written consent of the Company. -

Understanding and Analyzing Malicious Domain Take-Downs
Cracking the Wall of Confinement: Understanding and Analyzing Malicious Domain Take-downs Eihal Alowaisheq1,2, Peng Wang1, Sumayah Alrwais2, Xiaojing Liao1, XiaoFeng Wang1, Tasneem Alowaisheq1,2, Xianghang Mi1, Siyuan Tang1, and Baojun Liu3 1Indiana University, Bloomington. fealowais, pw7, xliao, xw7, talowais, xm, [email protected] 2King Saud University, Riyadh, Saudi Arabia. [email protected] 3Tsinghua University, [email protected] Abstract—Take-down operations aim to disrupt cybercrime “clean”, i.e., no longer involved in any malicious activities. involving malicious domains. In the past decade, many successful Challenges in understanding domain take-downs. Although take-down operations have been reported, including those against the Conficker worm, and most recently, against VPNFilter. domain seizures are addressed in ICANN guidelines [55] Although it plays an important role in fighting cybercrime, the and in other public articles [14, 31, 38], there is a lack of domain take-down procedure is still surprisingly opaque. There prominent and comprehensive understanding of the process. seems to be no in-depth understanding about how the take-down In-depth exploration is of critical importance for combating operation works and whether there is due diligence to ensure its cybercrime but is by no means trivial. The domain take-down security and reliability. process is rather opaque and quite complicated. In particular, In this paper, we report the first systematic study on domain it involves several steps (complaint submission, take-down takedown. Our study was made possible via a large collection execution, and release, see SectionII). It also involves multiple of data, including various sinkhole feeds and blacklists, passive parties (authorities, registries, and registrars), and multiple DNS data spanning six years, and historical WHOIS informa- domain management elements (DNS, WHOIS, and registry tion. -

Department of Homeland Security Daily Open Source Infrastructure
Daily Open Source Infrastructure Report 15 May 2012 Top Stories • Three former General Electric Co. bankers were convicted May 11 of defrauding cities and the U.S. Internal Revenue Service in a bid-rigging scheme involving hundreds of millions of dollars in municipal bonds. – Bloomberg (See item 10) • Police arrested three high school students accused of setting a massive fire that destroyed part of a high school in Woodburn, Oregon. – Associated Press (See item 38) • DHS issued a bulletin May 10 warning about a previously undisclosed, critical vulnerability in Movicon 11, software used to manage machines used in the manufacturing, energy, and water sectors. – Threatpost (See item 52) • Sheriff’s detectives in Fresno County, California, arrested a man they believe is responsible for stealing miles of phone wire that caused phone service to cut out for many customers. – KSFN 30 Fresno (See item 54) • Authorities were trying to trace the source of a food-borne outbreak that sickened up to 150 people who attended a party and food fair at a Buddhist monastery in Carmel, New York. – Melville Newsday (See item 56) • Seven businesses in downtown Mariposa, California, burned to the ground the weekend of May 12 in a fire that caused about $1 million in structural damage. – Bellingham Herald (See item 60) • Firefighters battled several wildfires in Arizona, May 14, including one that was human- caused, more than 4.5 square miles in size, and forced residents from their homes. – Associated Press (See item 61) - 1 - Fast Jump Menu PRODUCTION INDUSTRIES -

Trends in the Threat Landscape
Trends in the Threat Landscape Thad Mann, CISM, CISSP, CeH, PMP Cybersecurity Black Belt [email protected] , 336-339-7206, October 2013 © 2013 IBM Corporation © 2013 IBM Corporation Several critical security business issues resonate consistently across senior management, and have become the top security focus issues Maximize Develop & Enable Protect the Manage end to retain key Leverage effective Corporate & security end security security security across security Brand image investment personnel the business units Ensure Leverage tools Create optimal The security Avoid a company is and environment to Build a investments breach that getting best technologies secure security DNA & need to could have bang for buck that enable company and culture that support the significant for security limited staff to build a creates business & IT financial and spend & effectively program to security requirements approaches brand impacts integration address acquire mobility & security talent across the with IT/Risk business units projects cloud © 2013 IBM Corporation Vulnerabilities increase with emergence of new business models, new technologies and Big Data Adopting new business models and Exponentially growing and interconnected embracing new technologies and data digital universe Bring your Employees, 30 billion RFID 1 own IT customers, 1 billion tags (products, contractors, workers will passports, outsourcers be remote buildings and or mobile animals) 1 billion mobile 1 trillion connected Mobility Internet users Social business objects (cars, 30 -

Zerohack Zer0pwn Youranonnews Yevgeniy Anikin Yes Men
Zerohack Zer0Pwn YourAnonNews Yevgeniy Anikin Yes Men YamaTough Xtreme x-Leader xenu xen0nymous www.oem.com.mx www.nytimes.com/pages/world/asia/index.html www.informador.com.mx www.futuregov.asia www.cronica.com.mx www.asiapacificsecuritymagazine.com Worm Wolfy Withdrawal* WillyFoReal Wikileaks IRC 88.80.16.13/9999 IRC Channel WikiLeaks WiiSpellWhy whitekidney Wells Fargo weed WallRoad w0rmware Vulnerability Vladislav Khorokhorin Visa Inc. Virus Virgin Islands "Viewpointe Archive Services, LLC" Versability Verizon Venezuela Vegas Vatican City USB US Trust US Bankcorp Uruguay Uran0n unusedcrayon United Kingdom UnicormCr3w unfittoprint unelected.org UndisclosedAnon Ukraine UGNazi ua_musti_1905 U.S. Bankcorp TYLER Turkey trosec113 Trojan Horse Trojan Trivette TriCk Tribalzer0 Transnistria transaction Traitor traffic court Tradecraft Trade Secrets "Total System Services, Inc." Topiary Top Secret Tom Stracener TibitXimer Thumb Drive Thomson Reuters TheWikiBoat thepeoplescause the_infecti0n The Unknowns The UnderTaker The Syrian electronic army The Jokerhack Thailand ThaCosmo th3j35t3r testeux1 TEST Telecomix TehWongZ Teddy Bigglesworth TeaMp0isoN TeamHav0k Team Ghost Shell Team Digi7al tdl4 taxes TARP tango down Tampa Tammy Shapiro Taiwan Tabu T0x1c t0wN T.A.R.P. Syrian Electronic Army syndiv Symantec Corporation Switzerland Swingers Club SWIFT Sweden Swan SwaggSec Swagg Security "SunGard Data Systems, Inc." Stuxnet Stringer Streamroller Stole* Sterlok SteelAnne st0rm SQLi Spyware Spying Spydevilz Spy Camera Sposed Spook Spoofing Splendide -

North Dakota Homeland Security Anit-Terrorism Summary
UNCLASSIFIED NORTH DAKOTA HOMELAND SECURITY ANIT-TERRORISM SUMMARY The North Dakota Open Source Anti-Terrorism Summary is a product of the North Dakota State and Local Intelligence Center (NDSLIC). It provides open source news articles and information on terrorism, crime, and potential destructive or damaging acts of nature or unintentional acts. Articles are placed in the Anti-Terrorism Summary to provide situational awareness for local law enforcement, first responders, government officials, and private/public infrastructure owners. UNCLASSIFIED UNCLASSIFIED NDSLIC Disclaimer The Anti-Terrorism Summary is a non-commercial publication intended to educate and inform. Further reproduction or redistribution is subject to original copyright restrictions. NDSLIC provides no warranty of ownership of the copyright, or accuracy with respect to the original source material. QUICK LINKS North Dakota Energy Regional Food and Agriculture National Government Sector (including Schools and Universities) International Information Technology and Banking and Finance Industry Telecommunications Chemical and Hazardous Materials National Monuments and Icons Sector Postal and Shipping Commercial Facilities Public Health Communications Sector Transportation Critical Manufacturing Water and Dams Defense Industrial Base Sector North Dakota Homeland Security Emergency Services Contacts UNCLASSIFIED UNCLASSIFIED North Dakota Water project to provide high-quality water to NW ND. A $110 million pipeline project will bring high-quality drinking water to areas of northwest North Dakota that desperately need it, officials said May 15. The Western Area Water Supply Project pipeline between Crosby and Wildrose will bring high-quality, treated drinking water from the Missouri River to residents of Burke, Divide, McKenzie, Mountrail, and Williams counties where water quality is poor and in short supply. -
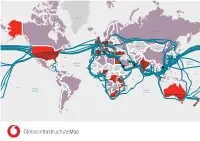
Global Infrastructure Map Switz
Greenland Iceland Sweden Russia Finland Faroe Is. Norway Estonia Latvia United Kingdom Denmark TEA Canada TEA Lanis-3 Lithuania ERA Lanis-2 Lanis-1 ERA Belarus TEA-3 Ireland Netherlands Concerto Poland Solas Germany TEA-3 Belgium Czech Rep. TEA-3 PC-1 Lux. EPEG Slovakia Ukraine PC-1 Tata TGN-Pacific GTT Atlantic Tata TGN-Pacific Tata TGN-Pacific GTT Atlantic HUGO Tata TGN-Pacific Liech. Moldova Kazakhstan Austria Trans-Pacific Express France Switz. Hungary Trans-Pacific Express FASTER Slovenia FASTER Romania Mongolia TEA Japan-U.S. Japan-U.S. Apollo Tata TGN- Croatia Western Europe PC-1 EPEG PC-1 Unity/EAC-Pacific Bos. & Herz. TEA Unity/EAC-Pacific Serbia Italy Mont. PC-1 TataTGN-Pacific FLAG Atlantic-1 Uzbekistan 2Africa Kos. Bulgaria FLAG Atlantic-1 Andorra Apollo Georgia AAE-1 Macedonia Kyrgyzstan EIG 2023 2023 IMEWE Hawk Albania Armenia Azerbaijan Portugal SeaMeWe-5 North 2Africa 2Africa SeaMeWe-3 Tata TGN-Western Europe TGN-Western Tata GLO-1 GLO-1 Europe India Gatway Gatway India Europe FLAG Europe-Asia FLAG SeaMeWe-4 Turkey Turkmenistan Greece Korea Spain MedNautilus VMSCS United States Tajikistan Japan-U.S. South EAC-C2C Korea Japan Malta MedNautilus Cyprus Syria Tunisia China Lebanon TEA TPE Afghanistan ERA SouthernHawaiki Cross WACS Iraq Iran Bermuda AAE-1 EIG Palestinian Terr. Japan-U.S. Morocco EPEG SAT-3/WASC TE North Israel Jordan TGN-Eurasia SEACOM Pakistan Alexandros Kuwait TPE Asia-America Gateway Nepal Japan-U.S. FALCON AJC Algeria TEA APCN-2 EAC-C2C Southern Cross Libya AAE-1 OMRAN/EPEG Bhutan Egypt Bahrain ASE/Cahaya Malaysia FOG Bahamas EIG Qatar FLAG/REACH NAL MENA/GBI EAC-C2C Pacific Bangladesh Mexico W. -

The State of Broadband 2020: Tackling Digital Inequalities a Decade for Action
The State of Broadband: Tackling digital inequalities A decade for action September 2020 The State of Broadband 2020: Tackling digital inequalities A decade for action September 2020 © International Telecommunication Union and United Nations Educational, Scientific and Cultural Organization, 2020 Some rights reserved. This work is available under the Creative Commons Attribution- NonCommercial-ShareAlike 3.0 IGO license (CC BY-NC-SA 3.0 IGO; https:// creativecommons .org/ licenses/ by -nc -sa/ 3 .0/ igo). Under the terms of this license, you may copy, redistribute and adapt the work for non-commercial purposes, provided the work is appropriately cited, as indicated below. In any use of this work, there should be no suggestion that ITU or UNESCO endorses any specific organization, products or services. The unauthorized use of the ITU or UNESCO names or logos is not permitted. If you adapt the work, then you must license your work under the same or equivalent Creative Commons license. If you create a translation of this work, you should add the following disclaimer along with the suggested citation: “This translation was not created by the International Telecommunication Union (ITU) or the United Nations Educational, Scientific and Cultural Organization (UNESCO). Neither ITU nor UNESCO are responsible for the content or accuracy of this translation. The original English edition shall be the binding and authentic edition”. Any mediation relating to disputes arising under the license shall be conducted in accordance with the mediation rules of the World Intellectual Property Organization (http:// www .wipo .int/ amc/ en/ mediation/ rules). Suggested citation. State of Broadband Report 2020: Geneva: International Telecommunication Union and United Nations Educational, Scientific and Cultural Organization, 2020. -

Hacktivisten
HACKTIVISTEN Abschlussbericht zum Projektteil der Hellfeldbeforschung Bundeskriminalamt Kriminalistisches Institut Forschungs- und Beratungsstelle Cybercrime KI 16 0 Wendy Füllgraf KI 16 Forschungs- und Beratungsstelle Cybercrime Bundeskriminalamt 65173 Wiesbaden [email protected] 1 0 Abbildungsverzeichnis __________________________________________________ IV 1 Einleitung _____________________________________________________________ 1 2 Projektbeschreibung _____________________________________________________ 3 2.1 Hintergrund ____________________________________________________________ 3 2.2 Projektziele _____________________________________________________________ 3 3 Methoden _____________________________________________________________ 5 3.1 Angemessenheit der Methode am Forschungsgegenstand _______________________ 5 3.2 Sekundäranalyse ________________________________________________________ 6 3.2.1 Materialerhebung _____________________________________________________________ 6 3.2.2 Auswertung __________________________________________________________________ 8 3.3 Fallanalyse _____________________________________________________________ 9 3.3.1 Datenerhebung _______________________________________________________________ 9 3.3.2 Auswertung _________________________________________________________________ 12 3.4 Expertenarbeitstreffen___________________________________________________ 13 3.4.1 Inhalte und Ablauf ____________________________________________________________ 13 3.4.2 Phänomenbezug der Teilnehmer _________________________________________________