BJMC IV SEM Course-XVII Social Media Social Networking Sites A
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Facilitating a Hybrid College-Level Course Using Microblogging: a Case Study
Facilitating a Hybrid College-level Course Using Microblogging: A Case Study A dissertation presented to the faculty of The Patton College of Education of Ohio University In partial fulfillment of the requirements for the degree Doctor of Philosophy Tian Luo August 2014 ©2014 Tian Luo. All Rights Reserved. 2 This dissertation titled Facilitating a Hybrid College-level Course Using Microblogging: A Case Study by TIAN LUO has been approved for the Department of Educational Studies and The Patton College of Education by David R. Moore Associate Professor of Instructional Technology Renée A. Middleton Dean, The Patton College of Education 3 Abstract LUO, TIAN, Ph.D., August 2014, Curriculum and Instruction, Instructional Technology Facilitating a Hybrid college-level Course Using Microblogging: A Case Study (290 pp.) Director of Dissertation: David R. Moore Social media has become an increasingly growing phenomenon that arouses mounting interest as well as heated discussion concerning its varied definitions and practices for academic use. Recently, a common type of social media, microblogging tools such as Twitter, has garnered researchers and educators' mounting attention due to its prevailing usage among the younger generation. This study seeks to both examine student learning in the Twitter-supported learning environments and to understand the potential factors affecting student perceptions and participation. The researcher incorporated three major Twitter-based instructional activities into a hybrid course, namely, Exploring Hashtags, Discussion Topics, and Live Chats. Twitter was employed as a backchannel to enhance classroom interaction during lectures and student presentations in face-to-face settings. The participants were 24 college-level Teacher Education program students enrolled in a technology course at a large Midwestern University. -

Social Media
What is Social media? Social media is defined as "a group of Internet-based applications that build on the ideological and technological foundations of the World Wide Web, and that allow the creation and exchange of user content.“ (Wikipedia 2014) What is Facebook? Facebook is a popular free social networking website that allows registered users to create profiles, upload photos and video, send messages and keep in touch with friends, family and colleagues.(Dean,A.2014) History on facebook Facebook was launched in February 2004. It was founded by Mark Zuckerberg his college roommates and fellow Harvard University student Eduardo Saverin. The website's membership was initially limited by the founders to Harvard students, but was expanded to other colleges in the Boston area. By September 2006, to everyone of age 13 and older to make a group with a valid email address. Reasons for using Facebook It is a medium of finding old friends(schoolmates..etc) It is a medium of advertising any business It is a medium of entertainment Sharing your photos and videos Connecting to love ones What makes Facebook popular? The adding of photos News feed The “Like” button Facebook messenger Relationship status Timeline Some hidden features of Facebook File transfer over FB chat See who is snooping in your account An inbox you didn’t know you have You Facebook romance* Save your post for later What is Twitter? Twitter is a service for friends, family, and coworkers to communicate and stay connected through the exchange of quick, frequent messages. People post Tweets, which may contain photos, videos, links and up to 140 characters of text. -

Title, Modify
Sentiment Analysis of Twitter Data for a Tourism Recommender System in Bangladesh Najeefa Nikhat Choudhury School of Science Thesis submitted for examination for the degree of Master of Science in Technology. Otaniemi 28.11.2016 Thesis supervisor: Assoc. Prof. Keijo Heljanko aalto university abstract of the school of science master’s thesis Author: Najeefa Nikhat Choudhury Title: Sentiment Analysis of Twitter Data for a Tourism Recommender System in Bangladesh Date: 28.11.2016 Language: English Number of pages: 8+65 Department of Computer Science Master’s Program in ICT Innovation Supervisor and advisor: Assoc. Prof. Keijo Heljanko The exponentially expanding Digital Universe is generating huge amount of data containing valuable information. The tourism industry, which is one of the fastest growing economic sectors, can benefit from the myriad of digital data travelers generate in every phase of their travel- planning, booking, traveling, feedback etc. One application of tourism related data can be to provide personalized destination recommendations. The primary objective of this research is to facilitate the business development of a tourism recommendation system for Bangladesh called “JatraLog”. Sentiment based recommendation is one of the features that will be employed in the recommendation system. This thesis aims to address two research goals: firstly, to study Sentiment Analysis as a tourism recommendation tool and secondly, to investigate twitter as a potential source of valuable tourism related data for providing recommendations for different countries, specifically Bangladesh. Sentiment Analysis can be defined as a Text Classification problem, where a document or text is classified into two groups: positive or negative, and in some cases a third group, i.e. -

ADL Report to Global Forum on Cyberhate 2015
Report of the Anti-Defamation League on Confronting Cyberhate 5th Global Forum for Combating Anti-Semitism May, 2015 ANTI-DEFAMATION LEAGUE Barry Curtiss-Lusher National Chair Abraham H. Foxman National Director Kenneth Jacobson Deputy National Director Milton S. Schneider President, Anti-Defamation League Foundation CIVIL RIGHTS DIVISION Christopher Wolf Chair Deborah M. Lauter Director Steven M. Freeman Associate Director Eva Vega-Olds Assistant Director Jonathan Vick Assistant Director, Cyberhate Response CENTER ON EXTREMISM Mitch Markow Chair Oren Segal Director Lauren Steinberg Terrorism Analyst For additional and updated resources please see: www.adl.org Copies of this publication are available in the Rita and Leo Greenland Library and Research Center. ©2015 Anti-Defamation League | Printed in the United States of America | All Rights Reserved Anti-Defamation League 605 Third Avenue, New York, NY 10158-3560 www.adl.org Table of Contents PREFACE .........................................................................................................................................................4 INTRODUCTION ..............................................................................................................................................5 CHARTING PROGRESS ....................................................................................................................................6 A NEW CHALLENGE: TERRORIST USE OF SOCIAL MEDIA ............................................................................11 RECOMMENDATIONS -

Mogućnosti Primjene Twitterovog Aplikacijskog Progamskog Sučelja
Mogućnosti primjene Twitterovog aplikacijskog progamskog sučelja Mance, Josip Master's thesis / Diplomski rad 2016 Degree Grantor / Ustanova koja je dodijelila akademski / stručni stupanj: Josip Juraj Strossmayer University of Osijek, Faculty of Electrical Engineering, Computer Science and Information Technology Osijek / Sveučilište Josipa Jurja Strossmayera u Osijeku, Fakultet elektrotehnike, računarstva i informacijskih tehnologija Osijek Permanent link / Trajna poveznica: https://urn.nsk.hr/urn:nbn:hr:200:039315 Rights / Prava: In copyright Download date / Datum preuzimanja: 2021-09-29 Repository / Repozitorij: Faculty of Electrical Engineering, Computer Science and Information Technology Osijek SVEUČILIŠTE JOSIPA JURJA STROSSMAYERA U OSIJEKU ELEKTROTEHNIČKI FAKULTET Sveučilišni studij MOGUĆNOSTI PRIMJENE TWITTEROVOG APLIKACIJSKOG PROGRAMSKOG SUČELJA Diplomski rad Josip Mance Osijek, 2016. godina Obrazac D1 Izjava o originalnosti Sadržaj 1. Uvod ............................................................................................................................................ 1 2. Aplikacijsko programsko sučelje ................................................................................................ 2 3. Društvene mreže.......................................................................................................................... 4 3.1. Twitter .................................................................................................................................. 6 3.1.1. Upotreba Twittera ........................................................................................................ -

Seamless Interoperability and Data Portability in the Social Web for Facilitating an Open and Heterogeneous Online Social Network Federation
Seamless Interoperability and Data Portability in the Social Web for Facilitating an Open and Heterogeneous Online Social Network Federation vorgelegt von Dipl.-Inform. Sebastian Jürg Göndör geb. in Duisburg von der Fakultät IV – Elektrotechnik und Informatik der Technischen Universität Berlin zur Erlangung des akademischen Grades Doktor der Ingenieurwissenschaften - Dr.-Ing. - genehmigte Dissertation Promotionsausschuss: Vorsitzender: Prof. Dr. Thomas Magedanz Gutachter: Prof. Dr. Axel Küpper Gutachter: Prof. Dr. Ulrik Schroeder Gutachter: Prof. Dr. Maurizio Marchese Tag der wissenschaftlichen Aussprache: 6. Juni 2018 Berlin 2018 iii A Bill of Rights for Users of the Social Web Authored by Joseph Smarr, Marc Canter, Robert Scoble, and Michael Arrington1 September 4, 2007 Preamble: There are already many who support the ideas laid out in this Bill of Rights, but we are actively seeking to grow the roster of those publicly backing the principles and approaches it outlines. That said, this Bill of Rights is not a document “carved in stone” (or written on paper). It is a blog post, and it is intended to spur conversation and debate, which will naturally lead to tweaks of the language. So, let’s get the dialogue going and get as many of the major stakeholders on board as we can! A Bill of Rights for Users of the Social Web We publicly assert that all users of the social web are entitled to certain fundamental rights, specifically: Ownership of their own personal information, including: • their own profile data • the list of people they are connected to • the activity stream of content they create; • Control of whether and how such personal information is shared with others; and • Freedom to grant persistent access to their personal information to trusted external sites. -

German Jewish Refugees in the United States and Relationships to Germany, 1938-1988
UNIVERSITY OF CALIFORNIA, SAN DIEGO “Germany on Their Minds”? German Jewish Refugees in the United States and Relationships to Germany, 1938-1988 A dissertation submitted in partial satisfaction of the requirements for the degree Doctor of Philosophy in History by Anne Clara Schenderlein Committee in charge: Professor Frank Biess, Co-Chair Professor Deborah Hertz, Co-Chair Professor Luis Alvarez Professor Hasia Diner Professor Amelia Glaser Professor Patrick H. Patterson 2014 Copyright Anne Clara Schenderlein, 2014 All rights reserved. The Dissertation of Anne Clara Schenderlein is approved, and it is acceptable in quality and form for publication on microfilm and electronically. _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ _____________________________________________________________________ Co-Chair _____________________________________________________________________ Co-Chair University of California, San Diego 2014 iii Dedication To my Mother and the Memory of my Father iv Table of Contents Signature Page ..................................................................................................................iii Dedication ..........................................................................................................................iv Table of Contents ...............................................................................................................v -
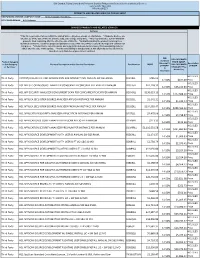
HCL Software's
IBM Branded, Fujistu Branded and Panasonic Branded Products and Related Services and Cloud Services Contract DIR-TSO-3999 PRICING SHEET PRODUCTS AND RELATED SERVICES PRICING SHEET RESPONDING VENDOR COMPANY NAME:____Sirius Computer Solutions_______________ PROPOSED BRAND:__HCL Software__________________________ BRANDED PRODUCTS AND RELATED SERVICES Software * This file is generated for use within the United States. All prices shown are US Dollars. * Products & prices are effective as of the date of this file and are subject to change at any time. * HCL may announce new or withdraw products from marketing after the effective date of this file. * Nothwithstanding the product list and prices identified on this file, customer proposals/quotations issued will reflect HCL's current offerings and commercial list prices. * Product list is not all inclusive and may not include products removed from availability (sale) or added after the date of this update. * Product availability is not guaranteed. Not all products listed below are found on every State/Local government contract. DIR DIR CUSTOMER Customer Product Category PRICE (MSRP- Discount % Description or SubCategory Product Description and/or Service Description Part Number MSRP DIR CUSTOMER off MSRP* of MSRP or Services* DISCOUNT Plus (2 Admin Fee) Decimals) HCL SLED Third Party CNTENT/COLLAB ACC AND WEBSPH PRTL SVR INTRANET PVU ANNUAL SW S&S RNWL E045KLL $786.02 14.50% $677.09 Price HCL SLED Third Party HCL APP SEC OPEN SOURCE ANALYZER CONSCAN PER CONCURRENT EVENT PER ANNUM D20H6LL $41,118.32 -

Monitoring Enterprise Collaboration Platform Change and the Building of Digital Transformation Capabilities
Monitoring Enterprise Collaboration Platform Change and the Building of Digital Transformation Capabilities: An Information Infrastructure Perspective by Clara Sabine Nitschke Approved Dissertation thesis for the partial fulfilment of the requirements for a Doctor of Economics and Social Sciences (Dr. rer. pol.) Fachbereich 4: Informatik Universität Koblenz-Landau Chair of PhD Board: Prof. Dr. Ralf Lämmel Chair of PhD Commission: Prof. Dr. Viorica Sofronie-Stokkermans Examiner and Supervisor: Prof. Dr. Susan P. Williams Further Examiners: Prof. Dr. Petra Schubert, Prof. Dr. Catherine A. Hardy Date of the doctoral viva: 28/07/2021 Acknowledgements Many thanks to all the people who supported me on my PhD journey, a life-changing experience. This work was funded by two research grants from the Deutsche Forschungsgemeinschaft (DFG). The related projects were designed as a joint work between two research groups at the University Koblenz-Landau. I am especially grateful to my supervisor Prof. Dr. Sue Williams who provided invaluable support throughout my whole project, particularly through her expertise, as well as her research impulses and discussions. Still, she gave me the freedom to shape my research, so many thanks! Further, I would like to thank my co-advisor Prof. Dr. Petra Schubert for very constructive feedback through the years. I am thankful for having had the unique opportunity to be part of the Center for Enterprise Information Research (CEIR) team with excellent researchers and the IndustryConnect initiative, which helped me bridge the gap between academia and ‘real world’ cases. IndustryConnect, founded by Prof. Dr. Schubert and Prof. Dr. Williams, enabled me to participate in long-term practice-oriented research with industry, a privilege that most other doctoral students cannot enjoy. -

Last 24Th of July, the New York Times Published a Story on a New
New trends on international communication The Rotary Club of Newport-Balboa, Corona del Mar, CA, 92625 September, 23, 2009, Teresa La Porte Assistant Professor of International Political Communication . Last July 24th 2008, the New York Times published a story on a new communication strategy started by Hamas, the Islamic fundamentalist group of Palestine. The headlines said: “Hamas shifts from rockets to culture war”. And latter explains: “Hamas has suspended its use of rockets and shifted focus to winning support at home and abroad through cultural initiatives and public relations”. After describing some of the events organized with that purpose (such as a theater play, a movie premiere, a presentation of a book of poems), the New York Times highlights a statement of the minister of culture from Gaza (Osama Alisawi): “We are not terrorists but resistance fighters, and we want to explain our reality to the outside world. We want the writers and intellectuals of the world to come and see how people are suffering on a daily basis”. I do not know yet what the reaction of other countries was, but at least in Spain, only some days later from this story, main newspapers brought out a report on Palestine children trying to get a Guinness Award. The challenge was to fly simultaneously the largest number of kites ever: pictures showed a beach, packed with young Palestinians trying to fly three thousand kites. Although nobody from Guinness World Records was there to register the event, the strategy set by Hamas had achieved it first hit being present in Spanish front pages with a different image. -

Leveraging the Israeli Diaspora in the US
Conceptual Framework for the ILC's Potential Leadership Role Leveraging the Israeli Diaspora in the US Final Draft for Comments Submitted to ILC Management and Board Kislev 5772 December 2011 1 November, 2011 Table of Contents Executive Summary ........................................................................................................ 2 Guidelines for Quick Reading ....................................................................................... 4 Background and Introduction ....................................................................................... 5 Part 1: The ILC’s Playing Field: Changes taking place among the Israeli Diaspora .......................................................................................................................................... 7 Background: Jewish Peoplehood is taking center stage - The changing relations between Israel and the Jewish world ............................................................................ 7 Major trends affecting the Israeli Diaspora: the current mindset ............................. 8 Major Trends affecting the Israeli Diaspora: the changing reality ......................... 10 The emergence of a new type of identity: The Israeli ‘New Tipus’ ......................... 12 Development of 'New Tipus' identity .......................................................................... 13 Who is the ‘New Tipus’? .............................................................................................. 16 The potential of the 'New Tipus' towards -

Social Media & Audience Participation in Regard to Television
The University of Akron IdeaExchange@UAkron The Dr. Gary B. and Pamela S. Williams Honors Honors Research Projects College Spring 2015 Social Media & Audience Participation in Regard to Television Jean Marie McBride The University Of Akron, [email protected] Please take a moment to share how this work helps you through this survey. Your feedback will be important as we plan further development of our repository. Follow this and additional works at: http://ideaexchange.uakron.edu/honors_research_projects Part of the Communication Technology and New Media Commons, Social Media Commons, and the Television Commons Recommended Citation McBride, Jean Marie, "Social Media & Audience Participation in Regard to Television" (2015). Honors Research Projects. 120. http://ideaexchange.uakron.edu/honors_research_projects/120 This Honors Research Project is brought to you for free and open access by The Dr. Gary B. and Pamela S. Williams Honors College at IdeaExchange@UAkron, the institutional repository of The nivU ersity of Akron in Akron, Ohio, USA. It has been accepted for inclusion in Honors Research Projects by an authorized administrator of IdeaExchange@UAkron. For more information, please contact [email protected], [email protected]. Social Media & Audience Participation in Regard to Television: Jean McBride 1 Social Media & Audience Participation in Regard to Television: Jean McBride Introduction Social media has been on the rise for years. From Twitter and Facebook, to Pinterest and Instagram, the social media world has grown. Originally, social media was used for teenagers’ enjoyment; however, in recent years broadcasters have jumped on the social media bandwagon, and used social media to “innovatively enhance consumer engagement, traditional marketing campaigns and promotions” (Benedict, 2013, p.1).