Identifier System Attack Mitigation Methodology DATE: 13 February 2017 Identifier System Attack Mitigation Methodology
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ethereum Based Domain Name System Using Smart Contracts
ETHEREUM BASED DOMAIN NAME SYSTEM USING SMART CONTRACTS (BC-DNS) A Project Presented to the faculty of the Department of Computer Science California State University, Sacramento Submitted in partial satisfaction of the requirements for the degree of MASTER OF SCIENCE in Computer Science by Rodney Pinto SPRING 2019 © 2019 Rodney Pinto ALL RIGHTS RESERVED ii ETHEREUM BASED DOMAIN NAME SYSTEM USING SMART CONTRACTS (BC-DNS) A Project by Rodney Pinto Approved by: __________________________________, Committee Chair Dr. Jun Dai. __________________________________, Second Reader Dr. Xuyu Wang. ____________________________ Date iii Student: Rodney Pinto I certify that this student has met the requirements for format contained in the university format manual, and that this project is suitable for shelving in the library and credit is to be awarded for the project. __________________________, Graduate Coordinator ____________________ Dr. Jinsong Ouyang, Ph.D. Date Department of Computer Science iv Abstract of ETHEREUM BASED DOMAIN NAME SYSTEM USING SMART CONTRACTS (BC-DNS) by Rodney Pinto One of the most critical resources that ensure the current working of the internet is the domain name system (DNS). It is a decentralized, hierarchical naming system that is responsible for translating the human-readable domain name to its associated IP address. The use of DNS thus eliminates the need for humans to remember the IP address of all their favorite websites (such as 172.217.6.68 an IPV4 address for google.com). Despite its widespread use, DNS is vulnerable to various security issues. This project focuses on replicating the basic functionality of the existing DNS on the blockchain and deploying it on a peer to peer network making it completely decentralized and, in the process, make it a bit more secure and reliable by addressing few of the security vulnerabilities of the existing system. -

ICANN, Ipv6 and the Root
ICANN, IPv6 and the Root John L. Crain Chief Technical Officer Beijing, China April 12, 2007 1 12 APRIL 2007 In the beginning . 2 12 APRIL 2007 Internet’s unique identifiers were coordinated through the Internet Address Naming Authority JonJon PostelPostel 19431943––19981998 3 12 APRIL 2007 Need for change circa 1996–97 • Globalisation of Internet • Commercialisation of Internet • Lack of competition in domain name space • Trademark–domain name conflicts • Need for a new model of governance 4 12 APRIL 2007 ICANN mission statement • To coordinate, overall, the global Internet's system of unique identifiers, and to ensure stable and secure operation of the Internet's unique identifier systems. In particular, ICANN coordinates: 1. Allocation and assignment of the three sets of unique identifiers for the Internet: • Domain names (forming a system called the DNS) • Internet protocol (IP) addresses and autonomous system (AS) numbers • Protocol port and parameter numbers 2. Operation and evolution of the DNS root name server system 3. Policy development reasonably and appropriately related to these technical functions 5 12 APRIL 2007 Principles of operation 1. Contribute to stability and security of the unique identifiers system and root management 2. Promote competition and choice for registrants and other users 3. Forum for multi-stakeholder bottom-up development of related policy 4. Ensuring on a global basis an opportunity for participation by all interested parties 6 12 APRIL 2007 The Secretariat (People doing the day to day work) 58 Staff from 26 Countries 7 12 APRIL 2007 • The secretariat’s work is administration and aiding policy processes. • We do not set policy, that is the job of the community. -

Thesis That TW-OR Forwards All DNS Queries to a Resolver in China
The Impact of DNSSEC on the Internet Landscape Von der Fakult¨atf¨urIngenieurwissenschaften, Abteilung Informatik und Angewandte Kognitionswissenschaft der Universit¨atDuisburg-Essen zur Erlangung des akademischen Grades Doktor der Ingenieurwissenschaften genehmigte Dissertation von Matth¨ausWander aus Lubin (L¨uben) Gutachter: Prof. Dr.-Ing. Torben Weis Prof. Dr.-Ing. Felix Freiling Tag der m¨undlichen Pr¨ufung:19. Juni 2015 Abstract In this dissertation we investigate the security deficiencies of the Domain Name System (DNS) and assess the impact of the DNSSEC security extensions. DNS spoofing attacks divert an application to the wrong server, but are also used routinely for blocking access to websites. We provide evidence for systematic DNS spoofing in China and Iran with measurement-based analyses, which allow us to examine the DNS spoofing filters from van- tage points outside of the affected networks. Third-parties in other countries can be affected inadvertently by spoofing-based domain filtering, which could be averted with DNSSEC. The security goals of DNSSEC are data integrity and authenticity. A point solution called NSEC3 adds a privacy assertion to DNSSEC, which is supposed to prevent disclosure of the domain namespace as a whole. We present GPU-based attacks on the NSEC3 privacy assertion, which allow efficient recovery of the namespace contents. We demonstrate with active measurements that DNSSEC has found wide adoption after initial hesitation. At server-side, there are more than five million domains signed with DNSSEC. A portion of them is insecure due to insufficient cryptographic key lengths or broken due to maintenance failures. At client-side, we have observed a worldwide increase of DNSSEC validation over the last three years, though not necessarily on the last mile. -

CS4700/CS5700 Fundamentals of Computer Networks
CS4700/CS5700 Fundamentals of Computer Networks Lecture 17: Domain Name System Slides used with permissions from Edward W. Knightly, T. S. Eugene Ng, Ion Stoica, Hui Zhang Alan Mislove amislove at ccs.neu.edu Northeastern1 University Human Involvement • Just like your friend needs to tell you his phone number for you to call him • Somehow, an application needs to know the IP address of the communication peer • There is no magic, some out-of-band mechanism is needed – Word of mouth – Read it in the advertisement in the paper – Etc. • But IP addresses are bad for humans to remember and tell each other • So need names that makes some sense to humans Alan Mislove amislove at ccs.neu.edu Northeastern2 University Internet Names & Addresses • Names: e.g. www.rice.edu – human-usable labels for machines – conforms to “organizational” structure • Addresses: e.g. 128.42.247.150 – router-usable labels for machines – conforms to “network” structure • How do you map from one to another? – Domain Name System (DNS) Alan Mislove amislove at ccs.neu.edu Northeastern3 University DNS: History • Initially all host-addess mappings were in a file called hosts.txt (in /etc/hosts) – Changes were submitted to SRI by email – New versions of hosts.txt ftp’d periodically from SRI – An administrator could pick names at their discretion – Any name is allowed: eugenesdesktopatrice • As the Internet grew this system broke down because: – SRI couldn’t handled the load – Hard to enforce uniqueness of names – Many hosts had inaccurate copies of hosts.txt • Domain Name System (DNS) was born Alan Mislove amislove at ccs.neu.edu Northeastern4 University Basic DNS Features • Hierarchical namespace – as opposed to original flat namespace • Distributed storage architecture – as opposed to centralized storage (plus replication) • Client--server interaction on UDP Port 53 – but can use TCP if desired Alan Mislove amislove at ccs.neu.edu Northeastern5 University Naming Hierarchy root edu com gov mil org net uk fr etc. -

DNS) Deployment Guide
Archived NIST Technical Series Publication The attached publication has been archived (withdrawn), and is provided solely for historical purposes. It may have been superseded by another publication (indicated below). Archived Publication Series/Number: NIST Special Publication 800-81 Revision 1 Title: Secure Domain Name System (DNS) Deployment Guide Publication Date(s): April 2010 Withdrawal Date: September 2013 Withdrawal Note: SP 800-81 Revision 1 is superseded in its entirety by the publication of SP 800-81-2 (September 2013). Superseding Publication(s) The attached publication has been superseded by the following publication(s): Series/Number: NIST Special Publication 800-81-2 Title: Secure Domain Name System (DNS) Deployment Guide Author(s): Ramaswamy Chandramouli, Scott Rose Publication Date(s): September 2013 URL/DOI: http://dx.doi.org/10.6028/NIST.SP.800-81-2 Additional Information (if applicable) Contact: Computer Security Division (Information Technology Lab) Latest revision of the SP 800-81-2 (as of August 7, 2015) attached publication: Related information: http://csrc.nist.gov/ Withdrawal N/A announcement (link): Date updated: ƵŐƵƐƚϳ, 2015 Special Publication 800-81r1 Sponsored by the Department of Homeland Security Secure Domain Name System (DNS) Deployment Guide Recommendations of the National Institute of Standards and Technology Ramaswamy Chandramouli Scott Rose i NIST Special Publication 800-81r1 Secure Domain Name System (DNS) Deployment Guide Sponsored by the Department of Homeland Security Recommendations of the National Institute of Standards and Technology Ramaswamy Chandramouli Scott Rose C O M P U T E R S E C U R I T Y Computer Security Division/Advanced Network Technologies Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899 April 2010 U.S. -

DNS: Domain Name System a Scalable Naming System for the Internet
Introduction Queries and Caching Protocol History and Growth DNS: Domain Name System A Scalable Naming System for the Internet Daniel Zappala Brigham Young University Computer Science Department 1/26 Introduction Introduction Queries and Caching Protocol History and Growth Domain Name System • people like to use names for computers (www.byu.edu), but computers need to use numbers (128.187.22.132) • the Domain Name System (DNS) is a distributed database providing this service • a program send a query a local name server • the local name server contacts other servers as needed • many DNS services • host name to IP address translation • host aliasing (canonical name versus alias names) • lookup mail server for a host • load distribution - can provide a set of IP addresses for one canonical name Demonstration: dig 3/26 Introduction Queries and Caching Protocol History and Growth Names • domain name: top-level domain (TLD) + one or more subdomains • example: cs.byu.edu • host name: a domain name with one or more IP addresses associated with it • TLDs • ccTLD: country codes (.us, .uk, .tv) • gTLD: generic (.com, .edu, .org, .net, .gov, .mil) { see full list at Wikipedia • iTLD: infrastructure (.arpa) • may be 127 levels deep, 63 characters per label, 255 characters per name 4/26 Introduction Queries and Caching Protocol History and Growth DNS Hierarchy • root, top-level domain (TLD), and local name servers • each level represents a zone • what zone is BYU in charge of? 5/26 Introduction Queries and Caching Protocol History and Growth Root Name -

Blockchain, Iot and DNS
Domain Name Registrar Blockchain, IoT and DNS ICANN64 Tech Day Kobe, Japan Tom Barrett EnCirca President About EnCirca Domain Name Registrar • Formed in 2001 in Boston, USA • ICANN Accredited Registrar • Specialty: Partnering with TLD Registries • Restricted and regulated TLDs • White-labelled Storefronts for DotBrand and regulated registries • Validation Provider for .BANK and six other TLDs • Blockchain integration with .LUXE, XYZ Why Do We Care? Domain Name Registrar The blockchain and the Internet of Things (IoT) are two of the most transformative technologies in the world today. “Blockchain technology is probably the best invention since the internet itself” IoT Investments Domain Name Registrar Blockchain Investments Domain Name Registrar Blockchain and IoT Domain Name Registrar • Both need DNS to work. • Both need features not present in today’s DNS • Alternative frameworks and protocols are emerging to address the limitations of the DNS • Will DNS advance to meet this challenge? • What role will ICANN play in this space? A World Exploding with Devices Domain Name Registrar IoT Defined Domain Name Registrar Connect physical things to communication networks with a special focus on: • Existing infrastructure (buildings, roads, vehicles, factory equipment, etc.) and • Constrained devices with extremely limited computing resources (switches, valves, sensors, actuators, thermostats, etc.) Blockchain Defined Domain Name Registrar • An open, distributed ledger that can record transactions between two parties efficiently and in a verifiable and permanent way • A growing list of records, called blocks, are linked using cryptography • Typically managed by a peer-to-peer network • Data in any block cannot be altered retroactively without alteration of all subsequent blocks Blockchain Benefits Domain Name Registrar • You have complete control of the value you own; there is no third party that holds your value or can limit your access to it. -

Analyzing and Mitigating Privacy with the DNS Root Service
Analyzing and Mitigating Privacy with the DNS Root Service Wes Hardaker USC/Information Sciences Institute [email protected] Keywords privacy, dns, root, analysis, leakage ABSTRACT Processing of all DNS requests start at the root of the DNS tree and make use of either cached data from previous re- quests, or by traversing the DNS tree for the missing in- formation. When QNAME minimization is not in use, queries forwarded to the parental nodes in the DNS tree may leak private DNS query data. In this paper we examine 31 days during the month of January 2017 of queries sent from two recursive resolvers placed in two residential networks to the DNS root server operated by USC/ISI’s, analyzing Figure 1: Domain Name System Resolution Process the leaked QNAMEs for an impact on the network’s privacy. We then compare a few DNS privacy preserving techniques against the privacy analysis against these networks. Finally, client query. The architecture of this query process is we introduce a new solution called\LocalRoot" that enables depicted in Figure 1. The leakage of DNS requests to users to entirely mitigate privacy concerns when interacting the Root Server System is the focus point of this paper. with the DNS root server system, while other solutions fail Most DNS recursive resolvers today send the entire to completely protect users from all privacy analysis meth- requested DNS name (e.g. www.example.com) unen- ods. crypted to all the servers it needs to correspond with, as it is unknown to them where in the name the dif- 1. -

Wow, That's a Lot of Packets
Wow, That’s a Lot of Packets Duane Wessels, Marina Fomenkov Abstract—Organizations operating Root DNS servers re- an authoritative answer. If the application does not know port loads exceeding 100 million queries per day. Given the where to send a query it asks the servers in the parent design goals of the DNS, and what we know about today’s In- zone. In the example above, not knowing anything about ternet, this number is about two orders of magnitude more ucsd.edu, the application should send a query to the au- than we would expect. thoritative server for the edu zone. If the application does With the assistance of one root server operator, we took a edu 24-hour trace of queries arriving at one of the thirteen root not know about the zone, it queries the “root zone.” servers. In this paper we analyze these data and use a simple This process is called recursive iteration. model of the DNS to classify each query into one of nine cat- The DNS root zone is served by 13 name servers (not to egories. We find that, by far, most of the queries are repeats be confused with the 13 generic top-level domain servers) and that only a small percentage are legitimate. distributed across the globe. Thirteen is the maximum We also characterize a few of the “root server abusers,” number of root servers possible in the current DNS archi- that is, clients sending a particularly large number of tecture because that is the most that can fit inside a 512- queries to the root server. -
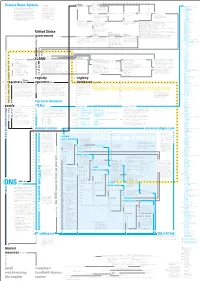
Domain Name System Concept
8 originally chartered standards charters 0 Concept Map organizations include ISoc members form 243 active ccTLDs Domain Name System rely on .ac Ascension Island (licensed) 28 Internet Society (ISoc) is a professional .ad Andorra A concept map is a web of terms. Verbs membership society with more than 150 This diagram is a model of the Domain .ae United Arab Emirates connect nouns to form propositions. organizations and 11,000 individual mem- .af Afghanistan 27 Name System (DNS), a system vital to the Groups of propositions form larger struc- bers from over 182 countries. tures. Examples and details accompany .ag Antigua and Barbuda smooth operation of the Internet. The goal most terms. More important terms re- .ai Anguilla of the diagram is to explain what DNS ceive visual emphasis; less important 11 .al Albania terms, details, and examples are in gray. IETF sponsors working groups are managed by IESG decisions can be appealed to IAB provides advice to IANA functions were moved to .am Armenia is, how it works, and how it’s governed. Terms related to names and addresses write approves .an Netherlands Antilles The diagram knits together many facts (the heart of DNS) are in blue. Terms Internet Engineering Task Force (IETF) Internet Engineering Steering Internet Architecture Board (IAB) Internet Assigned Numbers .ao Angola followed by a number link to terms pre- is a voluntary, non-commercial organization Group (IESG) Authority (IANA) originally handled .aq Antarctica about DNS in hopes of presenting a com- ceded by the same number. comprised of individuals concerned with the many of the functions that are now 626,000 .ar Argentina prehensive picture of the system and the evolution of the architecture and operation ICANN’s responsibility. -

SAC 045 – Invalid Top Level Domain Queries at the Root Level
Invalid Top Level Domain Queries at the Root Level of the Domain Name System SAC 045 Invalid Top Level Domain Queries at the Root Level of the Domain Name System A Report from the ICANN Security and Stability Advisory Committee (SSAC) 15 November 2010 SAC045 1 This document contains corrections to footnote 2 on page 6 and Section 8.1 Acknowledgements on page 10 Invalid Top Level Domain Queries at the Root Level of the Domain Name System Preface This is a report by the Security and Stability Advisory Committee (SSAC) on invalid Top Level Domain (TLD) queries at the root level of the domain name system (DNS). The report calls attention to the potential problems that may arise should a new TLD applicant use a string that has been seen with measurable (and meaningful) frequency in a query for resolution by the root system and the root system has previously generated a response. The SSAC advises the ICANN community and Board on matters relating to the security and integrity of the Internet's naming and address allocation systems. This includes operational matters (e.g., matters pertaining to the correct and reliable operation of the root name system), administrative matters (e.g., matters pertaining to address allocation and Internet number assignment), and registration matters (e.g., matters pertaining to registry and registrar services such as WHOIS). SSAC engages in ongoing threat assessment and risk analysis of the Internet naming and address allocation services to assess where the principal threats to stability and security lie, and advises the ICANN community accordingly. -

Retrait Effectif Ou Pluralisation Contrôlée?
UNIVERSITÉ DU QUÉBEC À MONTRÉAL RETRAlT EFFECTIF OU PLURALISATION CONTRÔLÉE? ANALYSE CRITIQUE DE LA STRATÉGIE DE LÉGITIMATION DE L'AUTORITÉ DU GOUVERNEMENT AMÉRICAIN DANS LA GOUVERNANCE POLITIQUE DU SYSTÈME DE NOMS DE DOMAINES D'INTERNET (DNS) MÉMOIRE PRÉSENTÉ COMME EXIGENCE PARTIELLE DE LA MAÎTRISE EN SCIENCE POLITIQUE PAR OLIVIER DAGENAIS JUILLET 2016 UNIVERSITÉ DU QUÉBEC À MONTRÉAL Service des bibliothèques Avertissement La diffusion de ce mémoire se fait dans le respect des droits de son auteur, qui a signé le formulaire Autorisation de reproduire et de diffuser un travail de recherche de cycles supérieurs (SDU-522 - Rév.1 0-2015). Cette autorisation stipule que «conformément à l'article 11 du Règlement no 8 des études de cycles supérieurs, [l 'auteur] concède à l'Université du Québec à Montréal une licence non exclusive d'utilisation et de publication de la totalité ou d'une partie importante de [son] travail de recherche pour des fins pédagogiques et non commerciales. Plus précisément, [l'auteur] autorise l'Université du Québec à Montréal à reproduire , diffuser, prêter, distribuer ou vendre des copies de [son] travail de recherche à des fins non commerciales sur quelque support que ce soit, y compris l'Internet. Cette licence et cette autorisation n'entraînent pas une renonciation de [la] part [de l'auteur] à [ses] droits moraux ni à [ses] droits de propriété intellectuelle. Sauf entente contraire, [l'auteur] conserve la liberté de diffuser et de commercialiser ou non ce travail dont [il] possède un exemplaire. » REMERCIEMENTS Quelqu'un m'a dit il n'y a pas si longremps que terminer un mémoire était un peu comme un accouchement, à la d ifférence près qu'une fo is te rminé, on n'avai t jam ais le goût de revoir le nouveau-né de notre vie.