Wow, That's a Lot of Packets
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Internet Governance Project
International internet Policy Priorities United States Department of Commerce, National Telecommunications and Information Administration (NTIA) [Docket No. 180124068–8068–01] RIN 0660–XC041 The Internet Governance Project (IGP) is a group of professors, postdoctoral researchers and students hosted at the Georgia Institute of Technology’s School of Public Policy. We conduct scholarly research, produce policy analyses and commentary on events in Internet governance, and bring our ideas and proposals directly into Internet governance processes. We also educate professionals and young people about Internet governance in various world regions. IGP welcomes NTIA’s broadly focused NOI on “International Internet Policy Priorities.” We believe that agency is asking many of the right questions and appreciate its desire to look for guidance from the public. Our response will follow the template of the NOI. I. THE FREE FLOW OF INFORMATION AND JURISDICTION A. What are the challenges to the free flow of information online? There are two distinct challenges to the free flow of information. The biggest and most fundamental is alignment,1 which is related to the issue of jurisdiction. Alignment refers to the attempt by national governments to assert sovereignty over cyberspace, by imposing exclusive territorial jurisdiction and national controls in a globally interoperable cyberspace. Data localization is one obvious example of a policy that seeks to achieve alignment, but the process is evident in multiple domains of Internet governance: in cybersecurity policy, trade policy, intellectual property protection and content regulation. In each case states erect barriers that 1 The concept of alignment was described in the book Will the Internet Fragment? (Polity Press, 2017). -

ICANN, Ipv6 and the Root
ICANN, IPv6 and the Root John L. Crain Chief Technical Officer Beijing, China April 12, 2007 1 12 APRIL 2007 In the beginning . 2 12 APRIL 2007 Internet’s unique identifiers were coordinated through the Internet Address Naming Authority JonJon PostelPostel 19431943––19981998 3 12 APRIL 2007 Need for change circa 1996–97 • Globalisation of Internet • Commercialisation of Internet • Lack of competition in domain name space • Trademark–domain name conflicts • Need for a new model of governance 4 12 APRIL 2007 ICANN mission statement • To coordinate, overall, the global Internet's system of unique identifiers, and to ensure stable and secure operation of the Internet's unique identifier systems. In particular, ICANN coordinates: 1. Allocation and assignment of the three sets of unique identifiers for the Internet: • Domain names (forming a system called the DNS) • Internet protocol (IP) addresses and autonomous system (AS) numbers • Protocol port and parameter numbers 2. Operation and evolution of the DNS root name server system 3. Policy development reasonably and appropriately related to these technical functions 5 12 APRIL 2007 Principles of operation 1. Contribute to stability and security of the unique identifiers system and root management 2. Promote competition and choice for registrants and other users 3. Forum for multi-stakeholder bottom-up development of related policy 4. Ensuring on a global basis an opportunity for participation by all interested parties 6 12 APRIL 2007 The Secretariat (People doing the day to day work) 58 Staff from 26 Countries 7 12 APRIL 2007 • The secretariat’s work is administration and aiding policy processes. • We do not set policy, that is the job of the community. -

L-Root and Internet in LAC Mauricio Vergara Ereche | Qos Internet CEPAL | Oct 2015 Agenda
L-Root and Internet in LAC Mauricio Vergara Ereche | QoS Internet CEPAL | Oct 2015 Agenda 1 2 3 What is L-Root LAC ICANN? Connectivity 4 5 Our model for Recommend deployment ations | 2 What is ICANN? What is a resilient and secure Internet? Quick Look at ICANN Overview ICANN is a global multi-stakeholder, private sector organization that manages Internet resources for the public benefit. It is best known for its role as technical coordinator of the Internet’s Domain Name System Mission To coordinate, at the overall level, the global Internet’s system of unique identifiers, and in particular to ensure the stable and secure operation of the Internet’s unique identifier system | 4 Supporting A Healthy, Resilient Internet | 5 SSR: Security, Stability and Resiliency Secure 1 Capacity to protect and prevent misuse of Internet Unique identifiers Stable Capacity to ensure that the system operates as expected, 2 and that users of the unique identifiers have confidence that the system operates as expected Resilient Capacity of the unique identifier system to effectively 3 withstand/tolerate/survive malicious attacks and other disruptive events without disruption or cessation of service | 6 L-Root DNS and Anycasting How DNS Works? Root Server 2 www.icann.org ? 1 3 4 8 .ORG Server 5 DNS Resolver (ISP) 6 9 7 www.icann.org ICANN.ORG Server | 8 What is L-Root? “L” is one of 13 independently operated root servers serving the DNS root zone ICANN DNS Engineering team operates L under the Autonomous System Number (ASN) AS20144 using the following -

Domain Name System 1 Domain Name System
Domain Name System 1 Domain Name System The Domain Name System (DNS) is a hierarchical distributed naming system for computers, services, or any resource connected to the Internet or a private network. It associates various information with domain names assigned to each of the participating entities. A Domain Name Service translates queries for domain names (which are easier to understand and utilize when accessing the internet) into IP addresses for the purpose of locating computer services and devices worldwide. An often-used analogy to explain the Domain Name System is that it serves as the phone book for the Internet by translating human-friendly computer hostnames into IP addresses. For example, the domain name www.example.com translates to the addresses 192.0.43.10 (IPv4) and 2620:0:2d0:200::10 (IPv6). The Domain Name System makes it possible to assign domain names to groups of Internet resources and users in a meaningful way, independent of each entity's physical location. Because of this, World Wide Web (WWW) hyperlinks and Internet contact information can remain consistent and constant even if the current Internet routing arrangements change or the participant uses a mobile device. Internet domain names are easier to remember than IP addresses such as 208.77.188.166 (IPv4) or 2001:db8:1f70::999:de8:7648:6e8 (IPv6). Users take advantage of this when they recite meaningful Uniform Resource Locators (URLs) and e-mail addresses without having to know how the computer actually locates them. The Domain Name System distributes the responsibility of assigning domain names and mapping those names to IP addresses by designating authoritative name servers for each domain. -

Identifier System Attack Mitigation Methodology DATE: 13 February 2017 Identifier System Attack Mitigation Methodology
Identifier System Attack Mitigation Methodology DATE: 13 February 2017 Identifier System Attack Mitigation Methodology Introduction This document is part of ICANN’s effort to contribute to enhancing the Stability, Security, and Resiliency (SSR) of the Internet’s system of unique identifiers (“Internet Identifiers”) by working with the Community to identify and increase awareness of related attacks and to promote broader adoption of attack mitigation practices. This effort also addresses Recommendation #12 of the Security, Stability & Resiliency (SSR) Review Team (SSR-RT) by creating an Identifier System Attack Mitigation Methodology. Specifically, this document identifies and prioritizes types of attacks against the Identifier System, providing a stepping-off point for ICANN to coordinate with the Community to develop a series of short technical documents (“Tech Notes”) on actual high-impact attacks and emerging high-risk vulnerabilities. This document will be periodically updated to reflect evolution of both the Identifier System and the cybercrime landscape, supporting on-going efforts within both ICANN and the Community to mitigate attacks that pose the greatest risk to Identifier System SSR. Authors: Lisa Phifer and David Piscitello Page 1 Identifier System Attack Mitigation Methodology DATE: 13 February 2017 Attack Mitigation Methodology ICANN is proposing a new Identifier System Attack Mitigation Methodology to: • Identify, prioritize, and periodically refresh a list of top Identifier System attacks; • Develop guidance on actual high-impact attacks and emerging high-risk vulnerabilities; • Describe corresponding attack mitigation practices that are commonly considered useful; and • Encourage broader adoption of those practices via contracts, agreements, incentives, etc. This document represents the first component of this methodology. -

Thesis That TW-OR Forwards All DNS Queries to a Resolver in China
The Impact of DNSSEC on the Internet Landscape Von der Fakult¨atf¨urIngenieurwissenschaften, Abteilung Informatik und Angewandte Kognitionswissenschaft der Universit¨atDuisburg-Essen zur Erlangung des akademischen Grades Doktor der Ingenieurwissenschaften genehmigte Dissertation von Matth¨ausWander aus Lubin (L¨uben) Gutachter: Prof. Dr.-Ing. Torben Weis Prof. Dr.-Ing. Felix Freiling Tag der m¨undlichen Pr¨ufung:19. Juni 2015 Abstract In this dissertation we investigate the security deficiencies of the Domain Name System (DNS) and assess the impact of the DNSSEC security extensions. DNS spoofing attacks divert an application to the wrong server, but are also used routinely for blocking access to websites. We provide evidence for systematic DNS spoofing in China and Iran with measurement-based analyses, which allow us to examine the DNS spoofing filters from van- tage points outside of the affected networks. Third-parties in other countries can be affected inadvertently by spoofing-based domain filtering, which could be averted with DNSSEC. The security goals of DNSSEC are data integrity and authenticity. A point solution called NSEC3 adds a privacy assertion to DNSSEC, which is supposed to prevent disclosure of the domain namespace as a whole. We present GPU-based attacks on the NSEC3 privacy assertion, which allow efficient recovery of the namespace contents. We demonstrate with active measurements that DNSSEC has found wide adoption after initial hesitation. At server-side, there are more than five million domains signed with DNSSEC. A portion of them is insecure due to insufficient cryptographic key lengths or broken due to maintenance failures. At client-side, we have observed a worldwide increase of DNSSEC validation over the last three years, though not necessarily on the last mile. -

CS4700/CS5700 Fundamentals of Computer Networks
CS4700/CS5700 Fundamentals of Computer Networks Lecture 17: Domain Name System Slides used with permissions from Edward W. Knightly, T. S. Eugene Ng, Ion Stoica, Hui Zhang Alan Mislove amislove at ccs.neu.edu Northeastern1 University Human Involvement • Just like your friend needs to tell you his phone number for you to call him • Somehow, an application needs to know the IP address of the communication peer • There is no magic, some out-of-band mechanism is needed – Word of mouth – Read it in the advertisement in the paper – Etc. • But IP addresses are bad for humans to remember and tell each other • So need names that makes some sense to humans Alan Mislove amislove at ccs.neu.edu Northeastern2 University Internet Names & Addresses • Names: e.g. www.rice.edu – human-usable labels for machines – conforms to “organizational” structure • Addresses: e.g. 128.42.247.150 – router-usable labels for machines – conforms to “network” structure • How do you map from one to another? – Domain Name System (DNS) Alan Mislove amislove at ccs.neu.edu Northeastern3 University DNS: History • Initially all host-addess mappings were in a file called hosts.txt (in /etc/hosts) – Changes were submitted to SRI by email – New versions of hosts.txt ftp’d periodically from SRI – An administrator could pick names at their discretion – Any name is allowed: eugenesdesktopatrice • As the Internet grew this system broke down because: – SRI couldn’t handled the load – Hard to enforce uniqueness of names – Many hosts had inaccurate copies of hosts.txt • Domain Name System (DNS) was born Alan Mislove amislove at ccs.neu.edu Northeastern4 University Basic DNS Features • Hierarchical namespace – as opposed to original flat namespace • Distributed storage architecture – as opposed to centralized storage (plus replication) • Client--server interaction on UDP Port 53 – but can use TCP if desired Alan Mislove amislove at ccs.neu.edu Northeastern5 University Naming Hierarchy root edu com gov mil org net uk fr etc. -

DNS) Deployment Guide
Archived NIST Technical Series Publication The attached publication has been archived (withdrawn), and is provided solely for historical purposes. It may have been superseded by another publication (indicated below). Archived Publication Series/Number: NIST Special Publication 800-81 Revision 1 Title: Secure Domain Name System (DNS) Deployment Guide Publication Date(s): April 2010 Withdrawal Date: September 2013 Withdrawal Note: SP 800-81 Revision 1 is superseded in its entirety by the publication of SP 800-81-2 (September 2013). Superseding Publication(s) The attached publication has been superseded by the following publication(s): Series/Number: NIST Special Publication 800-81-2 Title: Secure Domain Name System (DNS) Deployment Guide Author(s): Ramaswamy Chandramouli, Scott Rose Publication Date(s): September 2013 URL/DOI: http://dx.doi.org/10.6028/NIST.SP.800-81-2 Additional Information (if applicable) Contact: Computer Security Division (Information Technology Lab) Latest revision of the SP 800-81-2 (as of August 7, 2015) attached publication: Related information: http://csrc.nist.gov/ Withdrawal N/A announcement (link): Date updated: ƵŐƵƐƚϳ, 2015 Special Publication 800-81r1 Sponsored by the Department of Homeland Security Secure Domain Name System (DNS) Deployment Guide Recommendations of the National Institute of Standards and Technology Ramaswamy Chandramouli Scott Rose i NIST Special Publication 800-81r1 Secure Domain Name System (DNS) Deployment Guide Sponsored by the Department of Homeland Security Recommendations of the National Institute of Standards and Technology Ramaswamy Chandramouli Scott Rose C O M P U T E R S E C U R I T Y Computer Security Division/Advanced Network Technologies Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899 April 2010 U.S. -

DNS Performance – a Study of Free, Public and Popular DNS Servers in 2019
Linköping University | Department of Computer and Information Science Bachelor’s thesis, 16 ECTS | Informationsteknologi 2019 | LIU-IDA/LITH-EX-G--19/037--SE DNS Performance – A study of free, public and popular DNS servers in 2019 DNS prestanda – En studie av gratis, publika och populära DNS servrar år 2019 Filip Ström Felix Zedén Yverås Supervisor : Niklas Carlsson Examiner : Marcus Bendtsen Linköpings universitet SE–581 83 Linköping +46 13 28 10 00 , www.liu.se Upphovsrätt Detta dokument hålls tillgängligt på Internet - eller dess framtida ersättare - under 25 år från publicer- ingsdatum under förutsättning att inga extraordinära omständigheter uppstår. Tillgång till dokumentet innebär tillstånd för var och en att läsa, ladda ner, skriva ut enstaka ko- pior för enskilt bruk och att använda det oförändrat för ickekommersiell forskning och för undervis- ning. Överföring av upphovsrätten vid en senare tidpunkt kan inte upphäva detta tillstånd. All annan användning av dokumentet kräver upphovsmannens medgivande. För att garantera äktheten, säker- heten och tillgängligheten finns lösningar av teknisk och administrativ art. Upphovsmannens ideella rätt innefattar rätt att bli nämnd som upphovsman i den omfattning som god sed kräver vid användning av dokumentet på ovan beskrivna sätt samt skydd mot att dok- umentet ändras eller presenteras i sådan form eller i sådant sammanhang som är kränkande för up- phovsmannens litterära eller konstnärliga anseende eller egenart. För ytterligare information om Linköping University Electronic Press se förlagets hemsida http://www.ep.liu.se/. Copyright The publishers will keep this document online on the Internet - or its possible replacement - for a period of 25 years starting from the date of publication barring exceptional circumstances. -

DNS: Domain Name System a Scalable Naming System for the Internet
Introduction Queries and Caching Protocol History and Growth DNS: Domain Name System A Scalable Naming System for the Internet Daniel Zappala Brigham Young University Computer Science Department 1/26 Introduction Introduction Queries and Caching Protocol History and Growth Domain Name System • people like to use names for computers (www.byu.edu), but computers need to use numbers (128.187.22.132) • the Domain Name System (DNS) is a distributed database providing this service • a program send a query a local name server • the local name server contacts other servers as needed • many DNS services • host name to IP address translation • host aliasing (canonical name versus alias names) • lookup mail server for a host • load distribution - can provide a set of IP addresses for one canonical name Demonstration: dig 3/26 Introduction Queries and Caching Protocol History and Growth Names • domain name: top-level domain (TLD) + one or more subdomains • example: cs.byu.edu • host name: a domain name with one or more IP addresses associated with it • TLDs • ccTLD: country codes (.us, .uk, .tv) • gTLD: generic (.com, .edu, .org, .net, .gov, .mil) { see full list at Wikipedia • iTLD: infrastructure (.arpa) • may be 127 levels deep, 63 characters per label, 255 characters per name 4/26 Introduction Queries and Caching Protocol History and Growth DNS Hierarchy • root, top-level domain (TLD), and local name servers • each level represents a zone • what zone is BYU in charge of? 5/26 Introduction Queries and Caching Protocol History and Growth Root Name -

Analyzing and Mitigating Privacy with the DNS Root Service
Analyzing and Mitigating Privacy with the DNS Root Service Wes Hardaker USC/Information Sciences Institute [email protected] Keywords privacy, dns, root, analysis, leakage ABSTRACT Processing of all DNS requests start at the root of the DNS tree and make use of either cached data from previous re- quests, or by traversing the DNS tree for the missing in- formation. When QNAME minimization is not in use, queries forwarded to the parental nodes in the DNS tree may leak private DNS query data. In this paper we examine 31 days during the month of January 2017 of queries sent from two recursive resolvers placed in two residential networks to the DNS root server operated by USC/ISI’s, analyzing Figure 1: Domain Name System Resolution Process the leaked QNAMEs for an impact on the network’s privacy. We then compare a few DNS privacy preserving techniques against the privacy analysis against these networks. Finally, client query. The architecture of this query process is we introduce a new solution called\LocalRoot" that enables depicted in Figure 1. The leakage of DNS requests to users to entirely mitigate privacy concerns when interacting the Root Server System is the focus point of this paper. with the DNS root server system, while other solutions fail Most DNS recursive resolvers today send the entire to completely protect users from all privacy analysis meth- requested DNS name (e.g. www.example.com) unen- ods. crypted to all the servers it needs to correspond with, as it is unknown to them where in the name the dif- 1. -
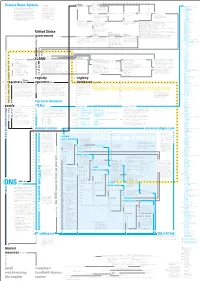
Domain Name System Concept
8 originally chartered standards charters 0 Concept Map organizations include ISoc members form 243 active ccTLDs Domain Name System rely on .ac Ascension Island (licensed) 28 Internet Society (ISoc) is a professional .ad Andorra A concept map is a web of terms. Verbs membership society with more than 150 This diagram is a model of the Domain .ae United Arab Emirates connect nouns to form propositions. organizations and 11,000 individual mem- .af Afghanistan 27 Name System (DNS), a system vital to the Groups of propositions form larger struc- bers from over 182 countries. tures. Examples and details accompany .ag Antigua and Barbuda smooth operation of the Internet. The goal most terms. More important terms re- .ai Anguilla of the diagram is to explain what DNS ceive visual emphasis; less important 11 .al Albania terms, details, and examples are in gray. IETF sponsors working groups are managed by IESG decisions can be appealed to IAB provides advice to IANA functions were moved to .am Armenia is, how it works, and how it’s governed. Terms related to names and addresses write approves .an Netherlands Antilles The diagram knits together many facts (the heart of DNS) are in blue. Terms Internet Engineering Task Force (IETF) Internet Engineering Steering Internet Architecture Board (IAB) Internet Assigned Numbers .ao Angola followed by a number link to terms pre- is a voluntary, non-commercial organization Group (IESG) Authority (IANA) originally handled .aq Antarctica about DNS in hopes of presenting a com- ceded by the same number. comprised of individuals concerned with the many of the functions that are now 626,000 .ar Argentina prehensive picture of the system and the evolution of the architecture and operation ICANN’s responsibility.