The MISRA C Coding Standard: a Key Enabler for the Development of Safety- and Security-Critical Embedded Software
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Language Subsetting in an Industrial Context: a Comparison of MISRA C 1998 and MISRA C 2004
Language subsetting in an industrial context: a comparison of MISRA C 1998 and MISRA C 2004 Les Hatton CISM, University of Kingston∗ November 20, 2005 Abstract The MISRA C standard [7] first appeared in 1998 with the objective of providing a set of guidelines to restrict features in the ISO C language of known undefined or otherwise dangerous behaviour. The standard was assembled by representatives of a number of companies in the automobile sector in response to the rapidly growing use of C in electronic embedded systems in automobiles. The standard attempts to build on the earlier work of [6], [3] and others. Due to various perceived deficiencies, notably considerable ambiguity in the rule definitions, a revision was planned and eventually appeared in 2004. This paper measures how well the two stan- dards compare on the same population of software and also determines how well the 2004 version achieved its stated goals. Given its increasing influence, the results raise important concerns. Keywords: safer subsets, MISRA C, embedded control systems 1 Overview Pragmatic safer subsetting of languages to remove dependence on poorly defined features is finally becoming a mainstream activity with the recent recommen- dation to form a high-integrity study group under the auspices of the ISO, [8] with the intention of producing sets of rules to restrict features with undefined or otherwise dangerous behaviour in programming languages in common use. It frequently comes as a surprise to developers that significant parts of a pro- gramming language can fall into this category. In practice, all standardised programming languages contain problematic features for a variety of reasons which include the inability of the standardising committee to agree on the be- haviour of a particular feature, the use of unintentionally ambiguous language in the standards document itself, omitting to say anything at all and so on. -

Introduction to Embedded C
INTRODUCTION TO EMBEDDED C by Peter J. Vidler Introduction The aim of this course is to teach software development skills, using the C programming language. C is an old language, but one that is still widely used, especially in embedded systems, where it is valued as a high- level language that provides simple access to hardware. Learning C also helps us to learn general software development, as many of the newer languages have borrowed from its concepts and syntax in their design. Course Structure and Materials This document is intended to form the basis of a self-study course that provides a simple introduction to C as it is used in embedded systems. It introduces some of the key features of the C language, before moving on to some more advanced features such as pointers and memory allocation. Throughout this document we will also look at exercises of varying length and difficulty, which you should attempt before continuing. To help with this we will be using the free RapidiTTy® Lite IDE and targeting the TTE®32 microprocessor core, primarily using a cycle-accurate simulator. If you have access to an FPGA development board, such as the Altera® DE2-70, then you will be able to try your code out in hardware. In addition to this document, you may wish to use a textbook, such as “C in a Nutshell”. Note that these books — while useful and well written — will rarely cover C as it is used in embedded systems, and so will differ from this course in some areas. Copyright © 2010, TTE Systems Limited 1 Getting Started with RapidiTTy Lite RapidiTTy Lite is a professional IDE capable of assisting in the development of high- reliability embedded systems. -

Embedded C Programming I (Ecprogrami)
To our customers, Old Company Name in Catalogs and Other Documents On April 1st, 2010, NEC Electronics Corporation merged with Renesas Technology Corporation, and Renesas Electronics Corporation took over all the business of both companies. Therefore, although the old company name remains in this document, it is a valid Renesas Electronics document. We appreciate your understanding. Renesas Electronics website: http://www.renesas.com April 1st, 2010 Renesas Electronics Corporation Issued by: Renesas Electronics Corporation (http://www.renesas.com) Send any inquiries to http://www.renesas.com/inquiry. Notice 1. All information included in this document is current as of the date this document is issued. Such information, however, is subject to change without any prior notice. Before purchasing or using any Renesas Electronics products listed herein, please confirm the latest product information with a Renesas Electronics sales office. Also, please pay regular and careful attention to additional and different information to be disclosed by Renesas Electronics such as that disclosed through our website. 2. Renesas Electronics does not assume any liability for infringement of patents, copyrights, or other intellectual property rights of third parties by or arising from the use of Renesas Electronics products or technical information described in this document. No license, express, implied or otherwise, is granted hereby under any patents, copyrights or other intellectual property rights of Renesas Electronics or others. 3. You should not alter, modify, copy, or otherwise misappropriate any Renesas Electronics product, whether in whole or in part. 4. Descriptions of circuits, software and other related information in this document are provided only to illustrate the operation of semiconductor products and application examples. -

Porting Musl to the M3 Microkernel TU Dresden
Porting Musl to the M3 microkernel TU Dresden Sherif Abdalazim, Nils Asmussen May 8, 2018 Contents 1 Abstract 2 2 Introduction 3 2.1 Background.............................. 3 2.2 M3................................... 4 3 Picking a C library 5 3.1 C libraries design factors . 5 3.2 Alternative C libraries . 5 4 Porting Musl 7 4.1 M3andMuslbuildsystems ..................... 7 4.1.1 Scons ............................. 7 4.1.2 GNUAutotools........................ 7 4.1.3 Integrating Autotools with Scons . 8 4.2 Repositoryconfiguration. 8 4.3 Compilation.............................. 8 4.4 Testing ................................ 9 4.4.1 Syscalls ............................ 9 5 Evaluation 10 5.1 PortingBusyboxcoreutils . 10 6 Conclusion 12 1 Chapter 1 Abstract Today’s processing workloads require the usage of heterogeneous multiproces- sors to utilize the benefits of specialized processors and accelerators. This has, in turn, motivated new Operating System (OS) designs to manage these het- erogeneous processors and accelerators systematically. M3 [9] is an OS following the microkernel approach. M3 uses a hardware/- software co-design to exploit the heterogeneous systems in a seamless and effi- cient form. It achieves that by abstracting the heterogeneity of the cores via a Data Transfer Unit (DTU). The DTU abstracts the heterogeneity of the cores and accelerators so that they can communicate systematically. I have been working to enhance the programming environment in M3 by porting a C library to M3. I have evaluated different C library implementations like the GNU C Library (glibc), Musl, and uClibc. I decided to port Musl as it has a relatively small code base with fewer configurations. It is simpler to port, and it started to gain more ground in embedded systems which are also a perfect match for M3 applications. -

MISRA-C Subset of the C Language for Critical Systems SAFETY-CRITICAL SYSTEMS
MISRA-C Subset of the C language for critical systems SAFETY-CRITICAL SYSTEMS System is safety-critical if people might die due to software bugs Examples Automobile stability / traction control Medical automation Many military applications You develop safety-critical software differently from non-critical software MISRA-C MISRA – Motor Industry Software Reliability Association Their bright idea: Can’t avoid C But can force developers to avoid features of C that are known to be problematic Some language flaws Some legitimate features that happen to be bad for embedded software Most of MISRA-C is just good common sense for any C programmer TERMINOLOGY Execution error: Something illegal done by a program Out-of-bounds array reference Divide by zero Uninitialized variable usage Trapped execution error: Immediately results in exception or program termination Untrapped execution error: Program keeps running But may fail in an unexpected way later on E.g., due to corrupted RAM In C, operations with undefined behavior are not trapped SAFETY A safe language does not allow untrapped execution errors A statically safe language catches all execution errors at compile time Useful languages can’t be completely statically safe Java is dynamically safe C and C++ are very unsafe MISRA C is not safe either However, adherence to MISRA-C can largely be statically checked This eliminates or reduces the likelihood of some kinds of untrapped execution errors MISRA-C RULE 1.2 No reliance shall be placed on undefined or unspecified behavior. Lots of things in C have undefined behavior Divide by zero Out-of-bounds memory access Signed integer overflow Lots of things in C have implementation-defined and unspecified behavior printf (“a”) + printf (“b”); Both of these hard to detect at compile time, in general Implementation-defined behavior is fine in MISRA-C Why? MISRA-C RULE 5.2 Identifiers in an inner scope shall not use the same name as an identifier in an outer scope, and therefore hide that identifier. -

Crosscore Embedded Studio 2.2.0 C/C++ Compiler Manual for SHARC
CrossCore Embedded Studio 2.2.0 C/C++ Compiler Manual for SHARC Processors Revision 1.5, February 2016 Part Number 82-100117-01 Analog Devices, Inc. One Technology Way Norwood, MA 02062-9106 Copyright Information ©2016 Analog Devices, Inc., ALL RIGHTS RESERVED. This document may not be reproduced in any form without prior, express written consent from Analog Devices, Inc. Printed in the USA. Disclaimer Analog Devices, Inc. reserves the right to change this product without prior notice. Information furnished by Ana- log Devices is believed to be accurate and reliable. However, no responsibility is assumed by Analog Devices for its use; nor for any infringement of patents or other rights of third parties which may result from its use. No license is granted by implication or otherwise under the patent rights of Analog Devices, Inc. Trademark and Service Mark Notice The Analog Devices logo, Blackfin, CrossCore, EngineerZone, EZ-Board, EZ-KIT, EZ-KIT Lite, EZ-Extender, SHARC, and VisualDSP++ are registered trademarks of Analog Devices, Inc. Blackfin+, SHARC+, and EZ-KIT Mini are trademarks of Analog Devices, Inc. All other brand and product names are trademarks or service marks of their respective owners. CrossCore Embedded Studio 2.2.0 i Contents Preface Purpose of This Manual................................................................................................................................. 1±1 Intended Audience........................................................................................................................................ -

MISRA-C:2004 Guidelines for the Use of the C Language in Critical Systems
MISRA-C:2004 Guidelines for the use of the C language in critical systems October 2004 Licensed to: Tyler Doering. 10 Sep 2008. Copy 1 of 1 First published October 2004 by MIRA Limited Watling Street Nuneaton Warwickshire CV10 0TU UK www.misra-c.com Edition 2 reprinted July 2008 incorporating Technical Corrigendum 1 © MIRA Limited, 2004, 2008. “MISRA”, “MISRA C” and the triangle logo are registered trademarks of MIRA Limited, held on behalf of the MISRA Consortium. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical or photocopying, recording or otherwise without the prior written permission of the Publisher. ISBN 978-0-9524156-2-6 paperback ISBN 978-0-9524156-4-0 PDF Printed by Hobbs the Printers Ltd British Library Cataloguing in Publication Data. A catalogue record for this book is available from the British Library This copy of MISRA-C:2004 - Guidelines for the use of the C language in critical systems is issued to Tyler Doering. The file must not be altered in any way. No permission is given for distribution of this file. This includes but is not exclusively limited to making the copy available to others by email, placing it on a server for access by intra- or inter-net, or by printing and distributing hardcopies. Any such use constitutes an infringement of copyright. MISRA gives no guarantees about the accuracy of the information contained in this PDF version of the Guidelines. The published paper document should be taken as authoritative. -

Evaluation of Open Source Operating Systems for Safety-Critical Applications Master’S Thesis in Embedded Electronic System Design
Evaluation of open source operating systems for safety-critical applications Master’s thesis in Embedded Electronic System Design Petter Sainio Berntsson Department of Computer Science and Engineering CHALMERS UNIVERSITY OF TECHNOLOGY UNIVERSITY OF GOTHENBURG Gothenburg, Sweden 2017 MASTER’S THESIS 2017 Evaluation of open source operating systems for Safety-critical applications Petter Sainio Berntsson Department of Computer Science and Engineering Chalmers University of Technology University of Gothenburg Gothenburg, Sweden 2017 Evaluation of open source operating systems for safety-critical applications Petter Sainio Berntsson © Petter Sainio Berntsson, 2017 Examiner: Per Larsson-Edefors Chalmers University of Technology Department of Computer Science and Engineering Academic supervisor: Jan Jonsson Chalmers University of Technology Department of Computer Science and Engineering Industrial supervisors: Lars Strandén RISE Research Institutes of Sweden Dependable Systems Fredrik Warg RISE Research Institutes of Sweden Dependable Systems Master’s Thesis 2017 Department of Computer Science and Engineering Chalmers University of Technology University of Gothenburg SE-412 96 Gothenburg Telephone +46(0) 31 772 1000 Abstract Today many embedded applications will have to handle multitasking with real-time time constraints and the solution for handling multitasking is to use a real-time operating system for scheduling and managing the real-time tasks. There are many different open source real-time operating systems available and the use of open source software for safety-critical applications is considered highly interesting by industries such as medical, aerospace and automotive as it enables a shorter time to market and lower development costs. If one would like to use open source software in a safety-critical context one would have to provide evidence that the software being used fulfills the requirement put forth by the industry specific standard for functional safety, such as the ISO 26262 standard for the automotive industry. -

TASKING VX-Toolset for Tricore User Guide
TASKING VX-toolset for TriCore User Guide MA160-800 (v3.2) February 25, 2009 TASKING VX-toolset for TriCore User Guide Copyright © 2009 Altium Limited. All rights reserved.You are permitted to print this document provided that (1) the use of such is for personal use only and will not be copied or posted on any network computer or broadcast in any media, and (2) no modifications of the document is made. Unauthorized duplication, in whole or part, of this document by any means, mechanical or electronic, including translation into another language, except for brief excerpts in published reviews, is prohibited without the express written permission of Altium Limited. Unauthorized duplication of this work may also be prohibited by local statute. Violators may be subject to both criminal and civil penalties, including fines and/or imprisonment. Altium, TASKING, and their respective logos are trademarks or registered trademarks of Altium Limited or its subsidiaries. All other registered or unregistered trademarks referenced herein are the property of their respective owners and no trademark rights to the same are claimed. Table of Contents 1. C Language .................................................................................................................. 1 1.1. Data Types ......................................................................................................... 1 1.1.1. Bit Data Type ........................................................................................... 2 1.1.2. Fractional Types ....................................................................................... -

PDF, Postscript(Tm) and HTML Form
T2 System Development Environment Creating custom Linux solutions (Compiled from r369) René Rebe Susanne Klaus T2 System Development Environment: Creating custom Linux solutions: (Compiled from r369) by René Rebe and Susanne Klaus Published (TBA) Copyright © 2002, 2003, 2004, 2005, 2006, 2007 René RebeSusanne Klaus This work is licensed under the Open Publication License, v1.0, including license option B: Distribution of the work or derivative of the work in any standard (paper) book form for commercial purposes is prohibited unless prior permission is obtained from the copyright holder. The latest version of the Open Publication License is presently available at ht- tp://www.opencontent.org/openpub/. Table of Contents Preface ....................................................................................................................x Audience ..........................................................................................................x How to Read this Book ...................................................................................... x Conventions Used in This Book ......................................................................... x Typographic Conventions .......................................................................... x Icons ........................................................................................................x Organization of This Book ................................................................................ xi This Book is Free ............................................................................................ -

4. Nios II Software Build Tools
4. Nios II Software Build Tools May 2011 NII52015-11.0.0 NII52015-11.0.0 This chapter describes the Nios® II Software Build Tools (SBT), a set of utilities and scripts that creates and builds embedded C/C++ application projects, user library projects, and board support packages (BSPs). The Nios II SBT supports a repeatable, scriptable, and archivable process for creating your software product. You can invoke the Nios II SBT through either of the following user interfaces: ■ The Eclipse™ GUI ■ The Nios II Command Shell The purpose of this chapter is to make you familiar with the internal functionality of the Nios II SBT, independent of the user interface employed. 1 Before reading this chapter, consider getting an introduction to the Nios II SBT by first reading one of the following chapters: ■ Getting Started with the Graphical User Interface chapter of the Nios II Software Developer’s Handbook ■ Getting Started from the Command Line chapter of the Nios II Software Developer’s Handbook This chapter contains the following sections: ■ “Road Map for the SBT” ■ “Makefiles” on page 4–3 ■ “Nios II Embedded Software Projects” on page 4–5 ■ “Common BSP Tasks” on page 4–8 ■ “Details of BSP Creation” on page 4–20 ■ “Tcl Scripts for BSP Settings” on page 4–27 ■ “Revising Your BSP” on page 4–30 ■ “Specifying BSP Defaults” on page 4–35 ■ “Device Drivers and Software Packages” on page 4–39 ■ “Boot Configurations for Altera Embedded Software” on page 4–40 ■ “Altera-Provided Embedded Development Tools” on page 4–42 ■ “Restrictions” on page 4–48 © 2011 Altera Corporation. -
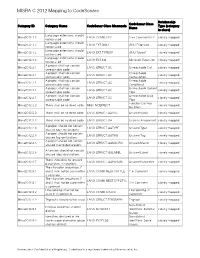
MISRA C 2012 Mapping to Codesonar®
MISRA C 2012 Mapping to CodeSonar® Relationship CodeSonar Class Category ID Category Name CodeSonar Class Mnemonic Type (category Name to class) Language extensions should Misra2012:1.2 LANG.COMM.CPP C++ Comment in C closely mapped not be used Language extensions should Misra2012:1.2 LANG.EXT.GNU GNU Extension closely mapped not be used Language extensions should Misra2012:1.2 LANG.EXT.TYPEOF GNU Typeof closely mapped not be used Language extensions should Misra2012:1.2 LANG.EXT.MS Microsoft Extension closely mapped not be used A project shall not contain Misra2012:2.1 LANG.STRUCT.UC Unreachable Call closely mapped unreachable code A project shall not contain Unreachable Misra2012:2.1 LANG.STRUCT.UC closely mapped unreachable code Computation A project shall not contain Unreachable Misra2012:2.1 LANG.STRUCT.UC closely mapped unreachable code Conditional A project shall not contain Unreachable Control Misra2012:2.1 LANG.STRUCT.UC closely mapped unreachable code Flow A project shall not contain Unreachable Data Misra2012:2.1 LANG.STRUCT.UC closely mapped unreachable code Flow Function Call Has Misra2012:2.2 There shall be no dead code MISC.NOEFFECT closely mapped No Effect Misra2012:2.2 There shall be no dead code LANG.STRUCT.UUVAL Unused Value closely mapped Misra2012:2.2 There shall be no dead code LANG.STRUCT.UA Useless Assignment closely mapped A project should not contain Misra2012:2.3 LANG.STRUCT.UUTYPE Unused Type closely mapped unused type declarations A project should not contain Misra2012:2.4 LANG.STRUCT.UUTAG Unused Tag closely