Evaluation of Open Source Operating Systems for Safety-Critical Applications Master’S Thesis in Embedded Electronic System Design
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Language Subsetting in an Industrial Context: a Comparison of MISRA C 1998 and MISRA C 2004
Language subsetting in an industrial context: a comparison of MISRA C 1998 and MISRA C 2004 Les Hatton CISM, University of Kingston∗ November 20, 2005 Abstract The MISRA C standard [7] first appeared in 1998 with the objective of providing a set of guidelines to restrict features in the ISO C language of known undefined or otherwise dangerous behaviour. The standard was assembled by representatives of a number of companies in the automobile sector in response to the rapidly growing use of C in electronic embedded systems in automobiles. The standard attempts to build on the earlier work of [6], [3] and others. Due to various perceived deficiencies, notably considerable ambiguity in the rule definitions, a revision was planned and eventually appeared in 2004. This paper measures how well the two stan- dards compare on the same population of software and also determines how well the 2004 version achieved its stated goals. Given its increasing influence, the results raise important concerns. Keywords: safer subsets, MISRA C, embedded control systems 1 Overview Pragmatic safer subsetting of languages to remove dependence on poorly defined features is finally becoming a mainstream activity with the recent recommen- dation to form a high-integrity study group under the auspices of the ISO, [8] with the intention of producing sets of rules to restrict features with undefined or otherwise dangerous behaviour in programming languages in common use. It frequently comes as a surprise to developers that significant parts of a pro- gramming language can fall into this category. In practice, all standardised programming languages contain problematic features for a variety of reasons which include the inability of the standardising committee to agree on the be- haviour of a particular feature, the use of unintentionally ambiguous language in the standards document itself, omitting to say anything at all and so on. -

AMNESIA 33: How TCP/IP Stacks Breed Critical Vulnerabilities in Iot
AMNESIA:33 | RESEARCH REPORT How TCP/IP Stacks Breed Critical Vulnerabilities in IoT, OT and IT Devices Published by Forescout Research Labs Written by Daniel dos Santos, Stanislav Dashevskyi, Jos Wetzels and Amine Amri RESEARCH REPORT | AMNESIA:33 Contents 1. Executive summary 4 2. About Project Memoria 5 3. AMNESIA:33 – a security analysis of open source TCP/IP stacks 7 3.1. Why focus on open source TCP/IP stacks? 7 3.2. Which open source stacks, exactly? 7 3.3. 33 new findings 9 4. A comparison with similar studies 14 4.1. Which components are typically flawed? 16 4.2. What are the most common vulnerability types? 17 4.3. Common anti-patterns 22 4.4. What about exploitability? 29 4.5. What is the actual danger? 32 5. Estimating the reach of AMNESIA:33 34 5.1. Where you can see AMNESIA:33 – the modern supply chain 34 5.2. The challenge – identifying and patching affected devices 36 5.3. Facing the challenge – estimating numbers 37 5.3.1. How many vendors 39 5.3.2. What device types 39 5.3.3. How many device units 40 6. An attack scenario 41 6.1. Other possible attack scenarios 44 7. Effective IoT risk mitigation 45 8. Conclusion 46 FORESCOUT RESEARCH LABS RESEARCH REPORT | AMNESIA:33 A note on vulnerability disclosure We would like to thank the CERT Coordination Center, the ICS-CERT, the German Federal Office for Information Security (BSI) and the JPCERT Coordination Center for their help in coordinating the disclosure of the AMNESIA:33 vulnerabilities. -

MISRA-C Subset of the C Language for Critical Systems SAFETY-CRITICAL SYSTEMS
MISRA-C Subset of the C language for critical systems SAFETY-CRITICAL SYSTEMS System is safety-critical if people might die due to software bugs Examples Automobile stability / traction control Medical automation Many military applications You develop safety-critical software differently from non-critical software MISRA-C MISRA – Motor Industry Software Reliability Association Their bright idea: Can’t avoid C But can force developers to avoid features of C that are known to be problematic Some language flaws Some legitimate features that happen to be bad for embedded software Most of MISRA-C is just good common sense for any C programmer TERMINOLOGY Execution error: Something illegal done by a program Out-of-bounds array reference Divide by zero Uninitialized variable usage Trapped execution error: Immediately results in exception or program termination Untrapped execution error: Program keeps running But may fail in an unexpected way later on E.g., due to corrupted RAM In C, operations with undefined behavior are not trapped SAFETY A safe language does not allow untrapped execution errors A statically safe language catches all execution errors at compile time Useful languages can’t be completely statically safe Java is dynamically safe C and C++ are very unsafe MISRA C is not safe either However, adherence to MISRA-C can largely be statically checked This eliminates or reduces the likelihood of some kinds of untrapped execution errors MISRA-C RULE 1.2 No reliance shall be placed on undefined or unspecified behavior. Lots of things in C have undefined behavior Divide by zero Out-of-bounds memory access Signed integer overflow Lots of things in C have implementation-defined and unspecified behavior printf (“a”) + printf (“b”); Both of these hard to detect at compile time, in general Implementation-defined behavior is fine in MISRA-C Why? MISRA-C RULE 5.2 Identifiers in an inner scope shall not use the same name as an identifier in an outer scope, and therefore hide that identifier. -

TCP/IP Enabled Legos
TCP/IP enabled legOS Student research project University of applied sciences Hamburg March 3, 2002 Olaf Christ [email protected] 1 Abstract In recent years, the interest for connecting small devices such as sensors or embedded systems into an existing network infrastructure (such as the global Internet) has steadily increased. Such devices often have very limited CPU and memory resources and may not be able to run an instance of the TCP/IP protocol suite. This document describes how to use the uIP TCP/IP stack, written by Adam Dunkels, on LEGO’s RCX Mindstorm platform, a very small device / toy powered by a h8300 Hitachi microcontroller with very limited RAM (32K) and processing power. Still, it is powerful enough to run alternative operating systems such as LegOS or even a tiny Java VM as a replacement of the original firmware. The advanced user is usually not satisfied with the original firmware due to its extremely limited capabilities in terms of executing complex code and the very limited number of variables. The uIP TCP/IP stack is intended for embedded systems running on low-end 8 or 16-bit microcontrollers. The code size of uIP is an order of a magnitude smaller than similar generic TCP/IP stacks available today. The uIP code and an up-to-date version of the uIP documentation can be downloaded from the uIP homepage maintained by Adam Dunkels. 2 3 Preface This work has been carried out as a student research project at the University of applied sciences Hamburg in Hamburg, Germany. The proposal was given to me by my supervisor Prof. -

Crosscore Embedded Studio 2.2.0 C/C++ Compiler Manual for SHARC
CrossCore Embedded Studio 2.2.0 C/C++ Compiler Manual for SHARC Processors Revision 1.5, February 2016 Part Number 82-100117-01 Analog Devices, Inc. One Technology Way Norwood, MA 02062-9106 Copyright Information ©2016 Analog Devices, Inc., ALL RIGHTS RESERVED. This document may not be reproduced in any form without prior, express written consent from Analog Devices, Inc. Printed in the USA. Disclaimer Analog Devices, Inc. reserves the right to change this product without prior notice. Information furnished by Ana- log Devices is believed to be accurate and reliable. However, no responsibility is assumed by Analog Devices for its use; nor for any infringement of patents or other rights of third parties which may result from its use. No license is granted by implication or otherwise under the patent rights of Analog Devices, Inc. Trademark and Service Mark Notice The Analog Devices logo, Blackfin, CrossCore, EngineerZone, EZ-Board, EZ-KIT, EZ-KIT Lite, EZ-Extender, SHARC, and VisualDSP++ are registered trademarks of Analog Devices, Inc. Blackfin+, SHARC+, and EZ-KIT Mini are trademarks of Analog Devices, Inc. All other brand and product names are trademarks or service marks of their respective owners. CrossCore Embedded Studio 2.2.0 i Contents Preface Purpose of This Manual................................................................................................................................. 1±1 Intended Audience........................................................................................................................................ -

MISRA-C:2004 Guidelines for the Use of the C Language in Critical Systems
MISRA-C:2004 Guidelines for the use of the C language in critical systems October 2004 Licensed to: Tyler Doering. 10 Sep 2008. Copy 1 of 1 First published October 2004 by MIRA Limited Watling Street Nuneaton Warwickshire CV10 0TU UK www.misra-c.com Edition 2 reprinted July 2008 incorporating Technical Corrigendum 1 © MIRA Limited, 2004, 2008. “MISRA”, “MISRA C” and the triangle logo are registered trademarks of MIRA Limited, held on behalf of the MISRA Consortium. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical or photocopying, recording or otherwise without the prior written permission of the Publisher. ISBN 978-0-9524156-2-6 paperback ISBN 978-0-9524156-4-0 PDF Printed by Hobbs the Printers Ltd British Library Cataloguing in Publication Data. A catalogue record for this book is available from the British Library This copy of MISRA-C:2004 - Guidelines for the use of the C language in critical systems is issued to Tyler Doering. The file must not be altered in any way. No permission is given for distribution of this file. This includes but is not exclusively limited to making the copy available to others by email, placing it on a server for access by intra- or inter-net, or by printing and distributing hardcopies. Any such use constitutes an infringement of copyright. MISRA gives no guarantees about the accuracy of the information contained in this PDF version of the Guidelines. The published paper document should be taken as authoritative. -
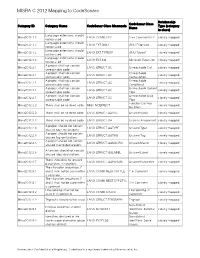
MISRA C 2012 Mapping to Codesonar®
MISRA C 2012 Mapping to CodeSonar® Relationship CodeSonar Class Category ID Category Name CodeSonar Class Mnemonic Type (category Name to class) Language extensions should Misra2012:1.2 LANG.COMM.CPP C++ Comment in C closely mapped not be used Language extensions should Misra2012:1.2 LANG.EXT.GNU GNU Extension closely mapped not be used Language extensions should Misra2012:1.2 LANG.EXT.TYPEOF GNU Typeof closely mapped not be used Language extensions should Misra2012:1.2 LANG.EXT.MS Microsoft Extension closely mapped not be used A project shall not contain Misra2012:2.1 LANG.STRUCT.UC Unreachable Call closely mapped unreachable code A project shall not contain Unreachable Misra2012:2.1 LANG.STRUCT.UC closely mapped unreachable code Computation A project shall not contain Unreachable Misra2012:2.1 LANG.STRUCT.UC closely mapped unreachable code Conditional A project shall not contain Unreachable Control Misra2012:2.1 LANG.STRUCT.UC closely mapped unreachable code Flow A project shall not contain Unreachable Data Misra2012:2.1 LANG.STRUCT.UC closely mapped unreachable code Flow Function Call Has Misra2012:2.2 There shall be no dead code MISC.NOEFFECT closely mapped No Effect Misra2012:2.2 There shall be no dead code LANG.STRUCT.UUVAL Unused Value closely mapped Misra2012:2.2 There shall be no dead code LANG.STRUCT.UA Useless Assignment closely mapped A project should not contain Misra2012:2.3 LANG.STRUCT.UUTYPE Unused Type closely mapped unused type declarations A project should not contain Misra2012:2.4 LANG.STRUCT.UUTAG Unused Tag closely -

C-STAT® Static Analysis Guide
C-STAT® Static Analysis Guide CSTAT-14 COPYRIGHT NOTICE © 2015–2021 IAR Systems AB and Synopsys, Inc. No part of this document may be reproduced without the prior written consent of IAR Systems AB. The software described in this document is furnished under a license and may only be used or copied in accordance with the terms of such a license. This publication incorporates portions of the Technical Report, “SEI CERT C Coding Standard Rules for Developing Safe, Reliable, and Secure Systems 2016 Edition,” by CERT. © 2016 Carnegie Mellon University, with special permission from its Software Engineering Institute. DISCLAIMERS The information in this document is subject to change without notice and does not represent a commitment on any part of IAR Systems. While the information contained herein is assumed to be accurate, IAR Systems assumes no responsibility for any errors or omissions. In no event shall IAR Systems, its employees, its contractors, or the authors of this document be liable for special, direct, indirect, or consequential damage, losses, costs, charges, claims, demands, claim for lost profits, fees, or expenses of any nature or kind. Any material of Carnegie Mellon University and/or its software engineering institute contained herein is furnished on an “as-is” basis. Carnegie Mellon University makes no warranties of any kind, either expressed or implied, as to any matter including, but not limited to, warranty of fitness for purpose or merchantability, exclusivity, or results obtained from use of the material. Carnegie Mellon University does not make any warranty of any kind with respect to freedom from patent, trademark, or copyright infringement. -
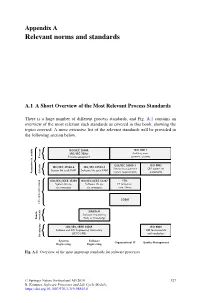
Relevant Norms and Standards
Appendix A Relevant norms and standards A.1 A Short Overview of the Most Relevant Process Standards There is a huge number of different process standards, and Fig. A.1 contains an overview of the most relevant such standards as covered in this book, showing the topics covered. A more extensive list of the relevant standards will be provided in the following section below. ISO/IEC 15504, ISO 19011 ISO/IEC 330xx Auditing man- agement systems Process Process assessment ISO/IEC 20000-1 ISO 9001 ISO/IEC 15504-6 ISO/IEC 15504-5 Service management QM system re- System life cycle PAM Software life cycle PAM Assessments, audits Criteria system requirements quirements ISO/IEC/IEEE 15288 ISO/IEC/IEEE 12207 ITIL System life cy- Software life cy- IT Infrastruc- cle processes cle processes ture Library COBIT Life cycle processes SWEBoK Software engineering Funda- Body of Knowledge mentals ISO/IEC/IEEE 24765 ISO 9000 Systems and SW Engineering Vocabulary QM fundamentals (SEVOCAB) and vocabulary Vocabulary Systems Software Organzational IT Quality Management Engineering Engineering Fig. A.1 Overview of the most important standards for software processes © Springer Nature Switzerland AG 2018 327 R. Kneuper, Software Processes and Life Cycle Models, https://doi.org/10.1007/978-3-319-98845-0 328 A Relevant norms and standards A.2 ISO and IEC Standards The International Organization for Standardization (ISO) is the main international standard-setting organisation, working with representatives from many national standard-setting organisations. Standards referring to electrical, electronic and re- lated technologies, including software, are often published jointly with its sister organisation, the International Electrotechnical Commission (IEC), but IEC also publishes a number of standards on their own. -

IEC 61508 Standard for Functional Safety of Electrical/Electronic/Programmable Electronic Safety-Related Systems
IEC 61508 Overview Report A Summary of the IEC 61508 Standard for Functional Safety of Electrical/Electronic/Programmable Electronic Safety-Related Systems exida Sellersville, PA 18960, USA +1-215-453-1720 © exida IEC 61508 Overview Report, Version 2.0, January 2, 2006 Page 1 of 29 1 Overall Document Summary IEC 61508 is an international standard for the “functional safety” of electrical, electronic, and programmable electronic equipment. This standard started in the mid 1980s when the International Electrotechnical Committee Advisory Committee of Safety (IEC ACOS) set up a task force to consider standardization issues raised by the use of programmable electronic systems (PES). At that time, many regulatory bodies forbade the use of any software-based equipment in safety critical applications. Work began within IEC SC65A/Working Group 10 on a standard for PES used in safety-related systems. This group merged with Working Group 9 where a standard on software safety was in progress. The combined group treated safety as a system issue. The total IEC 61508 standard is divided into seven parts. Part 1: General requirements (required for compliance); Part 2: Requirements for electrical/electronic/programmable electronic safety-related systems (required for compliance); Part 3: Software requirements (required for compliance); Part 4: Definitions and abbreviations (supporting information) Part 5: Examples of methods for the determination of safety integrity levels (supporting information) Part 6: Guidelines on the application of parts 2 and 3 (supporting information) Part 7: Overview of techniques and measures (supporting information). Parts 1, 3, 4, and 5 were approved in 1998. Parts 2, 6, and 7 were approved in February 2000. -

D1.5 Impact on Standards and Open Initiatives - First Analysis
Ref. Ares(2020)1266005 - 28/02/2020 D1.5 Impact on standards and open initiatives - First analysis Version 1.0 Document Information Contract Number 825473 Project Website https://elastic-project.eu/ Contractual Deadline M15, Feb 2020 Dissemination Level CO Nature R Author(s) Thales R&T Contributor(s) BSC, ISEP, SIX, THALIT Reviewer(s) SIX, BSC Keywords Railway Safety Standards, Open Initiatives, Impact Notices: The ELASTIC project has received funding from the European Union’s Horizon 2020 research and innovation programme under the grant agreement Nº 825473. © 2019 ELASTIC. A Software Architecture for Extreme-ScaLe Big-Data AnalyticS in Fog CompuTing ECosystems. All rights reserved. D1.5 Impact on standards and open initiatives - First analysis Version 1.0 Change Log Version Author Description of Change V0.1 TRT Initial Draft Contribution on the analysis of OpenFog V0.2 BSC Initiative V0.2 TRT Contribution 61508 std, Railway std V0.3 SIX DMTF V0.4 ISEP FIWARE V0.5 BSC OpenFog V0.6 THALIT Contribution 61508 std, Railway std V0.7 TRT Final version, including revision V0.8 SIX Internal review V1.0 BSC Final adjustments. Version released to EC. 2 D1.5 Impact on standards and open initiatives - First analysis Version 1.0 Table of contents Change Log ...................................................................................... 2 1. Executive Summary ....................................................................... 5 2. Introduction ............................................................................... 6 2.1 Purpose -

CIP Safety Protocol Training Session 0: Overview of Functional Safety and Safety Networks
CIP Safety Protocol Training Session 0: Overview of Functional Safety and Safety Networks Virtual Training Courses Before We Begin • Introductions • All attendees are automatically muted with no video connection as a default. • Please use the Q&A to ask questions, not the chat. We will address questions as they come in. • At the end if there is time, we will take questions verbally from the attendees. We will advise if and when there is time for you to “raise your hand” if you have a question. • Please complete the 4 question post session survey. The survey will launch when you close out of the webinar. PUB00303R6, CIP Safety Protocol Training, © 2021 ODVA 2 Overview of Functional Safety Standards Jim Grosskreuz Rockwell Automation Evolution of Factory Safety In early factories, workers were encouraged to act in unsafe ways to meet production goals. Industry 2.0 and 3.0 gave us increased focus improved safety by focusing on human factors and developing best practices. Industry 4.0 requires flexibility, ease of use, human-machine collaboration, and interoperability between vendors. PUB00303R6, CIP Safety Protocol Training, © 2021 ODVA 4 Machinery Builder & Operator Responsibilities • European Union – Machinery Directive • Prescriptive approach to machinery safety • Mandates risk assessments and safe machines • United States – OSHA • Less prescriptive approach to machinery safety • Introduces fines for violations – Litigious Culture • OEMs and System Integrators aren’t protected from litigation • Elsewhere – Mixed legal and cultural environments