Helping Smartphone Users Manage Their Privacy Through Nudges Hazim Almuhimedi
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Delaney Opposes Name Change Polk Gets Aid to Buffer AP Range
C M Y K LIVING B12 www.newssun.com NEWS-SUN New year, new you? Highlands County’s Hometown Newspaper Since 1927 Sticking to your New Yearʼs Sunday, January 26, 2014 Volume 95/Number 12 | 75 cents resolutions Dragons done DeLaney opposes name change Boys and girls stopped in By PHIL ATTINGER who served as president of the Monday at 123 E. Pine St. run for titles [email protected] Avon Park City Council for two Kris DeLaney, the former AVON PARK — South Delaney terms and as mayor for 28 years. mayor’s grandson, said it’s fine if SPORTS, B1 Avenue bears the name of a man Current council members are the city wants to name a street for who helped bring Walker scheduled to hear community King, but it shouldn’t be the Memorial Hospital, South Florida input on changing the street name street the city named for his Junior College and federal hous- to Dr. Martin Luther King Jr. grandfather. Polk gets ing projects to Avon Park. Boulevard or if there are other In a letter sent to the city coun- Delaney Heights still bears the suitable streets to name for King. See BATTLE, A6 E.A. DeLANEY Sr. aid to name of Edgar A. DeLaney Sr., The meeting is set for 6 p.m. buffer AP A little Range more than By TOM PALMER Halifax Media Group frost on the BARTOW – Polk County has received $200,000 to aid in ongoing work to buffer Avon Park Air Force windows Range from encroachment by sur- rounding development, Gov. -

Presentazione Standard Di Powerpoint
World’s Best People Data. 1 A B O U T ZEOTAP I DATI DETERMINISTICI DI ZEOTAP GARANTISCONO LA MIGLIORE QUALITÀ DATI UNICI TECNOLOGIA SUPERIORE DATA SECURITY Dati telco in esclusiva, app Piattaforma proprietaria e Privacy e sicurezza come vantaggio usage, purchase intent, dati sul brevettata competitivo mondo travel e real estate ZEOTAP 2 DATA SOURCING ZEOTAP RACCOGLIE DATI DI 6 TIPOLOGIE IN MANIERA DETERMINISTICA TELCO PURCHASE INTENT APP USAGE Dati socio-demo provenienti dal CRM Dati ottenuti in contesto puramente Dati di interesse rilevati dalle app delle Telco e-commerce scaricate ed utilizzate su device mobili REAL ESTATE TRAVEL PROXIMITY Dati di purchase intent provenienti da un Dati di purchase intent provenienti da Dati ottenuti da rilevamento GPS dei sito verticale sul real estate Kayak, azienda leader nel mondo del point-of-interest e da Beacon turismo ZEOTAP 3 DATA SOURCING TELCO Grazie a degli accordi unici, zeotap mette a disposizione degli advertiser i dati socio-demografici presenti nel CRM delle Telco. CARATTERISTICHE DEI DATI: • Sesso • Età • Partite Iva • Tipologia di contratto e pagamento • Residenza • ARPU (Average revenue per user) L’accuratezza dei dati arriva al 95% ZEOTAP 4 DATA SOURCING APP USAGE Dopo un’attenta selezione in base a parametri di qualità, zeotap collabora oggi con 15 data partner in grado di fornire dati sull’utilizzo delle app tramite SDK. CARATTERISTICHE DEI DATI: • Il catalogo app contiene più di 10.000 app • Possono essere selezionate intere categorie o singole app • Opzione “App Affinity” permette di ottenere un un’audience extension con profili simili rispetto al segmento originale ZEOTAP 5 DATA SOURCING PURCHASE INTENT Grazie ad alcuni data partner mondiali otteniamo dati di intento di acquisto da ambiente e-commerce. -
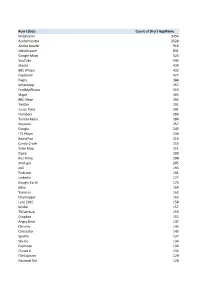
Row Labels Count of Short Appname Mobileiron 3454 Authenticator 2528
Row Labels Count of Short AppName MobileIron 3454 Authenticator 2528 Adobe Reader 916 vWorkspace 831 Google Maps 624 YouTube 543 iBooks 434 BBC iPlayer 432 Facebook 427 Pages 388 WhatsApp 357 FindMyiPhone 313 Skype 303 BBC News 292 Twitter 291 Junos Pulse 291 Numbers 289 TuneIn Radio 284 Keynote 257 Google 243 ITV Player 234 BoardPad 219 Candy Crush 215 Tube Map 211 Zipcar 209 Bus Times 208 mod.gov 205 4oD 193 Podcasts 191 LinkedIn 177 Google Earth 172 eBay 164 Yammer 163 Citymapper 163 Lync 2010 158 Kindle 157 TVCatchup 153 Dropbox 152 Angry Birds 147 Chrome 143 Calculator 143 Spotify 137 Sky Go 136 Evernote 134 iTunes U 132 FileExplorer 129 National Rail 128 iPlayer Radio 127 FasterScan 125 BBC Weather 125 FasterScan HD 124 Gmail 123 Instagram 116 Cleaner Brent 107 Viber 104 Find Friends 98 PDF Expert 95 Solitaire 91 SlideShark 89 Netflix 89 Dictation 89 com.amazon.AmazonUK 88 Flashlight 81 iMovie 79 Temple Run 2 77 Smart Office 2 74 Dictionary 72 UK & ROI 71 Journey Pro 71 iPhoto 70 TripAdvisor 68 Guardian iPad edition 68 Shazam 67 Messenger 65 Bible 64 BBC Sport 63 Rightmove 62 London 62 Sky Sports 61 Subway Surf 60 Temple Run 60 Yahoo Mail 58 thetrainline 58 Minion Rush 58 Demand 5 57 Documents 55 Argos 55 LBC 54 Sky+ 51 MailOnline 51 GarageBand 51 Calc 51 TV Guide 49 Phone Edition 49 Translate 48 Print Portal 48 Standard 48 Word 47 Skitch 47 CloudOn 47 Tablet Edition 46 MyFitnessPal 46 Bus London 46 Snapchat 45 Drive 42 4 Pics 1 Word 41 TED 39 Skyscanner 39 SoundCloud 39 PowerPoint 39 Zoopla 38 Flow Free 38 Excel 38 Radioplayer -

Voorbeeldaanvraag Promotiesteun VAF/Gamefonds
Leg uit Vooral in zijn spelopbouw is de game uniek daar het zich focust op real-time multiplayer. De meeste quiz-games op de markt bieden vaak enkel asynchronous gameplay modes. Switch heeft als USP (Unique selling proposition) zijn real-time multiplayer, 3D avatars en prachtige presentatie. Verder is de link naar een bestaande TV-show ook een USP. 2. Vormgeving van de personages, de setting, het verhaal en de omgeving Ja Leg uit De USP van Switch op het vlak van vormgeving zit hem vooral in het gebruik van leuke en customizable avatars. 99% van de huidige quiz-games presenteren zich als een 2D applicatie. Bij Switch maken we het onderscheid door avatars te gebruiken en alles te presenteren als een volwaardige 3D game. 3. Gebruikte muziek of sound design Ja Leg uit Voor de muziek is er samengewerkt met Vlaamse partners, Waarbij Panenka en Sonicville het sounddesign van de TV-show hebben aangeleverd om dit zo goed mogelijk te vertalen naar de game. 4. Interactiviteit, meerdere spelers, gebruikersinterface, user-generated content Ja Leg uit Zoals reeds vermeld, is één van de uitzonderlijke features van Switch zijn real-time multiplayer functionaliteit. Hier is ook op ingezet na de lancering door het uitbouwen van andere social features, zoals in-game chat functionaliteit en het vergelijken van spelprofielen. 5. Gebruik van artificiële intelligentie Nee Leg uit Er wordt bij Switch een simpele integratie gebruikt om bots te voorzien wanneer de spelers geen actieve spelers kunnen vinden. Dit is echter een eenvoudige implementatie die niet echt innovatief is en waarbij men moeilijk kan spreken van echte AI. -

Apps for Mobile Devices 1
Apps for Mobile Devices 1 Apps for Mobile Devices Dr. Mark Morton Centre for Teaching Excellence University of Waterloo Introduction The term “mobile device” is sometimes used to refer to a laptop computer, but more often it refers to a tablet computer (such as Apple’s iPad, Microsoft’s Surface, or Samsung’s Galaxy) or a smart phone (such as Apple’s iPhone, Samsung’s Galaxy, Microsoft’s Windows Phone, or Blackberry’s Passport). The term “app” – which is short for “application software – refers to a computer program that is designed to run on a mobile device. Since the emergence of the iPhone in 2007, the number of apps that have been developed for the various mobile device operating systems has grown enormously. As of October 2014, there were 1.3 million apps for Apple devices; 800,000 apps for Android devices; 400,000 apps for Windows devices; and 120,000 apps for Blackberry devices. Most of these apps are designed for some purpose relating to entertainment, productivity, or education. Many are of high quality, while others are not. Hundreds if not thousands of them can be used by instructors and students to enhance learning. This document will identify apps that will be of interest to many instructors and students. However, given the large number of apps, and given that some apps will be of interest to those working in one discipline but not another, this document will not attempt to be comprehensive. Instead, the apps included here will be useful in their own right, but they are also intended to suggest the kind and range of apps that are available. -

Mobile Developer's Guide to the Galaxy
Don’t Panic MOBILE DEVELOPER’S GUIDE TO THE GALAXY ly upd te ate le d p m o c 6 E S E R TI F LL FOR published by: We create Apps. Enough Software GmbH + Co. KG Stavendamm 22 28195 Bremen Germany www.enough.de 16th Edition February 2016 This Developer Guide is licensed under the Creative Commons Some Rights Reserved License. Please send your feedback, questions or sponsorship requests to: [email protected] Follow us on Twitter: @MobileDevGuide Art Direction and Design by Cornelius Kwietniak Mladenka Vrdoljak Editors: Marco Tabor Mladenka Vrdoljak www.mobiledevelopersguide.com Mobile Developer’s Guide Contents 1 Prologue 4 The Galaxy of Mobile: An Introduction by Robert Virkus & Marco Tabor 18 From Idea To Concept by Sebastian Meyer 28 User Experience & User Interface Design by Anna Alfut 42 Android by Andre Schmidt & Vikram Kriplaney 60 iOS by Alex Repty 74 Windows by Robert Virkus 84 Going Cross-Platform by Robert Virkus 96 Mobile Sites & Web Technologies by Daniel Kranz 112 Enterprise Apps by Ian Thain & Davoc Bradley 124 Mobile Gaming by Oscar Clark 150 Mobile Development & the Internet of Things by Alex Jonsson 160 Apps for Wearables by Robert Virkus 168 Application Security by Dean Churchill 180 Accessibility by Sally Cain 200 Testing by Julian Harty & Marc van’t Veer 224 Mobile Analytics by Julian Harty 236 Collecting & Understanding User Feedback by Julian Harty 246 Monetisation by Michel Shuqair 262 Epilogue 263 About the Book Prologue Another year, another big round of changes: Mozilla stopped Firefox OS and Jolla went through financial crisis that almost put an end to the project. -

GLU MOBILE INC Form 10-K Annual Report Filed 2019-02-28
SECURITIES AND EXCHANGE COMMISSION FORM 10-K Annual report pursuant to section 13 and 15(d) Filing Date: 2019-02-28 | Period of Report: 2018-12-31 SEC Accession No. 0001558370-19-001331 (HTML Version on secdatabase.com) FILER GLU MOBILE INC Mailing Address Business Address 875 HOWARD STREET, 875 HOWARD STREET, CIK:1366246| IRS No.: 000000000 | State of Incorp.:DE | Fiscal Year End: 1231 SUITE 100 SUITE 100 Type: 10-K | Act: 34 | File No.: 001-33368 | Film No.: 19644136 SAN FRANCISCO CA 94103 SAN FRANCISCO CA 94103 SIC: 7371 Computer programming services 415-800-6100 Copyright © 2019 www.secdatabase.com. All Rights Reserved. Please Consider the Environment Before Printing This Document Table of Contents UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 Form 10-K (Mark One) ☑ ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended December 31, 2018 OR ☐ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 Commission file number: 001-33368 Glu Mobile Inc. (Exact name of registrant as specified in its charter) Delaware 91-2143667 (State or Other Jurisdiction of (IRS Employer Incorporation or Organization) Identification No.) 875 Howard Street, Suite 100 94103 San Francisco, California (Zip Code) (Address of Principal Executive Offices) (415) 800-6100 (Registrant’s Telephone Number, Including Area Code) Securities registered pursuant to Section 12(b) of the Act: Title of Each Class Name of Each Exchange on Which Registered Common Stock, par value $0.0001 per share Nasdaq Global Select Market Securities registered pursuant to Section 12(g) of the Act: None (Title of Class) Indicate by check mark if the registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. -

Connectpreneur June 30 Program Book
June 30, 2021 connectpreneur.org WEDNES DAY, JUNE 30, 2021 11:00-11:05am | VIRTUAL NETWORKING (via Private Message) 11:05-11:15am | WELCOME and INTRODUCTIONS - TIEN WONG, Founder and Host, CONNECTpreneur Community -PATRICK SHERIDAN, Co-Founder & Managing Partner, Modus Create 11:15-12:25pm | ROCKET PITCH SESSION Companies will be introduced by: - ANTHONY MILLIN, Founder & Chair, NEXT by Shulman Rogers -TIM BRAUE, Founding Partner & Attorney, Nemphos Braue PRESENTING COMPANIES: CleanFiber – Jonathan Strimling Community Data Platforms – Alan Worden Dark Block – Christopher Seline FireBot – Mark Baldino Identify Sensors – Greg Hummer Intelligent Fluids – Christian Roemlein Land Intelligence – Gore Bolton MySnoozepod.com – Brandy Lockwood Rentado – Justin Morgan SuperAger World – Stuart Bold Trust Science – Evan Chrapko Zirconia – Benjamin Cook 12:25-1:00pm | BREAKOUT ROOMS & NETWORKING (Breakout rooms hosted by presenting companies) TIEN WONG, CEO, OPUS8, INC.; FOUNDER AND HOST, CONNECTPRENEUR COMMUNITY Tien Wong is a tech entrepreneur and investor. He is CEO of Opus8, Inc. which makes tech investments and helps VC and PE funds and companies raise capital. Opus8’s Phoenix Fund invests in remarkable entrepreneurs who are changing the world through disruptive technologies. Sectors include fintech, health tech, marketing tech/CRM and cyBer. Tien is Chairman of Lumious, a provider of advanced tech training and moBile e-learning solutions to Fortune 500 customers, and is also Chairman of Lore, an IT and BPO services company. Tien was co-founder and CEO of CyBerRep, Inc. until its acquisition in 2003 By a “Fortune 500” company. CyberRep was one of the world’s largest CRM companies with 2,300+ employees and $80+ million in revenue. -
JSON Document Management Application to Support a Real-Time Mobile Quiz Application
JSON Document management application to support a real-time mobile quiz application. A dissertation submitted in partial fulfilment of the requirements for the degree of Bachelor of Science (Honours) in Software Engineering by Julian Wreford 15st January 2016 BSc – Software Engineering Cardiff School of Management Cardiff Metropolitan University, Llandaff, Cardiff, South Wales, United Kingdom i Declaration I hereby declare that this dissertation entitled Systems of Logic Based on Ordinals is entirely my own work, and it has never been submitted nor is it currently being submitted for any other degree. Candidate: Julian Wreford Signature: Date: Supervisor: Stuart McNeil Signature: Date: ii Abstract With the growth of mobile devices and availability of mobile applications from games to utilities they have become part of everyday life. Real time mobile quiz applications have also been increasing in popularity over recent years and are now available across all smartphone and tablet devices. This project introduces quiz topic category specialisation to a real-time mobile quiz application and covered the developed of a document management application that produces and manages quiz question documents in JavaScript Object Notation in support of the quiz. This project also produced a fully functional mobile quiz application and a server- side component to support this. The aim of this project was to develop a document management application to produce JavaScript Object Notation question documents and answer the question could the document management application produce these question documents in a way that can support a real-time mobile quiz application. Development methodology combined a mix of the Spiral Model and Software Prototyping and this project used user testing and performance testing evaluations in assessing its success. -

Quizup Single Player Web
QuizUp Single Player Web Gunnar Marteinsson Kristinn Júlíusson Sonja Jónsdóttir Steinar Þór Árnason May 12, 2016 Instructor: Stefán Freyr Stefánsson T-404-LOKA Examiner: Lóa Jóhannsdóttir School of Computer Science QuizUp Single Player Web Abstract In this report we discuss the B.Sc. project named QuizUp Single Player Web. The project was developed at Reykjavik University in the spring of 2016 in collaboration with Plain Vanilla Games, the makers of the world famous QuizUp app. We developed a Single Player Web application based on the original multiplayer game. 2 QuizUp Single Player Web Contents 1 Introduction6 2 Product Description7 2.1 The Project...................................7 2.2 Development Environment...........................8 3 Work Procedure9 3.1 Kanban.....................................9 3.2 Repositories...................................9 3.3 Work Hours................................... 10 3.4 Kanban Board.................................. 11 3.5 Backlog..................................... 14 3.6 Milestone.................................... 14 3.6.1 Milestone Planning........................... 14 3.6.2 Milestone Review............................ 15 3.6.3 Milestone Schedule........................... 15 3.7 Meetings..................................... 16 4 Project Structure 17 4.1 Time management............................... 17 4.2 Calendar..................................... 17 4.3 Backlog..................................... 18 5 Risk Analysis 19 5.1 Managing Events................................ 20 6 Architecture -

European Dual Companies Scaleup Migration?
EUROPEAN DUAL COMPANIES SCALEUP MIGRATION? In partnership with: Wilson Sonsini Goodrich & Rosati PC With the support of: EUROPEAN DUAL COMPANIES SCALEUP MIGRATION? In partnership with: With the support of: About Startup Europe Partnership (SEP) Established by the European Commission in January 2014 at the World Economic Forum in Davos, SEP is the first pan-European open innovation platform dedicated to transforming European startups into scaleups by linking them with global corporations. By participating in the SEP program, global companies can ease the scale up process via business partnerships and strategic and venture corporate investments, providing them with access to the best technologies and talents through procurement of services or products, corporate acquisition or “acqui-hiring”. SEP is led by Mind the Bridge Foundation, a global organization based in Europe and United States, with the support of Nesta (the UK’s innovation foundation). SEP is a Startup Europe initiative. Partners include Telefónica, Orange, BBVA (Founding), and Telecom Italia, SKY, Unipol Group, Microsoft, Acciona and Enel (SEP Corporate Member), with the institutional support of the European Investment Fund/ European Investment Bank Group, London Stock Exchange Group, EBAN, Cambridge University, IE Business School and Alexander von Humboldt Institute for Internet and Society. For more info: http://startupeuropepartnership.eu | @sep_eu EUROPEAN DUAL COMPANIES out of European Scaleups 1 7 move their HQs abroad Where? Top Destinations 83% SILICON VALLEY 14% LONDON NEW YORK Dual Companies raise 30% more funding than Domestic Scaleups Why Expand? Access to Capital Exit Opportunities Market Size SHOULD I STAY OR SHOULD I GO? by Alberto Onetti & Daniel Glazer 1 out of 7 European scaleups move their headquarters and part of their value chain abroad. -

Instituto Federal De Educação, Ciência E Tecnologia Do Rio Grande Do Sul - Campus Porto Alegre
INSTITUTO FEDERAL DE EDUCAÇÃO, CIÊNCIA E TECNOLOGIA DO RIO GRANDE DO SUL - CAMPUS PORTO ALEGRE MESTRADO PROFISSIONAL EM INFORMÁTICA NA EDUCAÇÃO El Mochilero: Jogo Digital Educacional para o desenvolvimento da competência intercultural de aprendizes de língua espanhola DAIANE PADULA PAZ Porto Alegre - RS 2017 DAIANE PADULA PAZ El Mochilero: Jogo Digital Educacional para o desenvolvimento da competência intercultural de aprendizes de língua espanhola Dissertação e produto de pesquisa apresentados ao Programa de Pós- graduação do Mestrado Profissional em Informática na Educação, do Instituto Federal de Educação, Ciência e Tecnologia do Rio Grande do Sul – Campus Porto Alegre, como requisito parcial para obtenção do título de Mestre em Informática na Educação. Orientadora: Profª Dr.ª Márcia Häfele Islabão Franco. Coorientadora: Profª. Drª Silvia de Castro Bertagnolli. Porto Alegre – RS 2017 Dedico a todos professores que doam suas “horas-vida” em estudos incessantes, simplesmente por acreditarem num futuro melhor. AGRADECIMENTOS Realizar essa pesquisa foi, para mim, um grande desafio. Precisei ver o mundo com os olhos de outra área – tão diferente da que atuo -, superar obstáculos diversos e dedicar-me, incessantemente, ao novo caminho que se abriu sob meus pés. Estou certa que só consegui vencer graças à colaboração e apoio de muitas pessoas as quais gostaria de agradecer imensamente: Às professoras Márcia Häfele Islabão Franco e Silvia de Castro Bertagnolli por acreditarem em meu potencial, pelo incentivo e orientações prestadas mesmo à distância. Vocês me deram asas para que eu pudesse voar. Ao Humberto Jorge de Moura Costa, por todas as horas que dedicou para a codificação do jogo e, sobretudo, por escutar minhas angústias e apoiar todas minhas ideias de forma incessante.