THE INTELLECTUAL PROPERTY RENAISSANCE in CYBERSPACE: WHY COPYRIGHT LAW COULD BE UNIMPORTANT on the INTERNET ERIC SCHLACHTER T
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Leaving Reality Behind Etoy Vs Etoys Com Other Battles to Control Cyberspace By: Adam Wishart Regula Bochsler ISBN: 0066210763 See Detail of This Book on Amazon.Com
Leaving Reality Behind etoy vs eToys com other battles to control cyberspace By: Adam Wishart Regula Bochsler ISBN: 0066210763 See detail of this book on Amazon.com Book served by AMAZON NOIR (www.amazon-noir.com) project by: PAOLO CIRIO paolocirio.net UBERMORGEN.COM ubermorgen.com ALESSANDRO LUDOVICO neural.it Page 1 discovering a new toy "The new artist protests, he no longer paints." -Dadaist artist Tristan Tzara, Zh, 1916 On the balmy evening of June 1, 1990, fleets of expensive cars pulled up outside the Zurich Opera House. Stepping out and passing through the pillared porticoes was a Who's Who of Swiss society-the head of state, national sports icons, former ministers and army generals-all of whom had come to celebrate the sixty-fifth birthday of Werner Spross, the owner of a huge horticultural business empire. As one of Zurich's wealthiest and best-connected men, it was perhaps fitting that 650 of his "close friends" had been invited to attend the event, a lavish banquet followed by a performance of Romeo and Juliet. Defiantly greeting the guests were 200 demonstrators standing in the square in front of the opera house. Mostly young, wearing scruffy clothes and sporting punky haircuts, they whistled and booed, angry that the opera house had been sold out, allowing itself for the first time to be taken over by a rich patron. They were also chanting slogans about the inequity of Swiss society and the wealth of Spross's guests. The glittering horde did its very best to ignore the disturbance. The protest had the added significance of being held on the tenth anniversary of the first spark of the city's most explosive youth revolt of recent years, The Movement. -

Shuchita Times August 2019
ISSN : 0972-7124 August 2019 Volume 20 No. 8 ISSN : 0972-7124 August 2019 Volume 20 No. 8 Freedom is never more than one generation away from extinction. We didn't pass it to our children in the bloodstream. It must be fought for, protected, and handed on for them to do the same. - Ronald Reagan Contents Page No. Dear Friends, Dot-Com Bubble (1997 - 2001) 3 Freedom doesn’t mean you decide the way you Commerce Quiz 5 want. Freedom means responsibility, and the Hasta La Vista Monsoon Flu 5 independence is maintained by responsible freedom. Personality of the Month-Mr. Pranav Yadav 13 Freedom is nothing but a chance to be better and The Mother & the Wolf 13 earn peace. You can't separate peace from freedom Our Booksellers 24 because no one can be at peace unless he has his Cynosure of the Month 26 freedom. Being free is not merely to cast off one’s own shackles, but to live in a way that respects and enriches the freedom of others as well. Executive Editor Prof. Arun Kumar Freedom is always precarious, but it is the safest Editor thing we have. Respect your people who work hard for Dr. Priyadarshani Singh your freedom and ensure your part in this elevation. Happy Independence Day! Dr. K. K. Patra Prof. B. M. Agrawal Prof. M. P. Gupta CA Shashwat Singhal Dr. Pavan Jaiswal, CWA Sri Gaurab Ghosh Dr. Arpita Ghosh CA Ganpat Kumar CA Amar Omar CA Dilip Badlani CS (Dr.) Himanshu Srivastava CA Mohit Bahal Graphics Sai Graphics Editorial Office 25/19, L.I.C. -

Buy, Lie, and Sell High : How Investors Lost out on Enron and The
FMMills.F 5/14/02 3:56 PM Page i About Jonathan Lebed—a teenager who made money day trading on the Internet but ran afoul of Federal regulations—Arthur Levitt, former Chairman of the Securities and Exchange Com- mission, is said to have commented, “Put it this way, he’d buy, lie, and sell high.”1 FMMills.F 5/14/02 3:56 PM Page ii FMMills.F 5/14/02 3:56 PM Page iii Buy, Lie, and Sell High: How Investors Lost Out on Enron and the Internet Bubble FTPH_FM.fm Page i Wednesday, August 22, 2001 12:16 PM In an increasingly competitive world, it is quality of thinking that gives an edge—an idea that opens new doors, a technique that solves a problem, or an insight that simply helps make sense of it all. We work with leading authors in the various arenas of business and finance to bring cutting-edge thinking and best learning practice to a global market. It is our goal to create world-class print publications and electronic products that give readers knowledge and understanding which can then be applied, whether studying or at work. To find out more about our business products, you can visit us at www.ft-ph.com FMMills.F 5/14/02 3:56 PM Page v Buy, Lie, and Sell High: How Investors Lost Out on Enron and the Internet Bubble D. Quinn Mills An Imprint of PEARSON EDUCATION Upper Saddle River, NJ • New York • London • San Francisco • Toronto Sydney • Tokyo • Singapore • Hong Kong • Cape Town Madrid • Paris • Milan • Munich • Amsterdam www.ft-ph.com FMMills.F 5/14/02 3:56 PM Page vi Library of Congress Cataloging-in-Publication Data A catalog record for this book can be obtained from the Library of Congress. -

Risiko, Misserfolge Und Entwicklungsbrüche Junger E-Commerce-Unternehmen in Wissensbasierten Wirtschaftsfeldern in Kalifornien
Risiko, Misserfolge und Entwicklungsbrüche junger E-Commerce-Unternehmen in wissensbasierten Wirtschaftsfeldern in Kalifornien Dr. Gerhard Krauss* Nr. 225 / Dezember 2002 Arbeitsbericht ISBN 3-934629-88-1 ISSN 0945-9553 * Centre de Sociologie de l’Innovation (CSI), Ecole Nationale Supérieure des Mines de Paris Akademie für Technikfolgenabschätzung in Baden-Württemberg Industriestr. 5, 70565 Stuttgart Tel.: 0711 • 9063-0, Fax: 0711 • 9063-299 E-Mail: [email protected] Internet: http://www.ta-akademie.de Ansprechpartner: Dr. Gerhard Fuchs Tel. 0711 • 9063-199 E-Mail: [email protected] Die Akademie für Technikfolgenabschätzung in Baden-Württemberg gibt in loser Folge Aufsätze und Vorträge von Mitarbeitern sowie ausgewählte Zwischen- und Abschlussberichte von durchgeführten Forschungsprojekten als Arbeitsberichte der TA-Akademie heraus. Diese Reihe hat das Ziel, der jeweils interessierten Fachöffentlichkeit und dem breiten Publikum Gele- genheit zu kritischer Würdigung und Begleitung der Arbeit der TA- Akademie zu geben. Anregungen und Kommentare zu den publizierten Ar- beiten sind deshalb jederzeit willkommen. Inhaltsverzeichnis Zusammenfassung 1 Einleitung....................................................................................................................1 2 Regionale Innovationssysteme in Kalifornien.........................................................5 3 Zur Entwicklung des E-Commerce-Sektors in Kalifornien...............................17 4 Die Fallstudien..........................................................................................................29 -

01 Killian 13 12/14/00, 2:04 PM Black 14 IPOS for EVERYONE
How the IPO Market Works 13 SECRET 1 How the IPO Market Works It should come as no surprise that New York City was home to the first hot U.S. initial public offering (IPO). In the spring of 1791, the first Bank of the United States (BUS), which was the young American government’s new central bank, began plans for a stock subscription to raise $10 million. When the stock subscription—what Wall Street bro- kers called IPOs back then—was launched in July, it sold out in an hour. The lucky purchasers of BUS stock were the U.S. government itself, buying $2 million worth of shares, and the powerful, London-based Barings Bank, which scooped up the rest. The shares, priced at $100 each, quickly shot up to $185 before dropping back to $130 that Sep- tember. Until BUS was forced to go out of business by the federal gov- ernment in 1811, its shares were a popular speculative stock for New York’s stock market participants, who traded shares at the Merchants Coffee House at the corner of Wall and Water streets. The great success of the BUS offering spurred other entrepreneurs to organize banks and raise money. Following a pattern that would be repeated many times over the next three centuries, the first companies to go public in a particular business sector are usually the strongest, and they are quickly followed by weaker and weaker fry. The Bank of New York, today a staid New York institution, became the first company to trade on the new New York Stock Exchange (NYSE) in 1792. -

Regulation of Disintermediated Financial Ecosystems
Research Collection Doctoral Thesis Regulation of Disintermediated Financial Ecosystems Author(s): Elsner, Erasmus Publication Date: 2020 Permanent Link: https://doi.org/10.3929/ethz-b-000492901 Rights / License: In Copyright - Non-Commercial Use Permitted This page was generated automatically upon download from the ETH Zurich Research Collection. For more information please consult the Terms of use. ETH Library DISS. ETH NO. 26989 REGULATION OF DISINTERMEDIATED FINANCIAL ECOSYSTEMS A thesis submitted to attain the degree of DOCTOR OF SCIENCES of ETH ZURICH (Dr. sc. ETH Zurich) presented by ERASMUS ELSNER M.A, University of Zurich born on 13.08.1985 citizen of Zurich accepted on the recommendation of Prof. Stefan Bechtold Prof. Ryan Bubb Prof. Christoph Stadtfeld 2020 Abstract The overarching theme of this PhD thesis is the analysis of the interplay between regulation and financial intermediation. The research focuses on the analysis of the role played by security laws and industry-specific financial regulation in shaping the allocation through either the firm or the market. Through a law and economics perspective, the thesis tries to answer two related questions in the realm of both equity and credit markets. Firstly, it tries to establish how different regulations impose (implicit or explicit) prices on transactions and thereby either promote a market-based or a firm-based allocation mechanism. Secondly, for the competing allocative regimes, the thesis questions how the presence of both positive and negative externalities of firms and markets may favor a particular allocation mechanism. The PhD project is divided into five separate chapters, with each one examining different aspects of the law and economics of financial intermediation. -

Contents Berkeley Technology Law
CONTENTS BERKELEY TECHNOLOGY LAW JOURNAL A CONTINUATION OF HIGH TECHNOLOGY LAW JOURNAL EFFECTIVE VOLUME 11 VOLUME 12 NUMBER 1 1997 SYMPOSIUM DIGITAL CONTENT: New Products and New Business Models ARTICLES Foreword to the Digital Content Symposium Pam ela Sam uelson ............................................................................ 1 The Intellectual Property Renaissance in Cyberspace: Why Copyright Law Could Be Unimportant on the Internet Eric Schlachter ................................................................................. 15 Copyright Preemption After the ProCD Case: A Market-Based Approach M aureen A . O 'Rourke ..................................................................... 53 Copyright Policy and the Limits of Freedom of Contract N iva Elkin-K oren ............................................................................ 93 The End of Friction? Property Rights and Contract in the "Newtonian" World of On-line Commerce R obert P . M erges ................................................................................ 115 TECHNICAL PERSPECTIVE Shifting the Possible: How Trusted Systems and Digital Property Rights Challenge Us to Rethink Digital Publishing M ark Stefik ......................................................................................... 137 ARTICLES (CONTINUED) Some Reflections on Copyright Management Systems and Laws Designed to Protect Them Ju lie E . C ohen ..................................................................................... 161 Chaos, Cyberspace and Tradition: Legal -
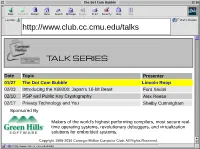
The Dot Com Bubble
http://www.club.cc.cmu.edu/talks TALK SERIES Date Topic Presenter 01/27 The Dot Com Bubble Lincoln Roop 02/03 Introducing the X68000: Japan's 16-bit Beast Ford Seidel 02/10 PGP and Public Key Cryptography Alex Reese 02/17 Privacy Technology and You Shelby Cunningham Sponsored By Makers of the world's highest performing compilers, most secure real- time operating systems, revolutionary debuggers, and virtualization solutions for embedded systems. Copyright 1969-2016 Carnegie Mellon Computer Club. All Rights Reserved. Background ● Initially, consumer Internet use would have been mostly limited to college students and defense employees. ● Why? Computers were still pretty expensive, and access to the real Internet was difficult for average consumers to get even if they had the money. – The death of 8-bit home computers unfortunately came before the price of Windows PCs and Macintoshes got close to their price point. – On-Line Services targeted at consumers, such as AOL and Genie, didn't actually give their customers access to the Internet, instead providing a “walled garden” experience and maybe e-mail to the outside world. Best Buy flyer from 1996 showing sale prices of some basic desktop computers. Note that the Macintosh is more expensive and doesn't include the monitor. Background ● However, in the mid 1990s on-line services such as AOL and Genie started giving their users access to the actual Internet. – They also undertook extensive marketing drives, distributing install media everywhere and giving away free trials. – Initially, these free trials didn't even require a credit card, so some people would just sign up for another account whenever their free hours ran out. -
Bold New Series from National Geographic — Valley of the Boom
Bold new series from National Geographic — Valley Of The Boom — delivers the drama of Silicon Valley’s internet pioneers during the dot-com boom and bust; premieres in Asia on January 13, 2019 Set during the 1990s in Silicon Valley, the six-part limited series stars two-time Emmy award-winning actor Bradley Whitford, Steve Zahn and Lamorne Morris, with Showrunner Matthew Carnahan and Executive Producer Arianna Huffington. HONG KONG, JANUARY 7, 2019 – Silicon Valley spawned some of the world’s most influential people and recognizable brands during the 1990s and attracted geniuses and charlatans alike. It is also where the new phenomenon of the overnight tech millionaire was born. Using a blend of narrative devices and interviews with the real subjects and experts woven into scripted drama, showrunner, creator, director and executive producer Matthew Carnahan (“House of Lies”) charts the meteoric rise and cataclysmic burst of the dot-com bubble. From STX Entertainment, Valley of the Boom is also executive produced by Arianna Huffington and is set to premiere on National Geographic in Hong Kong and South East Asia on Sunday, January 13, 2019 at 10.00 PM (HKT) and on video-streaming service FOX+. The new six-part limited series features an unconventional hybrid of scripted storytelling and documentary interviews with the key players whose stories are dramatized in the show. In the series, Carnahan follows the turbulent ride of three different companies whose founders were trying to change the world using the new technology of the internet. Before Google, Netscape pioneered the first commercial web browser and launched the “browser wars” with Microsoft. -

1 Clean MSIC AR
■ organizing programs, new initiatives, Web-based public policy effort BEYOND 2000 and networking resource for and activities throughout the year. including summaries of the companies; the most effective Massachusetts national and Massachusetts We remain committed to our advocate on public policy issues The Technology Company Software & Internet perspectives on public policy mission as we head into 2001: to affecting the industry; the most Mediation Program, (developed issues promote the software and Internet innovative catalyst for finding with Hanify & King, Professional Council 2000ANNUALREPORT industry; to assist executives in solutions to such pressing Corporation; Lucash, Gesmer ■ Project descriptions of all past starting, managing and growing their industry issues as the shortage www.msicouncil.org & Updegrove, LLP; and Nixon Above and Beyond Award companies; and to help software of workers; and the most visible Peabody, LLP) launched in winners highlighting best and Internet companies be and vocal supporter of the September of 2000 in response to practices in educational successful in global markets, strengths of the Massachusetts member requests, is a first-in-the technology 2000: Continued Industry Leadership for the New Millenium remains. We continue to strive to technology community. ■ industry program to assist ■ Investment Conference be the best information, referral, companies in settling their business Presenting Company Presenta- in last year’s Guide. The Guide potential investors, partners and from up and down the east coast and technology disputes outside the tion for review and follow-up was produced in cooperation employees; to interact with national and across the country came to courtroom by highly experienced after the conference Board of Directors 2000 with Mass High Tech and and local industry luminaries; to hear the company presentations. -

Believing in the Net
Believe in the net: Implicit religion and the internet hype, 1994-2001 Pärna, K. Citation Pärna, K. (2010, January 28). Believe in the net: Implicit religion and the internet hype, 1994-2001. Retrieved from https://hdl.handle.net/1887/14622 Version: Not Applicable (or Unknown) Licence agreement concerning inclusion of doctoral thesis in the License: Institutional Repository of the University of Leiden Downloaded from: https://hdl.handle.net/1887/14622 Note: To cite this publication please use the final published version (if applicable). Believing in the Net Cover illustration: Visual representation of the Internet. The Opte Project. http://opte.org/ Cover design: Maedium, Utrecht Lay out: Florian Duijsens ISBN-10 9087280750 ISBN-13 9789087280758 NUR-706 / 988 © K. Pärna / Leiden University Press, 2010 All rights reserved. Without limiting the rights under copyright reserved above, no part of this book may be reproduced, stored in or introduced into a retrieval system, or transmitted, in any form or by any means (electronic, mechanical, photocopying, recording or otherwise) without the written permission of both the copyright owner and the author of the book. Believing in the Net Implicit Religion and the Internet Hype, 1994-2001 Proefschrift ter verkrijging van de graad van Doctor aan de Universiteit Leiden, op gezag van de Rector Magnificus prof.mr. P.F. van der Heijden, volgens besluit van het College voor Promoties te verdedigen op donderdag 28 januari 2010 klokke 15.00 uur door Karen Pärna geboren te Tallinn, Estland in 1977 Promotor: Prof. dr. M.B. ter Borg Commissieleden: Prof. dr. E.G.E. van der Wall Prof. -

Flags of Many Colors Three Undergraduates Win Goldwater
RESEARCHER IN THE PINK A new mild, sweet - and pink - onion variety is a pleasant inadvertent co ELL discovery. APPLE FOR THE STUDENTS . Two seniors split time between their studies and their popular World Wide Web-service business. ILR School will establish institute to study conflict resolution By Darryl Geddes nouncement, applauded the formation of cated to "hands-on" engagement in conflict "The School of Industrial and Labor the institute, saying that he had "very high prevention and resolution throughout con Relations is exactly the school at Cornell to Cornell, with support from the newly cre expectations"for its work and thatofPERC. temporary society and to stimulating take the lead in establishing an institute for ated Foundation for Prevention and Early Cornell President Hunter Rawlings also thoughtful public discourse on the theory prevention and resolution of all types of Resolution of Conflict (pERq, plans to es has endorsed the institution's creation. and practice ofdispute prevention and reso conflicts," Kheel said. "The School of In tablish an institute at the School of Industrial "The new institute will enable Cornell lution. Theodore W. Kheel, PERC's presi dustrial and Labor Relations has now en and Labor Relations for the study ofconflict University and the School of Industrial and dent, has served as a mediator or arbitrator in joyed 50 years ofinten e experience coping resolution. The institute, to be located on Labor Relations to bring their commitment thousands of disputes. PERC co-chairmen with labor-management disputes under the campus, is expected to open in August. to public service and applied research to a areThomasDonahue, former presidentofthe procedures ofthe National Labor Relations Cornell and PERC made the joint an new level," he said.