Random Tales from a Mobile Phone Hacker
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

2017 Registration Document
2017 Registration document Annual financial report Table of contents 1. Overview of the Group 5. Corporate, social and and of its business environmental responsibility 1.1 Overview 4 5.1 Social commitments 311 1.2 Market and strategy 7 5.2 Employee information 316 1.3 Operating activities 12 5.3 Environmental information 328 1.4 Networks and real- estate 38 5.4 Duty of care 337 1.5 Innovation at Orange 40 5.5 Report by one of the Statutory Auditors 338 1.6 Regulation of telecom activities 43 6. Shareholder Base 2. Risk factors and activity and Shareholders’ Meeting management framework 6.1 Share capital 342 2.1 Risk factors 64 6.2 Major shareholders 343 2.2 Activity and risk management framework 69 6.3 Draft resolutions to be submitted to the Combined Ordinary and Extraordinary Shareholders’ Meeting of May 4, 2018 345 3. Financial report 6.4 Report of the Board of Directors on the resolutions submitted to the Combined Ordinary and 3.1 Analysis of the Group’s financial position and earnings 78 Extraordinary Shareholders’ Meeting of May 4, 2018 350 3.2 Recent events and Outlook 131 6.5 Statutory Auditors’ report on resolutions 3.3 Consolidated financial statements 133 and related party agreements 357 3.4 Annual financial statements Orange SA 240 3.5 Dividend distribution policy 278 7. Additional information 4. Corporate Governance 7.1 Person responsible 362 7.2 Statutory Auditors 362 4.1 Composition of management and supervisory bodies 280 7.3 Statutory information 363 4.2 Functioning of the management 7.4 Factors that may have an impact in the event and supervisory bodies 290 of a public offer 365 4.3 Reference to a Code of Corporate Governance 298 7.5 Regulated agreements and related party transactions 366 4.4 Compensation and benefits paid to Directors, 7.6 Material contracts 366 Officers and Senior Management 298 8. -
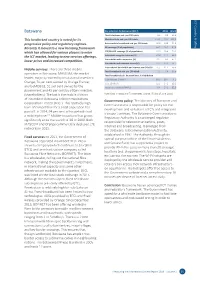
Botswana Key Indicators for Botswana (2017) Africa World Fixed-Telephone Sub
ICT Country Profiles Botswana Key indicators for Botswana (2017) Africa World Fixed-telephone sub. per 100 inhab. 6�2 0�9 13�0 This landlocked country is noted for its Mobile-cellular sub. per 100 inhab. 141�4 74�4 103�6 progressive policy and regulatory regimes. Active mobile-broadband sub. per 100 inhab. 66�9 24�8 61�9 Recently it moved to a new licensing framework 3G coverage (% of population) 84�0 62�7 87�9 which has allowed for various players to enter LTE/WiMAX coverage (% of population) 65�0 28�4 76�3 the ICT market, leading to new services offerings, Individuals using the Internet (%) 41.4 22�1 48�6 lower prices and increased competition. Households with a computer (%) 31.2 8�9 47�1 Households with Internet access (%) 45.7 19�4 54�7 International bandwidth per Internet user (kbit/s) 26�5 11�2 76�6 Mobile services: There are three mobile Fixed-broadband sub. per 100 inhab. 2�1 0�6 13�6 operators in Botswana: MASCOM, the market Fixed-broadband sub. by speed tiers, % distribution leader, majority-owned by institutional investors; -256 kbit/s to 2 Mbit/s 84�0 38�7 4�2 Orange, 74 per cent owned by Orange France; -2 to 10 Mbit/s 15�5 37�2 13�2 and beMOBILE, 51 per cent owned by the -equal to or above 10 Mbit/s 0�4 24�1 82�6 government and 45 per cent by citizen investors (shareholders). The last is the mobile division Note: Data in italics are ITU estimates. -

National Broadband Strategy
MINISTRY OF TRANSPORT AND COMMUNICATIONS NATIONAL BROADBAND STRATEGY June 2018 Table of Contents LIST OF FIGURES .................................................................................................................... 4 LIST OF TABLES ...................................................................................................................... 5 ABBREVIATIONS .................................................................................................................... 6 EXECUTIVE SUMMARY ........................................................................................................... 7 1 INTRODUCTION .............................................................................................................. 9 2 SITUATIONAL ANALYSIS ............................................................................................... 11 2.1 International Connectivity ................................................................................................................................. 11 2.2 National Backbone ................................................................................................................................................ 11 2.3 Backhauling .............................................................................................................................................................. 11 2.4 Mobile Coverage .................................................................................................................................................... -

Privacy Leaks in Mobile Phone Internet Access
1 Privacy Leaks in Mobile Phone Internet Access Collin Mulliner Security in Telecommunications Technische Universit¨at Berlin / Deutsche Telekom Labs Berlin D-10587, Germany [email protected] Abstract—Accessing the Internet and specifically the World discussion forums1 where this topic was discussed. The Wide Web from a mobile phone is common today. Especially main issue was that those discussions did not come to any since the usage fees for packet-data access dropped to a point meaningful result since only rumors and very simple studies where anybody who can can afford a mobile phone can afford mobile Internet access. Almost every mobile phone today comes where presented by the individuals. Therefore, we decided with an integrated web browser that can display HTML web to investigate for ourselfs. The only bit of information that pages and execute JavaScript. Almost all major web sites such seemed coherent is that some private information is leaked as news sites, social networks, and shopping sites run websites through HTTP [3] headers. that are optimized for small displays of mobile phones. Due to the broad use of mobile web access we investigated possible privacy problems of mobile phone web access. We conducted In this paper we presented a study on if and how private a study where we monitor all HTTP headers sent from mobile data is leaked through mobile phone-based web access. The phones to our web server. We analyzed the logged data for study concentrates on data that is leaked through HTTP privacy problems. Through this study we determined that a headers. -

Understanding What Is Happening in ICT in Botswana
Evidence for ICT Policy Action Policy Paper 1, 2013 Understandingwhat is happening in ICT in Botswana A supply- and demand- side analysis of the ICT sector Steve Esselaar and Sebusang Sebusang Research ICT Africa Research ICT Africa (RIA) is an information and communication technology (ICT) policy and regulation research network based in Cape Town, South Africa, under the directorship of Dr. Alison Gillwald. As a public interest think tank, RIA fills a strategic gap in the development of a sustainable information society and knowledge economy. The network builds the ICT policy and regulatory research capacity needed to inform effective ICT governance in Africa. RIA was launched a decade ago and has extended its activities through national, regional and continental partnerships. The network emanates from the growing demand for data and analysis necessary for appropriate but visionary policy required to catapult the continent into the information age. Through development of its research network, RIA seeks to build an African knowledge base in support of sound ICT policy and regulatory design, transparent implementation processes, and monitoring and review of policy and regulatory developments on the continent. The research, arising from a public interest agenda, is made available in the public domain, and individuals and entities from the public sector, private sector and civil society are encouraged to use it for purposes of teaching and further research or to enable them to participate more effectively in national, regional and global ICT policymaking and governance. Series Editor: Alison Gillwald Editorial assistance: Broc Rademan Evidence for ICT Policy Action Acknowledgements Research ICT Africa (RIA) is an information and communication technology (ICT) policy and regulation research network based in Cape Town, South Africa, under the directorship of Dr. -
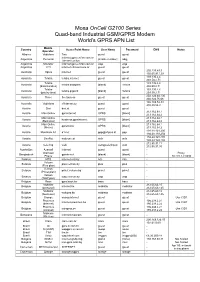
Moxa Oncell G2100 Series Quad-Band Industrial GSM/GPRS Modem World’S GPRS APN List
Moxa OnCell G2100 Series Quad-band Industrial GSM/GPRS Modem World’s GPRS APN List Mobile Country Acess Point Name User Name Password DNS Notes Operator Albania Vodafone Twa guest guest internet.gprs.unifon.com.ar Argentina Personal [mobile number] adgj internet.unifon Argentina Movistar internet.gprs.unifon.com.ar wap wap Argentina CTI internet.ctimovil.com.ar guest guest 202.139.83.3 Australia Optus internet guest guest 192.65.91.129 139.130.4.4 Australia Telstra telstra.internet guest guest 203.50.2.71 Telstra 139.130.4.4 Australia telstra.datapack [blank] Telstra (data bundles) 203.50.2.71 Telstra 139.130.4.4 Australia telstra.pcpack [blank] Telstra (pay by time) 203.50.2.71 202.124.68.130 Australia Three 3netaccess guest guest 202.124.76.66 192.189.54.33 Australia Vodafone vfinternet.au guest guest 210.80.58.3 Austria Drei drei.at guest guest - 213.162.64.1 Austria Max Online gprsinternet GPRS [blank] 213.162.64.2 Max Online 213.162.64.1 Austria business.gprsinternet GPRS [blank] (Business) 213.162.64.2 Max Online 213.162.64.1 Austria gprsmetro GPRS [blank] (Metro) 213.162.64.2 194.48.124.200 Austria Mobilkom A1 a1.net [email protected] ppp 194.48.139.254 194.24.128.100 Austria OneNet web.one.at web web 194.24.128.102 212.95.31.11 Austria tele.ring web [email protected] web 212.95.31.35 Azerbaijan Azercell internet guest guest - Grameen Proxy: Bangladesh gpinternet [blank] [blank] - Phone 10.128.1.2:8080 Belarus MTS internet.mts.by mts mts - Velcom Belarus plus.velcom.by plus plus - (Plus plan) Velcom Belarus privet.velcom.by privet privet -

Annual Report
2015Annual Report INTRODUCTION FINANCIAL STATEMENTS Chairman’s Statement 1 Members of the Board report 49 Board Members 3 Board Members Responsibilities Board Member Profiles 4 and Approval 50 Executive Managment 5 Independent Auditor’s Report 51 Chief Executive’s Report 6 Statement of Financial Position 52 Statement of Comprehensive GOVERNANCE Income 53 Board Participation 11 Statement of Cash Flows 54 Internal Audit 12 Statement of Changes in Equity 55 Policy and Legal Review 12 Accounting Policies 56 Operational Plan Review 13 Notes to the Annual Financial Licensing of ICT Service Statements 64 Providers 13 Detailed Statement of Review of Licensing Comprehensive Income 77 Framework 15 ICT Market Performance 15 Mobile Telephony Market 15 Fixed Market Segment 16 Internet Uptake 16 Mobile Internet Market 18 Value Added Services 18 Technical Services 19 Type Approval 19 Spectrum Management 20 Broadcasting Regulation 25 Postal Sector Regulation 26 Regulatory Initiatives 28 Compliance Monitoring 29 Investigations 29 Network Performance 30 Consumer Protection 35 Stakeholder Engagements 36 BOCRA Brand and Strategy Launch 39 Media Relations 39 Regional Engagements 39 International Engagements 39 Corporate Social Investment 41 Human Capital 41 TRANSPARENCY Our decision making will be open and informed by consultation with various stakeholders. We will embrace the diverse interests of our different stakeholders. CONSISTENCY We will ensure that our decisions are fair, predictable and dependable. We will be objective in our decision making and apply remedies that are proportionate. PEOPLE CENTERED We believe that our people are indispensable assets who drive our success through their commitment to excellence. We shall therefore harness individual skill and trengths and work as one. -

Mar 29 2020 FINAL BB FACTS and FIGURES
BOTSWANA COMMUNICATIONS REGULATORY AUTHORITY BROADBAND FACTS AND FIGURES MARCH 2020 1 Contents FOREWORD ........................................................................................................................................ 3 EXECUTIVE SUMMARY .................................................................................................................... 4 INTRODUCTION ................................................................................................................................. 4 UNIVERSAL ACCESS AND SERVICE FUND (UASF) AND ITS ACHIEVEMENTS IN BROADBAND DEPLOYMENT ......................................................................................................... 7 BOFINET AND ITS ROLE IN BROADBAND DEPLOYMENT .................................................... 8 FIXED BROADBAND ......................................................................................................................... 8 Types of Fixed Broadband .......................................................................................................... 9 Pricing for Fixed Broadband .................................................................................................... 12 FIXED WIRELESS BROADBAND ................................................................................................. 14 Pricing for Fixed Wireless Broadband ................................................................................... 15 SATELLITE BROADBAND ............................................................................................................ -

Towards an Information Society for Botswana
Chapter 5 TOWARDS AN INFORMATION SOCIETY FOR BOTSWANA INFORMATION, INFORMATION AND COMMUNICATION welfare. In Section 19 of the Universal Declaration of Human Rights, the TECHNOLOGIES AND HUMAN DEVELOPMENT1 international community via the United Nations recognises that “everyone has the right to freedom of opinion and expression; this right includes The introduction and rapid uptake of ICTs have expanded opportunities for freedom to hold opinions without interference and to seek, receive and people and increased the social and economic benefits of creating and impart information and ideas through any media and regardless of frontiers”2. using technology. The information economy spawned is pervasive and no government, organization, business or community, whatever the scale of In integrating this question of equity and freedom of expression and of its operation, can afford to ignore it. access to information, human development shares a common vision with human rights. The common goal here is human freedom (see Box 5.1). Along with other breakthroughs, ICTs, are pushing forward the frontiers of Empowerment and freedom are closely related. Access to information and how people can use technology to eradicate poverty. The development related factors, especially information policies, are fundamental when dilemma is that, for those with access to ICTs, the opportunities for considering the role that ICTs can play in human development. individual and community empowerment have increased, whilst for those without, ICTs might remain elements of curiosity as the picture below Box 5.1: seems to suggest. They could equally exacerbate the already widening ICTs for human development: access and empowerment gaps between urban and rural communities. -

Final Report
FINAL REPORT Botswana Communications Regulatory Authority (BOCRA) Plot 50671, Independence Avenue Gaborone CONSUMER AND SERVICE PROVIDER SATISFACTION SURVEY PREPARED BY BOTSWANA INSTITUTE FOR DEVELOPMENT POLICY ANALYSIS (BIDPA) 134 International Finance Park, Tshwene Drive P/Bag BR 29, Gaborone NOVEMBER 2018 TABLE OF CONTENTS LIST OF TABLES ....................................................................................................................... iv LIST OF FIGURES ....................................................................................................................... v LIST OF ACROYMNS ................................................................................................................ vi FOREWORD .............................................................................................................................. vii ACKNOWLEDGEMENTS ........................................................................................................ viii EXECUTIVE SUMMARY ...............................................................................................................ix CHAPTER 1 ..................................................................................................................................... 1 INTRODUCTION AND OBJECTIVES ............................................................................................ 1 1.1 INTRODUCTION ............................................................................................................. 1 1.2 OBJECTIVES OF THE STUDY -

Botswana Thetha Final 4 March
Title: Towards an Information Society in Botswana © DLIS 2010 Country Research Partner : Department of Library and Information Studies University of Botswana Tel: +267 355 2627 / E-mail: [email protected] Project Coordination: David Barnard Southern African NGO Network (SANGONeT) Tel: +27 11 403 4935 / E-mail: [email protected] Editing and Research Coordination: Tina James Icteum consulting Tel: +27 12 346 8264 / E-mail: [email protected] This report forms part of the Thetha - Regional ICT Discussion Forum Project The information contained in this document may be reproduced, used and shared without prior permission but with acknowledgement of this publication as the source The project is funded by the Open Society Initiative for Southern Africa (OSISA) and the Embassy of Finland (South Africa) www.thetha.org PREFACE The Thetha - Regional ICT Discussion Forum Project is an initiative of SANGONeT aimed at tracking ICT4D initiatives in SADC member states and facilitating networking and dialogue among civil society organisations, academia, government organisations, corporate sector and development agencies to share information and experiences of the different countries in this regard. The Thetha project is funded by the Embassy of Finland (South Africa) and the Open Society Initiative for Southern Africa (OSISA), and is administered by SANGONeT. The Botswana Thetha - Regional ICT Discussion Forum is organised through the partnership of the Department of Library and Information Studies (University of Botswana) and SANGONeT. A similar event was co-hosted by BOCONGO and SANGONeT - dubbed the Botswana ICT Discussion Forum - in Gaborone from 5-6 October 2006. The Forum at that time sought to provide a platform for discussing the Maitlamo ICT policy which was at that stage a draft document. -

Integrated Report for the Year Ended 31 December 2019 TBWA\HUNT\LASCARIS 921574 TBWA\HUNT\LASCARIS Report Navigation
MTN Group Limited Integrated Report for the year ended 31 December 2019 ended 31 December year the for Report Integrated Limited MTN Group Together, we go from isolated25YEAR to celebrated. BIRTHDAY Any dream can become a reality, with over 560 million Africans covered by a high-speed digital highway. When you can reach out to the most isolated people amongst you, and connect them from village to village, from nation to nation and from there to the world, you go. When you can use technology to teach, where books can’t reach, we all go. When 30 million people who could never bank before, now have a bank in their pocket, they go. Every day, MTN is# inspiredGoodTogether by the unstoppable spirit of the people we serve. That’s why, We’re good together. everywhere you go In Africa, every valley MTN Group Limited Integrated Report for the year can be Silicon Valley. TBWA\HUNT\LASCARIS 921574 TBWA\HUNT\LASCARIS ended 31 December 2019 Any dream can become a reality, with over 560 million Africans covered by a high-speed digital highway. When you can reach out to the most isolated people amongst you, and connect them from village to village, from nation to nation and from there to the world, you go. When you can use technology to teach, where books can’t reach, we all go. When 30 million people who could never bank before, now have a bank in their pocket, they go. Every day, MTN is inspired by the unstoppable spirit of the people we serve.