Master's Thesis
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Verification of Vulnerable Zones Identified Under the Nitrate
CONTENTS 1 INTRODUCTION 1 1.1 OVERVIEW OF THE QUALITY OF CONTINENTAL WATERS 1 1.2 PROBLEMS ENCOUNTERED DURING THE INVESTIGATIONS 2 2 PROCEDURES FOR DESIGNATING SENSITIVE AREAS AND VULNERABLE ZONES AND APPLICATION OF CRITERIA ESTABLISHED IN DIRECTIVES 5 2.1 INTRODUCTION 5 2.2 PROCEDURES FOR DESIGNATING SENSITIVE AND LESS SENSITIVE AREAS (DIRECTIVE 91/271/EEC) 8 2.3 PROCEDURES FOR DESIGNATING VULNERABLE ZONES (DIRECTIVE 91/676/EEC). 14 2.4 ANALYSIS OF THE APPLICATION OF CRITERIA FOR DESIGNATION OF SITES UNDER DIRECTIVES 91/271/EEC AND 91/676/EEC. 20 3 CONCLUSIONS REGARDING THE RELATIONSHIP BETWEEN VULNERABLE ZONES AND SENSITIVE AREAS IN SPAIN, TAKING INTO ACCOUNT COMMON STANDARDS. 30 1 INTRODUCTION 1.1 OVERVIEW OF THE QUALITY OF CONTINENTAL WATERS At the end of 1998, the national Ministry of the Environment completed the “Libro Blanco del Agua en España”, or (White Paper for Water in Spain). This document was designed as a tool for assessing and guiding water management in Spain. Although Spain’s future water policy is outlined in the conclusions, the points mentioned refer only to quantitative aspects of water resources without considering the issue of quality. Nonetheless, the issue of river, reservoir, lake and groundwater pollution is taken into account in the assessment section. Amongst the problems related to water quality, the White Paper notes, among others, problems related with Directives 91/271/EEC and 91/676/EEC. A brief summary of the main issues addressed is provided below. Surface water and diffuse pollution. In general, diffuse pollution produced by agricultural and livestock raising activities (e.g. -

Serveis Socials D'osona
SERVEIS SOCIALS D’OSONA Memòria 2018 SERVEIS SOCIALS D’OSONA 2018 D’OSONA SOCIALS SERVEIS 01 Àrea de Serveis Socials Bàsics 02 Àrea d’Inclusió i desenvolupament comunitari 03 Àrea d’Infància, Adolescència i Família 04 Àrea de Promoció a l’Autonomia i Atenció a la dependència 05 Àrea de Polítiques d’Igualtat de gènere i LGTB ESTRUCTURA ORGANITZATIVA D’OSONA Els professionals de serveis socials s’estructuren amb àrees de treball totalment transversals entre elles Centre Calldetenes Espinelves Gurb Cada equip territorial està format per un equip de 3 tècnics, 2 Sta Eugènia de Berga treballadors socials (TS) i un educador social (ES). Lluçanès St Julià de Vilatorta St Sadurní d’Osormort Prats de Lluçanès Vilanova de Sau St Agustí del Lluçanès Bisaura, Vall del ges i Hi ha un TS referent de gent gran, promoció a l’autonomia i St Bartomeu del Grau Votreganès atenció a la dependència, i un TS junt amb l’ES com a St Boi de Lluçanès Montesquiu referents d’adults, infància i família. St Feliu Sasserra St Quirze de Besora, St Martí d’Albars Sta Maria de Besora Sobremunt Sora Amb aquesta nova organització dels equips es busca tenir Alpens, Lluçà Vidrà referents clars en els territoris i que puguin ser els tècnics de Olost St Pere de Torelló Oristà St Vicenç de Torelló referència pels diferents agents que actuen en els municipis. Perafita St Hipòlit de Voltregà Santa Cecília de Voltregà * Torelló i Centelles no estan a la gestió del Consorci però tenen una organització SERVEIS SOCIALS D’OSONA 2018 D’OSONA SOCIALS SERVEIS Les Masies de Voltregà Orís. -

Fires, Festes I Mercats Més Destacats D'osona
Fires, festes i mercats més destacats d’Osona GENER • Manlleu: Badanadal • Sant Pere de Torelló: Fira de Sant Sebastià • Santa Eugènia de Berga: Festa del Tonis • Taradell: Festa de Sant Antoni Abat FEBRER • Centelles: Cau de bruixes i Mercat màgic • Perafita: 1r diumenge, Festes i Fires de la Candelera. • Torelló: Carnaval Terra Endins • Vic: Dijous Llarder MARÇ • Balenyà: Dilluns de Pasqua Florida, Fira de l'Aplec dels Ous (març o abril) • Muntanyola: Festa de l'arbre • Sant Bartomeu del Grau: Fira de Natura i Muntanya • Sant Julià de Vilatorta: caramelles del Roser • Santa Maria de Besora: Mercat medieval • Vic: Fira Slot Clàssic ABRIL • Roda de Ter: Fira de la Llavor • Santa Eulàlia de Riuprimer: Aplec de Sant Sebastià • Tona: Tona és Fira • Vic: Mercat del Ram i Làctium MAIG • Alpens: Fira del Jovent i trobada de forjadors. • Balenyà: Fira de la cervesa • L'Esquirol: Cabrerès BTT • Les Masies de Voltregà: Ruta de les Ermites (BTT) • Manlleu: Fira Circ • Olost: Fira de Santa Creu de Jutglar • Sant Julià de Vilatorta: Fira del Tupi • Tona: Festival Internacional de Màgia JUNY • Alpens: Cursa Tres Comarques • Centelles: Fira de la Ratafia • Tona: Aplec de la Rosa a Lurdes i al Castell • Vilanova de Sau: Fira d’Herbes Remeieres JULIOL • Manlleu: Llunes del Ter • Prats de Lluçanès: Fira de Sant Jaume • Roda de Ter: Fira del Pescador • Torelló: Festus: Festival d’Arts al Carrer. AGOST • Manlleu: Llunes del Ter i Festa del Serpent • Santa Eulàlia de Riuprimer: Festa del Segar i el Batre • Taradell: Festa del Toca-Sons. Mercat Medieval • Vic: Fira d'Antiguitats SETEMBRE • Calldetenes: Fira de la Mercè • Manlleu: Festa del Porc i la Cervesa • Sant Agustí de Lluçanès: Fira de l’Hostal del Vilar • Vic: Mercat de Música Viva OCTUBRE • Montesquiu: Fira de la Nou • Orís: Mercat de la Patata del Bufet • Sant Quirze de Besora: Fira del Tast del Bisaura • Santa Eulàlia de Riuprimer: Fira del Fredolic • Seva: Festa del Bolet • Tavèrnoles: Fira de Sant Galderic • Viladrau: Fira de la Castanya. -

Vols Comprar Aliments Ecològics a Osona?
Vols comprar aliments ecològics a Osona? www.setmanabio.cat On comprar Bio a la comarca? Directament als 7 La cabra de la Vall d’en Ges CC PA I CEREALS Ramaders de cabrum productors i [email protected] 14 Farines Ylla 1878 elaboradors Farines i derivats 8 Embotits Salgot [email protected] Carn i embotits de porc ylla1878.com AVIRAM I OUS [email protected] 1 Granja La Riera salgot.com 15 Mas Bellpuig Pollastres, ous i conills Pa i derivats. Horta. [email protected] [email protected] DEL BOSC 2 Niu Verd 16 Mas Corcó VD Pollastres 9 Castanya de Viladrau VD CC Pa i derivats [email protected] Castanyes i derivats [email protected] niuverd.cat [email protected] 3 Tofaroques 10 Mel Llàgrimes del Ra VD CC VERDURES, HORTALISSES, Ous Mel [email protected] FRUITA I FRUITS SECS [email protected] tofaroques.blogspot.com melcasasas.com 17 El Circell VD Horta 4 Viubé VD CC VD CC [email protected] Pollastres 11 Sambucus elcircell.cat [email protected] Herbes per a infusions [email protected] viube.com sambucus.cat 18 Masia Escrigas VD CC Horta i ous BEGUDES [email protected] 5 Companyia Cervesera FORMATGES I LÀCTICS masiaescrigas.com del Montseny Cervesa 12 Formatgeria Betara 19 Mas Jalech [email protected] Formatges i derivats Horta cervesamontseny.cat [email protected] [email protected] betara.cat CARN I EMBOTITS 20 Horta Vila VD CC 6 Arblanch Alimentació 13 Formatges Mas el Garet Horta Embotits Formatges de cabra [email protected] [email protected] [email protected] arblanch.com maselgaret.cat -

Guia Turística De Centelles
Centelles És una vila amb un entorn immillorable i un magnífic patri- moni històric, artístic i cultural. Amb la Festa del Pi i el Cau de Bruixes, viureu les tradicions d’un poble inquiet, dinàmic i ple d’atractius. A Centelles, coneixereu un poble per viure i conviure, assaborireu una samfaina autòctona i embo- tits artesanals de qualitat. Cada diumenge us hi espera el mercat tradicional i un comerç proper amb les portes obertes. Seva Seva Tona Gurb Malla El Brull Taradell Viladrau Centelles Espinelves Folgueroles Calldetenes Muntanyola Aiguafreda Vilanova de Sau Vilanova St. Julià de Vilatorta St. St. Martí de Centelles St. Sta. Eugènia de Berga Sta. Balenyà - Els Hostalets Balenyà St. Sadurní d’Osormort Sadurní St. S. Eulàlia de Riuprimer S. Ajuntament Com arribar-hi Patrimoni històric Adreça k C-17 sortida de Centelles, en direcció a Vic La Sagrera c/ Nou, 19 k C-1413 de Sant Feliu de Codines La plaça Major La Sagrera és l’espai de 30 passes al voltant Telèfon Urbanitzada entre el 1514 i el 1549, on es va edificar la nova de l’Església de Santa Coloma documentat Empresa Sagalés: 938 810 375 k casa del baró i les dels seus dos germans. Presideix la plaça des de 1145. Va ser el punt de partida del Línia Barcelona-Vic / Línia Castellterçol-Vic / 932 312 756 creixement urbanístic de Centelles realitzat Codi postal el Palau dels Comtes, construït a mitjans del segle XVI i pels barons el segle XVI. Una passejada per 08540 reconstruït el segle XIX. La façana principal conserva l’escut k Renfe: Línia Barcelona-Puigcerdà dels Comtes de Centelles. -

Biblioteca I Hemeroteca Arxiu Municipal Centelles (Autor)
Biblioteca i hemeroteca Arxiu Municipal Centelles (autor) Autor Títol "Balmes y la monarquia". A.C.N. de P: Publicació Madrid: Asociación Católica Nacional de Propagandistas, 1 de gener de 1947, año XXIII, núm. 383 Format Publicació periòdica Autor Títol "Centellas (Barcelona)". Policia municipal. Revista tecnico-legislativa Publicació Madrid: Cosema, 1978. Núm. 340, p. 41-43 Format Revista, article Autor Títol "Centelles homenatja Mn. Ramon Vidal, sacerdot i mestre". Butlletí" de l'Assossiació d'Amics de l'Escola Normal de la Generalitat Publicació Barcelona: Assossiació d'Amics de l'Escola Normal de la Generalitat, 2001. Núm. 26, p. 3 Format Butlletí, article Autor Títol "Centelles". Gran Enciclopèdia Catalana Publicació Barcelona: Enciclopèdia Catalana, 1968, volum 4, fascicle núm. 104, p. 814-820 21/10/2020 Pàgina 1 de 248 Format Fascicle Autor Títol "Centelles. Terra de Bruixes". Sortida pel Pirineu, la Costa Brava i Andorra. Revista de Promoció Turística i Cultural. Publicació [Ripoll: S'agaró: Encamp]: iTram Comunicació : S'Agaró Press, SL : Promarts, SA, 2014. Núm. 5, p. 12-13. Format Revista Autor Títol "El Ilmo. Sr. D. José Prims Bagés, alcalde de Centellas (Barcelona)". Policia municipal. Revista tecnico-legislativa Publicació Madrid: Cosema, 1975-1976?. p.189-190 Format Article Autor Títol "El tranvía de Centelles". Carril Publicació [Barcelona]: Associació d'Amics del Ferrocarril, 1986. Núm. 6, p. 55-57 Format Article, fotocòpies Autor Títol "Es alcalde de Centellas el Ilmo. Sr. Francisco Pujol Albañel". Policia municipal. Revista tecnico-legislativa Publicació Madrid: Cosema, 1977. Núm. 329, p. 121-123 Format Article, fotocòpies 21/10/2020 Pàgina 2 de 248 Autor Títol "Excursió al Castell de Centelles (Sant Martí). -

Improvement of Spain's Regional Railway System Based Off of Germany's Railway Model
Improvement of Spain’s regional railway system based off of Germany’s railway model: Making R3 an efficient train line. Gil Salvans Torras Bachelor thesis Thesis advisor: María del Carmen Moreno Course 2018-2019 Abstract This research aims to compare the Spanish and German regional railway mobility systems, by analyzing infrastructures which compose each network, services operating them and legal framework that comprises them. To make it the most accurate and realistic, two study cases are analyzed in depth: R3 of Rodalies Renfe and RB22 of DB Regio Mitte. All of this composes the input to create an Improvement Project which will put forward and eliminate the innefficiecies of the Rodalies Renfe services based on the DB Regio experience. Key words: railway, regional, Deutsche Bahn, Renfe, system, transportation, Rodalies, R3, RB22. Resumen Esta investigación presenta una analogía entre los sistemas ferroviarios regionales de España y Alemania, donde se analizan las dos redes ferroviarias y sus infraestructuras correspondientes, los servicios que las operan y sus respectivos marcos legales presentes. Para darle más precisión y aplicabilidad práctica, se analizan profundamente dos casos de estudio: la línea R3 de Rodalies Renfe y la RB22 de DB Regio Mitte. Todo esto conforma la base para crear un proyecto de mejora que expondrá y eliminará las ineficiencias de los servicios de Rodalies basado en la experiencia alemana de DB Regio. Palabras clave: ferrocarril, regional, Deutsche Bahn, Renfe, sistema, transporte, Rodalies, R3, RB22. 1 Table of contents 1. Introduction............................................................................................................... 3 1.1. Presentation of the topic and motivations ........................................................ 3 1.2. Objectives and hypothesis ................................................................................. 4 1.3. -

Laquadra D' Aiguafreda
LAQUADRA D'AIGUAFREDA Historia d'un senyoriu del Montseny CARLES PUIGFERRAT I OLIVA Fotos: Servei del Patrimoni Arquitectonic (Generalitat de Catalunya) El petit municipi d'Aiguafreda, de 7,96 krn.2 de superfície, és el successor del que durant segles es va anomenar la quadra (després baronia) d'Aiguafre da. Aquest article vol ser una aproxirnació a la historia d'aquesta quadra o dis tricte jurisdiccional que, en arribar al segle XIX, va esdevenir un municipi cons titucional, un dels més petits dels que envolten el Montseny. L'actual municipi d'Aiguafreda, que ocupa un dels darrers contraforts ponentins del massís, té uns lírnits ben precisos que vénen fixats gairebé sempre per accidents geo grafics naturals: la riera o torrent de l'Avencó, a migdia, frontera amb Tagama nent, el torrent o riera de Martinet i l'Afrau del Muntanya, al nord, que separa Aiguafreda de Seva, i el riu Congost, a ponent, que passa per la zona baixa del terme i és el lírnit tradicional amb el municipi de Sant Martí de Centelles i anti gament amb la baronia i comtat de Centelles. El lírnit de llevant, tocant al Brull, és més arbitrari i va de la falda del turó de Montgros fins al pont de Picamena. LA QUADRA D'AIGUAFREDA, UN CAS SINGULAR Una quadra era, a l' edat rnitjana, un districte o petit territori dins un terme jurisdiccional més gran, generalment el terme d'un castell. La paraula comern;a a apareixer a la docurnentació a partir del segle XI a les comarques que alesho res es trobaven a la marca o frontera amb el món isfarnic (com la Segarra o l'Ur gell), per tal de designar un sector concret dins la circurnscripció d'un castell que disposava de deterrninats trets específics. -

Resultats De Contaminació Per Nitrats a Les
LABORATORI PRAT. LABPRAT | H2O | Carrer del Pont, 21 08570 TORELLÓ Telf. 938590381 FAX 938594076 Laboratori autoritzat per la Direcció General de Salut Pública amb el nº LSAA-104-97 Laboratori inscrit amb el núm.300 com a Reconegut en el Registre de Laboratoris Agroalimentaris de Catalunya Laboratori sotmès a autoavaluació continuada de resultats en Exercicis d'Intercomparació GRUP DE DEFENSA DEL TER MES DE GENER DE 2018 CONCENTRACIÓ DE NITRATS A L'AIGUA DE LES FONTS DE LA COMARCA D'OSONA Mètode: Espectrofotometria UV MUNICIPI PUNT DE MOSTREIG Nitrats MUNICIPI PUNT DE MOSTREIG Nitrats mg/l. mg/l. ALPENS FONT DE LA LLENA 0,8 PRATS DE LLUÇANÉS FONT DE LES 3 FONTS 70,1 ALPENS FONT DE LA PIXARELLA 2,0 PRATS DE LLUÇANÉS FONT DE LA VILA no raja BALENYÀ FONT DE L'ABEURADOR 16,7 RODA DE TER LES TRES FONTS. 166 133,3 BALENYÀ FONT DE LA TRIA 140,8 RUPIT FONT DE LA SALA 6,9 BALENYÀ FONT DE LA TALAÏA 178,2 RUPIT FONT DEL SALTIRI 4,1 CALLDETENES FONT DEL FIGUERAL 181,2 RUPIT FONT DE LA GUITARRA 15,6 CALLDETENES FONT DE LA GANA no raja SEVA FONT DEL MONTMANY 53,4 CALLDETENES FONT DE LA BOGA 154,5 SEVA FONT DE LA SERRA 14,3 CENTELLES FONT GROSSA. 220 104,5 SEVA FONT DEL SORS. 242 38,8 CENTELLES FONT CALENTA 106,1 SOBREMUNT FONT DEL GRAU 59,6 CENTELLES FONT DE SAUVA NEGRE 1,0 SOBREMUNT FONT CONJUNTA no raja COLLSUSPINA FONT DE LA PULLOSA no raja SOBREMUNT FONT DE LA ROCA 60,5 COLLSUSPINA FONT D'EN REGÀS 93,2 SOBREMUNT FONT DE STA. -

Calendari De Competició
Federació Catalana de Futbol Calendari de Competicions TERCERA CATALANA, GRUP 5 Temporada 2021-2022 Equips Participants 1.- AIGUAFREDA, C.E. "A" (6403) 2.- SANTA EUGENIA, J.E. "A" (1454) 3.- BORGONYA, C.D. "A" (1179) 4.- SANT VICENÇ TORELLO, U.E. "A" (1365) 5.- CENTELLES, U.E. "A" (1151) 6.- NAVAS,C.E. "B" (1170) 7.- FOLGUEROLES,C.F. "A" (1211) 8.- TONA, U.E. "B" (1219) 9.- CALDES MONTBUI, C.F. "B" (1021) 10.- MOIÀ, C.E. "A" (1057) 11.- SEVA, U.E. "A" (1456) 12.- VOLTREGA,C.F. "A" (1186) 13.- PRADENC,F.C. "A" (1059) 14.- RODA DE TER, C.E. "A" (1075) 15.- CASTELLTERÇOL, C.F. "A" (1068) 16.- OLIMPIC LA GARRIGA, C.F. "A" (1149) 17.- SANT FELIU DE CODINES, C.F. "A" (1070) TERCERA CATALANA, GRUP 5 Página: 1 de 6 Federació Catalana de Futbol Primera Volta Segona Volta Jornada 1 (19-09-2021) Jornada 18 (06-02-2022) AIGUAFREDA, C.E. "A" - BORGONYA, C.D. "A" BORGONYA, C.D. "A" - AIGUAFREDA, C.E. "A" OLIMPIC LA GARRIGA, C.F. "A" - CENTELLES, U.E. "A" CENTELLES, U.E. "A" - OLIMPIC LA GARRIGA, C.F. "A" RODA DE TER, C.E. "A" - FOLGUEROLES,C.F. "A" FOLGUEROLES,C.F. "A" - RODA DE TER, C.E. "A" VOLTREGA,C.F. "A" - CALDES MONTBUI, C.F. "B" CALDES MONTBUI, C.F. "B" - VOLTREGA,C.F. "A" MOIÀ, C.E. "A" - SEVA, U.E. "A" SEVA, U.E. "A" - MOIÀ, C.E. "A" TONA, U.E. "B" - PRADENC,F.C. "A" PRADENC,F.C. "A" - TONA, U.E. -

Olalde Et Al. Science 2019
RESEARCH POPULATION GENETICS fromtheanalysisdatasetsindividualscoveredby <10,000 SNPs, with evidence of contamination, or first-degree relatives of others (table S1). We analyzed the data with principal components The genomic history of the Iberian analysis (PCA) (Fig. 1, C and D), f-statistics (11), and qpAdm (12) and summarize the results in Peninsula over the past 8000 years Fig. 1E. We confirmed the robustness of key findings by repeating analyses after remov- Iñigo Olalde1*, Swapan Mallick1,2,3, Nick Patterson2, Nadin Rohland1, ing SNPs in CpG dinucleotides (table S5) that Vanessa Villalba-Mouco4,5, Marina Silva6, Katharina Dulias6, Ceiridwen J. Edwards6, are susceptible to cytosine-to-thymine errors Francesca Gandini6, Maria Pala6, Pedro Soares7, Manuel Ferrando-Bernal8, even in UDG-treated libraries (1). Nicole Adamski1,3, Nasreen Broomandkhoshbacht1,3, Olivia Cheronet9, Previous knowledge of the genetic structure Brendan J. Culleton10, Daniel Fernandes9,11, Ann Marie Lawson1,3, of Mesolithic Iberia comes from three individ- 1,2,3 1,3 1,3 1 2 Matthew Mah , Jonas Oppenheimer , Kristin Stewardson , Zhao Zhang , uals from the northwest: LaBraña1 ( ), Canes1 5 5 Juan Manuel Jiménez Arenas12,13,14, Isidro Jorge Toro Moyano15, ( ), and Chan ( ). We add LaBraña2, who was a Domingo C. Salazar-García16, Pere Castanyer17, Marta Santos17, Joaquim Tremoleda17, brother of the previously reported LaBraña1 (figs. S1 and S2 and table S6), as well as Cueva Marina Lozano18,19, Pablo García Borja20, Javier Fernández-Eraso21, de la Carigüela (fig. S10), Cingle del Mas Nou, José Antonio Mujika-Alustiza21, Cecilio Barroso22, Francisco J. Bermúdez22, and Cueva de la Cocina from the southeast. In Enrique Viguera Mínguez23, Josep Burch24, Neus Coromina24, David Vivó24, northwest Iberia, we document a previously un- Artur Cebrià25, Josep Maria Fullola25, Oreto García-Puchol26, Juan Ignacio Morales25, appreciated ancestry shift before the arrival of F. -
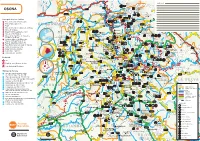
El Ripollès El Bages El Moianès La Selva El Vallès
Sant 907 Milany NOTES EL RIPOLLÈS 1536 C-17 Santa Margarida C-26 Castell de Cabagés OSONA de Milany GR 151 Ciuret Volcà de Santa Maria BP-4654 la Farga 700 de Bebié PARC DEL de Besora Puigsacalm CASTELL 1515 DE MONTESQUIU BV-5227 Vidrà Principals atractius turístics Alpens Castell de Montesquiu Salt Salt Puigsalla del Mir de Molí Parc del Castell de Montesquiu Sora 1027 Bellmunt Museu Episcopal de Vic BERGA Montesquiu EL BERGUEDÀ Cussons 1247 BV-5224 Rupit Sant Quirze Mare de Déu Túnel l'Alou de Bellmunt Museu del Coure, les Masies de Voltregà Sant Agustí de Besora de Bracons de Lluçanès Sant Andreu els Munts GR 210 Sant Pere Monestir de Lluçà Saderra de la Vola Santa Eulàlia de Torelló Espai Perot Rocaguinarda, Olost BV-4341 Bosc de Cabrera de Puig-oriol Gallifa Museu del Ter, Manlleu la Mambla la Grevolosa 1308 (Lluçà) Sant Boi S Borgonyà Sant Vicenç e Monestir de Sant Pere de Casserres, Monestir de r de Lluçanès Orís de Torelló ra les Masies de Roda Santa Maria de Lluçà d Castell e C Vila-seca C-37 ab Jaciment i Museu de l’Esquerda, Lluçà d’Orís rera Masies de Roda i Roda de Ter Perata BV-4608 C-17 GR 151 la Blava Torelló Cantonigròs Ruta literària Miquel Martí i Pol Pruit BV-4342 Vinyoles la Colònia Ruta Modernista, Sant Julià de Vilatorta BV-4341 la Farga Lacambra l’Esquirol Riera de Merlés les Masies Camp de les Lloses, Tona Sant Martí Sobremunt C-153 d'Albars de Voltregà Salt de C-63 Espai Montseny, Viladrau el Ter la Foradada Rupit C-154 Prats de BP-4653 Sant Hipòlit Sant Martí BV-4601 Sescorts (Rupit i Pruit) Camí Oliba - GR