Border Gateway Protocol Best Practices
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
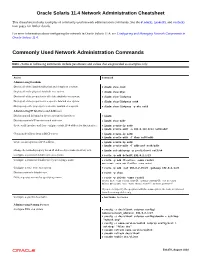
Oracle® Solaris 11.4 Network Administration Cheatsheet
Oracle Solaris 11.4 Network Administration Cheatsheet This cheatsheet includes examples of commonly used network administration commands. See the dladm(8), ipadm(8), and route(8) man pages for further details. For more information about configuring the network in Oracle Solaris 11.4, see Configuring and Managing Network Components in Oracle Solaris 11.4. Commonly Used Network Administration Commands Note - Some of following commands include parameters and values that are provided as examples only. Action Command Administering Datalinks Display all of the datalinks (physical and virtual) on a system. # dladm show-link Display all of the physical datalinks on a system. # dladm show-phys Display all of the properties for all of the datalinks on a system. # dladm show-linkprop Display all of the properties for a specific datalink on a system. # dladm show-linkprop net0 Display a specific property for a specific datalink on a system. # dladm show-linkprop -p mtu net0 Administering IP Interfaces and Addresses Display general information about a system's IP interfaces. # ipadm Display a system's IP interfaces and addresses. # ipadm show-addr Create an IP interface and then configure a static IPv4 address for that interface. # ipadm create-ip net0 # ipadm create-addr -a 203.0.113.0/24 net0/addr Obtain an IP address from a DHCP server. # ipadm create-ip net0 # ipadm create-addr -T dhcp net0/addr Create an auto-generated IPv6 address. # ipadm create-ip net0 # ipadm create-addr -T addrconf net0/addr Change the netmask property for an IP address object name (net3/v4) to 8. # ipadm set-addrprop -p prefixlen=8 net3/v4 Configure a persistent default route on a system. -

Manual Update Configuring a Default Gateway
S3290 Manual Update Configuring a Default Gateway The following information is to be included with the S3290 Web User Guide. IP Configuration Configure the S3290-managed IPv4 information from Configuration > System > IP as one of the first steps. The S3290 supports an IPv4 / IPv6 dual stack. The S3290 can be assigned IP address statically or dynamically using DHCP. Here you can configure IP basic settings, IP interfaces and IP routes. Up to 8 interfaces and up to 32 routes are supported. IP Routes Click the Add Route button to display the editable fields: Delete Select this option to delete an existing IP route. Network The destination IP network or host address of this route. Valid format is dotted decimal notation or a valid IPv6 notation. A default route can use the value 0.0.0.0 or IPv6 :: notation. Mask Length The destination IP network or host mask, in number of bits (prefix length). It defines how much of a network address that must match, in order to qualify for this route. Valid values are 0 - 32 bits for IPv4 routes or 0 - 128 for IPv6 routes. Only a default route will have a mask length of 0 (as it will match anything). Gateway The IP address of the IP gateway. Valid format is dotted decimal notation or a valid IPv6 notation. The Gateway and Network must be of the same type. It may be necessary to add a static route if a default gateway is required or if the device does not reside within the same network. Routing can then be enabled at System > IP > IP Configuration. -

Lab 2.8.1: Basic Static Route Configuration
Lab 2.8.1: Basic Static Route Configuration Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 172.16.3.1 255.255.255.0 N/A R1 S0/0/0 172.16.2.1 255.255.255.0 N/A Fa0/0 172.16.1.1 255.255.255.0 N/A R2 S0/0/0 172.16.2.2 255.255.255.0 N/A S0/0/1 192.168.1.2 255.255.255.0 N/A FA0/0 192.168.2.1 255.255.255.0 N/A R3 S0/0/1 192.168.1.1 255.255.255.0 N/A PC1 NIC 172.16.3.10 255.255.255.0 172.16.3.1 PC2 NIC 172.16.1.10 255.255.255.0 172.16.1.1 PC3 NIC 192.168.2.10 255.255.255.0 192.168.2.1 Learning Objectives Upon completion of this lab, you will be able to: • Cable a network according to the Topology Diagram. • Erase the startup configuration and reload a router to the default state. • Perform basic configuration tasks on a router. All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 20 CCNA Exploration Routing Protocols and Concepts: Static Routing Lab 2.8.1: Basic Static Route Configuration • Interpret debug ip routing output. • Configure and activate Serial and Ethernet interfaces. • Test connectivity. • Gather information to discover causes for lack of connectivity between devices. • Configure a static route using an intermediate address. -

Configure BGP to Advertise a Default Route on Cisco Nexus Switches
Configure BGP to advertise a Default Route on Cisco Nexus Switches Contents Introduction Prerequisites Requirements Components Used Configure Network Command Redistribute and Default-Information Originate Commands Default-Originate Command Introduction This document describes different approaches to configure Border Gateway Protocol (BGP) to advertise a Default Route (0.0.0.0/0 network prefix) to BGP neighbors on Cisco Nexus NX-OS based Switches. Prerequisites Requirements Cisco recommends that you have knowledge of these topics: ● Nexus NX-OS Software. ● Routing Protocols, specifically BGP. Components Used The information in this document is based on Cisco Nexus 7000 with NX-OS version 7.3(0)D1(1) The outputs in this document were taken from devices in a specific lab environment. All devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command. Configure Network Command The network 0.0.0.0/0 command injects the default route in the BGP RIB (BGP Routing Information Base). The prerequisite is to have the default route in the Routing Table via any other Routing Protocol or manually configured with a Static Route. Once in the BGP RIB, the default route is advertised to all BGP neighbors unless specifically denied by an outbound filter configured per neighbor. BGP configuration as seen in the show running-config output. Nexus BGP Configuration Nexus# show running-config bgp !Command: show running-config bgp !Time: Tue Dec 4 01:27:43 2018 version 7.3(0)D1(1) feature bgp router bgp 64512 address-family ipv4 unicast network 0.0.0.0/0 neighbor 10.1.3.3 remote-as 64512 address-family ipv4 unicast In this example, Nexus receives the default route from EIGRP protocol. -

Configuring Ipv6 in AOS.Pdf 1116 KB
6AOSCG0016-29P March 2016 Configuration Guide Configuring IPv6 in AOS This configuration guide describes Internet Protocol version 6 (IPv6) and its use in ADTRAN Operating System (AOS) products. This guide provides a basic overview of IPv6 functionality and an overview of how IPv6 functions in AOS, as well as includes descriptions of command line interface (CLI) commands used by AOS for specific IPv6 feature configurations. This guide contains the following sections: • IPv6 Overview on page 2 • IP Addresses in IPv6 on page 5 • IPv6 Route Cache and Traffic Processing on page 8 • Hardware and Software Requirements and Limitations on page 10 • IPv6 Implementation in AOS on page 12 • IPv6 and the Interface in AOS on page 13 • Configuring IPv6 Routing in AOS on page 16 • IPv6 IPsec on page 19 • IPv6 General Utility Commands on page 33 • IPv6 Neighbor Discovery (ND) in AOS on page 39 • IPv6-Aware HTTP Server in AOS on page 48 • IPv6 DNS in AOS on page 51 • ICMPv6 in AOS on page 54 • NTP over IPv6 on page 55 • IPv6 Traffic Control in AOS on page 57 • Configuring IPv6 Traffic to Traverse an IPv4 GRE Tunnel on page 69 • Additional Resources on page 79 IPv6 Overview IPv6 in AOS IPv6 Overview IPv6 is the next generation of Internet protocols designed to replace IPv4. Both IPv4 and IPv6 are packet protocols designed to pass data, voice, and video over digital networks. IPv4 is the current standard used for Internet communication, however, its available address space is quickly diminishing. As new global markets gain access to the Internet and as new devices, particularly mobile devices, are connected to the Internet, IPv4 32-bit addressing limits the number of available IP addresses for these new markets and new devices. -

REDDIG II – Computer Networking Training
REDDIG II – Computer Networking Training JM SANCHEZ / PH RASSAT - 20/06/2012 IP Addressing and Subnetting Invierno 2011 | Capacitacion en fabrica - CORPAC IP Addressing and Subnetting IP Addresses An IP address is an address used to uniquely identify a device on an IP network. The address is made up of 32 binary bits which can be divisible into a network portion and host portion with the help of a subnet mask. 32 binary bits are broken into four octets (1 octet = 8 bits) Dotted decimal format (for example, 172.16.254.1) REDDIG II | Network Course | Module 2 | 3 IP Addressing and Subnetting Binary and Decimal Conversion REDDIG II | Network Course | Module 2 | 4 IP Addressing and Subnetting IP Address Classes • IP classes are used to assist in assigning IP addresses to networks with different size requirements. • Classful addressing: REDDIG II | Network Course | Module 2 | 5 IP Addressing and Subnetting Private Address Range • Private IP addresses provide an entirely separate set of addresses that still allow access on a network but without taking up a public IP address space. • Private addresses are not allowed to be routed out to the Internet, so devices using private addresses cannot communicate directly with devices on the Internet. REDDIG II | Network Course | Module 2 | 6 IP Addressing and Subnetting Network Masks • Distinguishes which portion of the address identifies the network and which portion of the address identifies the node. • Default masks: Class A: 255.0.0.0 Class B: 255.255.0.0 Class C: 255.255.255.0 • Once you have the address and the mask represented in binary, then identification of the network and host ID is easier. -

IP Addressing Design Issues and Protocols
IP Addressing Design Issues and Protocols CS2520/TELCOM2321 Wide Area Network Spring Term, 2019 Prof. Taieb Znati Department Computer Science Telecommunication Program Outline Internet Address Structure o Classfull Addresses o Classeless Addresses o Subnetting and Supernetting DHCP and ARP Network Address Translation IP Addressing IP Address Every device connected to the public Internet is assigned a unique IP address. o Typically addresses are assigned to internet service providers within region-based blocks, o IP address can often be used to identify the region or country from which a computer is connecting to the Internet. An IP address can sometimes be used to show the user's general location. IP addresses can be assigned by an ISP statically (Static IP Address) or dynamically (Dynamic IP Address) IP Address IPv4, defined by 4 bytes (32 bits) o IP address represents a network interface o Routers, for example, are typically assigned multiple IP addresses Address spaces o 0.0.0.0 ~ 255.255.255.255 o 232 = 4,294,967,296 hosts Classful IP Address Format Class P r i A 0 NetID HostID m a r y 10 NetID HostID C B l a s s 110 NetID HostID e C s D 1110 Multicast Address E 1111 Experimental Address 8 bits 8 bits 8 bits 8 bits Class A Networks Class B Networks Class C Networks IP Addresses IP Address dotted decimal notation o It divides the 32-bit IP address into 4 byte fields and specifies each byte independently as a decimal number with the fields separated by dots 10 010001 00001010 00100010 00000011 145 145 145 145 145.10.34.3 -

Static Routing/RIP Routing
CyberPatriot Session VI Topic 4: Basic Routing © 2010 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 1 Topic 4 – Basic Routing . IP addressing a simple network . Static routing/RIP routing . L3 Tools (Ping, traceroute) Cisco Basic Routing Agenda . Review IP Addressing: 10 min . Review Basic Routing: 20 min . Static Routing: 15 min . Static Routing Lab: 30 min . RIP Routing: 20 min . RIP Routing Lab: 20 min Topics . Identify a router as a computer with an OS and hardware designed for the routing process. Demonstrate the ability to configure devices and apply addresses. Describe the structure of a routing table. Describe how a router determines a path and switches packets . Discuss Static and RIP Routing Router as a Computer . Describe the basic purpose of a router -Computers that specialize in sending packets over the data network. They are responsible for interconnecting networks by selecting the best path for a packet to travel and forwarding packets to their destination . Routers are the network center -Routers generally have multiple network connections: -WAN connection to ISP -WAN connection to other remote sites -Multiple LAN connections Router as a Computer . Data is sent in form of packets between 2 end devices . Routers are used to direct packet to its destination Router as a Computer . Routers examine a packet’s destination IP address and determine the best path by enlisting the aid of a routing table Router as a Computer . Two major groups of Router Interfaces LAN Interfaces: .Are used to connect router to LAN network .Has a layer 2 MAC address .Can be assigned a Layer 3 IP address .Usually consist of an RJ-45 jack . -

Configuring Static IP Unicast Routing
Configuring Static IP Unicast Routing This chapter describes how to configure IP Version 4 (IPv4) static IP unicast routing on the switch. Static routing is supported only on switched virtual interfaces (SVIs) and not on physical interfaces. The switch does not support routing protocols. Restrictions for Static IP Unicast Routing By default, static IP routing is disabled on the switch. Information About Configuring Static IP Unicast Routing Note: When configuring routing parameters on the switch and to allocate system resources to maximize the number of unicast routes allowed, use the sdm prefer lanbase-routing global configuration command to set the Switch Database Management (SDM) feature to the routing template. IP Routing In some network environments, VLANs are associated with individual networks or subnetworks. In an IP network, each subnetwork is mapped to an individual VLAN. Configuring VLANs helps control the size of the broadcast domain and keeps local traffic local. However, network devices in different VLANs cannot communicate with one another without a Layer 3 device to route traffic between the VLANs, referred to as inter-VLAN routing. You configure one or more routers to route traffic to the appropriate destination VLAN. Figure 83 on page 665 shows a basic routing topology. Switch A is in VLAN 10, and Switch B is in VLAN 20. The router has an interface in each VLAN. Figure 83 Routing Topology Example VLAN 10 VLAN 20 A Switch A Switch B Host C B Host Host When Host A in VLAN 10 needs to communicate with Host B in VLAN 10, it sends a 8071 packet addressed to that host. -

ISP Failover with Default Routes Using IP SLA Tracking
ISP Failover with Default Routes using IP SLA Tracking Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations Verify Troubleshoot Introduction This document describes how to configure WAN (or ISP) redundancies, wherein multiple WAN links terminate on the same end router. This document also explains how to configure Network Address Translation (NAT) when there are multiple ISP's for internet connectivity and you want seamless failover i.e. when Primary ISP goes down then Secondary takes over with correct NAT with the use of the secondary ISP's public IP address. Prerequisites Requirements There are no specific requirements for this document. Basic understanding of creating IP SLA and Static Routing.Configuration of IP SLA must be supported on the device and platform. Components Used This document is not restricted to specific software and hardware versions. It applies to all Cisco routers that run Cisco IOS and where IP SLA and Track can be configured. The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If the network is live, make sure that you understand the potential impact of any command. Configure Network Diagram Configurations ISP 1 and ISP 2 directly connect to the Internet. For test purposes, use the IP address 10.10.10.10 as a reference to Internet. Customer Edge Router Configurations Interface Configurations interface GigabitEthernet0/0/1 description PRIMARY LINK TO ISP 1 ip address 10.0.12.1 255.255.255.252 ip nat outside negotiation auto interface GigabitEthernet0/0/0 description BACKUP LINK TO ISP 2 ip address 10.0.13.1 255.255.255.252 ip nat outside negotiation auto Track, IP SLA and Default Route Configurations. -

TCP/IP Routing and Workload Balancing
IBM i 7.2 Networking TCP/IP routing and workload balancing IBM Note Before using this information and the product it supports, read the information in “Notices” on page 33. This edition applies to IBM i 7.2 (product number 5770-SS1) and to all subsequent releases and modifications until otherwise indicated in new editions. This version does not run on all reduced instruction set computer (RISC) models nor does it run on CISC models. This document may contain references to Licensed Internal Code. Licensed Internal Code is Machine Code and is licensed to you under the terms of the IBM License Agreement for Machine Code. © Copyright International Business Machines Corporation 1998, 2013. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents TCP/IP routing and workload balancing..................................................................1 What's new for IBM i 7.2..............................................................................................................................1 PDF file for TCP/IP routing and workload balancing...................................................................................1 TCP/IP routing functions by release............................................................................................................2 Packet processing........................................................................................................................................ 2 General routing rules.................................................................................................................................. -

Using the Management Ethernet Interface
CHAPTER 10 Using the Management Ethernet Interface The Cisco ASR 1000 Series Routers have one Gigabit Ethernet Management Ethernet interface on each Route Processor. Finding Feature Information in This Module Your software release might not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the “Feature Information for Using the Management Ethernet Interface” section on page 10-8. Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required. Contents This guide covers the following topics: • Gigabit Ethernet Management Interface Overview, page 10-1 • Gigabit Ethernet Port Numbering, page 10-2 • Gigabit Ethernet Port Numbering, page 10-2 • IP Address Handling in ROMmon and the Management Ethernet Port, page 10-2 • Gigabit Ethernet Management Interface VRF, page 10-3 • Common Ethernet Management Tasks, page 10-3 Gigabit Ethernet Management Interface Overview The purpose of this interface is to allow users to perform management tasks on the router; it is basically an interface that should not and often cannot forward network traffic but can otherwise access the router, often via Telnet and SSH, and perform most management tasks on the router. The interface is most useful before a router has begun routing, or in troubleshooting scenarios when the SPA interfaces are inactive.