IP Addressing Design Issues and Protocols
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
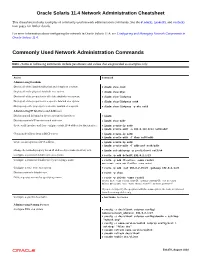
Oracle® Solaris 11.4 Network Administration Cheatsheet
Oracle Solaris 11.4 Network Administration Cheatsheet This cheatsheet includes examples of commonly used network administration commands. See the dladm(8), ipadm(8), and route(8) man pages for further details. For more information about configuring the network in Oracle Solaris 11.4, see Configuring and Managing Network Components in Oracle Solaris 11.4. Commonly Used Network Administration Commands Note - Some of following commands include parameters and values that are provided as examples only. Action Command Administering Datalinks Display all of the datalinks (physical and virtual) on a system. # dladm show-link Display all of the physical datalinks on a system. # dladm show-phys Display all of the properties for all of the datalinks on a system. # dladm show-linkprop Display all of the properties for a specific datalink on a system. # dladm show-linkprop net0 Display a specific property for a specific datalink on a system. # dladm show-linkprop -p mtu net0 Administering IP Interfaces and Addresses Display general information about a system's IP interfaces. # ipadm Display a system's IP interfaces and addresses. # ipadm show-addr Create an IP interface and then configure a static IPv4 address for that interface. # ipadm create-ip net0 # ipadm create-addr -a 203.0.113.0/24 net0/addr Obtain an IP address from a DHCP server. # ipadm create-ip net0 # ipadm create-addr -T dhcp net0/addr Create an auto-generated IPv6 address. # ipadm create-ip net0 # ipadm create-addr -T addrconf net0/addr Change the netmask property for an IP address object name (net3/v4) to 8. # ipadm set-addrprop -p prefixlen=8 net3/v4 Configure a persistent default route on a system. -

Empirical Analysis of the Effects and the Mitigation of Ipv4 Address Exhaustion
TECHNISCHE UNIVERSITÄT BERLIN FAKULTÄT FÜR ELEKTROTECHNIK UND INFORMATIK LEHRSTUHL FÜR INTELLIGENTE NETZE UND MANAGEMENT VERTEILTER SYSTEME Empirical Analysis of the Effects and the Mitigation of IPv4 Address Exhaustion vorgelegt von M.Sc. Philipp Richter geboren in Berlin von der Fakultät IV – Elektrotechnik und Informatik der Technischen Universität Berlin zur Erlangung des akademischen Grades DOKTOR DER NATURWISSENSCHAFTEN -DR. RER. NAT.- genehmigte Dissertation Promotionsausschuss: Vorsitzender: Prof. Dr.-Ing. Sebastian Möller, Technische Universität Berlin Gutachterin: Prof. Anja Feldmann, Ph.D., Technische Universität Berlin Gutachter: Prof. Vern Paxson, Ph.D., University of California, Berkeley Gutachter: Prof. Steve Uhlig, Ph.D., Queen Mary University of London Tag der wissenschaftlichen Aussprache: 2. August 2017 Berlin 2017 Abstract IP addresses are essential resources for communication over the Internet. In IP version 4, an address is represented by 32 bits in the IPv4 header; hence there is a finite pool of roughly 4B addresses available. The Internet now faces a fundamental resource scarcity problem: The exhaustion of the available IPv4 address space. In 2011, the Internet Assigned Numbers Authority (IANA) depleted its pool of available IPv4 addresses. IPv4 scarcity is now reality. In the subsequent years, IPv4 address scarcity has started to put substantial economic pressure on the networks that form the Internet. The pools of available IPv4 addresses are mostly depleted and today network operators have to find new ways to satisfy their ongoing demand for IPv4 addresses. Mitigating IPv4 scarcity is not optional, but mandatory: Networks facing address shortage have to take action in order to be able to accommodate additional subscribers and customers. Thus, if not confronted, IPv4 scarcity has the potential to hinder further growth of the Internet. -

74 Network Addressin
CSC414 Communication Models Computer Network Client/Server Model System - Server Program Fundamentals Addressing - Runs on computer that has files to be shared - Web Server, Mail Server, Warcraft Server Server Client - Client Program Apache Firefox - Computer that needs to access remote files - Web Browser, Mail Client, World of Warcraft Digital Forensics Center Department of Computer Science and Statics THINK BIG WE DO Peer to Peer Model - Single program U R I - makes files on computer available Peer Peer http://www.forensics.cs.uri.edu - accesses remote files LimeWire LimeWire Addressing Data Domain Names http://www.uri.edu:80/courses/cs/index.html Hierarchical system for name creation and registration protocol computer directory file - Created so users would not have to memorize IP addresses address port - Global domain name system provides global scope for user friendly addresses OSI Model Domain Name Application Layer Country Codes Country Domain Type Common .us United States .biz Business File requested by client Presentation Layer Top Level .uk United Kingdom .com Commercial .au Australia .edu US Educational Folder or directory path on server Session Layer Maps to special directory used by Port Domains .cn China .gov US Government application .mil Military Transport Layer .ca Canada Mailbox on the machine the .de Germany .net Network server or peer is checking Top level Network Layer .org Nonprofit Organization IP Address (Logical) domains are .ru Russia What machine has the shared data .info Info Domain approved by .in India Where -

AX1800 Wifi 6 Router Model RAX15
User Manual AX1800 WiFi 6 Router Model RAX15 NETGEAR, Inc. August 2021 350 E. Plumeria Drive 202-12029-02 San Jose, CA 95134, USA AX1800 WiFi 6 Router Support and Community Visit netgear.com/support to get your questions answered and access the latest downloads. You can also check out our NETGEAR Community for helpful advice at community.netgear.com. Regulatory and Legal Si ce produit est vendu au Canada, vous pouvez accéder à ce document en français canadien à https://www.netgear.com/support/download/. (If this product is sold in Canada, you can access this document in Canadian French at https://www.netgear.com/support/download/.) For regulatory compliance information including the EU Declaration of Conformity, visit https://www.netgear.com/about/regulatory/. See the regulatory compliance document before connecting the power supply. For NETGEAR’s Privacy Policy, visit https://www.netgear.com/about/privacy-policy. By using this device, you are agreeing to NETGEAR’s Terms and Conditions at https://www.netgear.com/about/terms-and-conditions. If you do not agree, return the device to your place of purchase within your return period. Trademarks ©NETGEAR, Inc. NETGEAR and the NETGEAR Logo are trademarks of NETGEAR, Inc. Any non-NETGEAR trademarks are used for reference purposes only. 2 Contents Chapter 1 Hardware Setup Unpack your router...............................................................................9 Front panel LEDs and buttons..........................................................10 Rear panel and side panel.................................................................12 -

Unicast Multicast IP Multicast Introduction
Outline 11: ❒ IP Multicast ❒ Multicast routing IP Multicast ❍ Design choices ❍ Distance Vector Multicast Routing Protocol (DVMRP) Last Modified: ❍ Core Based Trees (CBT) ❍ Protocol Independent Multicast (PIM) 4/9/2003 1:15:00 PM ❍ Border Gateway Multicast Protocol (BGMP) ❒ Issues in IP Multicast Deplyment Based on slides by Gordon Chaffee Berkeley Multimedia Research Center URL: http://bmrc.berkeley.edu/people/chaffee 4: Network Layer 4a-1 4: Network Layer 4a-2 What is multicast? Unicast ❒ ❒ 1 to N communication Problem Sender ❍ ❒ Nandwidth-conserving technology that Sending same data to reduces traffic by simultaneously many receivers via unicast is inefficient delivering a single stream of information to R multiple recipients ❒ Example ❒ Examples of Multicast ❍ Popular WWW sites ❍ Network hardware efficiently supports become serious multicast transport bottlenecks • Example: Ethernet allows one packet to be received by many hosts ❍ Many different protocols and service models • Examples: IETF IP Multicast, ATM Multipoint 4: Network Layer 4a-3 4: Network Layer 4a-4 Multicast IP Multicast Introduction ❒ Efficient one to many Sender ❒ Efficient one to many data distribution data distribution ❍ Tree style data distribution ❍ Packets traverse network links only once R ❒ Location independent addressing ❍ IP address per multicast group ❒ Receiver oriented service model ❍ Applications can join and leave multicast groups ❍ Senders do not know who is listening ❍ Similar to television model ❍ Contrasts with telephone network, ATM 4: Network Layer -

Manual Update Configuring a Default Gateway
S3290 Manual Update Configuring a Default Gateway The following information is to be included with the S3290 Web User Guide. IP Configuration Configure the S3290-managed IPv4 information from Configuration > System > IP as one of the first steps. The S3290 supports an IPv4 / IPv6 dual stack. The S3290 can be assigned IP address statically or dynamically using DHCP. Here you can configure IP basic settings, IP interfaces and IP routes. Up to 8 interfaces and up to 32 routes are supported. IP Routes Click the Add Route button to display the editable fields: Delete Select this option to delete an existing IP route. Network The destination IP network or host address of this route. Valid format is dotted decimal notation or a valid IPv6 notation. A default route can use the value 0.0.0.0 or IPv6 :: notation. Mask Length The destination IP network or host mask, in number of bits (prefix length). It defines how much of a network address that must match, in order to qualify for this route. Valid values are 0 - 32 bits for IPv4 routes or 0 - 128 for IPv6 routes. Only a default route will have a mask length of 0 (as it will match anything). Gateway The IP address of the IP gateway. Valid format is dotted decimal notation or a valid IPv6 notation. The Gateway and Network must be of the same type. It may be necessary to add a static route if a default gateway is required or if the device does not reside within the same network. Routing can then be enabled at System > IP > IP Configuration. -

Emulation of the IP Core Network for Testing of the Service GPRS Support Node (SGSN) Routing Application
Technical report, IDE0959, November 2009 Emulation of the IP Core Network for Testing of the Service GPRS Support Node (SGSN) Routing Application Master’s Thesis in Computer Network Engineering Hossein Torkaman School of Information Science, Computer and Electrical Engineering Halmstad University Emulation of the IP Core Network for Testing of the Service GPRS Support Node (SGSN) Routing Application Master’s thesis in Computer Network Engineering School of Information Science, Computer and Electrical Engineering Halmstad University Box 823, S-301 18 Halmstad, Sweden November 2009 Description of cover page picture: IP Core Network picture on GPRS Networks. Preface The following report is based on the data and information gathered through literature studies, Ericsson’s Intranet documents and other several GPRS standards published by 3rd Generation Partnership Project (3GPP), observations, emulating different IP core network scenarios, meetings and executed experiments during December 2008 - August 2009 at Ericsson AB Lindholmen. The input martial to this thesis formed primarily by Internet Protocols and Drivers section in Product Development Department Packet Core at Ericsson AB, Göteborg, Sweden with leadership of Gunilla Zachrisson, my supervisor, to whom I should give an immense thank you due to her kind guidance on each phase of project and for her valuable supports on the implementation of improvements. I am also thankful to my manager, Matthew Crockett, who also made me feel welcomed at Ericsson AB Lindholmen. A big thanks is also directed to my supervisor at Halmstad University, Tony Larsson, for pointing me in the right direction and for the feedback regarding the performance of the project. I would also like to use this opportunity to thank Colin Taylor and Daniel Nilsson and all other colleagues at Ericsson, for interrupting their busy schedules in order to provide me with their technical feedback and experience. -

Lab 2.8.1: Basic Static Route Configuration
Lab 2.8.1: Basic Static Route Configuration Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 172.16.3.1 255.255.255.0 N/A R1 S0/0/0 172.16.2.1 255.255.255.0 N/A Fa0/0 172.16.1.1 255.255.255.0 N/A R2 S0/0/0 172.16.2.2 255.255.255.0 N/A S0/0/1 192.168.1.2 255.255.255.0 N/A FA0/0 192.168.2.1 255.255.255.0 N/A R3 S0/0/1 192.168.1.1 255.255.255.0 N/A PC1 NIC 172.16.3.10 255.255.255.0 172.16.3.1 PC2 NIC 172.16.1.10 255.255.255.0 172.16.1.1 PC3 NIC 192.168.2.10 255.255.255.0 192.168.2.1 Learning Objectives Upon completion of this lab, you will be able to: • Cable a network according to the Topology Diagram. • Erase the startup configuration and reload a router to the default state. • Perform basic configuration tasks on a router. All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 20 CCNA Exploration Routing Protocols and Concepts: Static Routing Lab 2.8.1: Basic Static Route Configuration • Interpret debug ip routing output. • Configure and activate Serial and Ethernet interfaces. • Test connectivity. • Gather information to discover causes for lack of connectivity between devices. • Configure a static route using an intermediate address. -

Configure BGP to Advertise a Default Route on Cisco Nexus Switches
Configure BGP to advertise a Default Route on Cisco Nexus Switches Contents Introduction Prerequisites Requirements Components Used Configure Network Command Redistribute and Default-Information Originate Commands Default-Originate Command Introduction This document describes different approaches to configure Border Gateway Protocol (BGP) to advertise a Default Route (0.0.0.0/0 network prefix) to BGP neighbors on Cisco Nexus NX-OS based Switches. Prerequisites Requirements Cisco recommends that you have knowledge of these topics: ● Nexus NX-OS Software. ● Routing Protocols, specifically BGP. Components Used The information in this document is based on Cisco Nexus 7000 with NX-OS version 7.3(0)D1(1) The outputs in this document were taken from devices in a specific lab environment. All devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command. Configure Network Command The network 0.0.0.0/0 command injects the default route in the BGP RIB (BGP Routing Information Base). The prerequisite is to have the default route in the Routing Table via any other Routing Protocol or manually configured with a Static Route. Once in the BGP RIB, the default route is advertised to all BGP neighbors unless specifically denied by an outbound filter configured per neighbor. BGP configuration as seen in the show running-config output. Nexus BGP Configuration Nexus# show running-config bgp !Command: show running-config bgp !Time: Tue Dec 4 01:27:43 2018 version 7.3(0)D1(1) feature bgp router bgp 64512 address-family ipv4 unicast network 0.0.0.0/0 neighbor 10.1.3.3 remote-as 64512 address-family ipv4 unicast In this example, Nexus receives the default route from EIGRP protocol. -

NAT++: Address Sharing in Ipv4 - the Internet Protocol Journal, Volume 13, No.2 - Cisco 10/8/18, 08�03
NAT++: Address Sharing in IPv4 - The Internet Protocol Journal, Volume 13, No.2 - Cisco 10/8/18, 0803 NAT++: Address Sharing in IPv4 - The Internet Protocol Journal, Volume 13, No.2 HOME by Geoff Huston, APNIC ABOUT CISCO In this article I examine the topic that was discussed in a session at the 74th meeting of the PRESS Internet Engineering Task Force (IETF) in March 2009, about Address Sharing (the SHARA BOF) [0], and look at the evolution of Network Address Translation (NAT) architectures in the THE INTERNET PROTOCOL face of the forthcoming depletion of the unallocated IPv4 address pool. JOURNAL Within the next couple of years we will run out of the current supply of IPv4 addresses. As of the ISSUES time of writing this article, the projected date when the Internet Assigned Numbers Authority (IANA) pool will be depleted is August 3, 2011, and the first Regional Internet Registry (RIR) will VOLUME 13, NUMBER 2, JUNE deplete its address pool about March 20, 2012. 2010 Irrespective of the precise date of depletion, the current prediction is that the consumption rate of addresses at the time when the free pool of addresses is exhausted will probably be running at From the Editor some 220 million addresses per year, indicating a deployment rate of some 170–200 million new Address Sharing services per year using IPv4. The implication is that the Internet will exhaust its address pool while operating its growth engines at full speed. Implementing DNSSEC How quickly will IPv6 come to the rescue? Even the most optimistic forecast of IPv6 uptake for Book Review the global Internet is measured in years rather than months following exhaustion, and the more pessimistic forecasts extend into multiple decades. -

Internet Deep Dive Webinar Handout Copy
Introduction to IT Networking Featuring Robert Lastinger from Distech Controls Agenda • Internet • Static IP • DHCP • IP Routing • Gateway • Subnet • NAT • DNS and Hosting • External Access: Firewalls, VPNs Internet Internet Layer The Internet layer is responsible for placing data that needs to be transmitted into data packets known as IP datagrams. These will contain the source and destination addresses for the data within. This layer is also responsible for routing the IP datagrams. The main protocols included at Internet layer are IP (Internet Protocol), ICMP (Internet Control Message Protocol), ARP (Address Resolution Protocol), RARP (Reverse Address Resolution Protocol) and IGMP (Internet Group Management Protocol). Terms you will commonly hear that relate to this layer are IPV4 and IPV6. For the purposes of this training we will only be talking about IPV4. IP Addressing 192.168.99.11 192.168.12.1 192.168.12.101 192.168.12.100 192.168.12.2 Network mask: 255.255.255.0 (/24) Default gateway: 192.168.12.1 Notable IP Addresses • Loopback/localhost (127.0.0.0/8) • Private network (10.0.0.0/8, 192.168.0.0/16, 172.16.0.0/12) • Network source address (0.0.0.0/8) • Reserved (anything between 224.0.0.0 and 255.255.255.254) • Limited broadcast (255.255.255.255) • Last IP in a subnet ONS-S8 and ONS-NC600 ONS-C1601pi ONS-YX Network ONS-C401i Router/core switch ONS-C2410p ONS-YX Optical fiber ONS-C401i ONS-C401i Ethernet Static IP IPV4 DHCP (Dynamic Host Configuration Protocol) DHCP Lease (Dynamic vs Reserved) Static IP Subnet Gateway DNS ( Domain Name System) DHCP DHCP DHCP – is a client/server protocol that automatically provides an Internet Protocol (IP) host with its IP address and other related configuration information such as the subnet mask and default gateway. -

A Look at the Ipv4 Consumption Data
A look at the IPv4 consumption data • Use a fundamental assumption that the driver for address consumption is the public Internet, and that the growth of the Internet is reflected in address consumption demands • Adjust the model to include each individual RIR’s allocation behaviour over time • Set the ‘exhaustion’ date at the point when any RIR cannot honour an address request Advertised and Unadvertised Addresses Advertised Address Growth Unadvertised / Advertised Ratio The Address Consumption Model Total demand level The Address Consumption Model Combined RIR Model The Address Consumption Model Full Model Some Projections from this Model • IANA Pool exhaustion 15 March 2012 • RIR Pool exhaustion 4 June 2013 gory details and code: http://www.potaroo.net/tools/ipv4 Commentary • These address consumption models assumes an orderly procession right up to the point of effective exhaustion of the unallocated IPv4 address pool –This is highly unlikely to eventuate! – Within the current policy framework a more likely industry response will be accelerating demands as imminent exhaustion of the unallocated address pool becomes more visible – It is not easy to model such “last chance run” behaviours based purely on the historical address allocation and BGP data • Some other form of modelling of social and market behaviour of a last chance run would be better positioned to make some guesstimates here Early signs of a rush? Commentary • Exhaustion of the IPv4 unallocated address pool does not imply complete unavailability of IPv4 address resources