REDDIG II – Computer Networking Training
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
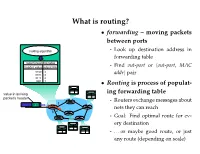
What Is Routing?
What is routing? • forwarding – moving packets between ports - Look up destination address in forwarding table - Find out-port or hout-port, MAC addri pair • Routing is process of populat- ing forwarding table - Routers exchange messages about nets they can reach - Goal: Find optimal route for ev- ery destination - . or maybe good route, or just any route (depending on scale) Routing algorithm properties • Static vs. dynamic - Static: routes change slowly over time - Dynamic: automatically adjust to quickly changing network conditions • Global vs. decentralized - Global: All routers have complete topology - Decentralized: Only know neighbors & what they tell you • Intra-domain vs. Inter-domain routing - Intra-: All routers under same administrative control - Intra-: Scale to ∼100 networks (e.g., campus like Stanford) - Inter-: Decentralized, scale to Internet Optimality A 6 1 3 2 F 1 E B 4 1 9 C D • View network as a graph • Assign cost to each edge - Can be based on latency, b/w, utilization, queue length, . • Problem: Find lowest cost path between two nodes - Must be computed in distributed way Distance Vector • Local routing algorithm • Each node maintains a set of triples - (Destination, Cost, NextHop) • Exchange updates w. directly connected neighbors - periodically (on the order of several seconds to minutes) - whenever table changes (called triggered update) • Each update is a list of pairs: - (Destination, Cost) • Update local table if receive a “better” route - smaller cost - from newly connected/available neighbor • Refresh existing -

Control Plane Overview Subnet 1.2 Subnet 1.2
The Network Layer: Control Plane Overview Subnet 1.2 Subnet 1.2 R3 R2 R6 Interior Subnet 1.2 R5 Subnet 1.2 Subnet 1.2 R7 1. Routing Algorithms: Link-State, Distance Vector R8 R4 R1 Subnet 1.2 Dijkstra’s algorithm, Bellman-Ford Algorithm Exterior Subnet 1.2 Subnet 1.2 2. Routing Protocols: OSPF, BGP Raj Jain 3. SDN Control Plane Washington University in Saint Louis 4. ICMP Saint Louis, MO 63130 5. SNMP [email protected] Audio/Video recordings of this lecture are available on-line at: Note: This class lecture is based on Chapter 5 of the textbook (Kurose and Ross) and the figures provided by the authors. http://www.cse.wustl.edu/~jain/cse473-16/ Washington University in St. Louis http://www.cse.wustl.edu/~jain/cse473-16/ ©2016 Raj Jain Washington University in St. Louis http://www.cse.wustl.edu/~jain/cse473-16/ ©2016 Raj Jain 5-1 5-2 Network Layer Functions Overview Routing Algorithms T Forwarding: Deciding what to do with a packet using 1. Graph abstraction a routing table Data plane 2. Distance Vector vs. Link State T Routing: Making the routing table Control Plane 3. Dijkstra’s Algorithm 4. Bellman-Ford Algorithm Washington University in St. Louis http://www.cse.wustl.edu/~jain/cse473-16/ ©2016 Raj Jain Washington University in St. Louis http://www.cse.wustl.edu/~jain/cse473-16/ ©2016 Raj Jain 5-3 5-4 Rooting or Routing Routeing or Routing T Rooting is what fans do at football games, what pigs T Routeing: British do for truffles under oak trees in the Vaucluse, and T Routing: American what nursery workers intent on propagation do to T Since Oxford English Dictionary is much heavier than cuttings from plants. -

Mainframe OSA Connectivity and Routing in a Cisco Environment Junnie Sadler Cisco Systems
Mainframe OSA Connectivity and Routing in a Cisco Environment Junnie Sadler Cisco Systems August 02, 2010 Objective • Give audience members exposure to the router/networking world beyond the mainframe • Impart an appreciation of network design issues • Present the network as a whole vs Box Centric • Enable greater ability to troubleshoot connectivity/performance problems • Not to make CCIE‟s out of anyone • Not to sell Cisco equipment 2 SHARE Boston 2010© Copyright Cisco Systems, Inc. 2008 All rights reserved Overview • Background – IP From the Mainframe's View • Mainframe IP Communications ` Hypersockets , XCF • IP Routing Protocols: Static, RIP (v1 & v2), OSPF • Network Design Considerations: 3 SHARE Boston 2010© Copyright Cisco Systems, Inc. 2008 All rights reserved Mainframe view of the Network • The network is just a big cloud • Stuff happens ? ? ? ? ? ? ? ? ? 4 SHARE Boston 2010© Copyright Cisco Systems, Inc. 2008 All rights reserved Network view of the Mainframe • Sysplex – isn‟t that a big movie theater • VIPA – that‟s a poisonous snake, right? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? • LPAR – is that something Tiger Woods worries about? 5 SHARE Boston 2010© Copyright Cisco Systems, Inc. 2008 All rights reserved IP Connectivity Evolution 10 Gig OSA OSA Express OSA CIP/CPA 3172 6 SHARE Boston 2010© Copyright Cisco Systems, Inc. 2008 All rights reserved Background • - Mainframe as a IP Server • - Driving Factors toward IP Routing Requirements: • New Applications are IP Based • QoS (Quality of Service) required for these Applications • Old SNA Applications being re-written or replaced with IP transport (EE) Enterprise Extender • TN3270 Application Requirements (IP to & from the MF) • Data Replication – IP Based High Performance Requirements • VIPA (Virtual IP Address) • IP Load Balancing between Sysplex 7 SHARE Boston 2010© Copyright Cisco Systems, Inc. -

Chapter 6: Chapter 6: Implementing a Border Gateway Protocol Solution Y
Chapter 6: Implementing a Border Gateway Protocol Solution for ISP Connectivity CCNP ROUTE: Implementing IP Routing ROUTE v6 Chapter 6 © 2007 – 2010, Cisco Systems, Inc. All rights reserved. Cisco Public 1 Chapter 6 Objectives . Describe basic BGP terminology and operation, including EBGP and IBGP. ( 3) . Configure basic BGP. (87) . Typical Issues with IBGP and EBGP (104) . Verify and troubleshoot basic BGP. (131) . Describe and configure various methods for manipulating path selection. (145) . Describe and configure various methods of filtering BGP routing updates. (191) Chapter 6 © 2007 – 2010, Cisco Systems, Inc. All rights reserved. Cisco Public 2 BGP Terminology, Concepts, and Operation Chapter 6 © 2007 – 2010, Cisco Systems, Inc. All rights reserved. Cisco Public 3 IGP versus EGP . Interior gateway protocol (IGP) • A routing protocol operating within an Autonomous System (AS). • RIP, OSPF, and EIGRP are IGPs. Exterior gateway protocol (EGP) • A routing protocol operating between different AS. • BGP is an interdomain routing protocol (IDRP) and is an EGP. Chapter 6 © 2007 – 2010, Cisco Systems, Inc. All rights reserved. Cisco Public 4 Autonomous Systems (AS) . An AS is a group of routers that share similar routing policies and operate within a single administrative domain. An AS typically belongs to one organization. • A singgpgyp()yle or multiple interior gateway protocols (IGP) may be used within the AS. • In either case, the outside world views the entire AS as a single entity. If an AS connects to the public Internet using an exterior gateway protocol such as BGP, then it must be assigned a unique AS number which is managed by the Internet Assigned Numbers Authority (IANA). -

The Routing Table V1.12 – Aaron Balchunas 1
The Routing Table v1.12 – Aaron Balchunas 1 - The Routing Table - Routing Table Basics Routing is the process of sending a packet of information from one network to another network. Thus, routes are usually based on the destination network, and not the destination host (host routes can exist, but are used only in rare circumstances). To route, routers build Routing Tables that contain the following: • The destination network and subnet mask • The “next hop” router to get to the destination network • Routing metrics and Administrative Distance The routing table is concerned with two types of protocols: • A routed protocol is a layer 3 protocol that applies logical addresses to devices and routes data between networks. Examples would be IP and IPX. • A routing protocol dynamically builds the network, topology, and next hop information in routing tables. Examples would be RIP, IGRP, OSPF, etc. To determine the best route to a destination, a router considers three elements (in this order): • Prefix-Length • Metric (within a routing protocol) • Administrative Distance (between separate routing protocols) Prefix-length is the number of bits used to identify the network, and is used to determine the most specific route. A longer prefix-length indicates a more specific route. For example, assume we are trying to reach a host address of 10.1.5.2/24. If we had routes to the following networks in the routing table: 10.1.5.0/24 10.0.0.0/8 The router will do a bit-by-bit comparison to find the most specific route (i.e., longest matching prefix). -
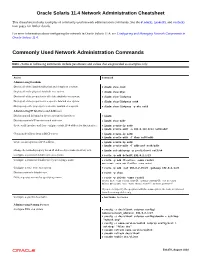
Oracle® Solaris 11.4 Network Administration Cheatsheet
Oracle Solaris 11.4 Network Administration Cheatsheet This cheatsheet includes examples of commonly used network administration commands. See the dladm(8), ipadm(8), and route(8) man pages for further details. For more information about configuring the network in Oracle Solaris 11.4, see Configuring and Managing Network Components in Oracle Solaris 11.4. Commonly Used Network Administration Commands Note - Some of following commands include parameters and values that are provided as examples only. Action Command Administering Datalinks Display all of the datalinks (physical and virtual) on a system. # dladm show-link Display all of the physical datalinks on a system. # dladm show-phys Display all of the properties for all of the datalinks on a system. # dladm show-linkprop Display all of the properties for a specific datalink on a system. # dladm show-linkprop net0 Display a specific property for a specific datalink on a system. # dladm show-linkprop -p mtu net0 Administering IP Interfaces and Addresses Display general information about a system's IP interfaces. # ipadm Display a system's IP interfaces and addresses. # ipadm show-addr Create an IP interface and then configure a static IPv4 address for that interface. # ipadm create-ip net0 # ipadm create-addr -a 203.0.113.0/24 net0/addr Obtain an IP address from a DHCP server. # ipadm create-ip net0 # ipadm create-addr -T dhcp net0/addr Create an auto-generated IPv6 address. # ipadm create-ip net0 # ipadm create-addr -T addrconf net0/addr Change the netmask property for an IP address object name (net3/v4) to 8. # ipadm set-addrprop -p prefixlen=8 net3/v4 Configure a persistent default route on a system. -

Understanding Linux Internetworking
White Paper by David Davis, ActualTech Media Understanding Linux Internetworking In this Paper Introduction Layer 2 vs. Layer 3 Internetworking................ 2 The Internet: the largest internetwork ever created. In fact, the Layer 2 Internetworking on term Internet (with a capital I) is just a shortened version of the Linux Systems ............................................... 3 term internetwork, which means multiple networks connected Bridging ......................................................... 3 together. Most companies create some form of internetwork when they connect their local-area network (LAN) to a wide area Spanning Tree ............................................... 4 network (WAN). For IP packets to be delivered from one Layer 3 Internetworking View on network to another network, IP routing is used — typically in Linux Systems ............................................... 5 conjunction with dynamic routing protocols such as OSPF or BGP. You c an e as i l y use Linux as an internetworking device and Neighbor Table .............................................. 5 connect hosts together on local networks and connect local IP Routing ..................................................... 6 networks together and to the Internet. Virtual LANs (VLANs) ..................................... 7 Here’s what you’ll learn in this paper: Overlay Networks with VXLAN ....................... 9 • The differences between layer 2 and layer 3 internetworking In Summary ................................................. 10 • How to configure IP routing and bridging in Linux Appendix A: The Basics of TCP/IP Addresses ....................................... 11 • How to configure advanced Linux internetworking, such as VLANs, VXLAN, and network packet filtering Appendix B: The OSI Model......................... 12 To create an internetwork, you need to understand layer 2 and layer 3 internetworking, MAC addresses, bridging, routing, ACLs, VLANs, and VXLAN. We’ve got a lot to cover, so let’s get started! Understanding Linux Internetworking 1 Layer 2 vs. -

The Network Layer: Control Plane
CHAPTER 5 The Network Layer: Control Plane In this chapter, we’ll complete our journey through the network layer by covering the control-plane component of the network layer—the network-wide logic that con- trols not only how a datagram is forwarded among routers along an end-to-end path from the source host to the destination host, but also how network-layer components and services are configured and managed. In Section 5.2, we’ll cover traditional routing algorithms for computing least cost paths in a graph; these algorithms are the basis for two widely deployed Internet routing protocols: OSPF and BGP, that we’ll cover in Sections 5.3 and 5.4, respectively. As we’ll see, OSPF is a routing protocol that operates within a single ISP’s network. BGP is a routing protocol that serves to interconnect all of the networks in the Internet; BGP is thus often referred to as the “glue” that holds the Internet together. Traditionally, control-plane routing protocols have been implemented together with data-plane forwarding functions, monolithi- cally, within a router. As we learned in the introduction to Chapter 4, software- defined networking (SDN) makes a clear separation between the data and control planes, implementing control-plane functions in a separate “controller” service that is distinct, and remote, from the forwarding components of the routers it controls. We’ll cover SDN controllers in Section 5.5. In Sections 5.6 and 5.7 we’ll cover some of the nuts and bolts of managing an IP network: ICMP (the Internet Control Message Protocol) and SNMP (the Simple Network Management Protocol). -

Overview of Routing Security Landscape for the Quilt Member Meeting, Winter 2019 Mark Beadles, CISO, Oarnet [email protected] BGP IDLE
Overview of Routing Security Landscape for the Quilt Member Meeting, Winter 2019 Mark Beadles, CISO, OARnet [email protected] BGP IDLE CONNECT ACTIVE OPEN OPEN SENT CONFIRM ESTAB- LISHED 2/13/2019 Routing Security Landscape - The Quilt 2 Overview of Routing Security Landscape • Background • Threat environment • Current best practices • Gaps 2/13/2019 Routing Security Landscape - The Quilt 3 Background - Definitions • BGP • Border Gateway Protocol, an exterior path-vector gateway routing protocol • Autonomous System & Autonomous System Numbers • Collection of IP routing prefixes under control of a network operator on behalf of a single administrative domain that presents a defined routing policy to the Internet • Assigned number for each AS e.g. AS600 2/13/2019 Routing Security Landscape - The Quilt 4 Background - The BGP Security Problem By design, routers running BGP accept advertised routes from other BGP routers by default. (BGP was written under the assumption that no one would lie about the routes, so there’s no process for verifying the published announcements.) This allows for automatic and decentralized routing of traffic across the Internet, but it also leaves the Internet potentially vulnerable to accidental or malicious disruption, known as BGP hijacking. Due to the extent to which BGP is embedded in the core systems of the Internet, and the number of different networks operated by many different organizations which collectively make up the Internet, correcting this vulnerabilityis a technically and economically challenging problem. 2/13/2019 Routing Security Landscape - The Quilt 5 Background – BGP Terminology • Bogons • Objects (addresses/prefixes/ASNs) that don't belong on the internet • Spoofing • Lying about your address. -

P2P Resource Sharing in Wired/Wireless Mixed Networks 1
INT J COMPUT COMMUN, ISSN 1841-9836 Vol.7 (2012), No. 4 (November), pp. 696-708 P2P Resource Sharing in Wired/Wireless Mixed Networks J. Liao Jianwei Liao College of Computer and Information Science Southwest University of China 400715, Beibei, Chongqing, China E-mail: [email protected] Abstract: This paper presents a new routing protocol called Manager-based Routing Protocol (MBRP) for sharing resources in wired/wireless mixed networks. MBRP specifies a manager node for a designated sub-network (called as a group), in which all nodes have the similar connection properties; then all manager nodes are employed to construct the backbone overlay network with ring topology. The manager nodes act as the proxies between the internal nodes in the group and the external world, that is not only for centralized management of all nodes to a certain extent, but also for avoiding the messages flooding in the whole network. The experimental results show that compared with Gnutella2, which uses super-peers to perform similar management work, the proposed MBRP has less lookup overhead including lookup latency and lookup hop count in the most of cases. Besides, the experiments also indicate that MBRP has well configurability and good scaling properties. In a word, MBRP has less transmission cost of the shared file data, and the latency for locating the sharing resources can be reduced to a great extent in the wired/wireless mixed networks. Keywords: wired/wireless mixed network, resource sharing, manager-based routing protocol, backbone overlay network, peer-to-peer. 1 Introduction Peer-to-Peer technology (P2P) is a widely used network technology, the typical P2P network relies on the computing power and bandwidth of all participant nodes, rather than a few gathered and dedicated servers for central coordination [1, 2]. -

IS-IS Client for BFD C-Bit Support
IS-IS Client for BFD C-Bit Support The Bidirectional Forwarding Detection (BFD) protocol provides short-duration detection of failures in the path between adjacent forwarding engines while maintaining low networking overheads. The BFD IS-IS Client Support feature enables Intermediate System-to-Intermediate System (IS-IS) to use Bidirectional Forwarding Detection (BFD) support, which improves IS-IS convergence as BFD detection and failure times are faster than IS-IS convergence times in most network topologies. The IS-IS Client for BFD C-Bit Support feature enables the network to identify whether a BFD session failure is genuine or is the result of a control plane failure due to a router restart. When planning a router restart, you should configure this feature on all neighboring routers. • Finding Feature Information, on page 1 • Prerequisites for IS-IS Client for BFD C-Bit Support, on page 1 • Information About IS-IS Client for BFD C-Bit Support, on page 2 • How to Configure IS-IS Client for BFD C-Bit Support, on page 2 • Configuration Examples for IS-IS Client for BFD C-Bit Support, on page 3 • Additional References, on page 4 • Feature Information for IS-IS Client for BFD C-Bit Support, on page 4 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table. -

Manual Update Configuring a Default Gateway
S3290 Manual Update Configuring a Default Gateway The following information is to be included with the S3290 Web User Guide. IP Configuration Configure the S3290-managed IPv4 information from Configuration > System > IP as one of the first steps. The S3290 supports an IPv4 / IPv6 dual stack. The S3290 can be assigned IP address statically or dynamically using DHCP. Here you can configure IP basic settings, IP interfaces and IP routes. Up to 8 interfaces and up to 32 routes are supported. IP Routes Click the Add Route button to display the editable fields: Delete Select this option to delete an existing IP route. Network The destination IP network or host address of this route. Valid format is dotted decimal notation or a valid IPv6 notation. A default route can use the value 0.0.0.0 or IPv6 :: notation. Mask Length The destination IP network or host mask, in number of bits (prefix length). It defines how much of a network address that must match, in order to qualify for this route. Valid values are 0 - 32 bits for IPv4 routes or 0 - 128 for IPv6 routes. Only a default route will have a mask length of 0 (as it will match anything). Gateway The IP address of the IP gateway. Valid format is dotted decimal notation or a valid IPv6 notation. The Gateway and Network must be of the same type. It may be necessary to add a static route if a default gateway is required or if the device does not reside within the same network. Routing can then be enabled at System > IP > IP Configuration.