Ipv6 Feature Overview and Configuration Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SIP Software for Avaya 1200 Series IP Deskphones-Administration
SIP Software for Avaya 1200 Series IP Deskphones-Administration Release 4.4 NN43170-601 Issue 06.05 Standard July 2015 © 2015 Avaya Inc. list of Heritage Nortel Products located at http://support.avaya.com/ All Rights Reserved. LicenseInfo under the link “Heritage Nortel Products” or such successor site as designated by Avaya. For Heritage Nortel Notice Software, Avaya grants You a license to use Heritage Nortel While reasonable efforts have been made to ensure that the Software provided hereunder solely to the extent of the authorized information in this document is complete and accurate at the time of activation or authorized usage level, solely for the purpose specified printing, Avaya assumes no liability for any errors. Avaya reserves in the Documentation, and solely as embedded in, for execution on, the right to make changes and corrections to the information in this or for communication with Avaya equipment. Charges for Heritage document without the obligation to notify any person or organization Nortel Software may be based on extent of activation or use of such changes. authorized as specified in an order or invoice. Documentation disclaimer Copyright “Documentation” means information published by Avaya in varying Except where expressly stated otherwise, no use should be made of mediums which may include product information, operating materials on this site, the Documentation, Software, Hosted Service, instructions and performance specifications that Avaya may generally or hardware provided by Avaya. All content on this site, the make available to users of its products and Hosted Services. documentation, Hosted Service, and the product provided by Avaya Documentation does not include marketing materials. -
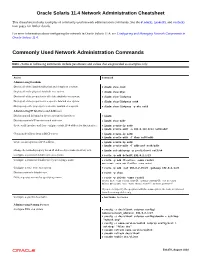
Oracle® Solaris 11.4 Network Administration Cheatsheet
Oracle Solaris 11.4 Network Administration Cheatsheet This cheatsheet includes examples of commonly used network administration commands. See the dladm(8), ipadm(8), and route(8) man pages for further details. For more information about configuring the network in Oracle Solaris 11.4, see Configuring and Managing Network Components in Oracle Solaris 11.4. Commonly Used Network Administration Commands Note - Some of following commands include parameters and values that are provided as examples only. Action Command Administering Datalinks Display all of the datalinks (physical and virtual) on a system. # dladm show-link Display all of the physical datalinks on a system. # dladm show-phys Display all of the properties for all of the datalinks on a system. # dladm show-linkprop Display all of the properties for a specific datalink on a system. # dladm show-linkprop net0 Display a specific property for a specific datalink on a system. # dladm show-linkprop -p mtu net0 Administering IP Interfaces and Addresses Display general information about a system's IP interfaces. # ipadm Display a system's IP interfaces and addresses. # ipadm show-addr Create an IP interface and then configure a static IPv4 address for that interface. # ipadm create-ip net0 # ipadm create-addr -a 203.0.113.0/24 net0/addr Obtain an IP address from a DHCP server. # ipadm create-ip net0 # ipadm create-addr -T dhcp net0/addr Create an auto-generated IPv6 address. # ipadm create-ip net0 # ipadm create-addr -T addrconf net0/addr Change the netmask property for an IP address object name (net3/v4) to 8. # ipadm set-addrprop -p prefixlen=8 net3/v4 Configure a persistent default route on a system. -

Is QUIC a Better Choice Than TCP in the 5G Core Network Service Based Architecture?
DEGREE PROJECT IN INFORMATION AND COMMUNICATION TECHNOLOGY, SECOND CYCLE, 30 CREDITS STOCKHOLM, SWEDEN 2020 Is QUIC a Better Choice than TCP in the 5G Core Network Service Based Architecture? PETHRUS GÄRDBORN KTH ROYAL INSTITUTE OF TECHNOLOGY SCHOOL OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE Is QUIC a Better Choice than TCP in the 5G Core Network Service Based Architecture? PETHRUS GÄRDBORN Master in Communication Systems Date: November 22, 2020 Supervisor at KTH: Marco Chiesa Supervisor at Ericsson: Zaheduzzaman Sarker Examiner: Peter Sjödin School of Electrical Engineering and Computer Science Host company: Ericsson AB Swedish title: Är QUIC ett bättre val än TCP i 5G Core Network Service Based Architecture? iii Abstract The development of the 5G Cellular Network required a new 5G Core Network and has put higher requirements on its protocol stack. For decades, TCP has been the transport protocol of choice on the Internet. In recent years, major Internet players such as Google, Facebook and CloudFlare have opted to use the new QUIC transport protocol. The design assumptions of the Internet (best-effort delivery) differs from those of the Core Network. The aim of this study is to investigate whether QUIC’s benefits on the Internet will translate to the 5G Core Network Service Based Architecture. A testbed was set up to emulate traffic patterns between Network Functions. The results show that QUIC reduces average request latency to half of that of TCP, for a majority of cases, and doubles the throughput even under optimal network conditions with no packet loss and low (20 ms) RTT. Additionally, by measuring request start and end times “on the wire”, without taking into account QUIC’s shorter connection establishment, we believe the results indicate QUIC’s suitability also under the long-lived (standing) connection model. -

Internet Protocol Suite
InternetInternet ProtocolProtocol SuiteSuite Srinidhi Varadarajan InternetInternet ProtocolProtocol Suite:Suite: TransportTransport • TCP: Transmission Control Protocol • Byte stream transfer • Reliable, connection-oriented service • Point-to-point (one-to-one) service only • UDP: User Datagram Protocol • Unreliable (“best effort”) datagram service • Point-to-point, multicast (one-to-many), and • broadcast (one-to-all) InternetInternet ProtocolProtocol Suite:Suite: NetworkNetwork z IP: Internet Protocol – Unreliable service – Performs routing – Supported by routing protocols, • e.g. RIP, IS-IS, • OSPF, IGP, and BGP z ICMP: Internet Control Message Protocol – Used by IP (primarily) to exchange error and control messages with other nodes z IGMP: Internet Group Management Protocol – Used for controlling multicast (one-to-many transmission) for UDP datagrams InternetInternet ProtocolProtocol Suite:Suite: DataData LinkLink z ARP: Address Resolution Protocol – Translates from an IP (network) address to a network interface (hardware) address, e.g. IP address-to-Ethernet address or IP address-to- FDDI address z RARP: Reverse Address Resolution Protocol – Translates from a network interface (hardware) address to an IP (network) address AddressAddress ResolutionResolution ProtocolProtocol (ARP)(ARP) ARP Query What is the Ethernet Address of 130.245.20.2 Ethernet ARP Response IP Source 0A:03:23:65:09:FB IP Destination IP: 130.245.20.1 IP: 130.245.20.2 Ethernet: 0A:03:21:60:09:FA Ethernet: 0A:03:23:65:09:FB z Maps IP addresses to Ethernet Addresses -

Using PANA for Mobile Ipv6 Bootstrapping Julien Bournelle, Jean-Michel Combes, Maryline Laurent, Sondes Larafa
Using PANA for mobile IPv6 bootstrapping Julien Bournelle, Jean-Michel Combes, Maryline Laurent, Sondes Larafa To cite this version: Julien Bournelle, Jean-Michel Combes, Maryline Laurent, Sondes Larafa. Using PANA for mobile IPv6 bootstrapping. NETWORKING 2007 : 6th international IFIP-TC6 networking conference on ad hoc and sensor networks, wireless networks, next generation Internet, May 2007, Atlanta, United States. pp.345 - 355, 10.1007/978-3-540-72606-7_30. hal-01328113 HAL Id: hal-01328113 https://hal.archives-ouvertes.fr/hal-01328113 Submitted on 7 Jun 2016 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Using PANA for Mobile IPv6 Bootstrapping Julien Bournelle1, Jean-Michel Combes2, Maryline Laurent-Maknavicius1, Sondes Larafa1 1 GET/INT, 9 rue Charles Fourier, 91011 Evry, France 2 France Telecom R&D, 38/40 rue du General Leclerc, 92784 Issy-Les-Moulineaux, France Abstract One of the current challenge of the Mo- 2 Mobile IPv6 Overview bile IPv6 Working Group at the IETF is to dynami- As it stands in [1], an IPv6 Mobile Node (MN) is cally assign to a Mobile Node its Home Agent, Home uniquely identi¯ed by its Home Address (HoA), and Address and to setup necessary security associations. -

Ipv6 Security: Myths & Legends
IPv6 security: myths & legends Paul Ebersman – [email protected] 21 Apr 2015 NANOG on the Road – Boston So many new security issues with IPv6! Or are there… IPv6 Security issues • Same problem, different name • A few myths & misconceptions • Actual new issues • FUD (Fear Uncertainty & Doubt) Round up the usual suspects! Remember these? • ARP cache poisoning • P2p ping pong attacks • Rogue DHCP ARP cache poisoning • Bad guy broadcasts fake ARP • Hosts on subnet put bad entry in ARP Cache • Result: MiM or DOS Ping pong attack • P2P link with subnet > /31 • Bad buy sends packet for addr in subnet but not one of two routers • Result: Link clogs with routers sending packet back and forth Rogue DHCP • Client broadcasts DHCP request • Bad guy sends DHCP offer w/his “bad” router as default GW • Client now sends all traffic to bad GW • Result: MiM or DOS Look similar? • Neighbor cache corruption • P2p ping pong attacks • Rogue DHCP + rogue RA Solutions? • Lock down local wire • /127s for p2p links (RFC 6164) • RA Guard (RFC 6105) And now for something completely different! So what is new? • Extension header chains • Packet/Header fragmentation • Predictable fragment headers • Atomic fragments The IPv4 Packet 14 The IPv6 Packet 15 Fragmentation • Minimum 1280 bytes • Only source host can fragment • Destination must get all fragments • What happens if someone plays with fragments? IPv6 Extension Header Chains • No limit on length • Deep packet inspection bogs down • Confuses stateless firewalls • Fragments a problem • draft-ietf-6man-oversized-header-chain-09 -

The Internet Protocol, Version 4 (Ipv4)
Today’s Lecture I. IPv4 Overview The Internet Protocol, II. IP Fragmentation and Reassembly Version 4 (IPv4) III. IP and Routing IV. IPv4 Options Internet Protocols CSC / ECE 573 Fall, 2005 N.C. State University copyright 2005 Douglas S. Reeves 1 copyright 2005 Douglas S. Reeves 2 Internet Protocol v4 (RFC791) Functions • A universal intermediate layer • Routing IPv4 Overview • Fragmentation and reassembly copyright 2005 Douglas S. Reeves 3 copyright 2005 Douglas S. Reeves 4 “IP over Everything, Everything Over IP” IP = Basic Delivery Service • Everything over IP • IP over everything • Connectionless delivery simplifies router design – TCP, UDP – Dialup and operation – Appletalk – ISDN – Netbios • Unreliable, best-effort delivery. Packets may be… – SCSI – X.25 – ATM – Ethernet – lost (discarded) – X.25 – Wi-Fi – duplicated – SNA – FDDI – reordered – Sonet – ATM – Fibre Channel – Sonet – and/or corrupted – Frame Relay… – … – Remote Direct Memory Access – Ethernet • Even IP over IP! copyright 2005 Douglas S. Reeves 5 copyright 2005 Douglas S. Reeves 6 1 IPv4 Datagram Format IPv4 Header Contents 0 4 8 16 31 •Version (4 bits) header type of service • Functions version total length (in bytes) length (x4) prec | D T R C 0 •Header Length x4 (4) flags identification fragment offset (x8) 1. universal 0 DF MF s •Type of Service (8) e time-to-live (next) protocol t intermediate layer header checksum y b (hop count) identifier •Total Length (16) 0 2 2. routing source IP address •Identification (16) 3. fragmentation and destination IP address reassembly •Flags (3) s •Fragment Offset ×8 (13) e t 4. Options y IP options (if any) b •Time-to-Live (8) 0 4 ≤ •Protocol Identifier (8) s e t •Header Checksum (16) y b payload 5 •Source IP Address (32) 1 5 5 6 •Destination IP Address (32) ≤ •IP Options (≤ 320) copyright 2005 Douglas S. -

61A Lecture 35 Distributed Computing Internet Protocol Transmission
Announcements • Homework 9 (6 pts) due Wednesday 11/26 @ 11:59pm ! Homework Party Monday 6pm-8pm in 2050 VLSB • Guest in live lecture, TA Soumya Basu, on Monday 11/24 • Optional Scheme recursive art contest due Monday 12/1 @ 11:59pm 61A Lecture 35 • No lecture on Wednesday 11/26 (turkey) • No lab on Tuesday 11/25 & Wednesday 11/26 • The week of 12/1: Homework 10 due Wednesday 12/3 & Quiz 3 due Thursday 12/4 on SQL Monday, November 24 ! The lab on SQL (12/2 & 12/3) will be an excellent place to get homework help 2 Distributed Computing A distributed computing application consists of multiple programs running on multiple computers that together coordinate to perform some task. • Computation is performed in parallel by many computers. • Information can be restricted to certain computers. • Redundancy and geographic diversity improve reliability. Distributed Computing Characteristics of distributed computing: • Computers are independent — they do not share memory. • Coordination is enabled by messages passed across a network. • Individual programs have differentiating roles. Distributed computing for large-scale data processing: • Databases respond to queries over a network. • Data sets can be partitioned across multiple machines (next lecture). 4 Network Messages Computers communicate via messages: sequences of bytes transmitted over a network. Messages can serve many purposes: • Send data to another computer • Request data from another computer • Instruct a program to call a function on some arguments. Internet Protocol • Transfer a program to be executed by another computer. Messages conform to a message protocol adopted by both the sender (to encode the message) & receiver (to interpret the message). -

Manual Update Configuring a Default Gateway
S3290 Manual Update Configuring a Default Gateway The following information is to be included with the S3290 Web User Guide. IP Configuration Configure the S3290-managed IPv4 information from Configuration > System > IP as one of the first steps. The S3290 supports an IPv4 / IPv6 dual stack. The S3290 can be assigned IP address statically or dynamically using DHCP. Here you can configure IP basic settings, IP interfaces and IP routes. Up to 8 interfaces and up to 32 routes are supported. IP Routes Click the Add Route button to display the editable fields: Delete Select this option to delete an existing IP route. Network The destination IP network or host address of this route. Valid format is dotted decimal notation or a valid IPv6 notation. A default route can use the value 0.0.0.0 or IPv6 :: notation. Mask Length The destination IP network or host mask, in number of bits (prefix length). It defines how much of a network address that must match, in order to qualify for this route. Valid values are 0 - 32 bits for IPv4 routes or 0 - 128 for IPv6 routes. Only a default route will have a mask length of 0 (as it will match anything). Gateway The IP address of the IP gateway. Valid format is dotted decimal notation or a valid IPv6 notation. The Gateway and Network must be of the same type. It may be necessary to add a static route if a default gateway is required or if the device does not reside within the same network. Routing can then be enabled at System > IP > IP Configuration. -

Ipv6 – What Is It, Why Is It Important, and Who Is in Charge? … Answers to Common Questions from Policy Makers, Executives and Other NonTechnical Readers
IPv6 – What is it, why is it important, and who is in charge? … answers to common questions from policy makers, executives and other nontechnical readers. A factual paper prepared for and endorsed by the Chief Executive Officers of ICANN and all the Regional Internet Registries, October 2009. 1. What is IPv6? “IP” is the Internet Protocol, the set of digital communication codes which underlies the Internet infrastructure. IP allows the flow of packets of data between any pair of points on the network, providing the basic service upon which the entire Internet is built. Without IP, the Internet as we know it would not exist. Currently the Internet makes use of IP version 4, or IPv4, which is now reaching the limits of its capacity to address additional devices. IPv6 is the “next generation” of IP, which provides a vastly expanded address space. Using IPv6, the Internet will be able to grow to millions of times its current size, in terms of the numbers of people, devices and objects connected to it1. 2. Just how big is IPv6? To answer this question, we must compare the IPv6 address architecture with that of IPv4. The IPv4 address has 32 bits, allowing today’s Internet to connect up to around four billion devices. By contrast, IPv6 has an address of 128 bits. Because each additional bit doubles the size of the address space, an extra 96 bits increases the theoretical size of the address space by many trillions of times. For comparison, if IPv4 were represented as a golf ball, then IPv6 would be approaching the size of the Sun.2 IPv6 is certainly not infinite, but it is not going to run out any time soon. -

Guidelines for the Secure Deployment of Ipv6
Special Publication 800-119 Guidelines for the Secure Deployment of IPv6 Recommendations of the National Institute of Standards and Technology Sheila Frankel Richard Graveman John Pearce Mark Rooks NIST Special Publication 800-119 Guidelines for the Secure Deployment of IPv6 Recommendations of the National Institute of Standards and Technology Sheila Frankel Richard Graveman John Pearce Mark Rooks C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 December 2010 U.S. Department of Commerce Gary Locke, Secretary National Institute of Standards and Technology Dr. Patrick D. Gallagher, Director GUIDELINES FOR THE SECURE DEPLOYMENT OF IPV6 Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-119 Natl. Inst. Stand. Technol. Spec. Publ. 800-119, 188 pages (Dec. 2010) Certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. -

DOD Memorandum: Department of Defense Implementation of Internet
DEPUTY SECRETARY OF DEFENSE 1010 DEFENSE PENTAGON WASHINGTON DC 20301-1010 June 29, 2021 MEMORANDUM FOR SENIOR PENTAGON LEADERSHIP DEFENSE AGENCY AND DOD FIELD ACTIVITY DIRECTORS SUBJECT: Directive-type Memorandum 21-004 – “Department of Defense Implementation of Internet Protocol Version 6” References: See Attachment 1 Purpose. Pursuant to the Federal requirements in Office of Management and Budget (OMB) Memorandum M-21-07, this directive-type memorandum (DTM): • Establishes policy, assigns responsibilities, and prescribes procedures for deploying and using Internet Protocol version 6 (IPv6) in DoD information systems. • Is effective June 29, 2021; it will be converted to a new DoD instruction. This DTM will expire effective 12 months from the date issuance is published on the DoD Issuances Website, June 29, 2022. Applicability. This DTM: • Applies to OSD, the Military Departments (including the Coast Guard at all times, including when it is a Service in the Department of Homeland Security by agreement with that Department), the Office of the Chairman of the Joint Chiefs of Staff and the Joint Staff, the Combatant Commands, the Office of Inspector General of the Department of Defense, the Defense Agencies, the DoD Field Activities, and all other organizational entities within DoD (referred to collectively in this issuance as the “DoD Components”). • Does not apply to National Security Systems, as defined by Committee on National Security Systems Instruction 4009. Definitions. See Glossary. Policy. Pursuant to OMB Memorandum M-21-07, all new networked DoD information systems that use internet protocol (IP) technologies will be IPv6-enabled before implementation and operational use by the end of fiscal year (FY) 2023.