Ipv6 – What Is It, Why Is It Important, and Who Is in Charge? … Answers to Common Questions from Policy Makers, Executives and Other NonTechnical Readers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Future of Internet Governance: Should the United States Relinquish Its Authority Over ICANN?
The Future of Internet Governance: Should the United States Relinquish Its Authority over ICANN? Lennard G. Kruger Specialist in Science and Technology Policy September 1, 2016 Congressional Research Service 7-5700 www.crs.gov R44022 The Future of Internet Governance: Should the U.S. Relinquish Its Authority over ICANN Summary Currently, the U.S. government retains limited authority over the Internet’s domain name system, primarily through the Internet Assigned Numbers Authority (IANA) functions contract between the National Telecommunications and Information Administration (NTIA) and the Internet Corporation for Assigned Names and Numbers (ICANN). By virtue of the IANA functions contract, the NTIA exerts a legacy authority and stewardship over ICANN, and arguably has more influence over ICANN and the domain name system (DNS) than other national governments. Currently the IANA functions contract with NTIA expires on September 30, 2016. However, NTIA has the flexibility to extend the contract for any period through September 2019. On March 14, 2014, NTIA announced the intention to transition its stewardship role and procedural authority over key Internet domain name functions to the global Internet multistakeholder community. To accomplish this transition, NTIA asked ICANN to convene interested global Internet stakeholders to develop a transition proposal. NTIA stated that it would not accept any transition proposal that would replace the NTIA role with a government-led or an intergovernmental organization solution. For two years, Internet stakeholders were engaged in a process to develop a transition proposal that will meet NTIA’s criteria. On March 10, 2016, the ICANN Board formally accepted the multistakeholder community’s transition plan and transmitted that plan to NTIA for approval. -

The Regional Internet Registry System Leslie Nobile
“How It Works” The Regional Internet Registry System Leslie Nobile v Overview • The Regional Internet Registry System • Internet Number Resource Primer: IPv4, IPv6 and ASNs • Significant happenings at the RIR • IPv4 Depletion and IPv6 Transition • IPv4 transfer market • Increase in fraudulent activity • RIR Tools, technologies, etc. 2 The Regional Internet Registry System 3 Brief History Internet Number Resource Administration • 1980s to 1990s • Administration of names, numbers, and protocols contracted by US DoD to ISI/Jon Postel (eventually called IANA) • Registration/support of this function contracted to SRI International and then to Network Solutions • Regionalization begins - Regional Internet Registry system Jon Postel forms • IP number resource administration split off from domain name administration • US Govt separates administration of commercial Internet (InterNIC) from the military Internet (DDN NIC) 4 What is an RIR? A Regional Internet Registry (RIR) manages the allocation and registration of Internet number resources in a particular region of the world and maintains a unique registry of all IP numbers issued. *Number resources include IP addresses (IPv4 and IPv6) and autonomous system (AS) numbers 5 Who Are the RIRs? 6 Core Functions of an RIR Manage, distribute -Maintain directory -Support Internet and register Internet services including infrastructure through Number Resources Whois and routing technical coordination (IPv4 & IPv6 registries addresses and Autonomous System -Facilitate community numbers (ASNs) -Provide -

IANA Report on Recognition of Afrinic As a Regional Internet Registry
IANA Report Subject: Recognition of AfriNIC as a Regional Internet Registry Date: 6 April 2005 The Internet Assigned Numbers Authority (the IANA), as part of the administrative functions associated with management of the Internet Protocol (IP) address space, is responsible for evaluating applications for approval of new Regional Internet Registries. ICANN has received an application for final approval and recognition of the African Internet Numbers Registry (AfriNIC) as the fifth Regional Internet Registry (RIR). Background The role and responsibilities of ICANN/IANA in this area are defined in the Address Supporting Organization Memorandum of Understanding <http://www.icann.org/aso/aso- mou-29oct04.htm> (ASO MOU), and ICP-2 <http://www.icann.org/icp/icp-2.htm> ("Criteria for Establishment of New Regional Internet Registries"). In September 2004, an application was submitted by the AfriNIC organization for recognition, together with a detailed transition which included draft bylaws, policies, funding model, and staff resumes. On request of the ICANN President, the IANA staff conducted a preliminary evaluation. In September 2004 the President reported to the Board his conclusion that the application and transition plan constituted a reasonable basis for eventual recognition, though he noted that some adjustments would be necessary. Also in September 2004, the existing RIRs, APNIC, ARIN, LACNIC and RIPE NCC, through the Number Resource Organization (NRO), issued a statement expressing their ongoing and continuing support for AfriNIC, and recommending a favorable response to the application by recognizing AfriNIC's accomplishments thus far. Consistent with the IANA©s preliminary evaluation and the recommendations of the existing RIRs, the ICANN Board on 30 September 2004 gave provisional approval <http://www.icann.org/minutes/resolutions-30sep04.htm> to the AfriNIC application, with the expectation that the transition plan would be completed and an amended or revised application for recognition would be submitted. -

Empirical Analysis of the Effects and the Mitigation of Ipv4 Address Exhaustion
TECHNISCHE UNIVERSITÄT BERLIN FAKULTÄT FÜR ELEKTROTECHNIK UND INFORMATIK LEHRSTUHL FÜR INTELLIGENTE NETZE UND MANAGEMENT VERTEILTER SYSTEME Empirical Analysis of the Effects and the Mitigation of IPv4 Address Exhaustion vorgelegt von M.Sc. Philipp Richter geboren in Berlin von der Fakultät IV – Elektrotechnik und Informatik der Technischen Universität Berlin zur Erlangung des akademischen Grades DOKTOR DER NATURWISSENSCHAFTEN -DR. RER. NAT.- genehmigte Dissertation Promotionsausschuss: Vorsitzender: Prof. Dr.-Ing. Sebastian Möller, Technische Universität Berlin Gutachterin: Prof. Anja Feldmann, Ph.D., Technische Universität Berlin Gutachter: Prof. Vern Paxson, Ph.D., University of California, Berkeley Gutachter: Prof. Steve Uhlig, Ph.D., Queen Mary University of London Tag der wissenschaftlichen Aussprache: 2. August 2017 Berlin 2017 Abstract IP addresses are essential resources for communication over the Internet. In IP version 4, an address is represented by 32 bits in the IPv4 header; hence there is a finite pool of roughly 4B addresses available. The Internet now faces a fundamental resource scarcity problem: The exhaustion of the available IPv4 address space. In 2011, the Internet Assigned Numbers Authority (IANA) depleted its pool of available IPv4 addresses. IPv4 scarcity is now reality. In the subsequent years, IPv4 address scarcity has started to put substantial economic pressure on the networks that form the Internet. The pools of available IPv4 addresses are mostly depleted and today network operators have to find new ways to satisfy their ongoing demand for IPv4 addresses. Mitigating IPv4 scarcity is not optional, but mandatory: Networks facing address shortage have to take action in order to be able to accommodate additional subscribers and customers. Thus, if not confronted, IPv4 scarcity has the potential to hinder further growth of the Internet. -

Ipv6 AAAA DNS Whitelisting a BROADBAND INTERNET TECHNICAL ADVISORY GROUP TECHNICAL WORKING GROUP REPORT
IPv6 AAAA DNS Whitelisting A BROADBAND INTERNET TECHNICAL ADVISORY GROUP TECHNICAL WORKING GROUP REPORT A Near-Uniform Agreement Report (100% Consensus Achieved) Issued: September 2011 Copyright / Legal NotiCe Copyright © Broadband Internet Technical Advisory Group, Inc. 2011. All rights reserved. This document may be reproduced and distributed to others so long as such reproduction or distribution complies with Broadband Internet Technical Advisory Group, Inc.’s Intellectual Property Rights Policy, available at www.bitag.org, and any such reproduction contains the above copyright notice and the other notices contained in this section. This document may not be modified in any way without the express written consent of the Broadband Internet Technical Advisory Group, Inc. This document and the information contained herein is provided on an “AS IS” basis and BITAG AND THE CONTRIBUTORS TO THIS REPORT MAKE NO (AND HEREBY EXPRESSLY DISCLAIM ANY) WARRANTIES (EXPRESS, IMPLIED OR OTHERWISE), INCLUDING IMPLIED WARRANTIES OF MERCHANTABILITY, NON-INFRINGEMENT, FITNESS FOR A PARTICULAR PURPOSE, OR TITLE, RELATED TO THIS REPORT, AND THE ENTIRE RISK OF RELYING UPON THIS REPORT OR IMPLEMENTING OR USING THE TECHNOLOGY DESCRIBED IN THIS REPORT IS ASSUMED BY THE USER OR IMPLEMENTER. The information contained in this Report was made available from contributions from various sources, including members of Broadband Internet Technical Advisory Group, Inc.’s Technical Working Group and others. Broadband Internet Technical Advisory Group, Inc. takes no position regarding the validity or scope of any intellectual property rights or other rights that might be claimed to pertain to the implementation or use of the technology described in this Report or the extent to which any license under such rights might or might not be available; nor does it represent that it has made any independent effort to identify any such rights. -

9 China and Global Internet Governance a Tiger by the Tail
9 China and Global Internet Governance A Tiger by the Tail Milton L. Mueller As of June 2010 the Chinese government claimed the country’ s number of “ netizens, ” or Internet users, had increased to 430 million. 1 That very large number is only 32 percent of China ’ s total population. 2 Already one of the biggest presences on the Internet, and with a long way to go yet, China and the Internet enjoy a complex and seemingly paradoxical relationship. Many Westerners have trouble making sense of the way China ’ s socialist market economy (SME) combines heavy restrictions with vibrant growth, and globalized networking with an insistence on territorial sover- eignty. Western observers have long abandoned the notion that the Internet was inherently uncontrollable and that its use would automatically overthrow dictator- ships. They are now replacing that simplistic notion with an equally coarse inversion: the image of China as the constructor of an impregnable “ Great Firewall, ” a place of omnipotent surveillance, a population susceptible to well-organized propaganda cam- paigns, and a source of pervasive and insidious cyber attacks and cyber espionage. It is a new Internet version of the Cold War. The Internet in the People ’ s Republic of China (PRC) strains and challenges the capacity of the Chinese Communist Party (CCP) to maintain control. And the fact that China needs to be linked to the external world, through the Internet as well as through trade, provides a double challenge. The international environment of Internet governance is freer, is private-sector based, and is more capitalistic than China ’ s rulers would prefer. -

Guidelines for the Secure Deployment of Ipv6
Special Publication 800-119 Guidelines for the Secure Deployment of IPv6 Recommendations of the National Institute of Standards and Technology Sheila Frankel Richard Graveman John Pearce Mark Rooks NIST Special Publication 800-119 Guidelines for the Secure Deployment of IPv6 Recommendations of the National Institute of Standards and Technology Sheila Frankel Richard Graveman John Pearce Mark Rooks C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 December 2010 U.S. Department of Commerce Gary Locke, Secretary National Institute of Standards and Technology Dr. Patrick D. Gallagher, Director GUIDELINES FOR THE SECURE DEPLOYMENT OF IPV6 Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-119 Natl. Inst. Stand. Technol. Spec. Publ. 800-119, 188 pages (Dec. 2010) Certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. -

DOD Memorandum: Department of Defense Implementation of Internet
DEPUTY SECRETARY OF DEFENSE 1010 DEFENSE PENTAGON WASHINGTON DC 20301-1010 June 29, 2021 MEMORANDUM FOR SENIOR PENTAGON LEADERSHIP DEFENSE AGENCY AND DOD FIELD ACTIVITY DIRECTORS SUBJECT: Directive-type Memorandum 21-004 – “Department of Defense Implementation of Internet Protocol Version 6” References: See Attachment 1 Purpose. Pursuant to the Federal requirements in Office of Management and Budget (OMB) Memorandum M-21-07, this directive-type memorandum (DTM): • Establishes policy, assigns responsibilities, and prescribes procedures for deploying and using Internet Protocol version 6 (IPv6) in DoD information systems. • Is effective June 29, 2021; it will be converted to a new DoD instruction. This DTM will expire effective 12 months from the date issuance is published on the DoD Issuances Website, June 29, 2022. Applicability. This DTM: • Applies to OSD, the Military Departments (including the Coast Guard at all times, including when it is a Service in the Department of Homeland Security by agreement with that Department), the Office of the Chairman of the Joint Chiefs of Staff and the Joint Staff, the Combatant Commands, the Office of Inspector General of the Department of Defense, the Defense Agencies, the DoD Field Activities, and all other organizational entities within DoD (referred to collectively in this issuance as the “DoD Components”). • Does not apply to National Security Systems, as defined by Committee on National Security Systems Instruction 4009. Definitions. See Glossary. Policy. Pursuant to OMB Memorandum M-21-07, all new networked DoD information systems that use internet protocol (IP) technologies will be IPv6-enabled before implementation and operational use by the end of fiscal year (FY) 2023. -

Ipv4 and Ipv6 Subnetting Demo
IPv4 and IPv6 Subnetting Demo Instructor: Networks rely on the use of IP addresses to allow devices to communicate with each other. These addresses are often obtained as a single large block and are given to the organizations that require them. However, a single block of addresses rarely meets the needs of a network and it needs to be segmented in order to better accommodate the network. An IP address is made up of two parts, the address itself and the subnet mask. The subnet mask helps us determine which part of the address defines the network and which part defines the specific host in the network. This is done by comparing the binary bits of the subnet mask to the address itself. Where there is a one in the subnet mask, we are looking at the network portion of the address; where there is a zero, we are looking at the host portion, or the identifier of the specific machine. The subnet can be represented in "CIDR" notation which includes a slash followed by the number of ones, or network bits, in the subnet. So the subnet mask 255.255.255.0 could be shortened to /24 because there are 24 binary ones. Subnets are an effective way to segment a single large network into a Page 1 of 4 group of smaller ones. In IPv4, this concept is fairly simple. A network will be assigned an address block, let's say 192.168.1.0/24. Then, we determine the amount of subnets we need and how many hosts we need in each subnet. -

Ipv6 Cheat Sheet
Internet Protocol Version 6 (IPv6) Basics Cheat Sheet IPv6 Addresses by Jens Roesen /64 – lan segment, 18,446,744,073,709,551,616 v6 IPs IPv6 quick facts /48 – subscriber site, 65536 /64 lan segments successor of IPv4 • 128-bit long addresses • that's 296 times the IPv4 address space • that's 2128 or 3.4x1038 or over 340 /32 – minimum allocation size, 65536 /48 subscriber sites, allocated to ISPs undecillion IPs overall • customer usually gets a /64 subnet, which yields 4 billion times the Ipv4 address space • no need for network address translation (NAT) any more • no broadcasts any more • no ARP • stateless address 2001:0db8:0f61:a1ff:0000:0000:0000:0080 configuration without DHCP • improved multicast • easy IP renumbering • minimum MTU size 1280 • mobile IPv6 • global routing prefix subnet ID interface ID mandatory IPsec support • fixed IPv6 header size of 40 bytes • extension headers • jumbograms up to 4 GiB subnet prefix /64 IPv6 & ICMPv6 Headers IPv6 addresses are written in hexadecimal and divided into eight pairs of two byte blocks, each containing four hex IPv6 header digits. Addresses can be shortened by skipping leading zeros in each block. This would shorten our example address to 0 8 16 24 32 2001:db8:f61:a1ff:0:0:0:80. Additionally, once per IPv6 IP, we can replace consecutive blocks of zeros with a version traffic class flow label double colon: 2001:db8:f61:a1ff::80. The 64-bit interface ID can/should be in modified EUI-64 format. A MAC 00 03 ba 24 a9 6c payload length next header hop limit 48-bit MAC can be transformed to an 64-bit interface ID by inverting the 7th (universal) bit and inserting a ff and fe byte after rd source IPv6 address the 3 byte. -
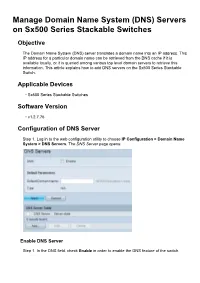
Manage Domain Name System (DNS) Servers on Sx500 Series Stackable Switches
Manage Domain Name System (DNS) Servers on Sx500 Series Stackable Switches Objective The Domain Name System (DNS) server translates a domain name into an IP address. This IP address for a particular domain name can be retrieved from the DNS cache if it is available locally, or it is queried among various top level domain servers to retrieve this information. This article explains how to add DNS servers on the Sx500 Series Stackable Switch. Applicable Devices • Sx500 Series Stackable Switches Software Version • v1.2.7.76 Configuration of DNS Server Step 1. Log in to the web configuration utility to choose IP Configuration > Domain Name System > DNS Servers. The DNS Server page opens: Enable DNS Server Step 1. In the DNS field, check Enable in order to enable the DNS feature of the switch. Step 2. In the Default Domain Name field in the Default Parameters area, enter the domain name that you want to configure as Fully Qualified Domain Name (FQDN). The switch appends this domain name to non-fully qualified domain names to make them FQDNs. Note: The switch identifies the default domain name server type in the Type field. • DHCP — Default name is given dynamically by the DHCP Server. • Static — Default name is user-defined. • N/A — No default domain name. Step 3. Click Apply to save the DNS settings. Add DNS Server Step 1. In the DNS Server Table, click Add at the bottom of the table to add DNS servers so that the switch can query the IP address of domain names. Step 2. In the IP Version field, click either the Version 4 radio button or the Version 6 radio button based upon the type of server IP address (IPv4 or IPv6). -

Ipv6 and DNS Ipv6 – the Future of IP
IPv6 and DNS Chapters 22,29 CSA 442 IPv6 – The Future of IP • Current version of IP - version 4 - is over 20 years old • IPv4 has shown remarkable ability to move to new technologies – IP has accommodated dramatic changes since original design – Basic principles still appropriate today – Many new types of hardware – Scaling - from a few tens to a few tens of millions of computers • But, as with any old technology, it has some problems • IETF has proposed entirely new version to address some specific problems 1 Motivation for Change • Address space – 32 bit address space allows for over a million networks – But…all that is left is Class C and too small for many organizations – Predictions we would have run out of IP addresses by now – Besides, how will we network all our toasters and cell phones to the Internet? • Type of service – Different applications have different requirements for delivery reliability and speed ; i.e. real time data, quality of service – Current IP has type of service that's not often implemented • Multicast Name and Version Number • Preliminary versions called IP - Next Generation (IPng) • Several proposals all called IPng • One was selected and uses next available version number (6) – Version 5 was already assigned to an experimental protocol, ST, Streams Protocol • Result is IP version 6 (IPv6) • In the works since 1990 2 New Features of IPv6 • Address size - IPv6 addresses are 128bits – ~3*1038 possible addresses in theory • Header format - entirely different • Extension headers - Additional information stored