Practical Wine
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Red Hat Enterprise Linux 6 Developer Guide
Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Dave Brolley William Cohen Roland Grunberg Aldy Hernandez Karsten Hopp Jakub Jelinek Developer Guide Jeff Johnston Benjamin Kosnik Aleksander Kurtakov Chris Moller Phil Muldoon Andrew Overholt Charley Wang Kent Sebastian Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Edition 0 Author Dave Brolley [email protected] Author William Cohen [email protected] Author Roland Grunberg [email protected] Author Aldy Hernandez [email protected] Author Karsten Hopp [email protected] Author Jakub Jelinek [email protected] Author Jeff Johnston [email protected] Author Benjamin Kosnik [email protected] Author Aleksander Kurtakov [email protected] Author Chris Moller [email protected] Author Phil Muldoon [email protected] Author Andrew Overholt [email protected] Author Charley Wang [email protected] Author Kent Sebastian [email protected] Editor Don Domingo [email protected] Editor Jacquelynn East [email protected] Copyright © 2010 Red Hat, Inc. and others. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. -

Virtual Machine Technologies and Their Application in the Delivery of ICT
Virtual Machine Technologies and Their Application In The Delivery Of ICT William McEwan accq.ac.nz n Christchurch Polytechnic Institute of Technology Christchurch, New Zealand [email protected] ABSTRACT related areas - a virtual machine or network of virtual machines can be specially configured, allowing an Virtual Machine (VM) technology was first ordinary user supervisor rights, and it can be tested implemented and developed by IBM to destruction without any adverse effect on the corporation in the early 1960's as a underlying host system. mechanism for providing multi-user facilities This paper hopes to also illustrate how VM in a secure mainframe computing configurations can greatly reduce our dependency on environment. In recent years the power of special purpose, complex, and expensive laboratory personal computers has resulted in renewed setups. It also suggests the important additional role interest in the technology. This paper begins that VM and VNL is likely to play in offering hands-on by describing the development of VM. It practical experience to students in a distance e- discusses the different approaches by which learning environment. a VM can be implemented, and it briefly considers the advantages and disadvantages Keywords: Virtual Machines, operating systems, of each approach. VM technology has proven networks, e-learning, infrastructure, server hosting. to be extremely useful in facilitating the Annual NACCQ, Hamilton New Zealand July, 2002 www. Annual NACCQ, Hamilton New Zealand July, teaching of multiple operating systems. It th offers an alternative to the traditional 1. INTRODUCTION approaches of using complex combinations Virtual Machine (VM) technology is not new. It was of specially prepared and configured OS implemented on mainframe computing systems by the images installed via the network or installed IBM Corporation in the early 1960’s (Varian 1997 pp permanently on multiple partitions or on 3-25, Gribben 1989 p.2, Thornton 2000 p.3, Sugarman multiple physical hard drives. -

CASE STUDY Userful Multiplier and Win4lin Pro Reduce Costs of Point
CASE STUDY TM Userful Multiplier and Win4Lin Pro Reduce Costs of Point-of-Sale Terminals A Case Study by Omni Technology Solutions, leverage the Linux Desktop, he recommended the Userful a Userful Partner Multiplier*, a software add-on that allows multiple users to share a single computer. Win4Lin Pro Desktop was installed to allow Birchwood to run Simply Accounting on Linux. “Userful Multiplier* cut the hardware DOSEMU, which comes bundled with SUSE Linux, handled costs in half and Win4Lin Pro Desktop the DOS-based Framer’s Assistant point-of-sale application provided Windows compatibility to run quite nicely. their Simply Accounting package.” “Birchwood Art Gallery was always running into virus and - Mike Ducharme, spyware infections when they were using Windows 98 and IT consultant, Windows XP. Even with up-to-date anti-virus and anti- Birchwood Art Gallery spyware software, the systems were still getting major infections on a monthly basis, resulting in costly down-time Overview until they were cleaned up,” said Mr. Ducharme. “The security of Novell’s SUSE Linux Desktop provides peace of mind to Birchwood Art Gallery - based in Winnipeg, Canada - their staff,” continued Ducharme, “allowing them to carry out specializes in fine art reproductions and original artwork their work activities without fear of virus or spyware infesta- by a wide range of Canadian and international artists. On tion. Additionally, the Userful Multiplier* cut the hardware their web site and in their gallery, you will find artwork, costs in half and Win4Lin Pro Desktop provided Windows sculptures, prints and books from hundreds of artists. Lyn compatibility to run their Simply Accounting package.” Chercoe and Carole Solmundson, Birchwood Art Gallery’s owners, have earned a reputation for customer service The Results excellence since 1993 and sell art online all over the world. -

Improving Security Through Egalitarian Binary Recompilation
Improving Security Through Egalitarian Binary Recompilation David Williams-King Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy under the Executive Committee of the Graduate School of Arts and Sciences COLUMBIA UNIVERSITY 2021 © 2021 David Williams-King All Rights Reserved Abstract Improving Security Through Egalitarian Binary Recompilation David Williams-King In this thesis, we try to bridge the gap between which program transformations are possible at source-level and which are possible at binary-level. While binaries are typically seen as opaque artifacts, our binary recompiler Egalito (ASPLOS 2020) enables users to parse and modify stripped binaries on existing systems. Our technique of binary recompilation is not robust to errors in disassembly, but with an accurate analysis, provides near-zero transformation overhead. We wrote several demonstration security tools with Egalito, including code randomization, control-flow integrity, retpoline insertion, and a fuzzing backend. We also wrote Nibbler (ACSAC 2019, DTRAP 2020), which detects unused code and removes it. Many of these features, including Nibbler, can be combined with other defenses resulting in multiplicatively stronger or more effective hardening. Enabled by our recompiler, an overriding theme of this thesis is our focus on deployable software transformation. Egalito has been tested by collaborators across tens of thousands of Debian programs and libraries. We coined this term egalitarian in the context of binary security. Simply put, an egalitarian analysis or security mechanism is one that can operate on itself (and is usually more deployable as a result). As one demonstration of this idea, we created a strong, deployable defense against code reuse attacks. -

Chapter 1. Origins of Mac OS X
1 Chapter 1. Origins of Mac OS X "Most ideas come from previous ideas." Alan Curtis Kay The Mac OS X operating system represents a rather successful coming together of paradigms, ideologies, and technologies that have often resisted each other in the past. A good example is the cordial relationship that exists between the command-line and graphical interfaces in Mac OS X. The system is a result of the trials and tribulations of Apple and NeXT, as well as their user and developer communities. Mac OS X exemplifies how a capable system can result from the direct or indirect efforts of corporations, academic and research communities, the Open Source and Free Software movements, and, of course, individuals. Apple has been around since 1976, and many accounts of its history have been told. If the story of Apple as a company is fascinating, so is the technical history of Apple's operating systems. In this chapter,[1] we will trace the history of Mac OS X, discussing several technologies whose confluence eventually led to the modern-day Apple operating system. [1] This book's accompanying web site (www.osxbook.com) provides a more detailed technical history of all of Apple's operating systems. 1 2 2 1 1.1. Apple's Quest for the[2] Operating System [2] Whereas the word "the" is used here to designate prominence and desirability, it is an interesting coincidence that "THE" was the name of a multiprogramming system described by Edsger W. Dijkstra in a 1968 paper. It was March 1988. The Macintosh had been around for four years. -

CIS Ubuntu Linux 18.04 LTS Benchmark
CIS Ubuntu Linux 18.04 LTS Benchmark v1.0.0 - 08-13-2018 Terms of Use Please see the below link for our current terms of use: https://www.cisecurity.org/cis-securesuite/cis-securesuite-membership-terms-of-use/ 1 | P a g e Table of Contents Terms of Use ........................................................................................................................................................... 1 Overview ............................................................................................................................................................... 12 Intended Audience ........................................................................................................................................ 12 Consensus Guidance ..................................................................................................................................... 13 Typographical Conventions ...................................................................................................................... 14 Scoring Information ..................................................................................................................................... 14 Profile Definitions ......................................................................................................................................... 15 Acknowledgements ...................................................................................................................................... 17 Recommendations ............................................................................................................................................ -

Linux Games Page 1 of 7
Linux Games Page 1 of 7 Linux Games INTRODUCTION such as the number of players and the size of the map, then you start the game. Once the game is running clients may Hello. My name is Andrew Howlett. I've been using Linux join the game. Clients connect to the game using TCP/IP, since 1997. In 2000 I cutover to Linux for all my projects, so it is very easy to play multi-player games over the except I dual-booted Windows to play games. I like to play Internet. Like many Free games, clients are available for computer games. About a year ago I stopped dual booting. many platforms, including Windows, Amiga and Now I play computer games under Linux. The games I Macintosh. So there are lots of players out there. If you play can be divided into four groups: Free Games, native don't want to play against other humans, then Freeciv linux commercial games, Windows Emulated games, and includes some nasty AIs. Win4Lin enabled games. This presentation will demonstrate games from each of these four groups. BZFlag Platform BZFlag is a tank combat game along the same lines as the old BattleZone game. Like FreeCiv, BZFlag uses a client/ Before I get started, a little bit about my setup so you can server architecture over TCP/IP networks. Unlike FreeCiv, relate this to whatever you are running. This is a P3 900 the game contains no AIs – you must play this game MHz machine. It has a Crystal Sound 4600 sound card and against other humans (? entities ?) over the Internet. -
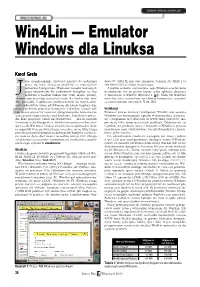
Win4lin — Emulator Windows Dla Linuksa
Win4Lin — Emulator Windows dla Linuksa Karol Grela ako chemik−organik, używający Linuksa do codziennej dows 95 OSR2 PL mój stary komputer Pentium 233 MMX z 64 pracy, nie mam zazwyczaj problemu ze znalezieniem MB RAM−u był aż nadto wystarczający. potrzebnych programów. Większość narzędzi tworzonych Z punktu widzenia użytkownika, sesja Windows uruchomiona przez naukowców dla naukowców kompiluje się bez w emulatorze jest po prostu jeszcze jedną aplikacją działającą problemu w każdym Uniksie (np. VMD, mopac, platon), w środowisku X Window (Rysunek 1, [8a]). Okno MS Windows a komercyjne posiadają zazwyczaj wersje dla Linuksa (np. mol− może być także wyświetlone na zdalnym komputerze, za pomo− den, pcmodel). Z aplikacjami przeznaczonymi dla innych syste− cą mechanizmów sieciowych X−ów [8b]. mów uniksowych, takimi jak XWinnmr dla Silicon Graphics, daje się bez problemu pracować w systemie X Window. Czasem jed− Instalacja nak muszę używać lub testować oprogramowanie, które nie po− Ponieważ proces instalacji i konfiguracji Win4Lin oraz systemu siada jeszcze odpowiednika pod Linuksem. Dodatkowo prowa− Windows jest wyczerpująco opisany w dokumentacji dostarcza− dzę kilka projektów, takich jak ChemPerfect — zestaw narzędzi nej z programem oraz dostępnej na WWW firmy TreLOS [5], sku− chemicznych do Wordperfecta. Projekt ten rozwijam w dwu wer− pię się na kilku mniej oczywistych punktach. Zakładam też, że sjach — dla Windows i Linuksa. Czasem muszę wprowadzić drob− Czytelnik zna podstawy pracy z Linuksem (i Windows), posiada ne poprawki w tej pierwszej wersji, a nie chce mi się tylko z tego uprawnienia roota i (ewentualnie) wie jak skompilować i zainsta− powodu restartować komputera i ładować MS Windows. Co więcej, lować jądro systemu. -

Linux Fundamentals Paul Cobbaut Linux Fundamentals Paul Cobbaut
Linux Fundamentals Paul Cobbaut Linux Fundamentals Paul Cobbaut Publication date 2015-05-24 CEST Abstract This book is meant to be used in an instructor-led training. For self-study, the intent is to read this book next to a working Linux computer so you can immediately do every subject, practicing each command. This book is aimed at novice Linux system administrators (and might be interesting and useful for home users that want to know a bit more about their Linux system). However, this book is not meant as an introduction to Linux desktop applications like text editors, browsers, mail clients, multimedia or office applications. More information and free .pdf available at http://linux-training.be . Feel free to contact the author: • Paul Cobbaut: [email protected], http://www.linkedin.com/in/cobbaut Contributors to the Linux Training project are: • Serge van Ginderachter: [email protected], build scripts and infrastructure setup • Ywein Van den Brande: [email protected], license and legal sections • Hendrik De Vloed: [email protected], buildheader.pl script We'd also like to thank our reviewers: • Wouter Verhelst: [email protected], http://grep.be • Geert Goossens: [email protected], http://www.linkedin.com/in/ geertgoossens • Elie De Brauwer: [email protected], http://www.de-brauwer.be • Christophe Vandeplas: [email protected], http://christophe.vandeplas.com • Bert Desmet: [email protected], http://blog.bdesmet.be • Rich Yonts: [email protected], Copyright 2007-2015 Netsec BVBA, Paul Cobbaut Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.3 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. -

Crossover Compared to Competing Emulation Solutions
CrossOver Compared to Competing Emulation Solutions CrossOver Compared to Competing Emulation Solutions CrossOver Compared to Competing Emulation Solutions Overview: Whether you’re running a Linux or Mac OS X machine, chances are you need a way to run at least some Windows applications or games that aren’t available on your platform of choice. And you have your choice of potential solutions to this problem. This page illustrates some of the key Every Windows advantages that CrossOver has in relation to the compatibility solution has other compatibility solutions. pros and cons. When presented with the need to run Windows applications on a Mac or Linux machine, you have basically three main choices: Dual-booting: running two separate operating systems on one PC, and switching between them as needed by rebooting. Applications such as Apple’s Bootcamp allow this to occur on a Mac OS X machine, for example. Running a virtual machine: Emulation products such as VMWare and Parallels allow you to install a copy of Windows within a logical partition within your native operating system. The Windows applications essentially run in a separate “box within a box.” Running Wine or CrossOver: Unlike emulation, Wine is a re-implementation of the Win32 API, allowing applications to run as if natively on the target OS. CrossOver is a commercialized version of Wine. Each solution has its advantages and disadvantages. This document is provided to help identify and evaluate key points of comparison between CodeWeavers’ CrossOver products and some of its key competitors. Technology Approach General Approach Dual-booting is exactly what it sounds like—shutting down one operating system, starting another, and dealing with the file transfer issues associated with same. -

An Empirical Study Into the Security Exposure to Hosts of Hostile Virtualized Environments
An Empirical Study into the Security Exposure to Hosts of Hostile Virtualized Environments Tavis Ormandy [email protected] Google, Inc. Abstract machine monitor is ‘root secure’[25], meaning that no level of As virtual machines become increasingly commonplace as privilege within the virtualized guest environment permits a method of separating hostile or hazardous code from com- interference with the host system. modity systems, the potential security exposure from imple- Detection mentation flaws has increased dramatically. This paper Detecting virtualized environments has been explored in investigates the state of popular virtual machine implementa- detail by other researchers[22]. Virtual machines employed in tions for x86 systems, employing a combination of source code malware analysis or honeypots should endeavour to be unde- auditing and blackbox random testing to assess the security tectable or risk changing the behaviour of the emulated code. exposure to the hosts of hostile virtualized environments. An emulated malware sample could choose to act benignly, Keywords for example, but when executed on a physical machine imme- virtualization, security, software testing diately performs some malicious action. Detection will not be considered any further in this paper, although being able to detect a virtual machine, or more spe- I. INTRODUCTION cifically, virtual machine implementation, may be a prerequi- Secure isolation is one of the fundamental concepts of vir- site for the more serious attacks investigated in this paper. tualization[15], confining a program to a virtualized environ- Without being able to identify which virtual machine imple- ment should guarantee that any action performed inside the mentation is present, an attacker would have difficulty deter- virtual machine cannot interfere with the system that hosts it1. -
![[Improving System Performance Using Application-Level Hints]](https://docslib.b-cdn.net/cover/7692/improving-system-performance-using-application-level-hints-1627692.webp)
[Improving System Performance Using Application-Level Hints]
Improving System Performance using Application-Level Hints Björn Döbel Technische Universität Dresden, Department of Computer Science, Operating Systems Group 8th June 2005 Supervising professor: Prof. Dr. Hermann Härtig Supervisor: Dipl.-Inf. Martin Pohlack Selbständigkeitserklärung Hiermit erkläre ich, die vorliegende Arbeit selbständig verfasst zu haben. Ich habe keine anderen als die im Quellenverzeichnis angegebenen Literaturhilfsmittel verwendet. Dresden, 08.06.2005 Björn Döbel 2 Contents 1 Introduction 5 1.1 State of the art .................................. 6 1.1.1 Monitoring ............................... 7 1.1.2 Resource management ......................... 8 1.1.3 Linux kernel modules ......................... 9 1.1.4 Caches in Linux ............................ 10 1.1.5 Using prefetching to increase application performance ........ 11 1.2 Related work .................................. 14 1.2.1 Transparent Informed Prefetch ..................... 14 1.2.2 Speculative Hinting ........................... 15 1.2.3 Integrating prefetching and caching .................. 16 2 Design 19 2.1 Disk accesses and application startup ...................... 19 2.2 Design goals ................................... 20 2.3 Design decisions ................................ 21 2.3.1 Collecting data ............................. 21 2.3.2 Modifying the Linux kernel ...................... 23 2.3.3 HintMod - the kernel module ...................... 24 2.3.4 HintGen - the hint generator ...................... 25 2.3.5 Application of hints .........................